Authentication and SSO
These topics cover concepts, implementation procedures, and customization techniques for working with the authentication and single sign-on (SSO) features of PingAM.
Configure AM for authentication
Learn about AM’s authentication mechanisms.
Multi-factor authentication
Require that users provide multiple forms of identification when logging in to services.
Single sign-on
Enable single sign-on (SSO) so that users can log in once with a single set of credentials.
Social authentication
Allow users to authenticate to your services by using third-party identity providers.
Name changes for ForgeRock products
Product names changed when ForgeRock became part of Ping Identity.
The following name changes have been in effect since early 2024:
| Old name | New name |
|---|---|
ForgeRock Identity Cloud |
PingOne Advanced Identity Cloud |
ForgeRock Access Management |
PingAM |
ForgeRock Directory Services |
PingDS |
ForgeRock Identity Management |
PingIDM |
ForgeRock Identity Gateway |
PingGateway |
Learn more about the name changes in New names for ForgeRock products in the Knowledge Base.
Introduction to authentication
Authentication is the act of confirming a user’s identity, for example, by providing a set of credentials.
In access management, authentication is tightly coupled with authorization. Usually, it is important to confirm that a user is who they say they are, and to ensure that they can access only a subset of information.
Consider a user who wants to access an online shop. As the owner of the shop, you want to make sure the user identity is confirmed as it’s tied to their shipping and email addresses and payment information. You also want to ensure the user can only access their own information.
You can deploy a web agent on the web server hosting the online shop. The agent redirects the user’s request to an AM login page, where the user enters their credentials, such as username and password. AM determines who the user is, and whether the user has the right to access the protected page. AM then redirects the user back to the protected page with authorization credentials that can be verified by the agent. The agent allows the user authorized by AM to access the page.
In the same way, you can also use AM to protect physical devices connected on the Internet of Things (IoT). For example, a delivery van tracking system could have its proxying gateway authenticate to a brokering system using an X.509 certificate to allow it to enable an HTTPS protocol and then connect to sensors in its delivery trucks. If the X.509 certificate is valid, the brokering system can monitor a van’s fuel consumption, speed, mileage, and overall engine condition to maximize each van’s operating efficiency.
AM supports authentication modules and chains and authentication nodes and trees to implement authentication.
|
Authentication nodes and trees are replacing authentication modules and chains. We recommend that you implement nodes and trees when possible. |
AM creates an authentication session to track the user’s authentication progress through an authentication chain or tree. Once the user has authenticated, AM creates a session to manage the user’s access to resources. To learn more about sessions, see Sessions.
Multi-factor authentication
Multi-factor authentication (MFA) is an authentication technique that requires users to provide multiple forms of identification when logging in to AM.
Multi-factor authentication provides a more secure method for users to access their accounts with the help of a device. Note that the word device is used in this section to mean a piece of equipment that can display a one-time password or that supports push notifications using protocols supported by AM multi-factor authentication. Devices are most commonly mobile phones with authenticator apps that support the OATH protocol or push notifications, but could also include other equipment.
The following is an example scenario of multi-factor authentication in AM:
-
An AM administrator configures an authentication tree to capture the user’s username and password and to create one-time passwords.
-
An end user authenticates to AM using that authentication tree.
-
AM prompts the user to enter the username and password—the first factor in multi-factor authentication.
-
If the user ID and password were correct, AM sends the user an email with a one-time password.
-
The user provides the one-time password to AM to successfully complete authentication—the second factor in multi-factor authentication.
AM supports the following multi-factor authentication protocols:
-
MFA: Open Authentication (OATH) to enable one-time password authentication.
-
MFA: Push authentication to receive push notifications in a device as part of the authentication process.
-
MFA: Web authentication (WebAuthn) to enable authentication using an authenticator device, such as a fingerprint scanner.
Configure AM for authentication
AM provides the following features to authenticate users:
- Authentication nodes and trees
-
AM provides a large variety of authentication nodes, and lets you develop custom nodes, based on your authentication requirements. You connect these nodes to create a tree that guides users through the authentication process.
- Authentication modules and chains
-
AM provides a number of authentication modules to handle different methods of authenticating users. The modules can be chained together to provide multiple authentication mechanisms. A user’s credentials must be evaluated by one module before control passes to the next module in the chain.
|
Authentication nodes and trees are replacing authentication modules and chains. If your deployment uses modules and chains, you should consider moving to nodes and trees when possible. |
The authentication process is extremely flexible, and can be adapted to suit your specific deployment. Although the number of choices can seem daunting, once you understand the basic process, you will be able to configure an authentication path to protect access to most applications in your organization.
Authentication is configured per realm. When a new realm is created, it inherits the authentication configuration of the parent realm. This can save time, especially if you are configuring several subrealms.
The following table summarizes the high-level tasks required to configure authentication in a realm:
| Task | Resources |
|---|---|
Configure the required authentication mechanisms You need to decide how your users are going to log in. For example, you may require your users to provide multiple credentials, or to log in using third-party identity providers, such as Facebook or Google. |
|
Configure the realm defaults for authentication Authentication chains and trees use several defaults that are configured at realm level. Review and configure them to suit your environment. |
|
Configure the success and failure URLs for the realm By default, AM redirects users to the UI after successful authentication. No failure URL is defined by default. |
|
Configure an identity store in your realm. The identity store you configure in the realm should contain those users that would log in to the realm. |
Authentication nodes and trees
Authentication trees (also referred to as Intelligent Authentication) provide fine-grained authentication by allowing multiple paths and decision points throughout the authentication flow. Use them to build complex authorization scenarios, while offering users a streamlined sign-on experience.
Authentication trees are made up of authentication nodes, which define actions taken during authentication. Each node performs a single task during authentication, such as, collecting a username or making a simple decision based on a cookie.
Nodes can have multiple outcomes rather than just success or failure. This allows you to create complex yet customer-friendly authentication experiences by linking nodes together, creating loops, branching the tree for different authentication scenarios, and nesting nodes within a tree:
To further control the authentication process, you can assign authentication levels to branches on a tree, with higher levels being used typically to allow access to more restricted resources.
Authentication trees differ in the following ways from traditional authentication chains:
-
Authentication trees can’t mix with authentication chains. Each authentication to AM can use either a tree or a chain, but not both together.
-
The functionality derived from post-authentication plugins, used traditionally with authentication chains, is handled differently when using trees. For example:
-
Session property management is handled by individual nodes. Learn more in Set Session Properties node.
-
Calling out to third-party systems is handled by scripted nodes. Learn more in Scripted Decision node.
-
Registering events to make HTTP POST calls to a server is handled by webhooks. Learn more in Configure authentication webhooks. Post-authentication plugins don’t get triggered when authenticating to a tree, only to a chain.
-
Authentication levels for trees
When a user successfully authenticates, AM creates a session, which allows AM to manage the user’s access to resources. The session is assigned an authentication level. The authentication level is often used as a measure of the strength of the authentication performed. For example, username and password could be assigned a low authentication level, and multi-factor with Push and webAuthn could be assigned a high one.
Authorization policies could require a particular authentication level to access protected resources. When an authenticated user tries to access a protected resource without satisfying the authentication level requirement, AM denies access to the resource and returns an advice indicating that the user needs to reauthenticate at the required authentication level to access the resource.
The web or Java agent or policy enforcement point can then send the user back to AM for session upgrade. Learn more in Session upgrade
AM provides the following nodes to manage authentication levels:
-
The
Authentication Level Decisionnode, which checks if the current authentication level is equal or greater than the one specified in the node. -
The
Modify Authentication Levelnode, which can raise or lower the authentication level.
Position these nodes to alter the authentication level depending on the route taken through the authentication tree.
Account lockout for trees
Use account lockout to limit the number of times an end user can attempt to authenticate with invalid credentials before rendering their account inactive. Limiting the number of attempts helps to prevent password-guessing and brute-force attacks.
By default, authentication trees support account lockout and provide nodes for checking and changing a user’s status:
- Account Active Decision node
-
Use this node to determine whether an account is locked or unlocked.
-
An account is considered locked under these conditions:
-
The status is
inactive. -
The status is
activeand a duration lockout is set on the account.
-
-
An account is considered unlocked under this condition:
-
The status is
activeand no duration lockout is set on the account.
-
-
- Account Lockout node
-
Use this node to change the account’s status to inactive or active.
When setting an account to inactive, the node doesn’t consider the realm’s account lockout settings, so effectively sets a persistent lockout on the account.
When setting an account to active, the node also resets the failed attempts and lockout duration counters.
In addition to the lockout-specific nodes above, the Success and Failure nodes include account lockout functionality, when lockout is enabled in a realm, as follows:
- Success node
-
-
Checks the User Status property of the user profile, when reached, and fails the authentication with an error message, if the account is marked as
Inactive:
The error message is returned in the JSON response if authenticating to the tree by using REST:
{ "code":401, "reason":"Unauthorized", "message":"User Locked Out." }json -
Resets the failure count in the user profile, when reached, if the User Status property is set to
Active.
-
- Failure node
-
-
Checks the invalid attempts property of the user profile, and returns a warning message if the number of failed attempts is equal to or greater than the configured Warn User After N Failures value in the realm:
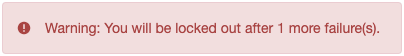
The error message is returned in the JSON response if authenticating to the tree by using REST:
{ "code":401, "reason":"Unauthorized", "message":"Warning: You will be locked out after 1 more failure(s)." }json -
Increments the failure count in the user profile, when reached.
-
Returns an error message if the account is marked as
Inactive:
The error message is returned in the JSON response if authenticating to the tree by using REST:
{ "code":401, "reason":"Unauthorized", "message":"User Locked Out." }json
-
You can find information on configuring account lockout in a realm in Account lockout.
Specify IDM identity resources in trees
When running AM as part of an integrated platform with IDM,
trees configured to use the platform need to identify
the type of identity resource or object the tree is working with.
To do this, use the identityResource configuration property.
If the property isn’t included in the tree configuration, it defaults to managed/user.
To update identityResource on a tree, use the REST API to update the tree:
$ curl \
--request PUT \
--header "iPlanetDirectoryPro: AQIC5wM…TU3OQ*" \
--header "Content-Type: application/json" \
--header "Accept-API-Version: protocol=2.1,resource=1.0" \
--header "If-None-Match: *" \
--data '{
"entryNodeId":"e301438c-0bd0-429c-ab0c-66126501069a",
"nodes":{},
"staticNodes":{},
"description":"Example tree description",
"identityResource":"managed/newObjectType"
}' \
"https://openam.example.com:8443/openam/json/realms/root/realm-config/authentication/authenticationtrees/trees/ExampleTree"In the previous example, the tree ExampleTree has no nodes added to it yet.
It includes the identityResource property, set to use a managed object in IDM called newObjectType.
Because this is a PUT request, you must include the entire tree as part of the request.
You can find more information about using the REST API in REST in AM.
Configure authentication trees
The following table summarizes the high-level tasks required to configure authentication trees:
| Task | Resources | ||
|---|---|---|---|
Design your user authentication journey Authentication trees are flexible. For example, the same tree can branch for different use cases, or users can be forced to loop though branches until they’re able to present the required credentials. It’s easy to create a massive tree that’s difficult to understand, read, and maintain in the UI. For this reason, AM lets you nest trees within trees. The best way to tackle the design decision is to write down a list of required steps users would need to take to sign on to your environment. Then, check the list of nodes available in AM.
|
|
||
Decide if you need custom authentication nodes and webhooks If the nodes available in AM or in the Marketplace don’t meet your needs, you can build your own nodes. In the same way, you can create custom webhooks for nodes that need them. |
|||
Configure your authentication trees Use the authentication tree designer to put together your trees quickly. |
|||
Configure webhooks, if required If you have configured the |
Create an authentication tree in the UI
-
In the AM admin UI, go to Realms > Realm Name > Authentication > Trees and click Create Tree.
-
Enter a tree name, for example
myAuthTree, and click Create.The authentication tree designer displays with the Start entry point connected to the Failure exit point.
The authentication tree designer provides the following features on the toolbar:
Authentication tree designer toolbar Button Usage 
Lay out and align nodes according to the order they’re connected.

Toggle the designer window between normal and full screen layout.

Remove the selected node. You can’t delete the Start entry point.
-
Add a node to the tree by dragging the node from the Components panel on the left-hand side, and dropping it into the designer area.
The list of authentication nodes is divided into categories. Click the category title to expand and collapse the categories.
Use the filter text field to restrict the list of authentication nodes. This will match on the node’s name and any tags applied to the node:
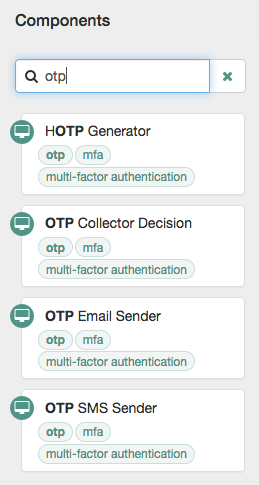
-
Configure the node properties by using the right-hand panel.
You can find more information on the available properties for each node in Authentication nodes configuration reference.
-
Connect the node to the tree as follows:
-
Select and drag the output connector from an existing node and drop it onto the new node.
-
Select and drag the output connector from the new node and drop it onto an existing node.
Nodes have one or more connectors, displayed as dots on the node. Unconnected connectors appear red until you connect them to other nodes in the tree.
Input connectors appear on the left of the node, output connectors appear on the right. A line is drawn between the connectors of connected nodes, and the connectors no longer appear red.
-
-
To change a connection, select and drag the green connector in the connection and drop it onto the new location.
-
Continue adding, connecting and removing nodes until the tree is complete, then click Save.
-
Test your authentication tree by navigating to a URL similar to the following:
https://openam.example.com:8443/openam/XUI/?realm=/alpha&service=myAuthTree#login
Create an authentication tree over REST
To create an authentication tree over REST, send individual PUT requests to create each node. Then send a PUT request to update the tree configuration, including the tree ID and all the nodes in the tree. You can find information on the required parameters in the online REST API reference.
Consider the following when creating authentication trees using the REST API:
-
You must re-create each node when creating a new authentication tree.
-
Each node must have a valid UUID as its identifier. You can generate UUIDs online, for example, using the Online UUID Generator.
If you don’t use a valid UUID, authentication will fail with the following error:
ERROR: Could not get SMS service: authenticationTreesService java.lang.IllegalArgumentException: Invalid UUID string: 12345
-
The
entryNodeIdfield specified when creating the authentication tree is the UUID of the first node in the tree. -
The
outcomefield specified when creating the authentication tree is the UUID of the next node. This allows you to move between nodes. -
The Success and Failure nodes have the following static UUIDs:
-
Success node:
70e691a5-1e33-4ac3-a356-e7b6d60d92e0 -
Failure node:
e301438c-0bd0-429c-ab0c-66126501069a
These UUIDs remain constant across all authentication trees and AM versions.
-
Example
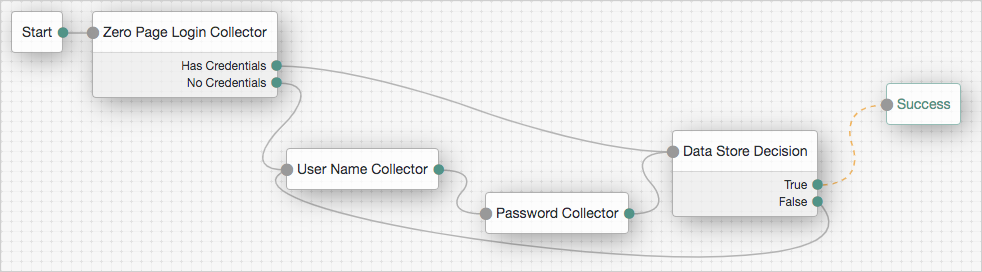
Complete these steps to create a simple authentication tree consisting of three nodes: Username Collector node, Password Collector node, and Data Store Decision node.
