SAML2 Authentication node
The SAML2 Authentication node integrates SAML 2.0 single sign-on into an authentication flow.
Use this node when deploying SAML 2.0 SSO in integrated mode (SP-initiated SSO only). This node doesn’t support single logout (SLO).
Implement the Write Federation Information node after this node in the journey to link the remote account to a local account.
Example
You can find examples that show this node in a SAML 2.0 authentication journey in SSO in integrated mode.
Availability
| Product | Available? |
|---|---|
PingOne Advanced Identity Cloud |
Yes |
PingAM (self-managed) |
Yes |
Ping Identity Platform (self-managed) |
Yes |
Dependencies
This node requires the following SAML 2.0 configuration:
-
A remote identity provider (IdP) and a hosted service provider (SP) in a circle of trust in the same realm where you’re configuring the journey.
-
You must configure the service provider for integrated mode.
Find more information in Configure Advanced Identity Cloud for integrated mode.
Configuration
| Property | Usage |
|---|---|
IdP Entity ID |
The name of the remote IdP. |
Validate IdP Entity ID |
Select this option to check that the IdP entity ID in the incoming SAML assertion matches the IdP entity ID configured for this node. If they don’t match, the journey proceeds to the The Default: |
SP MetaAlias |
The local alias for the SP in the format |
Allow IdP to Create NameID |
Select this option if you want the IdP to create a new identifier for the authenticating user if none exists. Learn more in AllowCreate in the SAML Version 2.0 specification. Default: |
Comparison Type |
The comparison method to evaluate authentication context classes or statements. This value overrides the value in the SP configuration: Find this value under Native Consoles > Access Management > Realms > Realm Name > Applications > Federation > Entity Providers > Service Provider Name > Assertion Content > Authentication Context > Comparison Type. Valid comparison methods are Learn more about comparison methods in Default: |
Authentication Context Class Reference |
(Optional) Set one or more URIs for authentication context classes to be included in the SAML request. Authentication context classes are unique identifiers for an authentication mechanism. The SAML 2.0 protocol supports a standard set of authentication context classes, defined in Authentication Context for the OASIS Security Assertion Markup Language (SAML) V2.0. You can specify your own authentication context classes in addition to the standard ones. Any authentication context class you specify here must be supported for the SP. To add authentication context classes to the SP:
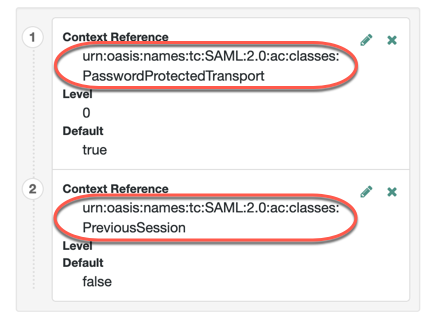
Use the | character to separate multiple authentication context classes, for example: urn:oasis:names:tc:SAML:2.0:ac:classes:Password|urn:oasis:names:tc:SAML:2.0:ac:classes:TimesyncToken |
Authentication Context Declaration Reference |
(Optional) One or more URIs that identify authentication context declarations. Use the | character to separate multiple URIs. Learn more in the section on the |
Request Binding |
The format of the authentication request that the SP sends to the IdP. Valid values are Default: |
Response Binding |
The format of the response that the IdP sends to the SP. Valid values are Default: |
Force IdP Authentication |
Indicate whether the IdP should force authentication or if it can reuse existing security contexts. Default: Disabled |
Passive Authentication |
Indicate whether the IdP should use passive authentication. When this setting is enabled, the IdP can only use authentication methods that don’t require user interaction, such as authenticating with an X.509 certificate. Default: Disabled |
NameID Format |
The SAML name ID format that’s requested in the SAML authentication request. Valid values are: urn:oasis:names:tc:SAML:2.0:nameid-format:persistent urn:oasis:names:tc:SAML:2.0:nameid-format:transient urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified Default: |
Outputs
This node updates the shared state with the SAML 2.0 assertion data as follows:
-
It adds a
userInfokey with two child keys:attributesanduserNames. -
The
attributesobject contains a map of SAML 2.0 attributes, each of which is stored as an array. -
The
attributesobject also stores the SAML 2.0 identity attributessun-fm-saml2-nameid-infoandsun-fm-saml2-nameid-infokey.These attributes are required by the Write Federation Information node.
-
The
userNamesobject contains the user’s UUID.
Example node state after node processing
{
"realm" : "/",
"authLevel" : 0,
"username" : "22fe07c3-ac8b-4e84-9016-b55f1c009924",
"userInfo" : {
"attributes" : {
"uid" : [ "bjensen" ],
"mail" : [ "bjensen@example.com" ],
"sun-fm-saml2-nameid-info" : [ "serviceprovider2|identityprovider1|sAdI2i7LT2YL0rbJC/QqsRt5SABV|identityprovider1|urn:oasis:names:tc:SAML:2.0:nameid-format:persistent|null|serviceprovider2|SPRole|false" ],
"sun-fm-saml2-nameid-infokey" : [ "serviceprovider2|identityprovider1|sAdI2i7LT2YL0rbJC/QqsRt5SABV" ]
},
"userNames" : {
"username" : [ "22fe07c3-ac8b-4e84-9016-b55f1c009924" ],
"uid" : [ "22fe07c3-ac8b-4e84-9016-b55f1c009924" ]
}
},
"emailAddress" : "bjensen@example.com"
}|
You can use a script to read the SAML 2.0 attributes, for example: |
The updated shared state depends on the node outcome:
-
If the outcome is
Account exists, the shared state is updated withnodeState.userNamesas follows:userNames={username=[bjensen], uid=[bjensen]}} -
If the outcome is
No account exists, the shared state is updated withnodeState.userNamesas follows:userNames={username=[null], uid=[null]}} -
If the
mailattribute exists in theattributesmap, the shared state is updated withnodeState.emailAddress. -
If the
RelayStateattribute exists in theattributesmap, the shared state is updated withnodeState.successUrl. -
The
usernameis added to the shared state, regardless of outcome.
The node also sets the following session properties:
-
SessionIndex: the session index -
NameID: the NameID of the Assertion XML -
isTransient: if the NameId isurn:oasis:names:tc:SAML:2.0:nameid-format:transient -
cacheKey: for internal use only
Outcomes
Account exists-
The node found a user account that matches the federated account.
No account exists-
The node didn’t find a matching user account.
Error-
The IdP entity ID in the incoming SAML assertion doesn’t match the IdP entity ID configured for this node.
Errors
This node can log the following errors:
| Message | Notes |
|---|---|
|
The node was unable to find the remote IdP descriptor. |
|
The node was unable to find the SP descriptor. |
|
The node was unable to retrieve the SAML 2.0 state from the second-factor authentication. |
|
The node was unable to read the SAML 2.0 response data. |
|
The node was unable to remove the SAML 2.0 response data. |
|
The |
|
The IdP entity ID in the incoming SAML assertion doesn’t match the IdP entity ID configured for this node. |