PingOne for Enterprise and SLO
PingOne for Enterprise uses a single logout (SLO) process to log out all participants of a PingOne for Enterprise session. In the PingOne for Enterprise context, the session participants are the identity repository, PingOne for Enterprise, and any applications to which a user has signed on (SSO) for the session.
Any one of the session participants can initiate SLO. PingOne for Enterprise acts as the session authority, mediating the SLO request and response messages so that all participants are notified. In this way, when a user logs off, the PingOne for Enterprise session is ended for all participants.
PingOne for Enterprise supplies three SLO endpoints, each for a particular purpose:
https://sso.connect.pingidentity.com/sso/SLO.saml2/-
This is the normal SAML endpoint to receive SLO requests and responses. It can be used only by SAML applications or SAML IdPs. Here’s an illustration of standard SAML SLO:
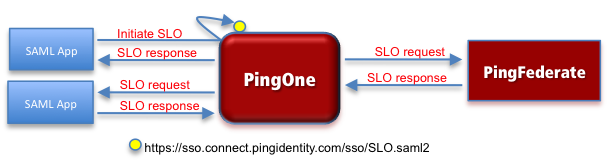
-
The user logs out of the SAML application, which results in an SLO request to PingOne.
-
PingOne for Enterprise redirects the request to
https://sso.connect.pingidentity.com/sso/SLO.saml2. -
PingOne for Enterprise sends SLO requests to the IdP and the other SAML application.
-
PingOne for Enterprise ends the user session.
-
PingOne for Enterprise sends the SLO response (session ended) to the SAML application.You can append the optional
idpidparameter to limit SLO only to sessions with the specifiedidpidvalue.The format for theidpidparameter is:
-
https://sso.connect.pingidentity.com/sso/SLO.saml2/?idpid=<idpid value>
https://sso.connect.pingidentity.com/sso/initslo/-
This is the PingOne for Enterprise endpoint to which non-SAML applications are redirected in response to their logout request. Here’s an illustration initiated by a non-SAML application:
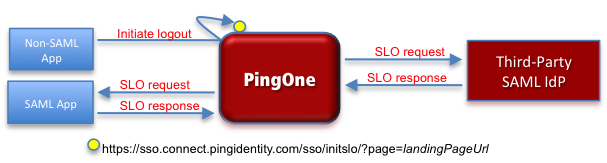
-
The user logs out of the non-SAML application, which results in an logout request to PingOne for Enterprise.
-
If specified, PingOne for Enterprise redirects the request to
https://sso.connect.pingidentity.com/sso/initslo/?page=<landing page URL>. -
PingOne for Enterprise sends SLO requests to the IdP and the other SAML application.
-
PingOne for Enterprise ends the user session. You can append the optional
pageparameter to specify a URL to direct logged out users to. The format for thepageparameter is:
-
https://sso.connect.pingidentity.com/sso/initslo/?page=<landing page URL>
If you specify the page parameter, PingOne for Enterprise will validate it. To be valid, an SLO page parameter value must meet one of the following criteria:
-
The URL has the same hostname as the identity provider’s (IdP’s) SSO URL.
-
The URL has the same hostname as the URL of one of the applications in the current session.
-
The URL has the same hostname as the
Assertion Consumer Service URLof one of the applications in the current SSO session. -
The domain of the URL is in the domain list of one of the applications in the current SSO session.
-
The URL is https://desktop.pingone.com/*.
-
The URL is https://sso.connect.pingidentity.com/*.
If we’re unable to validate the SLO page parameter value, the logout process continues and the page parameter is ignored. The PingOne default logout landing page then will be displayed. You can append the optional idpid parameter to limit SLO only to sessions with the specified idpid value. The format for the idpid parameter is:
https://sso.connect.pingidentity.com/sso/initslo/?idpid=<idpid value>
https://sso.connect.pingidentity.com/sso/terminatesession?page=logoutPageUrl-
This is the PingOne for Enterprise endpoint to which other participants are redirected when SLO isn’t supported or isn’t configured. The logout requests can be from non-SAML applications, non-SAML IdPs, or from a SAML IdP that doesn’t have SLO configured. Here’s an illustration of a session termination initiated by a non-SAML application and using Google as the IdP. In this case logoutPageUrl is https://accounts.google.com/Logout:
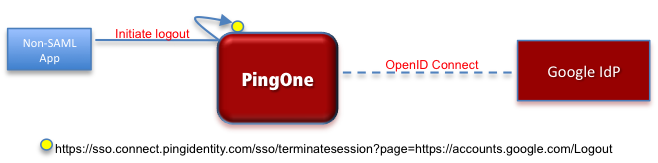
-
The user logs out of the non-SAML application, which results in a logout request to PingOne for Enterprise.
-
PingOne for Enterprise redirects the request to
https://sso.connect.pingidentity.com/sso/terminatesession?page=https://accounts.google.com/Logout. -
PingOne for Enterprise ends the user session.
{google} uses OpenID Connect as the authentication protocol, which does not support SLO.
You can append the optional page parameter to specify a URL to direct logged out users to. The format for the page parameter is:
https://sso.connect.pingidentity.com/sso/terminatesession?page=logoutPageUrl
If you specify the page parameter, PingOne for Enterprise will validate it. To be valid, an SLO page parameter value must meet one of the following criteria:
-
The URL has the same hostname as the identity provider’s (IdP’s) SSO URL.
-
The URL has the same hostname as the URL of one of the applications in the current session.
-
The URL has the same hostname as the
Assertion Consumer Service URLof one of the applications in the current SSO session. -
The domain of the URL is in the domain list of one of the applications in the current SSO session.
-
The URL is https://desktop.pingone.com/*.
-
The URL is https://sso.connect.pingidentity.com/*.
If we’re unable to validate the SLO page parameter value, the logout process continues and the page parameter is ignored. The PingOne for Enterprise default logout landing page then will be displayed. You can append the optional idpid parameter to limit SLO only to sessions with the specified idpid value. The format for the idpid parameter is:
https://sso.connect.pingidentity.com/sso/terminatesession?idpid=<idpid value>