-
Generate UUIDs for each of the nodes you want to create. This example uses the following UUIDs:
-
Username Collector node:
8f9d2280-caa7-433f-93a9-1f64f4cae60a -
Password Collector node:
54f14341-d1b7-436f-b159-d1f9b6c626eb -
Data Store Decision node:
3fc7ce22-fc79-4131-85f2-f1844709d042
-
-
Authenticate to AM as the
amAdminuser:$ curl \ --request POST \ --header "Content-Type: application/json" \ --header "X-OpenAM-Username: amadmin" \ --header "X-OpenAM-Password: password" \ --header "Accept-API-Version: resource=2.0, protocol=1.0" \ 'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/authenticate' { "tokenId":"AQIC5wM…TU3OQ*", "successUrl":"/am/console", "realm":"/alpha" }bash -
Create the Username Collector node, where the UUID is the one you generated in step 1:
$ curl \ --request PUT \ --header "iPlanetDirectoryPro: AQIC5wM…TU3OQ*" \ --header "Content-Type: application/json" \ --header "Accept-API-Version: protocol=2.1,resource=1.0" \ --header "If-None-Match: *" \ --data '{ "_id": "8f9d2280-caa7-433f-93a9-1f64f4cae60a", "_type": { "_id": "UsernameCollectorNode", "name": "Username Collector" } }' \ "https://openam.example.com:8443/openam/json/realms/root/realms/alpha/realm-config/authentication/authenticationtrees/nodes/UsernameCollectorNode/8f9d2280-caa7-433f-93a9-1f64f4cae60a" { "_id": "8f9d2280-caa7-433f-93a9-1f64f4cae60a", "_rev": "280717409", "_type": { "_id": "UsernameCollectorNode", "name": "Username Collector", "collection": true }, "_outcomes": [ { "id": "outcome", "displayName": "Outcome" } ] }bash -
Create the Password Collector node, where the UUID is the one you generated in step 1:
$ curl \ --request PUT \ --header "iPlanetDirectoryPro: AQIC5wM…TU3OQ*" \ --header "Content-Type: application/json" \ --header "Accept-API-Version: protocol=2.1,resource=1.0" \ --header "If-None-Match: *" \ --data '{ "_id": "54f14341-d1b7-436f-b159-d1f9b6c626eb", "_type": { "_id": "PasswordCollectorNode", "name": "Password Collector" } }' \ "https://openam.example.com:8443/openam/json/realms/root/realms/alpha/realm-config/authentication/authenticationtrees/nodes/PasswordCollectorNode/54f14341-d1b7-436f-b159-d1f9b6c626eb" { "_id": "54f14341-d1b7-436f-b159-d1f9b6c626eb", "_rev": "792175357", "_type": { "_id": "PasswordCollectorNode", "name": "Password Collector", "collection": true }, "_outcomes": [ { "id": "outcome", "displayName": "Outcome" } ] }bash -
Create the Data Store Decision node, where the UUID is the one you generated in step 1:
$ curl \ --request PUT \ --header "iPlanetDirectoryPro: AQIC5wM…TU3OQ*" \ --header "Content-Type: application/json" \ --header "Accept-API-Version: protocol=2.1,resource=1.0" \ --header "If-None-Match: *" \ --data '{ "_id": "3fc7ce22-fc79-4131-85f2-f1844709d042", "_type": { "_id": "DataStoreDecisionNode", "name": "Data Store Decision" } }' \ "https://openam.example.com:8443/openam/json/realms/root/realms/alpha/realm-config/authentication/authenticationtrees/nodes/DataStoreDecisionNode/3fc7ce22-fc79-4131-85f2-f1844709d042" { "_id": "3fc7ce22-fc79-4131-85f2-f1844709d042", "_rev": "2145625368", "_type": { "_id": "DataStoreDecisionNode", "name": "Data Store Decision", "collection": true }, "_outcomes": [ { "id": "true", "displayName": "True" }, { "id": "false", "displayName": "False" } ] }bash -
Create the authentication tree with these three nodes, where the UUIDs are the ones you used to create the nodes. Make sure you set
entryNodeIdto the UUID of the first node and set theoutcomeof each node to the UUID of the next node:$ curl \ --request PUT \ --header "iPlanetDirectoryPro: AQIC5wM…TU3OQ*" \ --header "Content-Type: application/json" \ --header "Accept-API-Version: protocol=2.1,resource=1.0" \ --header "If-None-Match: *" \ --data '{ "entryNodeId": "8f9d2280-caa7-433f-93a9-1f64f4cae60a", "nodes": { "8f9d2280-caa7-433f-93a9-1f64f4cae60a": { "displayName": "Username Collector", "nodeType": "UsernameCollectorNode", "connections": { "outcome": "54f14341-d1b7-436f-b159-d1f9b6c626eb" } }, "54f14341-d1b7-436f-b159-d1f9b6c626eb": { "displayName": "Password Collector", "nodeType": "PasswordCollectorNode", "connections": { "outcome": "3fc7ce22-fc79-4131-85f2-f1844709d042" } }, "3fc7ce22-fc79-4131-85f2-f1844709d042": { "displayName": "Data Store Decision", "nodeType": "DataStoreDecisionNode", "connections": { "false": "e301438c-0bd0-429c-ab0c-66126501069a", "true": "70e691a5-1e33-4ac3-a356-e7b6d60d92e0" } } } }' \ "https://openam.example.com:8443/openam/json/realms/root/realms/alpha/realm-config/authentication/authenticationtrees/trees/myNewTree" { "_id": "myNewTree", "_rev": "2061817222", "uiConfig": {}, "entryNodeId": "8f9d2280-caa7-433f-93a9-1f64f4cae60a", "innerTreeOnly": false, "nodes": { "8f9d2280-caa7-433f-93a9-1f64f4cae60a": { "displayName": "Username Collector", "nodeType": "UsernameCollectorNode", "connections": { "outcome": "54f14341-d1b7-436f-b159-d1f9b6c626eb" } }, "54f14341-d1b7-436f-b159-d1f9b6c626eb": { "displayName": "Password Collector", "nodeType": "PasswordCollectorNode", "connections": { "outcome": "3fc7ce22-fc79-4131-85f2-f1844709d042" } }, "3fc7ce22-fc79-4131-85f2-f1844709d042": { "displayName": "Data Store Decision", "nodeType": "DataStoreDecisionNode", "connections": { "false": "e301438c-0bd0-429c-ab0c-66126501069a", "true": "70e691a5-1e33-4ac3-a356-e7b6d60d92e0" } } }, "enabled": true }bash -
Verify the tree has been created in the AM admin UI. It should look similar to this:
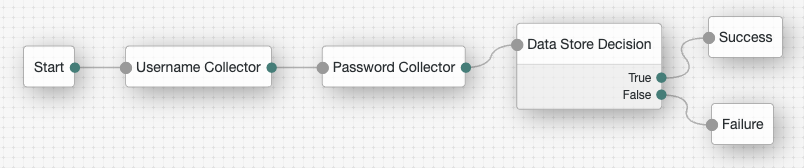
Enable and disable an authentication tree
Custom authentication trees are enabled by default when you save them. For security purposes, you can disable custom authentication trees during development and testing to prevent accidentally allowing access through these trees. Rather than having unused authentication trees enabled, you should disable the default authentication trees until you need them.
When a user attempts to authenticate through a disabled tree, AM returns a No configuration found error.
To enable or disable an authentication tree, send a PUT request to update the tree configuration. Include the tree ID
and all the nodes in the tree, and set the enabled property.
You can find information on the required parameters in the
online REST API reference.
Example
$ curl \
--request PUT \
--header "iPlanetDirectoryPro: AQIC5wM…TU3OQ*" \
--header "Content-Type: application/json" \
--header "Accept-API-Version: protocol=2.1,resource=1.0" \
--header "If-None-Match: *" \
--data '{
"entryNodeId": "c11e9cf8-ef48-4740-876f-6300e2f46aef",
"nodes": {
"c11e9cf8-ef48-4740-876f-6300e2f46aef": {
"displayName": "Page Node",
"nodeType": "PageNode",
"x": 147,
"y": 25,
"connections": {
"outcome": "15839e1c-5085-4f58-bc94-c4cc848a0ae8"
}
},
"15839e1c-5085-4f58-bc94-c4cc848a0ae8": {
"displayName": "Data Store Decision",
"nodeType": "DataStoreDecisionNode",
"x": 349,
"y": 25,
"connections": {
"true": "70e691a5-1e33-4ac3-a356-e7b6d60d92e0",
"false": "e301438c-0bd0-429c-ab0c-66126501069a"
}
}
},
"enabled": false
}' \
"https://openam.example.com:8443/openam/json/realms/root/realms/alpha/realm-config/authentication/authenticationtrees/trees/myAuthTree"
{
"_id": "myAuthTree",
"_rev": "2070284866",
"uiConfig": {},
"entryNodeId": "c11e9cf8-ef48-4740-876f-6300e2f46aef",
"nodes": {
"c11e9cf8-ef48-4740-876f-6300e2f46aef": {
"displayName": "Page Node",
"nodeType": "PageNode",
"x": 147,
"y": 25,
"connections": {
"outcome": "15839e1c-5085-4f58-bc94-c4cc848a0ae8"
}
},
"15839e1c-5085-4f58-bc94-c4cc848a0ae8": {
"displayName": "Data Store Decision",
"nodeType": "DataStoreDecisionNode",
"x": 349,
"y": 25,
"connections": {
"true": "70e691a5-1e33-4ac3-a356-e7b6d60d92e0",
"false": "e301438c-0bd0-429c-ab0c-66126501069a"
}
}
},
"staticNodes": {
"startNode": {
"x": 50,
"y": 25
},
"70e691a5-1e33-4ac3-a356-e7b6d60d92e0": {
"x": 570,
"y": 30
},
"e301438c-0bd0-429c-ab0c-66126501069a": {
"x": 573,
"y": 107
}
},
"innerTreeOnly": false,
"enabled": false
}Disable direct access through an inner tree
An inner tree or child tree lets you nest authentication logic. There is no limit to the depth of nesting.
You configure an inner tree like any other tree then call it from a parent tree using an Inner Tree Evaluator node.
You could want to hide inner trees as complete services. In other words, you could want to prevent users from authenticating directly through an inner tree, either for security reasons or because the inner tree is insufficient as a complete authentication service.
To prevent a tree from being used outside of its parent tree, set the innerTreeOnly property to true in the tree
configuration. Send a PUT request to update the tree configuration, including the tree ID and all the nodes in the tree.
You can find information on the required parameters in the
online REST API reference.
Example
$ curl \
--request PUT \
--header "iPlanetDirectoryPro: AQIC5wM…TU3OQ*" \
--header "Content-Type: application/json" \
--header "Accept-API-Version: protocol=2.1,resource=1.0" \
--header "If-None-Match: *" \
--data '{
"entryNodeId": "c11e9cf8-ef48-4740-876f-6300e2f46aef",
"nodes": {
"c11e9cf8-ef48-4740-876f-6300e2f46aef": {
"displayName": "Page Node",
"nodeType": "PageNode",
"x": 147,
"y": 25,
"connections": {
"outcome": "15839e1c-5085-4f58-bc94-c4cc848a0ae8"
}
},
"15839e1c-5085-4f58-bc94-c4cc848a0ae8": {
"displayName": "Data Store Decision",
"nodeType": "DataStoreDecisionNode",
"x": 349,
"y": 25,
"connections": {
"true": "70e691a5-1e33-4ac3-a356-e7b6d60d92e0",
"false": "e301438c-0bd0-429c-ab0c-66126501069a"
}
}
},
"innerTreeOnly": true
}' \
"https://openam.example.com:8443/openam/json/realms/root/realms/alpha/realm-config/authentication/authenticationtrees/trees/myAuthTree"
{
"_id": "myAuthTree",
"_rev": "1081620278",
"uiConfig": {},
"entryNodeId": "c11e9cf8-ef48-4740-876f-6300e2f46aef",
"innerTreeOnly": true,
"nodes": {
"c11e9cf8-ef48-4740-876f-6300e2f46aef": {
"displayName": "Page Node",
"nodeType": "PageNode",
"x": 147,
"y": 25,
"connections": {
"outcome": "15839e1c-5085-4f58-bc94-c4cc848a0ae8"
}
},
"15839e1c-5085-4f58-bc94-c4cc848a0ae8": {
"displayName": "Data Store Decision",
"nodeType": "DataStoreDecisionNode",
"x": 349,
"y": 25,
"connections": {
"true": "70e691a5-1e33-4ac3-a356-e7b6d60d92e0",
"false": "e301438c-0bd0-429c-ab0c-66126501069a"
}
}
},
"staticNodes": {
"startNode": {
"x": 50,
"y": 25
},
"70e691a5-1e33-4ac3-a356-e7b6d60d92e0": {
"x": 570,
"y": 30
},
"e301438c-0bd0-429c-ab0c-66126501069a": {
"x": 573,
"y": 107
}
},
"enabled": true
}Configure authentication webhooks
Webhooks are used to send HTTP POST calls to a server with contextual information about an authentication session when a predefined event occurs, for example, logging out.
Webhooks are used from within authentication trees by the Register Logout Webhook node.
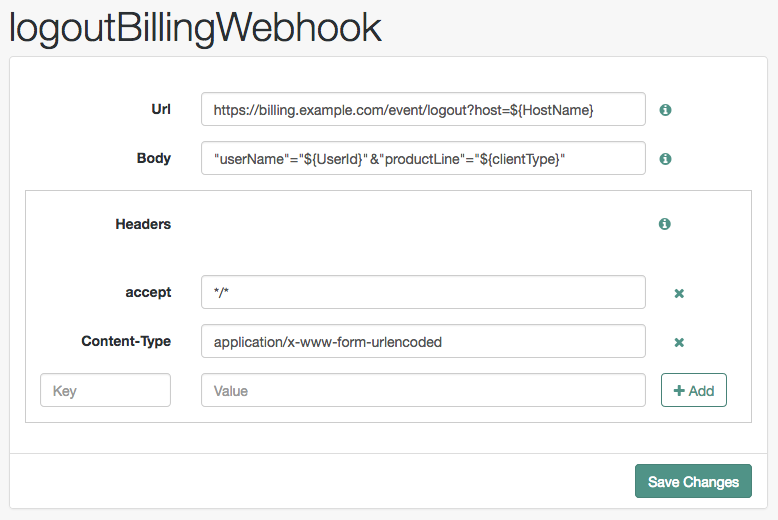
Create a webhook
-
In the AM admin UI, go to Realms > Realm Name > Authentication > Webhooks.
-
To create a new webhook, select Create Webhook, specify a webhook name, and click Create.
-
To edit an existing webhook, select the name of the webhook.
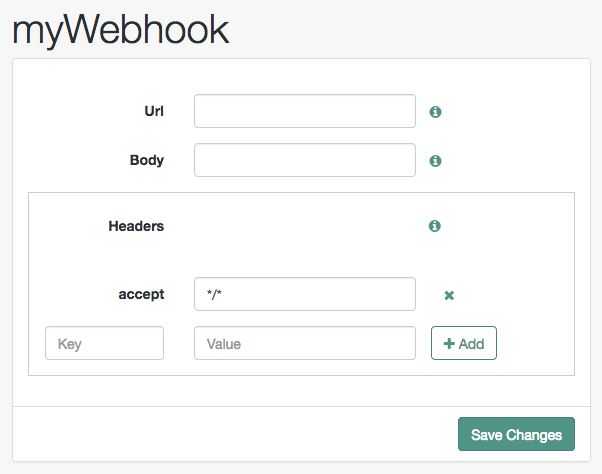
-
-
Complete the fields as required:
- Url
-
Specifies the URL to which the HTTP POST is sent when the event occurs.
- Body
-
Specifies the body of the HTTP POST. You can send different formats by also setting the correct Content-Type header in the
Headerproperty, for example:-
Form Data. Enter the body value in the format
parameter=value¶meter2=value2, and set aContent-Typeheader ofapplication/x-www-form-urlencoded. -
JSON Data. Enter the body value in the format
{"parameter":"value","parameter2":"value2"}, and set aContent-Typeheader ofapplication/json.
-
- Headers
-
Specifies any HTTP headers to add to the POST.
To add a header, enter the name of the header in the
Keyfield, and the value, and click Add (➕).To remove a header, click Delete (✖).
The fields in a webhook support variables for retrieving values from the user’s session after successfully authenticating.
Specify a variable in the following format:
${variable_name}To access the type of webhook event, use the
WebhookEventTypeparameter key to return one of the following possible values:-
LOGOUT -
UPGRADE -
DESTROY -
MAX_TIMEOUT -
IDLE_TIMEOUT
For example, to retrieve the event type as a query parameter:
&event=${WebhookEventType}You can use a variable to access custom properties added to the session with the Set Session Properties node as well as the following default session properties:
Default Session Properties
Property Example value Description AMCtxId22e73c81-708e-4849-b064-db29b68ef943-105372
The audit ID for the session. This is logged as the
trackingIdsfield in AM access audit logs.amlbcookie01
The cookie that identifies the AM server that generated the session. For environments with multiple AM servers, this can be used for load balancer stickiness.
authInstant2022-02-28T14:06:31Z
The exact time that authentication completed.
AuthLevel5
The authentication level of the session, determined by the login mechanism used to create the session. For example, a tree can have an authentication level of 10.
Step-up authentication is triggered if an authentication level specified by an agent or policy that is designed to protect a resource, is greater than or equal to the value of the
AuthLevelsession property.For more information, see Session upgrade.
AuthTypeDataStore
A pipe-separated list of modules to which the user has authenticated. For example,
module1|module2|module3(authentication chains only).CharSetUTF-8
The character set for the session, set to
UTF-8.clientTypegenericHTML
The type of client, set to
genericHTML.FullLoginURL/openam/XUI/?realm=%2Falpha
The full login URL, including query parameters.
Host192.0.2.1
The originating IP address of the authentication request (authentication trees only).
HostName192.0.2.1
The host name that was used when the session was authenticated.
IndexTypeservice
Based on the value of the
authIndexValuequery parameter during authentication. Typically, this is set toservice.Localeen_US
The session locale.
loginURL/openam/XUI
The base login URL. A subset of
FullLoginURL.OidcSidg0wmSpoAIwH6HAwCnurvRcfYqh4
Unique session ID used by AM to determine whether OIDC ID tokens granted for the same client relate to the same session. This appears when
Enable Session Management(storeOpsToken) is set to true in the OAuth 2.0 provider settings.Organizationo=alpha,ou=services,dc=openam,dc=forgerock,dc=org
The DN of the realm where authentication took place.
Principalid=demo,ou=user,o=alpha,ou=services,dc=openam,dc=forgerock,dc=org
The value of
sun.am.UniversalIdentifier.Principalsdemo
The username of the user. For multiple principals, this can be a pipe-separated list (authentication chains only).
ServiceldapService
The name of the tree or chain that was used to authenticate this session.
successURL/openam/console
The URL that was redirected to, upon a successful login request.
sun.am.UniversalIdentifierid=demo,ou=user,o=alpha,ou=services,dc=openam,dc=forgerock,dc=org
The DN of the user (username is lowercase).
UserIddemo
The
idvalue from thePrincipalproperty.UserProfileRequired
Can be one of:
Required,Create,Ignore, orCreateWithAlias. Based on the value of thedynamicProfileCreationauthentication configuration. Values other thanIgnoreindicates that user profile attributes were mapped based on theUser Attribute Mapping to Session Attributesetting. See authentication configuration for details.Default:
Required.UserTokendemo
The username, as defined in the
Principalsproperty. For authentication chains, this is the last principal value.XUSRef8700f1a5-904e-4849-8b2b-cb25296ef453-291173
If the cross-upgrade session reference property is enabled, this value identifies the session through its lifecycle. This is logged in the
trackingIdsfield in AM audit logs for session creation and upgrade events.
Customize authentication trees
Your deployment might require customizing standard authentication trees.
Learn more in Node development.
Create post-authentication hooks for trees
This section explains how to create a hook used by a node within an authentication tree. These tree hooks can perform custom processing after an authentication tree has successfully completed, and a session has been created.
AM includes the following authentication tree hooks:
CreatePersistentCookieTreeHook-
Used by the Set Persistent Cookie node.
UpdatePersistentCookieTreeHook-
Used by the Persistent Cookie Decision node.
The core class of an authentication tree hook
The following example shows an excerpt from the UpdatePersistentCookieTreehook class.
The Persistent Cookie Decision node uses this tree hook to recreate the persistent cookie.
/**
* A TreeHook for updating a persistent cookie.
*/
@TreeHook.Metadata(configClass = PersistentCookieDecisionNode.Config.class) (1)
public class UpdatePersistentCookieTreeHook implements TreeHook { (2)
...
@Inject (3)
public UpdatePersistentCookieTreeHook(@Assisted Request request, @Assisted Response response,
@Assisted PersistentCookieDecisionNode.Config config, @Assisted Realm realm,
PersistentJwtStringSupplier persistentJwtStringSupplier,
PersistentCookieResponseHandler persistentCookieResponseHandler,
PersistentJwtProvider persistentJwtProvider,
@Named("validSecrets") SecretsRetrievalService validSecretsRetrievalService,
NamedSecretsRetrievalService namedSecretsRetrievalService) {
this.request = request;
this.response = response;
this.config = config;
this.persistentJwtProvider = persistentJwtProvider;
this.persistentJwtStringSupplier = persistentJwtStringSupplier;
this.persistentCookieResponseHandler = persistentCookieResponseHandler;
this.realm = realm;
this.validSecretsRetrievalService = validSecretsRetrievalService;
this.namedSecretsRetrievalService = namedSecretsRetrievalService;
}
@Override
public void accept() throws TreeHookException { (4)
logger.debug("UpdatePersistentCookieTreeHook.accept");
String orgName = PersistentCookieResponseHandler.getOrgName(response);
Cookie originalJwt = getJwtCookie(request, config.persistentCookieName());
if (originalJwt != null) {
...
}
}
...
}| 1 | The @TreeHook.Metadata annotation.
Before defining the core class, use a Java @TreeHook.Metadata annotation
to specify the class the tree hook uses for its configuration.
Use the configClass property to specify the configuration class of the node that will be using the tree hook.
|
||
| 2 | The core class must implement the TreeHook interface.
For more information, refer to the TreeHook interface in the AM Public API Javadoc. |
||
| 3 | AM uses Google’s Guice dependency injection framework for authentication nodes and tree hooks.
Use the @Inject annotation to construct a new instance of the tree hook,
specifying the configuration interface set up earlier and any other required parameters.
For more information, refer to the
Inject annotation type
and the Assisted annotation type
in the Google Guice Javadoc. |
||
| 4 | Implement the public void accept() method to define actions to perform on a successful journey outcome.
Optionally, override the The main logic of a tree hook is handled by these two methods. |
Authentication modules and chains
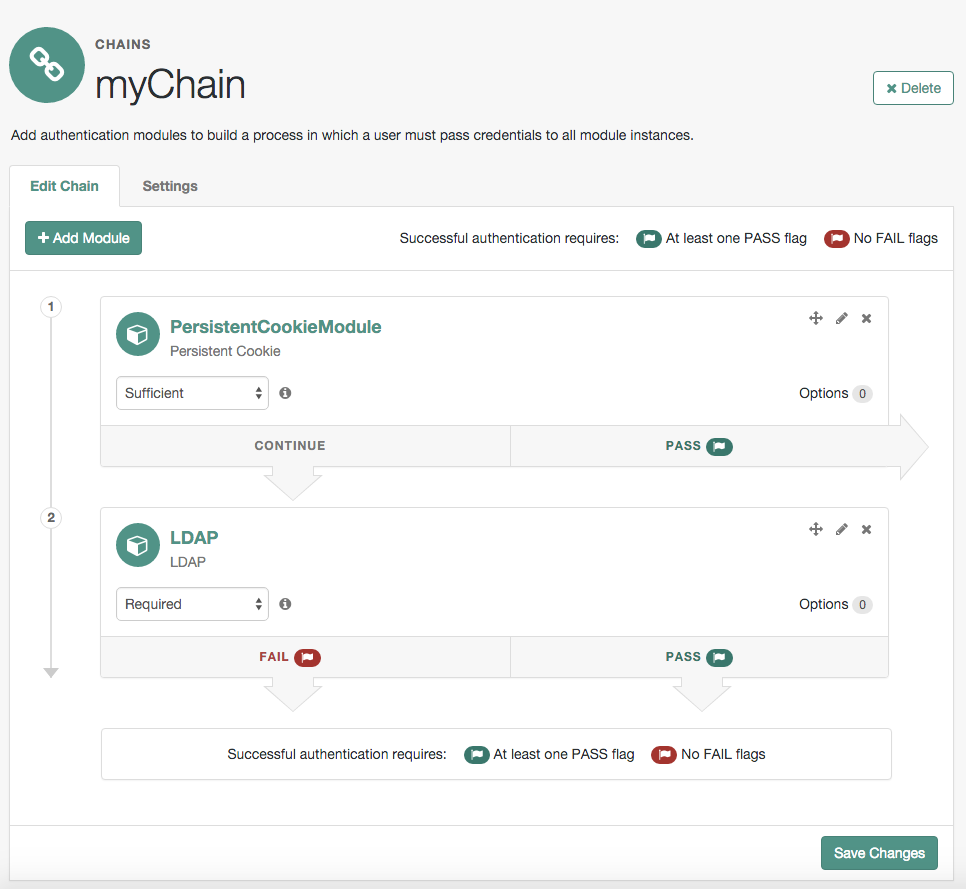
AM uses authentication modules to handle different ways of authenticating. Basically, each authentication module handles one way of obtaining and verifying credentials. You can chain different authentication modules together. In AM, this is called authentication chaining. Each authentication module can be configured to specify the continuation and failure semantics with one of the following four criteria: requisite, sufficient, required, or optional.
Authentication modules in a chain can assign a pass or fail flag to the authorization request. To successfully complete an authentication chain at least one pass flag must have been achieved, and there must be no fail flags.
Flags are assigned when completing a module as shown in the table below:
| Criteria | Fail | Pass | Example |
|---|---|---|---|
Requisite |
Assigns fail flag. 
Exits chain. |
Assigns pass flag. 
Continues chain. |
Active Directory, Data Store, and LDAP authentication modules are often set as requisite because of a subsequent requirement in the chain to identify the user. For example, the Device ID (Match) authentication module needs a user’s ID before it can retrieve information about the user’s devices. |
Sufficient |
Assigns no flag. Continues chain. |
Assigns pass flag. 
Exits chain. |
You could set Windows Desktop SSO as sufficient, so authenticated Windows users are let through, whereas web users must traverse another authentication module, such as one requiring a username and password. One exception is that if you pass a sufficient module after having failed a required module, you will continue through the chain and will not exit at that point. Consider using a requisite module instead of a required module in this situation. |
Required |
Assigns fail flag. 
Continues chain. |
Assigns pass flag. 
Continues chain. |
You could use a required module for login with email and password, so that it can fail through to another module to handle new users who have not yet signed up. |
Optional |
Assigns no flag. Continues chain. |
Assigns pass flag. 
Continues chain. |
You could use an optional module to assign a higher authentication level if it passes. Consider a chain with a requisite Data Store module and an optional Certificate module. Users who only passed the Data Store module could be assigned a lower authentication level than users who passed both the Data Store and Certificate modules. The users with the higher authentication level could be granted access to more highly-secured resources. |
|
In authentication chains with a single module, |
The AM authentication chain editor displays the flags that could be assigned by each module in the chain, and whether execution of the chain continues downwards through the chain or exits out, as shown below:
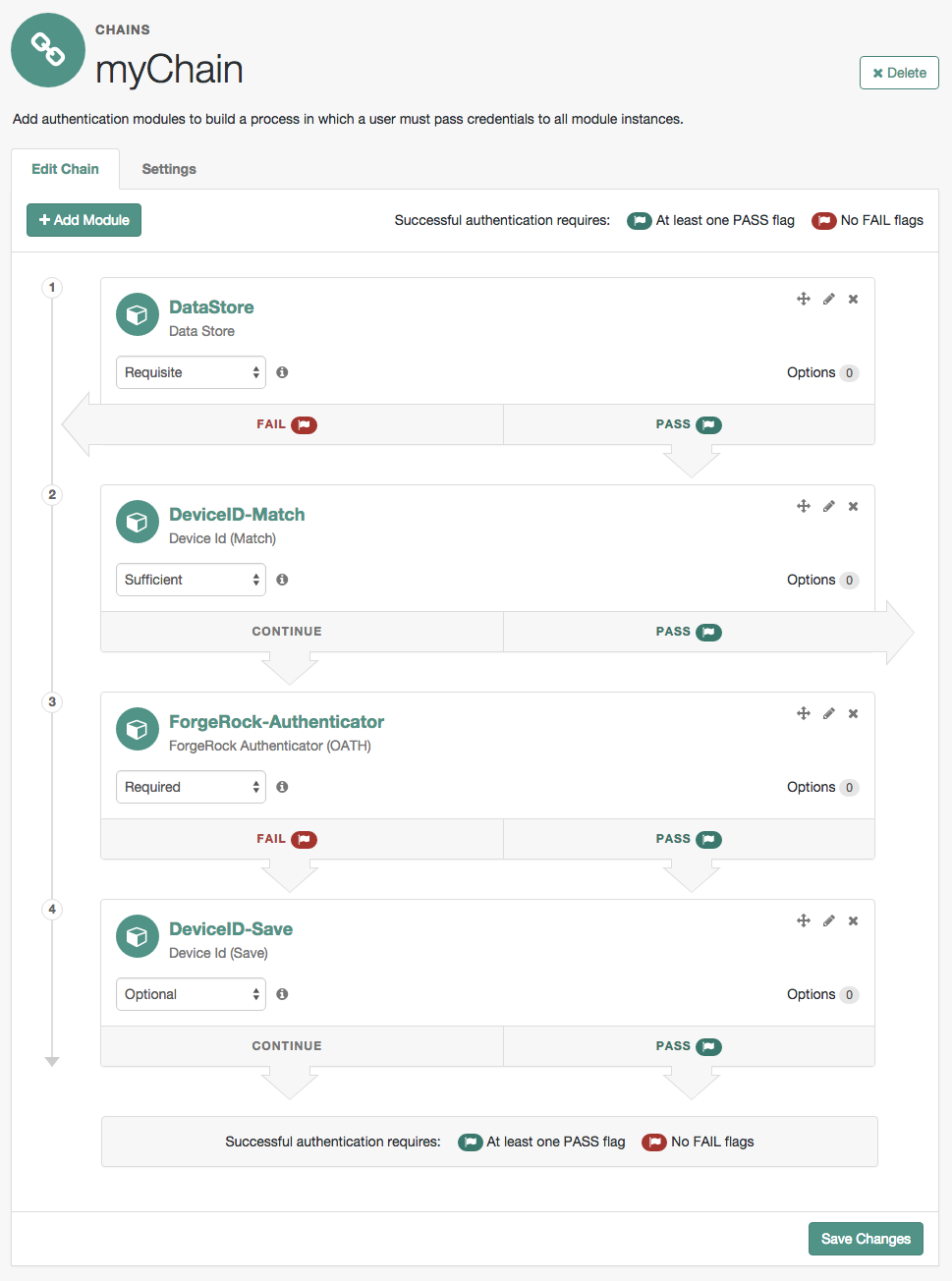
With AM, you can further set authentication levels per module, with higher levels being used typically to allow access to more restricted resources. The AM SPIs also let you develop your own authentication modules, and post-authentication plugins. Client applications can specify the authentication level, module, user, and authentication service to use among those you have configured. As described later in this guide, you can use realms to organize which authentication process applies for different applications or different domains, perhaps managed by different people.
Authentication levels for chains
When a user successfully authenticates, AM creates a session, which allows AM to manage the user’s access to resources. The session is assigned an authentication level, which is calculated to be the highest authentication level of any authentication module that passed. If the user’s session does not have the appropriate authentication level, then the user may need to reauthenticate again at a higher authentication level to access the requested resource.
The authentication level sets the level of security associated with a module. Typically, the strongest form of authentication is assigned the highest authentication level.
If an authentication chain contains requisite or required modules
that were not executed due to the presence of a passing sufficient module in front of them,
the session’s authentication level is calculated to be whichever is greater:
the highest authentication level of any authentication module that passed,
or the highest authentication level of requisite or required modules that were not executed.
You can modify AM’s default behavior, so that a session’s authentication level
is always the highest authentication level of any authentication module that passed,
even if there are requisite or required modules in the authentication chain that were not executed.
To modify the default behavior,
set the org.forgerock.openam.authLevel.excludeRequiredOrRequisite property to true
under Deployment > Servers > Server Name > Advanced and restart the AM server.
Authorization policies may also require a particular authentication level to access protected resources. When an authenticated user tries to access a protected resource without satisfying the authentication level requirement, AM denies access to the resource and returns an advice indicating that the user needs to reauthenticate at the required authentication level to access the resource.
The web or Java agent or policy enforcement point can then send the user back to AM for Session upgrade.
Configure authentication chains
The following table summarizes the high-level tasks required to configure authentication chains:
| Task | Resources | ||
|---|---|---|---|
Design the authentication journey of your users The best way to tackle the design decision is to write down a list of required steps users would need to take to log in to your environment, and then check the list of modules available in AM. |
|
||
Decide if you need custom authentication modules, server-side Scripts, or post-authentication plugins If the default authentication modules and plugins do not suit your needs, consider coding your own. |
|||
Configure authentication modules Before setting up your chains, configure the authentication modules you need. |
|||
Configure authentication chains Use the chain designer to put together your chains quickly. |
|||
Configure post-authentication plugins Post-authentication plugins allow you to manage session properties and run scripts after authentication, or after the user has logged out. |
Configure authentication modules
The AM admin UI provides two places where you can configure authentication modules:
-
Under Configure > Authentication, you configure default properties for global authentication modules.
-
Under Realms > Realm Name > Authentication v Modules, you configure modules for your realm.
To configure the authentication modules required by your environment, refer to the following resources:
For module reference information, see Authentication modules configuration reference.
Create an authentication chain
After you have configured authentication modules and added the modules to the list of module instances, you can configure authentication chains. Authentication chains let you handle cases where alternate modules or credentials are needed. If you need modules in the chain to share user credentials, then set options for the module.
-
In the AM admin UI, go to Realms > Realm Name > Authentication > Chains.
-
On the Authentication Chains page, click Add Chain. Enter a chain name, and click Create.
In the Edit Chain dialog, click Add a Module.
-
Choose the authentication module in the drop-down list, and then assign appropriate criteria (Optional, Required, Requisite, Sufficient).
Add as many modules as required.
-
If you need modules in the chain to share user credentials, consider the following available options:
Options to share credentials among modules
iplanet-am-auth-store-shared-state-enabled-
Set
iplanet-am-auth-store-shared-state-enabled=trueto store the credentials captured by this module in shared state. This enables subsequent modules in the chain to access the credentials captured by this module. The shared state is cleared when the user successfully authenticates, quits the chain, or logs out.Default:
trueOATH and OTP codes are never added to the shared state, and cannot be shared between other modules in the chain. iplanet-am-auth-shared-state-enabled-
Set
iplanet-am-auth-shared-state-enabled=trueto allow this module to access the credentials, such as user name and password, that have been stored in shared state by previous modules in the authentication chain.Default:
false iplanet-am-auth-shared-state-behavior-pattern-
Set
iplanet-am-auth-shared-state-behavior-pattern=tryFirstPassto try authenticating with the username and password stored in shared state. If authentication fails, AM displays the login screen of this module for the user to re-enter their credentials.Set
iplanet-am-auth-shared-state-behavior-pattern=useFirstPassto prevent the user from entering the username and password twice during authentication. Typically, you set the property touseFirstPassfor all modules in the chain except the first module. If authentication fails, then the module fails.Default:
tryFirstPass
Enter the key and its value, and click Plus (+). When you finish entering the options, click OK.
Examples
For example, consider a chain with two modules sharing credentials according to the following settings: the first module in the chain has the option
iplanet-am-auth-store-shared-state-enabled=true, and criteriaREQUIRED.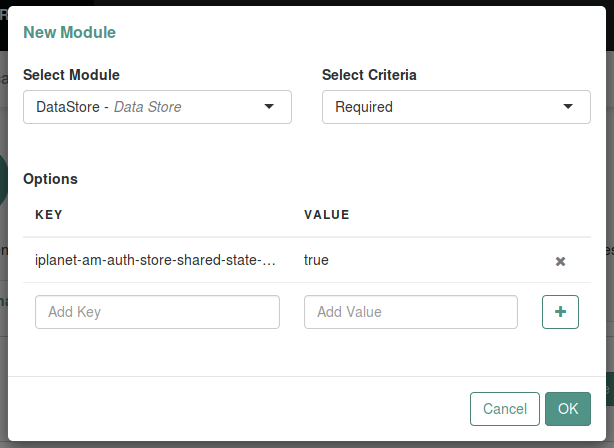 Figure 3. Authentication chain first module
Figure 3. Authentication chain first moduleThe second module in the chain has options
iplanet-am-auth-shared-state-enabled=true,iplanet-am-auth-shared-state-behavior-pattern=useFirstPasswith criteriaREQUIRED.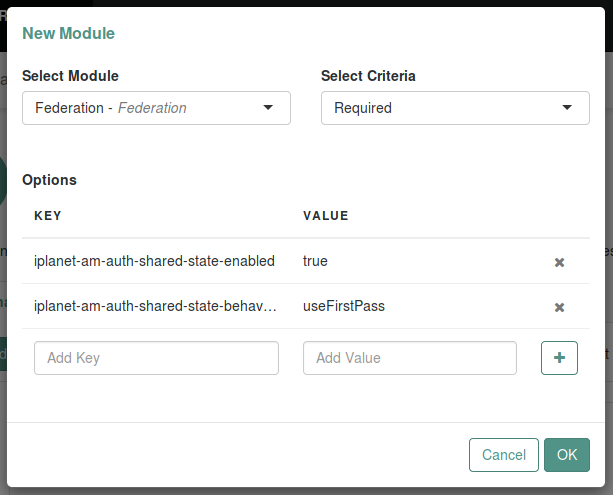 Figure 4. Authentication chain second module
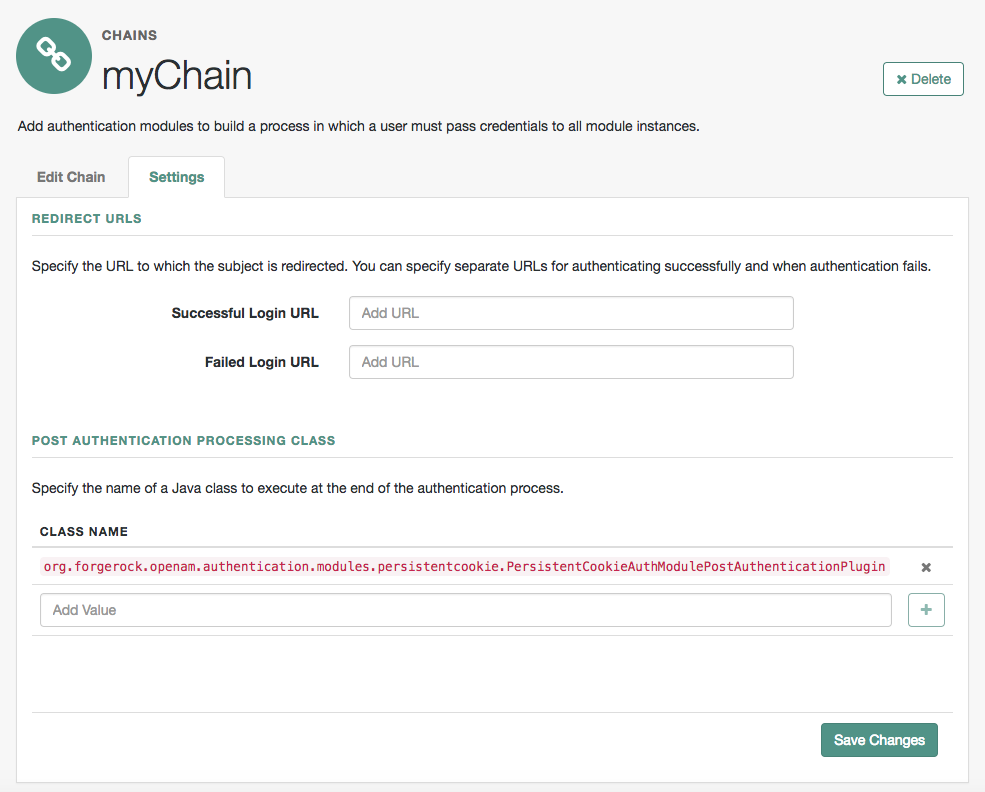
Figure 4. Authentication chain second module -
On the Settings tab, configure where AM redirects the user upon successful and failed authentication, and plug in your post-authentication processing classes as necessary.
If you configure absolute URLs that are not in the same scheme, FQDN, and port as AM, you must also configure the Success and failure redirection URLs.
-
Save your work.
The following authentication sequence would occur: the user enters their credentials for the first module and successfully authenticates. The first module shares the credentials with the second module, successfully authenticating the user without prompting again for their credentials, unless the credentials for the first module do not successfully authenticate the user to the second module.
Login session timeouts for chains
Login pages have a session timeout that specifies the number of minutes before the session times out, if the user has not logged in. The login session timeout has two components:
-
The timeout of the specific authentication module.
The default session timeout for an authentication module is two minutes.
-
The overall session timeout, set in Configure > Server Defaults > Session > Session Limits > Invalidate Session Max Time.
The default overall session timeout is three minutes.
You must set the overall session timeout to a value greater than the complete authentication process (including any multi-page authentication processes). If you have chained authentication modules, with different timeouts, you must set the overall session timeout to a value greater than the sum of these timeouts.
Learn more in How do I configure login page session timeouts in PingAM when using authentication modules? in the Knowledge Base.
Post-authentication plugins
Post-authentication plugins (PAP) let you include custom processing at the end of the authentication process and when users log out of AM.
In the AM admin UI, you add post-authentication plugins to an authentication chain. Go to Realms > Realm Name > Authentication > Chains > Auth Chain Name > Settings > Post Authentication Processing Class > Class Name.
See Create post-authentication plugins for chains for more information about post-authentication plugins.
AM provides some post-authentication plugins as part of the standard product delivery.
- Class name:
org.forgerock.openam.authentication.modules.adaptive.AdaptivePostAuthenticationPlugin -
The adaptive authentication plugin serves to save cookies and profile attributes after successful authentication.
Add it to your authentication chains that use the adaptive authentication module configured to save cookies and profile attributes.
- Class name:
org.forgerock.openam.authentication.modules.common.JaspiAuthLoginModulePostAuthenticationPlugin -
The Java Authentication Service Provider Interface (JASPI) post-authentication plugin initializes the underlying JASPI
ServerAuthmodule.JASPI defines a standard service provider interface (SPI) where developers can write message level authentication agents for Java containers on either the client side or the server side.
- Class name:
org.forgerock.openam.authentication.modules.oauth2.OAuth2PostAuthnPlugin -
The OAuth 2.0 post-authentication plugin builds a global logout URL used by
/oauth2c/OAuthLogout.jspafter successful OAuth 2.0 client authentication. This logs the resource owner out with the OAuth 2.0 provider when logging out of AM.Before using this plugin, configure the OAuth 2.0 authentication module with the correct OAuth 2.0 Provider logout service URL, and set the Logout options to Log out or Prompt. This plugin cannot succeed unless those parameters are correctly set.
Sometimes OAuth 2.0 providers change their endpoints, including their logout URLs. When using a provider like Facebook, Google, or MSN, make sure you are aware when they change their endpoint locations so that you can change your client configuration accordingly.
- Class name:
org.forgerock.openam.authentication.modules.saml2.SAML2PostAuthenticationPlugin -
The SAML v2.0 post-authentication plugin that gets activated for single logout. Supports HTTP-Redirect for logout-sending messages only.
Set the post-authentication processing class for the authentication chain that contains the SAML v2.0 authentication module.
- Class name:
org.forgerock.openam.authentication.modules.persistentcookie.PersistentCookieAuthModule -
The Persistent Cookie Authentication Module provides logic for persistent cookie authentication in AM. It makes use of the JASPI
JwtSessionmodule to create and verify the persistent cookie. - Class name:
com.sun.identity.authentication.spi.ReplayPasswd -
Password replay post-authentication plugin class that uses a DES/ECB/NoPadding encryption algorithm. This class is deprecated in favor of the
com.sun.identity.authentication.spi.JwtReplayPasswordclass. (Only one password replay post-authentication plugin class can be active for a given AM deployment.)The plugin encrypts the password captured by AM during the authentication process and stores it in a session property. PingGateway or a web agent looks up the property, decrypts it, and replays the password into legacy applications.
To configure password replay for AM and PingGateway, refer to Password replay from AM in the PingGateway documentation.
- Class name:
com.sun.identity.authentication.spi.JwtReplayPassword -
Password replay post-authentication plugin class that uses a JWT-based AES A128CBC-HS256 encryption algorithm. (Only one password replay post-authentication plugin class can be active for a given AM deployment.)
The plugin encrypts the password captured by AM during the authentication process and stores it in a session property. PingGateway looks up the property, decrypts it, and replays the password into legacy applications.
Only version 6 or later is supported.
To configure password replay for AM and PingGateway, refer to Password replay from AM in the PingGateway documentation.
If necessary, you can also write your own custom post-authentication plugin as described in Create post-authentication plugins for chains.
Customize authentication chains
Your deployment might require customizing standard authentication chain features.
Create a custom authentication module
This section shows how to customize authentication with a sample custom authentication module. For deployments with particular requirements not met by existing AM authentication modules, determine whether you can adapt one of the built-in or extension modules for your needs. If not, build the functionality into a custom authentication module.
The sample custom authentication module
The sample custom authentication module prompts for a user name and password to authenticate the user, and handles error conditions. The sample shows how you integrate an authentication module into AM such that you can configure the module through the AM admin UI, and also localize the user interface.
Learn about downloading and building PingAM sample source code in the following Knowledge Base article: How do I access and build the sample code provided for PingAM?.
Get a local clone so that you can try the sample on your system.
In the sources, you find the following files
under the /path/to/openam-samples-external/custom-authentication-module directory:
pom.xml-
Apache Maven project file for the module
This file specifies how to build the sample authentication module, and also specifies its dependencies on AM components and on the Java Servlet API.
src/main/java/org/forgerock/openam/examples/SampleAuth.java-
Core class for the sample authentication module
This class is called by AM to initialize the module and to process authentication. See Sample authentication logic for details.
src/main/java/org/forgerock/openam/examples/SampleAuthPrincipal.java-
Class implementing
java.security.Principalinterface that defines how to map credentials to identitiesThis class is used to process authentication. See The Sample Auth Principal for details.
src/main/resources/amAuthSampleAuth.properties-
Properties file mapping UI strings to property values
This file makes it easier to localize the UI. See Sample Auth properties for details.
src/main/resources/amAuthSampleAuth.xml-
Configuration file for the sample authentication service
This file is used when registering the authentication module with AM. See The Sample Auth Service Configuration for details.
src/main/resources/config/auth/default/SampleAuth.xml-
Callback file for deprecated AM classic UI authentication pages
The sample authentication module does not include localized versions of this file. See Sample Auth callbacks for details.
src/main/java/org/forgerock/openam/examples/SampleAuthPlugin.java-
These files serve to register the plugin with AM.
The Java class,
SampleAuthPlugin, implements theorg.forgerock.openam.plugins.AmPlugininterface. In the sample, this class registers theSampleAuthimplementation, and theamAuthSampleAuthservice schema for configuration.The services file,
org.forgerock.openam.plugins.AmPlugin, holds the fully qualified class name of theAmPluginthat registers the custom implementations. In this case,org.forgerock.openam.examples.SampleAuthPlugin.For an explanation of service loading, see the ServiceLoader Javadoc.
Sample Auth properties
AM uses a Java properties file per locale to retrieve the appropriate, localized strings for the authentication module.
The following is the Sample Authentication Module properties file, amAuthSampleAuth.properties.
#
# The contents of this file are subject to the terms of the Common Development and
# Distribution License (the License). You may not use this file except in compliance with the
# License.
#
# You can obtain a copy of the License at legal/CDDLv1.0.txt. See the License for the
# specific language governing permission and limitations under the License.
#
# When distributing Covered Software, include this CDDL Header Notice in each file and include
# the License file at legal/CDDLv1.0.txt. If applicable, add the following below the CDDL
# Header, with the fields enclosed by brackets [] replaced by your own identifying
# information: "Portions copyright [year] [name of copyright owner]".
#
# Copyright 2011-2017 ForgeRock AS. All Rights Reserved
#
sampleauth-service-description=Sample Authentication Module
a500=Authentication Level
a501=Service Specific Attribute
sampleauth-ui-login-header=Login
sampleauth-ui-username-prompt=User Name:
sampleauth-ui-password-prompt=Password:
sampleauth-error-1=Error 1 occurred during the authentication
sampleauth-error-2=Error 2 occurred during the authenticationSample Auth callbacks
AM callbacks XML files are used to build the deprecated classic UI
to prompt the user for identity information needed to process the authentication.
The document type for a callback XML file
is described in WEB-INF/Auth_Module_Properties.dtd where AM is deployed.
The value of the moduleName property in the callbacks file must match your custom authentication module’s class name.
Observe that the module name SampleAuth, shown in the example below,
matches the class name in SampleAuth.java.
<?xml version="1.0" encoding="UTF-8"?>
<!--
* The contents of this file are subject to the terms of the Common Development and
* Distribution License (the License). You may not use this file except in compliance with the
* License.
*
* You can obtain a copy of the License at legal/CDDLv1.0.txt. See the License for the
* specific language governing permission and limitations under the License.
*
* When distributing Covered Software, include this CDDL Header Notice in each file and include
* the License file at legal/CDDLv1.0.txt. If applicable, add the following below the CDDL
* Header, with the fields enclosed by brackets [] replaced by your own identifying
* information: "Portions copyright [year] [name of copyright owner]".
*
* Copyright 2011-2017 ForgeRock AS. All Rights Reserved
*
-->
<!DOCTYPE ModuleProperties PUBLIC
"=//iPlanet//Authentication Module Properties XML Interface 1.0 DTD//EN"
"jar://com/sun/identity/authentication/Auth_Module_Properties.dtd">
<ModuleProperties moduleName="SampleAuth" version="1.0" >
<Callbacks length="0" order="1" timeout="600" header="#NOT SHOWN#" />
<Callbacks length="2" order="2" timeout="600" header="#TO BE SUBSTITUTED#">
<NameCallback isRequired="true">
<Prompt>#USERNAME#</Prompt>
</NameCallback>
<PasswordCallback echoPassword="false" >
<Prompt>#PASSWORD#</Prompt>
</PasswordCallback>
</Callbacks>
<Callbacks length="1" order="3" timeout="600" header="#TO BE SUBSTITUTED#"
error="true" >
<NameCallback>
<Prompt>#THE DUMMY WILL NEVER BE SHOWN#</Prompt>
</NameCallback>
</Callbacks>
</ModuleProperties>This file specifies three states.
-
The initial state (order="1") is used dynamically to replace the dummy strings shown between hashes (for example,
#USERNAME#) by thesubstituteUIStrings()method inSampleAuth.java. -
The next state (order="2") handles prompting the user for authentication information.
-
The last state (order="3") has the attribute
error="true". If the authentication module state machine reaches this order then the authentication has failed. TheNameCallbackis not used and not displayed to user. AM requires that the callbacks array have at least one element. Otherwise AM does not permit header substitution.
Sample authentication logic
An AM authentication module must extend the com.sun.identity.authentication.spi.AMLoginModule abstract class,
and must implement the methods shown below.
|
The account lockout functionality in AM is triggered by counting invalid password exceptions, rather than invalid login exceptions. To trigger account lockouts after repeated failed attempts,
ensure your modules throw |
See the PingAM Java SDK API Specification for reference.
public void init(Subject subject, Map sharedState, Map options)
// OpenAM calls the process() method when the user submits authentication
// information. The process() method determines what happens next:
// success, failure, or the next state specified by the order
// attribute in the callbacks XML file.
public int process(Callback[] callbacks, int state) throws LoginException
// OpenAM expects the getPrincipal() method to return an implementation of
// the java.security.Principal interface.
public Principal getPrincipal()AM does not reuse authentication module instances. This means that you can store information specific to the authentication process in the instance.
The implementation, SampleAuth.java, is shown below:
/*
* The contents of this file are subject to the terms of the Common Development and
* Distribution License (the License). You may not use this file except in compliance with the
* License.
*
* You can obtain a copy of the License at legal/CDDLv1.0.txt. See the License for the
* specific language governing permission and limitations under the License.
*
* When distributing Covered Software, include this CDDL Header Notice in each file and include
* the License file at legal/CDDLv1.0.txt. If applicable, add the following below the CDDL
* Header, with the fields enclosed by brackets [] replaced by your own identifying
* information: "Portions copyright [year] [name of copyright owner]".
*
* Copyright 2011-2023 ForgeRock AS. All Rights Reserved
*/
package org.forgerock.openam.examples;
import java.security.Principal;
import java.util.Map;
import java.util.ResourceBundle;
import java.util.Set;
import javax.security.auth.Subject;
import javax.security.auth.callback.Callback;
import javax.security.auth.callback.NameCallback;
import javax.security.auth.callback.PasswordCallback;
import javax.security.auth.login.LoginException;
import org.slf4j.Logger;
import org.slf4j.LoggerFactory;
import com.sun.identity.authentication.spi.AMLoginModule;
import com.sun.identity.authentication.spi.AuthLoginException;
import com.sun.identity.authentication.spi.InvalidPasswordException;
import com.sun.identity.authentication.util.ISAuthConstants;
import com.sun.identity.shared.datastruct.CollectionHelper;
/**
* SampleAuth authentication module example.
*
* If you create your own module based on this example, you must modify all
* occurrences of "SampleAuth" in addition to changing the name of the class.
*
* Please refer to OpenAM documentation for further information.
*
* Feel free to look at the code for authentication modules delivered with
* OpenAM, as they implement this same API.
*/
public class SampleAuth extends AMLoginModule {
// Name for the debug-log
private final static String DEBUG_NAME = "SampleAuth";
private final static Logger debug = LoggerFactory.getLogger(SampleAuth.class);
// Name of the resource bundle
private final static String amAuthSampleAuth = "amAuthSampleAuth";
// User names for authentication logic
private final static String USERNAME = "demo";
private final static String PASSWORD = "Ch4ng31t";
private final static String ERROR_1_USERNAME = "test1";
private final static String ERROR_2_USERNAME = "test2";
// Orders defined in the callbacks file
private final static int STATE_BEGIN = 1;
private final static int STATE_AUTH = 2;
private final static int STATE_ERROR = 3;
// Errors properties
private final static String SAMPLE_AUTH_ERROR_1 = "sampleauth-error-1";
private final static String SAMPLE_AUTH_ERROR_2 = "sampleauth-error-2";
private Map<String, Set<String>> options;
private ResourceBundle bundle;
private Map<String, String> sharedState;
public SampleAuth() {
super();
}
/**
* This method stores service attributes and localized properties for later
* use.
* @param subject
* @param sharedState
* @param options
*/
@Override
public void init(Subject subject, Map sharedState, Map options) {
debug.debug("SampleAuth::init");
this.options = options;
this.sharedState = sharedState;
this.bundle = amCache.getResBundle(amAuthSampleAuth, getLoginLocale());
}
@Override
public int process(Callback[] callbacks, int state) throws LoginException {
debug.debug("SampleAuth::process state: {}", state);
switch (state) {
case STATE_BEGIN:
// Intialize Callback list if used in chain with
// iplanet-am-auth-shared-state-enabled=true
setForceCallbacksRead(true);
forceCallbacksInit();
// No time wasted here - simply modify the UI and
// proceed to next state
substituteUIStrings();
return STATE_AUTH;
case STATE_AUTH:
// Get data from callbacks. Refer to callbacks XML file.
NameCallback nc = (NameCallback) callbacks[0];
PasswordCallback pc = (PasswordCallback) callbacks[1];
String username = nc.getName();
String password = String.valueOf(pc.getPassword());
//First errorstring is stored in "sampleauth-error-1" property.
if (ERROR_1_USERNAME.equals(username)) {
setErrorText(SAMPLE_AUTH_ERROR_1);
return STATE_ERROR;
}
//Second errorstring is stored in "sampleauth-error-2" property.
if (ERROR_2_USERNAME.equals(username)) {
setErrorText(SAMPLE_AUTH_ERROR_2);
return STATE_ERROR;
}
if (USERNAME.equals(username) && PASSWORD.equals(password)) {
debug.debug("SampleAuth::process User '{}' " +
"authenticated with success.", username);
return ISAuthConstants.LOGIN_SUCCEED;
}
throw new InvalidPasswordException("password is wrong",
USERNAME, isReturningPrincipalAsDn());
case STATE_ERROR:
return STATE_ERROR;
default:
throw new AuthLoginException("invalid state");
}
}
@Override
public Principal getPrincipal() {
return new SampleAuthPrincipal(USERNAME);
}
private void setErrorText(String err) throws AuthLoginException {
// Receive correct string from properties and substitute the
// header in callbacks order 3.
substituteHeader(STATE_ERROR, bundle.getString(err));
}
private void substituteUIStrings() throws AuthLoginException {
// Get service specific attribute configured in OpenAM
String ssa = CollectionHelper.getMapAttr(options, "specificAttribute");
// Get property from bundle
String new_hdr = ssa + " " +
bundle.getString("sampleauth-ui-login-header");
substituteHeader(STATE_AUTH, new_hdr);
replaceCallback(STATE_AUTH, 0, new NameCallback(
bundle.getString("sampleauth-ui-username-prompt")));
replaceCallback(STATE_AUTH, 1, new PasswordCallback(
bundle.getString("sampleauth-ui-password-prompt"), false));
}
}The Sample Auth Principal
The implementation, SampleAuthPrincipal.java, is shown below:
/*
* The contents of this file are subject to the terms of the Common Development and
* Distribution License (the License). You may not use this file except in compliance with the
* License.
*
* You can obtain a copy of the License at legal/CDDLv1.0.txt. See the License for the
* specific language governing permission and limitations under the License.
*
* When distributing Covered Software, include this CDDL Header Notice in each file and include
* the License file at legal/CDDLv1.0.txt. If applicable, add the following below the CDDL
* Header, with the fields enclosed by brackets [] replaced by your own identifying
* information: "Portions copyright [year] [name of copyright owner]".
*
* Copyright 2011-2017 ForgeRock AS. All Rights Reserved
*/
package org.forgerock.openam.examples;
import java.io.Serializable;
import java.security.Principal;
/**
* SampleAuthPrincipal represents the user entity.
*/
public class SampleAuthPrincipal implements Principal, Serializable {
private final static String COLON = " : ";
private final String name;
public SampleAuthPrincipal(String name) {
if (name == null) {
throw new NullPointerException("illegal null input");
}
this.name = name;
}
/**
* Return the LDAP username for this <code>SampleAuthPrincipal</code>.
*
* @return the LDAP username for this <code>SampleAuthPrincipal</code>
*/
@Override
public String getName() {
return name;
}
/**
* Return a string representation of this <code>SampleAuthPrincipal</code>.
*
* @return a string representation of this
* <code>TestAuthModulePrincipal</code>.
*/
@Override
public String toString() {
return new StringBuilder().append(this.getClass().getName())
.append(COLON).append(name).toString();
}
/**
* Compares the specified Object with this <code>SampleAuthPrincipal</code>
* for equality. Returns true if the given object is also a
* <code> SampleAuthPrincipal </code> and the two SampleAuthPrincipal have
* the same username.
*
* @param o Object to be compared for equality with this
* <code>SampleAuthPrincipal</code>.
* @return true if the specified Object is equal equal to this
* <code>SampleAuthPrincipal</code>.
*/
@Override
public boolean equals(Object o) {
if (o == null) {
return false;
}
if (this == o) {
return true;
}
if (!(o instanceof SampleAuthPrincipal)) {
return false;
}
SampleAuthPrincipal that = (SampleAuthPrincipal) o;
if (this.getName().equals(that.getName())) {
return true;
}
return false;
}
/**
* Return a hash code for this <code>SampleAuthPrincipal</code>.
*
* @return a hash code for this <code>SampleAuthPrincipal</code>.
*/
@Override
public int hashCode() {
return name.hashCode();
}
}The Sample Auth Service Configuration
AM requires that all authentication modules be configured by means of an AM service.
At minimum, the service must include an authentication level attribute.
Your module can access these configuration attributes in the options parameter passed to the init() method.
Some observations about the service configuration file follow in the list below.
-
The document type for a service configuration file is described in
WEB-INF/sms.dtdwhere AM is deployed. -
The service name is derived from the module name. The service name must have the following format:
-
It must start with either
iPlanetAMAuthorsunAMAuth. -
The module name must follow. The case of the module name must match the case of the class that implements the custom authentication module.
-
It must end with
Service.
In the Sample Auth service configuration, the module name is
SampleAuthand the service name isiPlanetAMAuthSampleAuthService. -
-
The service must have a localized description, retrieved from a properties file.
-
The
i18nFileNameattribute in the service configuration holds the default (non-localized) base name of the Java properties file. Thei18nKeyattributes indicate properties keys to string values in the Java properties file. -
The authentication level attribute name must have the following format:
-
It must start with
iplanet-am-auth-,sun-am-auth-, orforgerock-am-auth-. -
The module name must follow, and must appear in lower case if the attribute name starts with
iplanet-am-auth-orforgerock-am-auth-. If the attribute name starts withsun-am-auth-, it must exactly match the case of the module name as it appears in the service name. -
It must end with
-auth-level.
In the Sample Auth service configuration, the authentication level attribute name is
iplanet-am-auth-sampleauth-auth-level. -
-
The Sample Auth service configuration includes an example
sampleauth-service-specific-attribute, which can be configured through the AM admin UI.
The service configuration file, amAuthSampleAuth.xml, is shown below.
Save a local copy of this file, which you use when registering the module.
<?xml version="1.0" encoding="UTF-8"?>
<!--
* The contents of this file are subject to the terms of the Common Development and
* Distribution License (the License). You may not use this file except in compliance with the
* License.
*
* You can obtain a copy of the License at legal/CDDLv1.0.txt. See the License for the
* specific language governing permission and limitations under the License.
*
* When distributing Covered Software, include this CDDL Header Notice in each file and include
* the License file at legal/CDDLv1.0.txt. If applicable, add the following below the CDDL
* Header, with the fields enclosed by brackets [] replaced by your own identifying
* information: "Portions copyright [year] [name of copyright owner]".
*
* Copyright 2011-2020 ForgeRock AS. All Rights Reserved
*
-->
<!DOCTYPE ServicesConfiguration
PUBLIC "=//iPlanet//Service Management Services (SMS) 1.0 DTD//EN"
"jar://com/sun/identity/sm/sms.dtd">
<ServicesConfiguration>
<Service name="iPlanetAMAuthSampleAuthService" version="1.0">
<Schema
serviceHierarchy="/DSAMEConfig/authentication/iPlanetAMAuthSampleAuthService"
i18nFileName="amAuthSampleAuth" revisionNumber="10"
i18nKey="sampleauth-service-description" resourceName="sample">
<Organization>
<!-- Specify resourceName for a JSON-friendly property in the REST SMS -->
<AttributeSchema name="iplanet-am-auth-sampleauth-auth-level" resourceName="authLevel"
type="single" syntax="number_range" rangeStart="0" rangeEnd="2147483647"
i18nKey="a500">
<DefaultValues>
<Value>1</Value>
</DefaultValues>
</AttributeSchema>
<!-- No need for resourceName when the name is JSON-compatible -->
<AttributeSchema name="specificAttribute"
type="single" syntax="string" validator="no" i18nKey="a501" />
<!--
For Auth Modules, the parent Schema element specifies the REST SMS resourceName,
and the nested SubSchema must have resourceName="USE-PARENT"
-->
<SubSchema name="serverconfig" inheritance="multiple" resourceName="USE-PARENT">
<AttributeSchema name="iplanet-am-auth-sampleauth-auth-level" resourceName="authLevel"
type="single" syntax="number_range" rangeStart="0" rangeEnd="2147483647"
i18nKey="a500">
<DefaultValues>
<Value>1</Value>
</DefaultValues>
</AttributeSchema>
<!-- No need for a DefaultValues element when the default is blank -->
<AttributeSchema name="specificAttribute"
type="single" syntax="string" validator="no" i18nKey="a501" />
</SubSchema>
</Organization>
</Schema>
</Service>
</ServicesConfiguration>Building and Installing the Sample Custom Auth Module
Build the module with Apache Maven, and install the module in AM.
Learn about downloading and building PingAM sample source code in the following Knowledge Base article: How do I access and build the sample code provided for PingAM?.
Installing the Module
Installing the sample authentication module consists of copying the .jar file
to AM’s WEB-INF/lib/ directory, registering the module with AM,
and then restarting AM or the web application container where it runs.
-
Copy the sample authentication module
.jarfile toWEB-INF/lib/where AM is deployed.$ cp target/custom*.jar /path/to/tomcat/webapps/openam/WEB-INF/lib/bash -
Restart AM or the container in which it runs.
For example if you deployed AM in Apache Tomcat, then you shut down Tomcat and start it again.
$ /path/to/tomcat/bin/shutdown.sh $ /path/to/tomcat/bin/startup.sh $ tail -1 /path/to/tomcat/logs/catalina.out INFO: Server startup in 14736 msbash
Configure and test the Sample Auth module
Authentication modules are registered as services with AM globally, and then set up for use in a particular realm. In this example, you set up the sample authentication module for use in the realm / (Top Level Realm).
In the AM admin UI, go to Realms > Top Level Realm > Authentication > Modules.
Click Add Module to create an instance of the Sample Authentication Module.
Name the module Sample.
Click Create, and then configure the authentication module as appropriate.
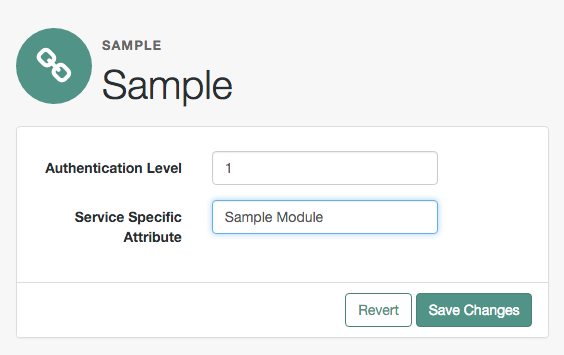
Now that the module is configured, log out of the AM admin UI.
Finally, try the module by specifying the Sample module.
Browse to the login URL such as https://openam.example.com:8443/openam/XUI/?realm=/&module=Sample#login,
and then authenticate with user name demo and password Ch4ng31t.

After authentication you are redirected to the end user page for the demo user.
You can logout of the AM admin UI,
and then try to authenticate as the non-existent user test123 to see what the error handling looks like to the user.
Server-side authentication scripts in authentication modules
This section demonstrates how to use the default server-side authentication script. An authentication script can be called from a Scripted authentication module.
The default server-side authentication script only authenticates a subject
when the current time on the AM server is between 09:00 and 17:00.
The script also uses the logger and httpClient functionality provided in the scripting API.
To examine the contents of the default server-side authentication script in the AM admin UI, go to Realms > Top Level Realm > Scripts, and click Scripted Module - Server Side.
For general information about scripting in AM, see Scripting.
Prepare AM to use server-side authentication scripts
AM requires a small amount of configuration before trying the example server-side authentication script.
You must create an authentication module of the Scripted type, and then include it in an authentication chain,
which can then be used when logging in to AM.
You must also ensure the demo user has an associated postal address.
Create a scripted authentication module that uses the default server-side authentication acript
In this procedure, create a Scripted Authentication module, and link it to the default server-side authentication script.
-
Log in as an AM administrator, for example
amAdmin. -
Go to Realms > Top Level Realm > Authentication > Modules.
-
On the Authentication Modules page, click Add Module.
-
On the New Module page, enter a module name, such as
myScriptedAuthModule, from the Type drop-down list, selectScripted Module, and click Create. -
On the module configuration page:
-
Uncheck the Client-side Script Enabled checkbox.
-
From the Server-side Script drop-down list, select
Scripted Module - Server Side. -
Click Save Changes.
-
Create an authentication chain that uses a Scripted Authentication module
In this procedure, create an authentication chain that uses a Data Store authentication module and the Scripted authentication module created in the previous procedure.
-
Log in as an AM administrator, for example
amAdmin. -
Go to Realms > Top Level Realm > Authentication > Chains.
-
On the Authentication Chains page, click Add Chain.
-
On the Add Chain page, enter a name, such as
myScriptedChain, and click Create. -
On the Edit Chain tab, click Add a Module.
-
In the New Module dialog box:
-
From the Select Module drop-down list, select
DataStore. -
From the Select Criteria drop-down list, select
Required. -
Click OK.
The Data Store authentication module checks the user credentials, whereas the Scripted authentication module does not check credentials, but instead only checks that the authentication request is processed during working hours. Without the Data Store module, the username in the Scripted authentication module cannot be determined. Therefore, do not configure the Scripted authentication module (server-side script) as the first module in an authentication chain, because it needs a username.
-
-
On the Edit Chain tab, click Add Module.
-
In the New Module dialog box:
-
From the Select Module drop-down list, select the Scripted Module from the previous procedure, for example
myScriptedAuthModule. -
From the Select Criteria drop-down list, select
Required. -
Click OK.
The resulting chain resembles the following:
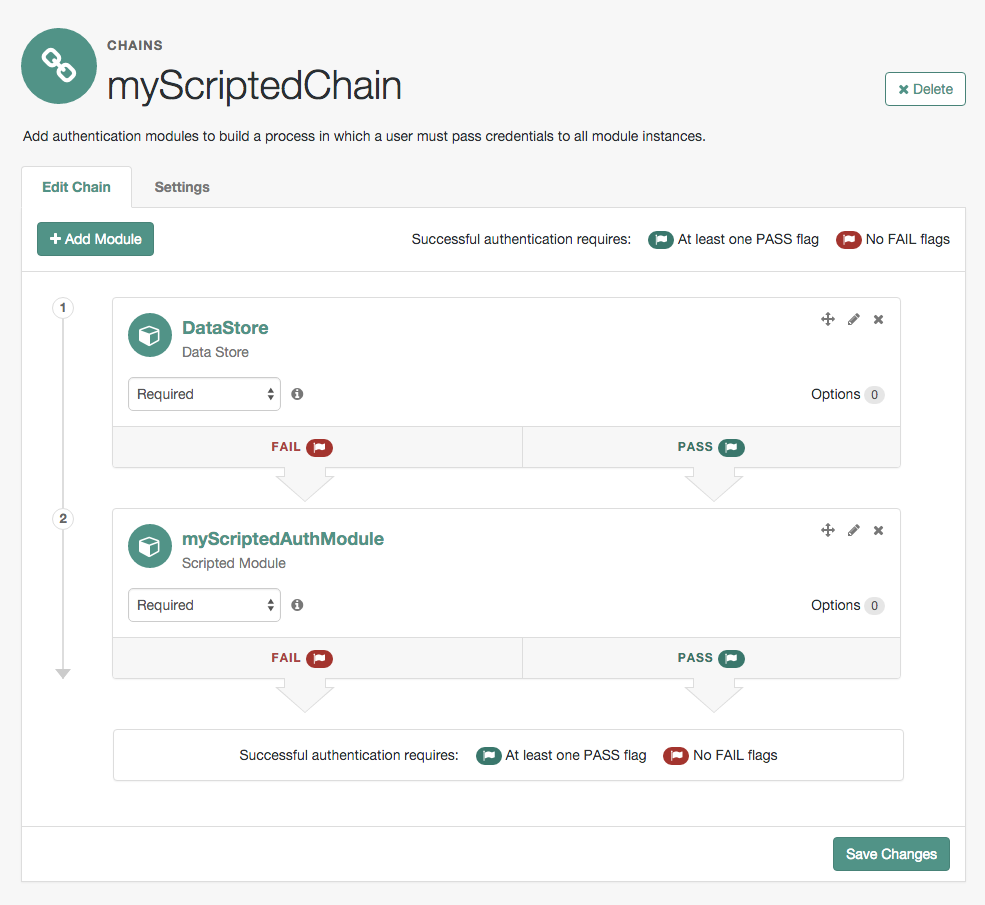
-
-
On the Edit Chain tab, click Save Changes.
Add a postal address to the demo user
-
Log in as an AM administrator, for example
amAdmin. -
Go to Realms > Top Level Realm > Identities.
-
On the Identities tab, click the
demouser. -
In the Home Address field, enter a valid postal address, with lines separated by commas.
For example:
ForgeRock Inc., 201 Mission St #2900, San Francisco, CA 94105, USA
-
Save your changes.
Trying the default server-side authentication script
This section shows how to log in using an authentication chain that contains a Scripted authentication module, which in turn uses the default server-side authentication script.
The default server-side authentication script gets the postal address of a user after they authenticate using a Data Store authentication module, and then makes an HTTP call to an external web service to determine the longitude and latitude of the address. Using these details, a second HTTP call is performed to get the local time at those coordinates. If that time is between two preset limits, authentication is allowed, and the user is given a session and redirected to the profile page.
Log in using a chain containing a Scripted Authentication module
-
Log out of AM.
-
In a browser, go to the AM login URL, and specify the authentication chain created in the previous procedure as the value of the
serviceparameter.For example:
https://openam.example.com:8443/openam/XUI/?service=myScriptedChain#login
-
Log in as user
demowith passwordCh4ng31t.If login is successful, the user profile page is displayed. The script will also output messages, such as the following in the
debug/Authenticationlog file:Starting scripted authentication amScript:02/27/2017 03:22:42:881 PM GMT: Thread[ScriptEvaluator-5,5,main]: TransactionId[7635cd7c-ea97-4be6-8694-9e2be8642d56-8581] User: demo amScript:02/27/2017 03:22:42:882 PM GMT: Thread[ScriptEvaluator-5,5,main]: TransactionId[7635cd7c-ea97-4be6-8694-9e2be8642d56-8581] User address: ForgeRock Inc., 201 Mission St #2900, San Francisco, CA 94105, USA amScript:02/27/2017 03:22:42:929 PM GMT: Thread[ScriptEvaluator-5,5,main]: TransactionId[7635cd7c-ea97-4be6-8694-9e2be8642d56-8581] User REST Call. Status: [Status: 200 OK] amScript:02/27/2017 03:27:31:646 PM GMT: Thread[ScriptEvaluator-7,5,main]: TransactionId[7635cd7c-ea97-4be6-8694-9e2be8642d56-8581] latitude:37.7914374 longitude:-122.3950694 amScript:02/27/2017 03:27:31:676 PM GMT: Thread[ScriptEvaluator-7,5,main]: TransactionId[7635cd7c-ea97-4be6-8694-9e2be8642d56-8581] User REST Call. Status: [Status: 200 OK] amScript:02/27/2017 03:27:31:676 PM GMT: Thread[ScriptEvaluator-7,5,main]: TransactionId[7635cd7c-ea97-4be6-8694-9e2be8642d56-8581] Current time at the users location: 10 amScript:02/27/2017 03:27:31:676 PM GMT: Thread[ScriptEvaluator-7,5,main]: TransactionId[7635cd7c-ea97-4be6-8694-9e2be8642d56-8581] Authentication allowed! amLoginModule:02/27/2017 03:27:31:676 PM GMT: Thread[http-nio-8080-exec-4,5,main]: TransactionId[7635cd7c-ea97-4be6-8694-9e2be8642d56-8581] Login NEXT State : -1 amLoginModule:02/27/2017 03:27:31:676 PM GMT: Thread[http-nio-8080-exec-4,5,main]: TransactionId[7635cd7c-ea97-4be6-8694-9e2be8642d56-8581] SETTING Module name.... :myScriptedAuthModule amAuth:02/27/2017 03:27:31:676 PM GMT: Thread[http-nio-8080-exec-4,5,main]: TransactionId[7635cd7c-ea97-4be6-8694-9e2be8642d56-8581] Module name is .. myScriptedAuthModule amAuth:02/27/2017 03:27:31:676 PM GMT: Thread[http-nio-8080-exec-4,5,main]: TransactionId[7635cd7c-ea97-4be6-8694-9e2be8642d56-8581] successModuleSet is : [DataStore, myScriptedAuthModule] amJAAS:02/27/2017 03:27:31:676 PM GMT: Thread[http-nio-8080-exec-4,5,main]: TransactionId[7635cd7c-ea97-4be6-8694-9e2be8642d56-8581] login successThe default server-side authentication script outputs log messages at the
messageanderrorlevel.AM does not log debug messages from scripts by default. You can configure AM to log such messages by setting the debug log level for the
amScriptservice. For details, see Debug logging. -
To test that the script is being used as part of the login process, edit the script to alter the times when authentication is allowed:
-
Log out the
demouser. -
Log in as an AM administrator, for example
amAdmin. -
Go to Realms > Top Level Realm > Scripts > Scripted Module - Server Side.
-
In the script, swap the values for
START_TIMEandEND_TIME, for example:var START_TIME = 17; var END_TIME = 9;
-
Click Save.
-
Repeat steps 1, 2, and 3 above, logging into the module as the
demouser as before. The authentication result will be the opposite of the previous result, as the allowed times have inverted.
-
Create post-authentication plugins for chains
Post-authentication plugins (PAP) let you include custom processing at the following places in the authentication cycle:
-
At the end of the authentication process, immediately before a user is authenticated.
-
When a user logs out of an AM session.
A common use of post-authentication plugins is to set state information in the session object in conjunction with web or Java agents. The post-authentication plugin sets custom session properties, and then the web or Java agent injects the custom properties into the header sent to the protected application.
Two issues should be considered when writing a post-authentication plugin for an AM deployment that uses client-side sessions:
- Cookie size
-
You can set an unlimited number of session properties in a post-authentication plugin. When AM creates a client-side session, it writes the session properties into the session cookie, increasing the size of the cookie. Very large session cookies can exceed browser limitations. Therefore, when implementing a post-authentication plugin in a deployment with client-side sessions, be sure to monitor the session cookie size and verify that you have not exceeded browser cookie size limits.
For more information about client-side session cookies, see Session cookies and session security.
- Cookie security
-
The AM administrator secures custom session properties in sessions residing in the CTS token store by using firewalls and other typical security techniques.
However, when using client-side sessions, custom session properties are written in cookies and reside on end users' systems. Cookies can be long-lasting and might represent a security issue if any session properties are of a sensitive nature. When developing a post-authentication plugin for a deployment that uses client-side sessions, be sure that you are aware of the measures securing the session contained within the cookie.
For more information about client-side session cookie security, see Configure client-side session security.
Design your post-authentication plugin
Your post-authentication plugin class implements the AMPostAuthProcessInterface interface,
and in particular the following three methods.
public void onLoginSuccess(
Map requestParamsMap,
HttpServletRequest request,
HttpServletResponse response,
SSOToken token
) throws AuthenticationException
public void onLoginFailure(
Map requestParamsMap,
HttpServletRequest request,
HttpServletResponse response
) throws AuthenticationException
public void onLogout(
HttpServletRequest request,
HttpServletResponse response,
SSOToken token
) throws AuthenticationExceptionAM calls the onLoginSuccess() and onLoginFailure() methods
immediately before informing the user of login success or failure, respectively.
AM calls the onLogout() method only when the user actively logs out, not when a user’s session times out.
See the PingAM Java SDK API Specification for reference.
These methods can perform whatever processing you require. Yet, know that AM calls your methods synchronously as part of the authentication process. Therefore, if your methods take a long time to complete, you will keep users waiting. Minimize the processing done in your post-authentication methods.
|
Implementing a post-authentication plugin in the top level realm can have unexpected effects. At the top level realm, AM invokes the post-authentication plugin for all types of authentication during startup, including user logins and internal administrative logins. The best practice is to let end users into subrealms only, and administrators into the top level realm. If you must execute the post-authentication plugin for administrative logins, make sure that the plugin can also handle internal authentications. An alternate solution is to configure the post-authentication plugin on a per authentication chain basis, which can be configured separately for user logins or internal administrative logins. Realm-level post-authentication plugins are only called when no post-authentication plugin is configured for the authentication chain. |
Post-authentication plugins must be stateless: they do not maintain state between login and logout. Store any information that you want to save between login and logout in a session property. AM stores session properties in the CTS token store after login, and retrieves them from the token store as part of the logout process.
Build your sample post-authentication plugin
The following example post-authentication plugin sets a session property during successful login, writing to its debug log if the operation fails.
/*
* The contents of this file are subject to the terms of the Common Development and
* Distribution License (the License). You may not use this file except in compliance with the
* License.
*
* You can obtain a copy of the License at legal/CDDLv1.0.txt. See the License for the
* specific language governing permission and limitations under the License.
*
* When distributing Covered Software, include this CDDL Header Notice in each file and include
* the License file at legal/CDDLv1.0.txt. If applicable, add the following below the CDDL
* Header, with the fields enclosed by brackets [] replaced by your own identifying
* information: "Portions copyright [year] [name of copyright owner]".
*
* Copyright 2011-2019 ForgeRock AS. All Rights Reserved
*/
package com.forgerock.openam.examples;
import java.util.Map;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import org.slf4j.Logger;
import org.slf4j.LoggerFactory;
import com.iplanet.sso.SSOException;
import com.iplanet.sso.SSOToken;
import com.sun.identity.authentication.spi.AMPostAuthProcessInterface;
import com.sun.identity.authentication.spi.AuthenticationException;
/**
* Set a session property on successful authentication.
* If authentication fails, log a debug message.
*/
public class SamplePAP implements AMPostAuthProcessInterface {
private final static String PROP_NAME = "MyProperty";
private final static String PROP_VALUE = "MyValue";
private final static String DEBUG_FILE = "SamplePAP";
private Logger debug = LoggerFactory.getLogger(SamplePAP.class);
public void onLoginSuccess(
Map requestParamsMap,
HttpServletRequest request,
HttpServletResponse response,
SSOToken token
) throws AuthenticationException {
try {
token.setProperty(PROP_NAME, PROP_VALUE);
} catch (SSOException e) {
debug.error("Unable to set property");
}
}
public void onLoginFailure(
Map requestParamsMap,
HttpServletRequest request,
HttpServletResponse response
) throws AuthenticationException {
// Not used
}
public void onLogout(
HttpServletRequest request,
HttpServletResponse response,
SSOToken token
) throws AuthenticationException {
// Not used
}
}If you have not already done so, download and build the sample code.
Learn about downloading and building PingAM sample source code in the following Knowledge Base article: How do I access and build the sample code provided for PingAM?.
In the sources, you find the following files:
pom.xml-
Apache Maven project file for the module
This file specifies how to build the sample post-authentication plugin, and also specifies its dependencies on AM components and on the Servlet API.
src/main/java/com/forgerock/openam/examples/SamplePAP.java-
Core class for the sample post-authentication plugin
Once built, copy the .jar to the WEB-INF/lib directory where you deployed AM.
$ cp target/*.jar /path/to/tomcat/webapps/openam/WEB-INF/lib/Restart AM or the container in which it runs.
Configure your post-authentication plugin
You can associate post-authentication plugins with realms or services (authentication chains). Where you configure the plugin depends on the scope to which the plugin should apply:
-
Plugins configured at the realm level are executed when authenticating to any authentication chain in the realm, provided the authentication chain does not have an associated plugin.
-
Plugins configured at the service level are executed if that authentication chain is used for authentication. Any plugins configured at the realm level will not execute.
In the AM admin UI, go to Realms > Realm Name > Authentication > Settings > Post Authentication Processing.
In the Authentication Post Processing Classes list,
add the sample plugin class, com.forgerock.openam.examples.SamplePAP, and click Save.
Alternatively, you can configure sample plugin for the realm by using the ssoadm command.
$ ssoadm set-svc-attrs \
--adminid uid=amAdmin,ou=People,dc=openam,dc=forgerock,dc=org \
--password-file /tmp/pwd.txt \
--servicename iPlanetAMAuthService \
--realm /myRealm \
--attributevalues iplanet-am-auth-post-login-process-class=
com.forgerock.openam.examples.SamplePAP
iPlanetAMAuthService under /myRealm was
modified.Test your post-authentication plugin
To test the sample post-authentication plugin,
login successfully to AM in the scope where the plugin is configured.
For example, if you configured your plugin for the realm, /myRealm, specify the realm in the login URL.
https://openam.example.com:8443/openam/XUI/?realm=/myRealm#login
Although you will not notice anywhere in the user interface that AM calls your plugin, a web or Java agent or custom client code could retrieve the session property that your plugin added to the user session.
Success and failure redirection URLs
AM determines the redirection URL based on authentication success or failure.
You can configure success and failure URLs in a number of places in AM. For each authentication outcome, the user is redirected to the URL with the highest precedence, which is determined by where it is defined in AM.
Success URL precedence
When a user authenticates successfully, AM evaluates the redirection URL according to the following order of precedence:
-
The URL set in the
gotologin URL parameter. For example:https://openam.example.com:8443/openam/XUI/?realm=/alpha&goto=http%3A%2F%2Fwww.example.com#loginUnless the URLs are in the same domain as PingAM, any URLs specified in the gotoparameter must be explicitly listed in the Valid goto URL Resources property of the Validation Service. Otherwise, they’re ignored. -
The URL set in the authentication tree.
Add a Success URL node to the tree and configure the Success URL in the node properties.
-
The URL set in the Success URL attribute in the user’s profile.
In the AM admin UI, go to Realm Name > Identities > identity. In the Success URL field, enter a URL, and save your changes.
You can also specify the client type by entering
ClientType|URLas the property value. If the client type is specified, it takes precedence over a regular URL in the user’s profile. -
The URL set in the Default Success Login URL attribute in the Top Level Realm.
Go to Configure > Authentication > Core Attributes > Post Authentication Processing. In the Default Success Login URL field, enter a URL, and save your changes.
You can also specify the client type by entering
ClientType|URLas the property value. If the client type is specified, it will have precedence over a Default Success Login URL in the Top Level realm.
Failure URL precedence
When a user fails to authenticate, AM evaluates the redirection URL according to the following order of precedence:
-
The URL set in the authentication chain or authentication tree.
-
To specify a URL in an authentication chain, in the AM admin UI, go to Realm Name > Authentication > Chains > chain > Settings. Enter a URL in the Failed Login URL field and save your changes.
-
To specify a URL in an authentication tree, add a Failure URL node to the tree and configure the failure URL in the node properties.
-
-
The URL set in the
gotoOnFailparameter. For example:https://openam.example.com:8443/openam/XUI/?realm=/alpha&gotoOnFail=http%3A%2F%2Fwww.example.com#loginUnless the URLs are in the same domain as PingAM, any URLs specified in the gotoOnFailparameter must be explicitly listed in the Valid goto URL Resources property of the Validation Service. Otherwise, they’re ignored. -
The URL set in the authentication tree.
Add a Failure URL node to the tree and configure the failure URL in the node properties.
-
The URL set in the Failure URL attribute in the user’s profile.
In the AM admin UI, go to Realm Name > Identities > identity. In the Failure URL field, enter a URL, and save your changes.
You can also specify the client type by entering
ClientType|URLas the property value. If the client type is specified, it will have precedence over a regular URL in the user’s profile. -
The URL set in the Default Failure Login URL attribute in the Top Level Realm.
In the AM admin UI, go to Configure > Authentication > Core Attributes > Post Authentication Processing. In the Default Failure Login URL field, enter a URL, and save your changes.
You can also specify the client type by entering
ClientType|URLas the property value. If the client type is specified, it will have precedence over a Default Failure Login URL in the Top Level realm.
Configure trusted URLs
Redirection URLs can be relative to AM’s URL, or absolute.
By default, AM trusts all relative URLs and those absolute URLs that are in the same scheme, FQDN, and port as AM. This increases security against possible phishing attacks through an open redirect.
To configure AM to trust other absolute URLs, add them to the validation service. If they are not added, AM will redirect to the user profile or to the administrator console on log in, and to the default logout page in the UI on log out.
Do I need to add my URL to the validation service?
Consider these example URLS for a deployment configured at https://openam.example.com:8443/openam:
| URL | Add to the validation service? |
|---|---|
|
Yes, the scheme and port are different. |
|
Yes, the port is different. |
|
No, the paths relative to the AM URL are trusted. |
|
Yes, the scheme, port, and FQDN are different. |
Add a URL to the validation service
-
In the AM admin UI, go to Realms > Realm Name > Services.
Note that you can add an instance of the validation service on the Top Level Realm, too.
-
If the Validation Service is not in the list of services, configure a new service:
-
Click Add a Service.
-
From the Choose a service type drop-down list, select Validation Service.
-
-
In the Valid goto URL Resources field, enter one or more valid URL patterns to allow.
For example,
http://app.example.com:80/*?*.General examples of URL pattern matching
-
If no port is specified,
http://www.example.comcanonicalizes tohttp://www.example.com:80andhttps://www.example.comcanonicalizes tohttps://www.example.com:443. -
A wildcard before "://" only matches up to "://"
For example,
http*://*.com/*matcheshttp://www.example.com/hello/worldandhttps://www.example.com/hello. -
A wildcard between "://" and ":" matches up to ":"
For example,
http://*:85matcheshttp://www.example.com:85. -
A wildcard between ":" and "/" only matches up to the first "/"
For example,
http://www.:/matcheshttp://www.example.com:80. In another example,http://www.example.com:*matcheshttp://www.example.com:<any port>andhttp://www.example.com:<any port>, but nothing more. -
A wildcard after "/" matches anything, depending on whether it is single-level or a wildcard appropriately.
For example,
https://www.example.com/*matcheshttps://www.example.com:443/foo/bar/baz/me. -
If you do not use any wildcards, AM exactly matches the string, so
http://www.example.comonly matcheshttp://www.example.com, but NOThttp://www.example.com/(trailing slash).If you put the wildcard after the path, AM expects a path (even if it is blank), so
http://www.example.com/*matcheshttp://www.example.com/andhttp://www.example.com/foo/bar/baz.html, but NOThttp://www.example.com. -
http://www.example.com:*/matcheshttp://www.example.com/, which also canonicalizes tohttp://www.example.com:80/. -
https://www.example.com:*/matcheshttps://www.example.com/, which also canonicalizes tohttps://www.example.com:443/.
For more information on pattern matching and wildcard rules, refer to Specifying resource patterns with wildcards.
-
-
Click Create to save your settings.
Validate a goto URL
To validate a goto URL over REST, use the /json/users?_action=validateGoto endpoint
(or /json/realms/root/realms/_Realm Name_/users?_action=validateGoto to specify a sub realm).
For example:
$ curl \
--request POST \
--header "Accept-API-Version: protocol=2.1,resource=3.0" \
--header "Content-Type: application/json" \
--header "iPlanetDirectoryPro: AQIC5…ACMDE.*" \
--data '{"goto":"https://www.example.com/"}' \
'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/users?_action=validateGoto'
{
"successURL":"https://www.example.com/"
}If the URL is valid, the endpoint returns the specified URL as the successURL response parameter.
A goto URL is considered valid if one of the following is true:
-
The URL is configured in the validation service
-
The URL is relative
-
The URL is encoded
Encoded URLs are treated as relative URLs for the purposes of validation. To be treated as an absolute URL, the URL must not be encoded.
If the specified URL is invalid, the endpoint returns the default success URL.
Note that a valid session is optional; you can still call the validateGoto endpoint with an expired session.
Realm authentication configuration
AM users always authenticate to a realm. Each realm has a set of authentication settings that apply to all authentication performed to that realm. The settings are referred to as core authentication attributes.
To configure core authentication attributes for an entire AM deployment, go to Configure > Authentication in the AM admin UI, and click Core Attributes.
Each realm has a set of authentication settings that apply to all authentication performed to that realm. The settings are referred to as core authentication attributes. To override the global core authentication configuration in a realm, go to Realms > Realm Name > Authentication > Settings in the AM admin UI. Note that when you configure core authentication attributes in a realm, the Global tab does not appear.
Use core authentication attributes to configure:
-
The list of available authentication modules
-
Which types of clients can authenticate with which modules
-
Connection pools for access to directory servers
-
Whether to retain objects used during authentication so they can be used at logout
-
Defaults for configuring authentication in a particular realm
For detailed information about the core configuration attributes, see Core authentication attributes.
Authenticate with a browser
When using AM’s extended user interface (XUI),
the base URL to authenticate to points to /XUI/#login under the deployment URL,
such as https://openam.example.com:8443/openam/XUI/#login.
The base URL to log out is similar, for example, https://openam.example.com:8443/openam/XUI/#logout/.
When authenticating using a browser, you can send AM a realm and also different authentication parameters that would help you customize the user’s experience.
Specify the realm in the URL
When making a request to the UI, specify the realm or realm alias as the value of a realm parameter
in the query string, or the DNS alias in the domain component of the URL.
If you don’t use a realm alias, you must specify the entire hierarchy of the realm.
For example: https://am.example.com:8443/am/XUI/?realm=/customers/europe#login/.
The following table demonstrates additional examples:
| Description | Example URL |
|---|---|
Full path of the realm as a parameter of |
|
Realm alias of the realm as a parameter of |
|
DNS Alias of the realm as the fully qualified host name in the URL |
|
The DNS alias is overridden by any use of either the full path or a realm alias as a query string parameter.
Authentication parameters
AM accepts the following parameters in the query string. Except for the IDToken parameters, do not set a
parameter more than once in a single query.
- arg=newsession
-
Request that AM end the user’s current session and start a new session.
- authlevel
-
Request that AM authenticate the user using a module with at least the specified authentication level that you have configured.
As this parameter determines authentication module selection, do not use it with
module,service, oruser.
- ForceAuth
-
If
ForceAuth=true, request that AM force the user to authenticate even if they already have a valid session.When
ForceAuth=true, on successful authentication AM does one of the following:-
(Authentication trees only) AM issues new session tokens to users on reauthentication, even if the current session already meets the security requirements.
-
(Authentication chains only) AM does not issue new session tokens on reauthentication, regardless of the security level they are authenticating to. Instead, it updates the session token with the new authentication information, if required. In this configuration, session upgrade is not supported for client-side sessions. When a user attempts to reauthenticate with a client-side session, they will see a
ForceAuth fails since session is statelessdialog.
For authentication chains, the
forceAuth.enabledadvanced server property controls whether the value of theForceAuthparameter is respected. -
- goto
-
On successful authentication, or successful logout, request that AM redirect the user to the specified location. Values must be URL-encoded. For more information, refer to Success and failure redirection URLs.
- gotoOnFail
-
On authentication failure, request that AM redirect the user to the specified location. Values must be URL-encoded. For more information, refer to Success and failure redirection URLs.
- IDToken1, IDToken2, …, IDTokenN
-
Pass the specified credentials as
IDTokenparameters in the URL. TheIDTokencredentials map to the fields in the Login page for the authentication module, such asIDToken1as user ID andIDToken2as password for basic user name, password authentication. The order depends on the callbacks in Login page for the module;IDTokenNrepresents the Nth callback of the Login page. - locale
-
Request that AM display the user interface in the specified, supported locale. Locale can also be set in the user’s profile, in the HTTP header from her browser, configured in AM, and so on.
- module
-
Request that AM use the authentication module instance as configured for the realm where the user is authenticating.
As this parameter determines authentication module selection, do not use it with
authlevel,service, oruser. - realm
-
Request that AM authenticate the user to the specified realm.
- resource
-
Set this parameter to
trueto request resource-based authentication.For resource-based authentication, also set the
resourceURLparameter. - resourceURL
-
Authentication chains only. This parameter does not apply to authentication trees.
Set the
resourceURLto the URL of the resource for resource-based authentication.Resource-based authentication applies when an authorization policy has an environment condition of type Authentication by Service or Authentication by Module Instance. When the resource URL matches a policy resource, AM finds the chain or module configured in the policy environment settings and uses the specified chain or module to perform authentication.
For example, if you configure a policy with the resource
https://www.example.com:443/index.htmland the environment condition Authentication by Service: DataStore, the following login URL causes AM to use the DataStore service to authenticate the user:https://openam.example.com:8443/openam/XUI/#login?resource=true&resourceURL=https://www.example.com:443/index.html&goto=https://www.example.com/
On successful authentication, AM redirects the user-agent to
https://www.example.com/.As shown in the example, when setting the
resourceURLparameter, also setresource=true. - service
-
Request that AM authenticate the user with the specified authentication chain.
As this parameter determines authentication module selection, do not use it with
authlevel,module, oruser. - user
-
Request that the user, specified by their AM universal ID, authenticate according to the chain specified by the User Authentication Configuration property in their user profile. You can configure this property for a user under Realms > Realm Name > Identities > UserName.
In order for the User Authentication Configuration property to appear in user profiles, the
iplanet-am-user-serviceobject class must contain theiplanet-am-user-auth-configattribute in the identity repository schema. The default identity repository schema provided with AM includes this object class and attribute.For information about identity repository schema, refer to Prepare identity repositories .
As this parameter determines authentication module selection, do not use it with
authlevel,module, orservice.
Example UI login URLs
Use any of the options listed in Authentication parameters as URL parameters. Note that URL parameters must appear before any occurrences of the pound or hash character (#). The following are example URLs with parameters:
| Description | Example URL |
|---|---|
Log in to the Top Level Realm, requesting that AM display the user interface in German. |
|
Log in to the |
|
Log in to the |
|
Authenticate over REST
AM provides the /json/authenticate endpoint for authentication,
and the /json/sessions endpoint for managing sessions and logging out.
The following table summarizes authentication operations you can perform using REST:
| Task | Resources |
|---|---|
Authenticate to AM Authenticating to AM means logging in to a specific realm and receiving a session token from AM. Add parameters to the authentication request to provide AM with more information about how you want to authenticate. |
|
Use the session token AM provides you with a session token after authenticating to a realm. Use this token in subsequent calls to AM. For example, when using REST calls to create, modify, or delete configuration objects. |
|
Log out of AM Log out your users by sending a |
|
Invalidate sessions Obtain all the sessions for a given user and invalidate them to ensure they are logged out of AM. |
Log in to AM over REST
To authenticate to AM using REST, make an HTTP POST request to the json/authenticate endpoint.
You must specify the entire hierarchy of the realm, starting at the Top Level Realm.
Prefix each realm in the hierarchy with the realms/ keyword.
For example, /realms/root/realms/customers/realms/europe.
|
The |
AM uses the default authentication service configured for the realm. You can override the default by specifying authentication services and other options in the REST request.
AM provides both simple authentication methods, such as providing username and password, and complex authentication journeys that may involve a tree with inner tree evaluation and/or multi-factor authentication.
For authentication journeys where providing a username and password is enough,
you can log in to AM using a curl command similar to the following:
$ curl \
--request POST \
--header "Content-Type: application/json" \
--header "X-OpenAM-Username: demo" \
--header "X-OpenAM-Password: Ch4ng31t" \
--header "Accept-API-Version: resource=2.0, protocol=1.0" \
'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/authenticate'
{
"tokenId":"AQIC5wM…TU3OQ*",
"successUrl":"/openam/console",
"realm":"/alpha"
}The username and password are sent in headers. This zero page login mechanism works only for name/password authentication.
Note that the POST body is empty; otherwise, AM interprets the body as a continuation of an existing authentication attempt, one that uses a supported callback mechanism. AM implements callback mechanisms to support complex authentication journeys, such as those where the user needs to be redirected to a third party or interact with a device as part of multi-factor authentication.
After a successful authentication,
AM returns a tokenId object that applications can present as a cookie value
for other operations that require authentication.
This object is known as the session token.
For more information about how applications can use the session token,
see Session token after authentication.
If HttpOnly cookies are enabled and a client calls the /json/authenticate endpoint with a valid SSO token,
AM returns the tokenId field empty.
For example:
{
"tokenId":"",
"successUrl":"/openam/console",
"realm":"/alpha"
}|
You can request AM to authenticate a user without providing them a session by using the |
UTF-8 usernames
To use UTF-8 usernames and passwords in calls to the /json/authenticate endpoint,
base64-encode the string, and wrap the string as described in RFC 2047:
encoded-word = "=?" charset "?" encoding "?" encoded-text "?="
For example, to authenticate using a UTF-8 username, such as ɗëɱø, perform the following steps:
-
Encode the string in base64 format:
yZfDq8mxw7g=. -
Wrap the base64-encoded string as per RFC 2047:
=?UTF-8?B?yZfDq8mxw7g=?=. -
Use the result in the
X-OpenAM-Usernameheader passed to the authentication endpoint as follows:$ curl \ --request POST \ --header "Content-Type: application/json" \ --header "X-OpenAM-Username: =?UTF-8?B?yZfDq8mxw7g=?=" \ --header "X-OpenAM-Password: Ch4ng31t" \ --header "Accept-API-Version: resource=2.0, protocol=1.0" \ 'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/authenticate' { "tokenId": "AQIC5w…NTcy*", "successUrl": "/openam/console", "realm":"/alpha" }bash
Authenticate to specific authentication services
You can provide AM with additional information about how you are authenticating. For example, you can specify the authentication tree you want to use, or request from AM a list of the authentication services that would satisfy a particular authentication condition.
The following example shows how to specify the ldapService chain
by using the authIndexType and authIndexValue query string parameters:
$ curl \
--request POST \
--header "X-OpenAM-Username: demo" \
--header "X-OpenAM-Password: Ch4ng31t" \
--header 'Accept-API-Version: resource=2.0, protocol=1.0' \
'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/authenticate?authIndexType=service&authIndexValue=ldapService'You can exchange the ldapService chain with any other chain or tree.
For more information about using the authIndexType parameter to authenticate to specific services,
see Authenticate endpoint parameters.
Return callback information to AM
The /json/authenticate endpoint supports callback mechanisms to perform complex authentication journeys.
Whenever AM needs to return or request information,
it will return a JSON object with the authentication step, the authentication identifier, and the related callbacks.
The following types of callbacks are available:
-
Read-only callbacks. AM uses read-only callbacks to provide information to the user, such as text messages or the amount of time that the user needs to wait before continuing their authentication journey.
-
Interactive callbacks. Interactive callbacks request information from the user. Use these, for example, to request a user’s username and password or to request that the user select between options.
-
Backchannel callbacks. AM uses backchannel callbacks when it needs to access additional information from the user’s request. For example, when it requires a particular header or a certificate.
Read-only and interactive callbacks have an array of output elements suitable for displaying to the end user.
The JSON returned in interactive callbacks also contains an array of link:input elements,
which must be completed and returned to AM.
For example:
"output": [
{
"name": "prompt",
"value": " User Name: "
}
],
"input": [
{
"name": "IDToken1",
"value": ""
}
]The value of some interactive callbacks can be returned as headers,
such as the X-OpenAM-Username and X-OpenAM-Password headers,
but most of them must be returned in JSON as a response to the request.
Depending on how complex the authentication journey is, AM may return several callbacks sequentially. Each must be completed and returned to AM until authentication is successful.
The following example shows a request for authentication,
and AM’s response of the NameCallback and PasswordCallback callbacks:
$ **curl \
--request POST \
--header "Content-Type: application/json" \
--header "Accept-API-Version: resource=2.0, protocol=1.0" \
'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/authenticate'
{
"authId": "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJvdGsiOiJ…", (1)
"template": "", (2)
"stage": "DataStore1", (3)
"callbacks": [
{
"type": "NameCallback", (4)
"output": [ (5)
{
"name": "prompt",
"value": " User Name: "
}
],
"input": [ (6)
{
"name": "IDToken1",
"value": ""
}
]
},
{
"type": "PasswordCallback",
"output": [
{
"name": "prompt",
"value": " Password: "
}
],
"input": [
{
"name": "IDToken2",
"value": ""
}
]
}
]
}| 1 | The JWT that uniquely identifies the authentication context to AM. |
| 2 | A template to customize the look of the authentication module, if it exists. Learn more in How do I customize the Login page? in the Knowledge Base. |
| 3 | The authentication module stage where the authentication journey is at the moment. |
| 4 | The type of callback. It must be listed under Supported callbacks. |
| 5 | The information AM offers about this callback. Usually, this information would be displayed to the user in the UI. |
| 6 | The information AM is requesting.
The user must fill the "value": "" object with the required information. |
To respond to a callback, send back the whole JSON object with the missing values filled.
The following example shows how to respond to the NameCallback and PasswordCallback callbacks,
with the demo and Ch4ng31t values filled:
$ curl \
--request POST \
--header "Content-Type: application/json" \
--header "Accept-API-Version: resource=2.0, protocol=1.0" \
--data '{
"authId":""eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJvdGsiOiJ…",
"template":"",
"stage":"DataStore1",
"callbacks":[
{
"type":"NameCallback",
"output":[
{
"name":"prompt",
"value":" User Name: "
}
],
"input":[
{
"name":"IDToken1",
"value":"demo"
}
]
},
{
"type":"PasswordCallback",
"output":[
{
"name":"prompt",
"value":" Password: "
}
],
"input":[
{
"name":"IDToken2",
"value":"Ch4ng31t"
}
]
}
]
}' \
'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/authenticate'
{
"tokenId":"AQIC5wM…TU3OQ*",
"successUrl": "/openam/console",
"realm":"/alpha"
}On complex authentication journeys, AM may send several callbacks sequentially. Each must be completed and returned to AM until authentication is successful.
For more information about the callbacks AM may return, refer to Supported callbacks.
Session token after authentication
After a successful authentication,
AM returns a tokenId object that applications can present as a cookie value
for other operations that require authentication.
This object is a session token—a
representation of the exchange of information and credentials between AM and the user or identity.
The type of tokenId returned varies
depending on where AM stores the sessions for the realm to which the user authenticates:
-
If server-side sessions are enabled, the
tokenIdobject is a reference to the session state stored in the CTS token store. -
If client-side sessions are enabled, the
tokenIdobject is the session state for that particular user or identity.
Developers should be aware that the size of the tokenId for client-side sessions—2000 bytes or greater—is
considerably longer than for server-side sessions—approximately 100 bytes.
For more information about session tokens, see Session cookies and session security.
The following is a common scenario when accessing AM by using REST API calls:
-
Call the
/json/authenticateendpoint to log a user in to AM.This REST API call returns a
tokenIDvalue, which is used in subsequent REST API calls to identify the user:$ curl \ --request POST \ --header "Content-Type: application/json" \ --header "X-OpenAM-Username: demo" \ --header "X-OpenAM-Password: Ch4ng31t" \ --header "Accept-API-Version: resource=2.0, protocol=1.0" \ 'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/authenticate' { "tokenId":"AQIC5wM…TU3OQ*", "successUrl":"/openam/console", "realm":"/alpha" }bashThe returned
tokenIDis known as a session token (also referred to as an SSO token). REST API calls made after successful authentication to AM must present the session token in the HTTP header as proof of authentication. -
Call one or more additional REST APIs on behalf of the logged-in user.
Each REST API call passes the user’s
tokenIDback to AM in the HTTP header as proof of previous authentication.The following is a partial example of a
curlcommand that inserts the token ID returned from a prior successful AM authentication attempt into the HTTP header:$ curl \ --request POST \ --header "Content-Type: application/json" \ --header "iPlanetDirectoryPro: AQIC5w…NTcy*" \ --header "Accept-API-Version: resource=2.0, protocol=1.0" \ --data '{ …bashObserve that the session token is inserted into a header field named
iPlanetDirectoryPro. This header field name must correspond to the name of the AM session cookie—by default,iPlanetDirectoryPro. You can find the cookie name in the AM admin UI, by navigating to Deployment > Servers > Server Name > Security > Cookie, in the Cookie Name field of the AM admin UI.Once a user has authenticated, it is not necessary to insert login credentials in the HTTP header in subsequent REST API calls. Note the absence of
X-OpenAM-UsernameandX-OpenAM-Passwordheaders in the preceding example.Users are required to have appropriate privileges in order to access AM functionality using the REST API. For example, users who lack administrative privileges cannot create AM realms. For more information on the AM privilege model, see Delegating Privileges.
-
Call the REST API to log the user out of AM, as described in Authenticate over REST.
As with other REST API calls made after a user has authenticated, the REST API call to log out of AM requires the user’s
tokenIDin the HTTP header.
Log out of AM over REST
Authenticated users can log out with the token cookie value and an HTTP POST to /json/sessions/?_action=logout:
$ curl \
--request POST \
--header "Content-type: application/json" \
--header "iPlanetDirectoryPro: AQICS…NzEz*" \
--header "Accept-API-Version: resource=3.1, protocol=1.0" \
'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/sessions/?_action=logout'
{
"result": "Successfully logged out"
}For information about using an administrator token to force the logout of other authenticated users, refer to Invalidate sessions.
Single sign-on
Single sign-on (SSO) lets users who have authenticated to AM access multiple independent services from a single login session by storing user sessions as HTTP cookies. (If you are unfamiliar with HTTP cookies, see HTTP cookies for more information.)
Cross-domain single sign-on (CDSSO) is an AM-specific capability
that provides SSO inside the same organization within a single domain or across domains.
For example, CDSSO allows your AM servers in the DNS domain .internal.net
to provide authentication and authorization to web and Java agents from the .internal.net domain
and other DNS domains, such as .example.net.
Since CDSSO removes the constraint of configuring SSO depending on the DNS domain, it simplifies the deployment of SSO in your environment.
When implementing CDSSO, take into account the following points:
-
For SSO across multiple organizations or when integrating with other access management software, use AM’s federation capabilities, such as OAuth 2.0 or SAML v2.0.
-
Web agents and Java agents both support CDSSO.
AM also supports CDSSO with PingGateway. Learn more in Single Sign-On and Cross-Domain Single Sign-On in the PingGateway documentation.
-
CDSSO supports server-side and client-side sessions. For more information about session state impact on CDSSO, see Impact of storage location for sessions.
Web agents and Java agents wrap the SSO session token inside an OpenID Connect (OIDC) JSON Web Token (JWT).
During the CDSSO flow, the agents create cookies for the different domains specified in the agent profile,
and the oauth2/authorize endpoint authorizes the different cookie domains as required.
The following diagram illustrates the CDSSO flow for web agents and Java agents:
Realms and SSO
When changing authentication realms, a subject leaves the current SSO realm. The new SSO realm might apply to different applications, and use a different authentication process. For AM, logging in to a new realm means logging out of the current realm.
When a user interactively changes realms through the end user UI, AM offers the option of logging out of the current realm to log in to the new realm, or choosing to remain logged in to the current realm.
The result depends on the user’s choice:
-
If the user cancels the change at this point, the user remains logged in to the current realm, and is not logged in to the new realm.
-
If the user chooses to log in to the new realm, AM first logs the user out of the current realm, and then prompts the user to log in to the new realm.
HTTP cookies
To understand how SSO works, you need to understand some key elements of the HTTP cookie, as described in RFC 6525, HTTP State Management Mechanism.
Within an HTTP cookie, you can store a single custom name=value pair, such as sessionid=value.
Other properties within a cookie are as follows:
- Domain
-
Normally set to the full URL that was used to access the configurator. To work with multiple subdomains, the
Domainshould be set to a URL likeDomain=server.example.net. This is also known as the cookie domain. - Path
-
The directory in the URL to which the cookie applies. If the
Path=/openam, the cookie applies to the/openamsubdirectory of the URL, and lower level directories, includingopenam/XUI. - Secure
-
If the
Securename is included, the cookie can be transferred only over HTTPS. When a request is made over HTTP, the cookie is not made available to the application.For more information, see Secure cookies by default.
- HttpOnly
-
When the
HttpOnlyflag is included, that cookie will not be accessible through JavaScript. According to RFC 6265, the noted flag "instructs the user agent to omit the cookie when providing access to cookies via 'non-HTTP' APIs (for example, a web browser API that exposes cookies to scripts)."For more information, see HttpOnly session cookies.
- Expires
-
The lifetime of a cookie can be limited, with an
Expiresname configured with a time, based on UTC (GMT).
|
Do not take a shortcut with a top-level domain.
Web browser clients today are designed to ignore cookies set to top-level domains including |
Implement CDSSO
CDSSO provides SSO capabilities for AM servers and web or Java agents within a single domain or across domains in the same organization.
CDSSO is the only mode of operation for web and Java agents, so no additional configuration is required to make it work.
You must, however, protect the session cookie against hijacking. For more information, see Restrict tokens for CDSSO session cookies.
|
PingGateway also supports CDSSO with AM. Learn more in the PingGateway Gateway Guide. |
Troubleshoot SSO
In general, problems with single sign-on relate to some sort of mismatch of domain names.
For example, a cookie that is configured on a third-level domain, such as sso.example.net,
will not work with an application on a similar domain, such as app.example.net.
The following list describes scenarios that may lead to similar problems:
-
When a cookie domain does not match a domain for the protected application.
Assume the application is configured on a domain named
example.org. That application will not receive an SSO token configured on theexample.netdomain. -
When a third-level domain is used for the SSO token.
If an SSO token is configured on
sso.example.net, an application onapp.example.netdoes not receive the corresponding session token. In this case, the solution is to configure the SSO token onexample.net. -
When the
Cookie Securityor theCDSSO Secure Enableproperties are configured in the agent profile with a regular HTTP application.If you need encrypted communications for an application protected by AM, use the
Cookie Securityor theCDSSO Secure Enableproperties and make sure the application is accessible over HTTPS. -
When the path listed in the cookie does not match the path for the application.
Perhaps the cookie is configured with a
/helloworldpath; that will not match an application that might be configured with a/hellomarspath. In that case, the application will not receive the cookie. -
When an inappropriate name is used for the cookie domain.
As noted earlier, client browsers are configured to ignore first-level domains, such as
comandnetas well as functional equivalents, such asco.ukandco.jp. -
When working with different browsers.
The
name=valuepairs described earlier may not apply to all browsers. The requirements for an HTTP cookie sent to an IE browser may differ from the requirements for other standard browsers, such as Firefox and Chrome. Based on anecdotal reports, IE does not recognize domain names that start with a number. In addition, IE reportedly refuses cookies that include the underscore (_) character in the FQDN. -
When a client-side session cookie exceeds the maximum size permitted by the browser.
As described in Session cookies and session security, the default size of the
iPlanetDirectoryProcookie is approximately 2,000 bytes. When you customize AM sessions by adding attributes, the cookie size grows. Browsers allow cookie sizes between 4,000 and 5,200 bytes, depending on the browser. AM single sign-on does not support a cookie size that exceeds the maximum cookie size allowed by the browser.
Social authentication
AM supports delegated authentication through third-party identity providers, such as Facebook, and Google. This lets users log in to AM using their social provider credentials.
|
This page shows you how to configure social authentication in a standalone AM deployment. To configure social authentication in the Ping Identity Platform, refer to the Ping Identity Platform Self-Service Guide. |
These topics describe the high-level steps to configure social authentication.
Configure social identity providers
AM supports social identity providers that are OAuth 2.0 or OIDC 1.0-compliant. A number of social identity providers are configured by default:
| Identity provider | Specification |
|---|---|
Amazon |
OAuth 2.0 |
Apple |
OIDC |
OAuth 2.0 |
|
OIDC |
|
OAuth 2.0 |
|
itsme(1) |
OIDC |
OAuth 2.0 |
|
Microsoft |
OAuth 2.0 |
Salesforce |
OAuth 2.0 |
OAuth 2.0 |
|
VK (Vkontakte) |
OAuth 2.0 |
OAuth 2.0 |
|
WordPress |
OAuth 2.0 |
Yahoo |
OIDC |
(1) To integrate with itsme, you must obtain an Organization Validation (OV) certificate.
You must also configure it in the container where AM runs, or in the reverse proxy offloading SSL.
You can add providers that are not configured by default, as long as these providers have a solution implemented using either OAuth 2.0, or OpenID Connect.
Add identity providers
-
Register a service in the identity provider, and keep the provider’s documentation within reach. You will use it during this procedure.
To register a service in a provider, you must at least create a client ID and add the redirect URL to AM.
Redirect URLs
A redirect URL is a path in AM to which the identity provider redirects the user on successful authentication. For example,
https://platform.example.com:8443/am.Depending on the social identity provider and on your environment, you might need to make changes to the redirect URL later.
Configure the same redirect URL in the identity provider service and in the AM client.
Some providers require that you enable a specific API in their service:
-
Enable the
Gmail APIin the Google Cloud Platform. - Apple
-
You must have access to the Apple Development Program (Enterprise program is not eligible), and you must enable
Sign In With Applein the Apple Developer site. -
You must have an Elevated Developer Twitter Account to obtain a token, and you must set up an application at https://developer.twitter.com/en/portal/dashboard.
-
In the AM admin UI, go to Realms > Realm Name > Services.
-
Check if the
Social Identity Provider Serviceappears in the list of services configured for the realm.If it does not, click Add a Service, select
Social Identity Provider Servicefrom the drop-down list, and click Create. -
Ensure the Enabled switch is on.
-
Go to the Secondary Configurations tab.
AM includes scripts and configurations for several common identity providers.
-
In the Add a Secondary Configuration drop-down list, select the required identity provider.
If the required provider isn’t available, select one of the following to add a custom identity provider client:
-
Client Configuration for providers that implement the OAuth2 specification
-
Client Configuration for providers that implement the OpenID Connect specification
-
-
Provide the details of the service you registered with the social provider, such as the Client ID, the Client Secret, the Scope Delimiter (usually an empty space), and the Redirect URL.
For OAuth 2.0 social identity providers, store the client secret in a secret store for greater security.
Use the Client Secret Label Identifier to create a dynamic secret label to map to an alias for the secret.
Learn more about secrets in Map and rotate secrets.
Redirect URLs
A redirect URL is a path in AM to which the identity provider redirects the user on successful authentication. For example,
https://platform.example.com:8443/am.Depending on the social identity provider and on your environment, you might need to make changes to the redirect URL later.
Configure the same redirect URL in the identity provider service and in the AM client.
Don’t worry if you are missing some details; you can edit the configuration later after saving the client profile for the first time.
Click Create your changes to access all the configuration fields for the client.
-
Provide the client’s advanced configuration details and edit any required configuration details if needed.
Where do I find the required identity provider information?
-
Refer to the provider’s documentation.
Providers must specify their integration needs in their documentation, as well as their API endpoints.
For example, providers usually have different scopes that you can configure depending on your service’s needs.
Financial-grade providers usually also require additional security-related configuration, such as
acrvalues, PKCE-related settings, and more.Keep their documentation close while configuring the client profile.
-
Visit the provider’s
.well-knownendpoint.OAuth 2.0/OpenID Connect-compliant providers will display much of the information you need to configure the identity provider client in their
.well-knownendpoint. For example, the endpoint should expose their endpoint URLs, and the signing and encryption algorithms they support.
AM provides a default configuration for the supported social identity providers based on each provider’s requirements. Providers sometimes change their requirements over time. Make sure the settings for the provider have not changed.
The important preconfigured fields are:
-
The provider’s URLs; for example, Authentication Endpoint URL, Access Token Endpoint URL, and User Profile Service URL.
-
The OAuth Scopes field.
-
The configuration in the UI Config Properties section.
For common UI properties, refer to UI Config Properties.
-
The script selected in the Transform Script drop-down list.
This script is responsible for mapping attributes provided by the identity providers to a profile format compatible with AM.
For details, refer to Transform Script.
Some features require choosing algorithms from those supported by the provider, as well as creating secrets. Consider the following points before configuring the client:
-
Several capabilities in the identity provider client share the same secret labels. For example, signing request objects and signing client authentication JWTs.
-
Every identity provider client in a realm shares the same secrets.
Therefore, ensure that you configure features requiring secrets in a way that they’re compatible across clients in the same realm.
Learn more in /oauth2/connect/rp/jwk_uri.
For details on client configuration settings, refer to Client configuration reference.
-
-
Save your changes.
You are now ready to Configure basic social registration trees.
|
To let AM contact Internet services through a proxy, refer to Configure AM behind a reverse proxy. You can control the behavior of the connection factory that AM uses as a client of the social identity providers: Client connection handler propertiesThe following advanced server properties control different aspects of the connection factory:
They have sensible defaults configured, but if you need to change them, see Advanced Properties. |
Configure basic social registration trees
There are two nodes associated with Identity Providers:
- Select Identity Provider node
-
The Select Identity Provider node prompts the user to select a social identity provider to register or log in with, or (optionally) continue on with a local registration or login flow. When a provider is selected, the flow continues on to the Social Provider Handler node.
- Social Provider Handler node
-
The Social Provider Handler node is used in combination with the Select Identity Provider node. It communicates with the selected provider and collects the information provided after the user has authorized the service. It runs the provider’s configured normalization script to map the information into a format that AM can consume.
Next, the node uses a transformation script provided by AM called
Normalized Profile to Identityto transform the profile information into an identity object.The node then queries the identity store available for the realm to verify the user already exists. If the user exists, they are logged in. If the user does not exist, the user will need to be created.
Set up a basic social registration tree
-
In the AM admin UI, go to Realms > Realm Name > Authentication > Trees, and create a new tree.
-
Decide whether users can log in with their AM credentials, and add the relevant nodes to the tree:
-
Social authentication trees allowing local authentication might look like the following:
-
Social authentication trees enforcing social authentication login might look like the following:
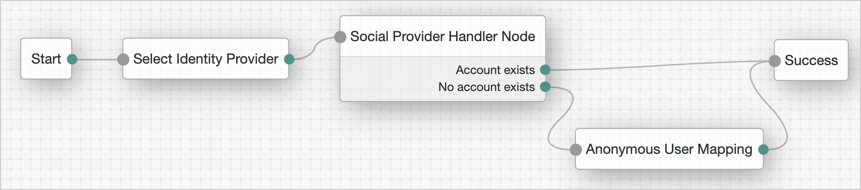
To configure either option, use the Include local authentication switch in the Select Identity Provider node.
To support both local and social authentication in the same page, you must use the Page node as shown in the example.
-
-
Configure the Social Provider Handler node:
-
In the Transformation Script field, select
Normalized Profile to Identity. This script transforms the normalized identity provider’s profile object into the appropriate user profile attributes of the realm’s identity store.If you are not using DS as the identity store, or if you added customized fields to it, you may need to modify the script.
To view the script and the available bindings, refer to normalized-profile-to-identity.js.]
-
In Client Type, select
BROWSERwhen using the AM UI, orNATIVEwhen using the ForgeRock SDKs.
-
Suspended authentication
Suspended authentication lets you save a user’s progress through an authentication tree, and later resume from the same point.
Any input provided during authentication is saved when the authentication tree is suspended, and restored when the authentication tree is resumed. This lets the authentication tree continue after closing the browser, using a different browser, or even on a different device.
When suspending an authentication tree, you provide the user with a URL they must visit to resume their authentication. That URL contains a unique identifier for retrieving the saved progress, and can only be used once. These URLs are sometimes referred to as magic links.
The Email Suspend node supports suspended authentication.
Typical use cases include passwordless authentication, and email verification during progressive profile completion.
The following example lets a user authenticate if they have forgotten their username:
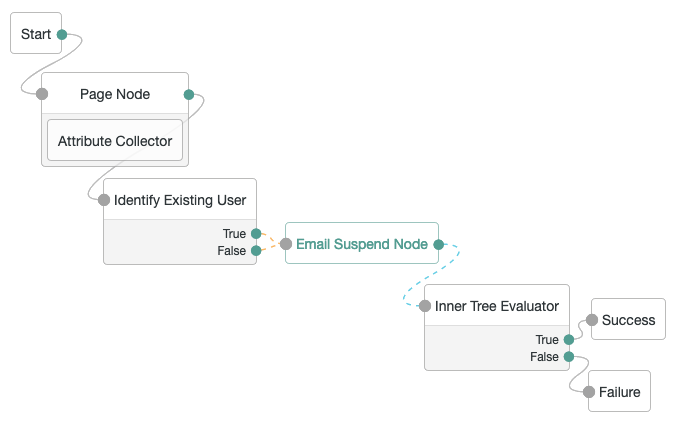
After obtaining the user’s email address in the Attribute Collector node, the example tree attempts to identify the user. Then, the tree attempts to email the user, and suspends itself.
Note that both the True and False outcomes are mapped into the Email Suspend node to reduce potential data leakage. If the username is found, it is included in the email sent to the user, along with the link to use to resume the authentication tree.
When the user follows the link, the authentication tree resumes at the Inner Tree Evaluator node, which lets the user authenticate with their recovered username and credentials.
Configure suspended authentication
You can configure the length of time an authentication session can last for in AM, so that resources can be freed up from incomplete authentications. You can also configure the length of time that a tree can be suspended.
You should set this value to the minimum reasonable time required to complete the authentication. For example, if you are sending an email, 10 minutes might be reasonable. The time allowed for suspending authentication must be the same or less than the maximum duration for the tree.
To configure these timeouts, in the AM admin UI, go to Configure > Authentication > Core Attributes > Trees. For more information about the properties, see Trees.
Add suspended authentication to custom nodes
You can enable suspended authentication in your custom nodes. For more information, see Action class.
MFA: Web authentication (WebAuthn)
WebAuthn lets users authenticate with an authenticator device, such as the fingerprint scanner on their laptop or phone. The user’s browser communicates with the authenticator device.
AM can request the browser to activate the authenticator device with certain criteria; for example:
-
The authenticator device must be built-in, not a USB device that the user can eject
-
The device must verify the user’s identity, not just the user’s presence
To use WebAuthn with AM, users must first register their authenticators. If recovery codes are enabled, users should copy their codes on successful registration.
Registration involves the selected authenticator creating, or minting, a key pair. The public key of the pair is returned to AM and stored in the user’s profile. The private key is stored securely in the authenticator itself or in the platform that manages the authenticators. The private key does not leave the client at any time.
When authenticating with WebAuthn, the authenticator device locks data with its stored private key and sends it to AM. AM verifies the data using the public key stored in the user’s profile. If the data verification succeeds and passes any attestation checks, AM considers the authentication successful.
| The user must connect over HTTPS to use WebAuthn. |
AM supports WebAuthn for the following user agents on the specified platforms:
| Browser(1) | Platform |
|---|---|
Google Chrome |
Desktop |
Android |
|
Safari |
Desktop |
iOS |
|
Microsoft Edge |
Desktop |
Mozilla Firefox |
Desktop |
(1) Latest stable versions are supported.
Create trees for WebAuthn
The example tree that follows registers the user’s device if necessary, and authenticates the user with the device. If the user has already registered their device, they only need to enter their username, and then perform the authorization gesture with their registered device to complete authentication.
If the user does not have a registered device, they must provide both their username and their password. The Data Store Decision node confirms their identity before allowing them to register their device. The user then authenticates with the new device to complete authentication.
|
The tree created here does not include user-friendly features, such as letting the user retry their password if they mistype it. |
Configure the WebAuthn Profile Encryption service
In the AM admin UI, configure the WebAuthn Profile Encryption service for the realm where you create the tree.
This service configures how AM stores registered device metadata.
-
In the AM admin UI for the realm, click Services > Add a Service.
-
Select WebAuthn Profile Encryption Service in the service type drop-down list, and create the new service configuration.
-
Accept the default configuration unless you must encrypt the device metadata in user profiles:
- Profile Storage Attribute
-
webauthnDeviceProfiles(default) - Device Profile Encryption Scheme
-
If you choose an encryption scheme, also edit the settings to access the keys.
For details, read Secrets, certificates, and keys.
Default:
No encryption of device settings.For detailed information about the available properties, refer to WebAuthn profile encryption service.
Create the WebAuthn tree
-
Configure the WebAuthn Profile Encryption service for the realm if you have not already done so.
-
In the AM admin UI, create a tree for WebAuthn under Realms > Realm Name > Authentication > Trees.
-
Add the following nodes to your tree:
-
Connect the nodes as demonstrated in the following figure:
-
On the WebAuthn Authentication node, select Allow recovery codes.
-
On the WebAuthn Registration node, select Generate recovery codes.
-
Save your changes.
Test the WebAuthn tree
-
Register a test user account unless you have already done so.
-
In an incognito browser window, browse to the WebAuthn tree.
The URL looks something like:
https://openam.example.com:8443/openam/XUI/?realm=/alpha&service=myWebAuthnTree#loginA login screen prompts for the username.
-
Enter the username for the test user account.
-
If the user does not have a registered device:
-
Enter the test user’s password when prompted.
-
Register a WebAuthn authenticator by performing an authorization gesture.
For example, press the button on a connected YubiKey or scan your fingerprint.

The browser may present a consent pop-up to allow access to the available authenticators.
When you grant consent, the browser activates the relevant authenticators, ready for registration.
If the device registration is successful, the tree returns to the WebAuthn Authentication node.
-
-
When prompted, authenticate by performing an authorization gesture with a registered device.
The UI displays the user profile page.
The dashboard page lists the registered devices that you can rename or delete.
The default name for a new WebAuthn device is
New Security Key.
Configure usernameless authentication with ForgeRock Go
With ForgeRock Go, you can create a secure and seamless login experience by authenticating with any credential on the user’s device that supports FIDO2 WebAuthn.
You can also extend passwordless authentication to include usernameless authentication with popular authenticators that support resident keys; for example, Windows Hello (biometric authenticators).
To use usernameless authentication, you must register an authenticator that supports resident keys to the user’s profile, and enable the option to associate a certificate on the device with the user’s username.
Once registered, that device can be used to authenticate the user without them having to provide their credentials; they need to select the appropriate entry to use from the list their device provides.
To configure usernameless authentication with ForgeRock Go, create a web authentication registration tree to associate a device that supports resident keys with a user. The registration tree is similar to that described in Create trees for WebAuthn.
Create a second tree that lets users authenticate to AM without entering their username or password, by using ForgeRock Go.
|
The trees created here do not include user-friendly features, such as allowing retries or redirecting for further help on failures. |
Create the ForgeRock Go registration tree
-
Configure the WebAuthn Profile Encryption service for the realm if you have not already done so.
-
In the AM admin UI, create a tree for ForgeRock Go registration under Realms > Realm Name > Authentication > Trees.
-
Add the following nodes to your tree:
-
(Optional) Scripted Decision node
When configured for ForgeRock Go, by default the WebAuthn Registration node stores the tree’s shared state variable
usernameon the device. During authentication, this value later identifies the user.Use a Scripted Decision node to customize the display name or string to be saved in the shared state.
Script to set the display name-
Next-generation
-
Legacy
var user = nodeState.get('username'); var identity = idRepository.getIdentity(user); var displayName = ''; var givenName = identity.getAttributeValues('givenName')[0]; var surname = identity.getAttributeValues('sn')[0]; var email = identity.getAttributeValues('mail')[0]; if (givenName) { displayName += givenName; } if (surname) { displayName += ' ' + surname; } if (email) { displayName += ' (' + email + ')'; } if (displayName) { nodeState.putShared('displayName', displayName); } else { nodeState.putShared('displayName', user); } action.goTo("true");javascriptvar fr = JavaImporter(org.forgerock.openam.auth.node.api.Action); var user = nodeState.get('username').asString(); var displayName = ''; var givenName = idRepository.getAttribute(user, 'givenName'); var surname = idRepository.getAttribute(user, 'sn'); var email = idRepository.getAttribute(user, 'mail'); if (givenName) { displayName += givenName.toArray()[0]; } if (surname) { displayName += ' ' + surname.toArray()[0]; } if (email) { displayName += ' (' + email.toArray()[0] + ')'; } if (displayName) { nodeState.putShared('displayName', displayName.toString()); } else { nodeState.putShared('displayName', user.toString()); } action = fr.Action.goTo("true").build();javascript -
-
Connect the nodes as demonstrated in the following figure:
If you do not use the Scripted Decision node, connect the Data Store Decision node
Trueoutput directly to the WebAuthn Registration node. -
If you use the Scripted Decision node:
-
Select your script in the Script dropdown.
-
Add the outcome of your script,
truein this example, in the Outcomes field.
-
-
On the WebAuthn Registration node:
-
Select Username to device.
-
If you do not use the Scripted Decision node, add
userNamein the Shared state attribute for display name field. -
If you use the Scripted Decision node, add the shared state variable name, such as
displayName, in the Shared state attribute for display name field.
-
-
Save your changes.
Create the ForgeRock Go authentication tree
-
Configure the WebAuthn Profile Encryption service for the realm if you have not already done so.
-
In the AM admin UI, create a tree for ForgeRock Go authentication under Realms > Realm Name > Authentication > Trees.
-
Add a WebAuthn Authentication node to your tree.
-
Connect the nodes as demonstrated in the following figure:
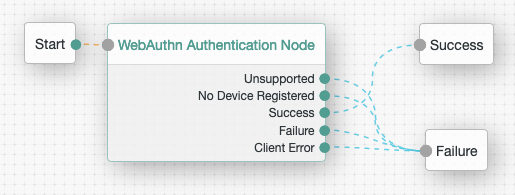
-
On the WebAuthn Authentication node, ensure Username from device is enabled.
-
Save your changes.
Register with ForgeRock Go
Follow these steps to register a device for usernameless authentication, and then authenticate with no username or password, only an authorization gesture.
-
Register a test user account unless you have already done so.
-
In an incognito browser window, browse to the ForgeRock Go registration tree.
The URL looks something like:
https://openam.example.com:8443/openam/XUI/?realm=/alpha&service=myForgeRockGoRegistrationTree#loginA login screen prompts for your credentials.
-
Sign in with the username and password of the test user.
-
If you are authenticating from a FIDO2-enabled device, it prompts you for the method to verify your identity.
For example, you might use a USB security key or a built-in biometric sensor.
Select the option to associate with the user.
-
Perform the authorization gesture of the chosen option when asked to do so.
For example, press the button on your USB security key or scan your fingerprint.
The UI displays the user profile page.
The dashboard page lists the registered devices that you can rename or delete.
Authenticate with ForgeRock Go
After registering, authenticate with ForgeRock Go without your username or password:
-
Sign out.
-
In the same browser window, browse to the ForgeRock Go authentication tree.
The URL looks something like:
https://openam.example.com:8443/openam/XUI/?realm=/alpha&service=myForgeRockGoAuthenticationTree#login -
Perform the authorization gesture of the chosen option when prompted.
A list of the accounts associated with the authentication device displays:
In this example, the user’s full name and email address appear. The Scripted Decision node gathered them during registration.
-
Select the account to sign in.
The UI displays the user profile page without you having to enter your username or password.
Configure WebAuthn trust anchors
AM 7 added support for a new CA attestation type, whereby the attestation data received from a device can be verified as authentic by using the relevant CA certificates.
If the trust chains defined by the CA certificates have CRL or OCSP entries, AM is also able to check for revocation.
To configure trust anchors in AM, you should obtain the CA-issued certificate chains for the devices you intend to verify, and make them available to AM in a secret store.
When the relevant certificate chains are in place,
configure the WebAuthn Registration node with the alias of the secret store,
and set Preferred mode of attestation to either DIRECT or INDIRECT.
Perform the following steps to enable trust anchors and achieve CA attestation for trusted devices:
-
Obtain the CA-issued certificate chains for the devices you want to verify.
You may need to consult the device manufacturer to obtain the certificate chains.
-
Import the certificate chains into a keystore:
$ keytool -import \ -file /Downloads/vendor-a-ca.crt \ -alias "vendor-a-devices" \ -storetype JCEKS \ -storepass changeit \ -keystore /path/to/openam/security/keystores/webauthnTrustStore.jceksbashThe command above imports a hypothetical trust chain from "Vendor A" into a secret store named
webauthnTrustStore.jceks, located in the default AM path for keystores,/path/to/openam/security/keystores.If the keystore does not exist, the command creates it and sets the store password to
changeit; otherwise, it adds the specified certificate to the secret store. -
Repeat the previous step until the
webauthnTrustStore.jcekssecret store contains all of the CA-issued certificate chains for the devices you want to verify. -
Ensure that the password to access the new
webauthnTrustStore.jcekssecret store is available to your AM instance; for example, by encrypting the password and adding the result to a new file namedwebauthnStorepass, in/path/to/openam/security/secrets/encrypted.For more information, see File System Secret Volumes Secret Stores.
-
In the AM admin UI, go to the realm containing the web authentication registration tree that will attempt CA-level attestation, go to Authentication > Trees, and click your registration tree.
-
Select the WebAuthn Registration Node, and in the properties pane:
-
Set the Preferred mode of attestation property to
DIRECTorINDIRECT. -
Set the Trust Store alias property to a string that identifies the trust store, and is the suffix of the secret label used for mappings; for example,
webauthnTrustStore. -
To act upon the attestation type achieved when registering a device; for example, using a script, enable the Store data in transient state property.
When you enable this property, the WebAuthn Registration Node stores the level of attestation achieved in a variable named
webauthnAttestationType, in the tree’s transient state.Use code similar to the following JavaScript to read the value of
webauthnAttestationType:var attestationLevel = transientState.get("webauthnAttestationType");javascript -
Save your changes.
For more information on the available properties, see WebAuthn Registration node.
-
-
Navigate back to the realm page, select Secret Stores, and click Add Secret Store.
-
In Secret Store ID, enter the alias you specified in the registration node earlier; for example,
webauthnTrustStore.Select the store type, specify the path to the store, and click Create.
-
Set the Store password secret label to the name of the file you created earlier with the encrypted value of the store password in; for example,
webauthnStorepass.Save your changes.
-
On the Mappings tab, click Add Mapping.
-
In Secret Label, select the secret label that begins with
am.authentication.nodes.webauthn.truststore, and has the alias you specified earlier as the suffix.For example,
am.authentication.nodes.webauthn.truststore.webauthnTrustStore. -
Enter the alias of the certificate chains you want to use for verification, and click Add.
Repeat this step to add all the aliases of certificate chains you want to use for CA-level attestation:
-
Save your changes.
Your registration tree is now ready to verify the attestation data against the list of configured certificate chains.
MFA: Push authentication
You can use push notifications as part of the authentication process in AM.
To receive push notifications when authenticating, end users must register an Android or iOS device with AM. The registered device can then be used as an additional factor when authenticating to AM. AM can send the device a push notification, which can be accepted by the ForgeRock Authenticator app. In the app, the user can allow or deny the request that generated the push notification and return the response to AM.
About push
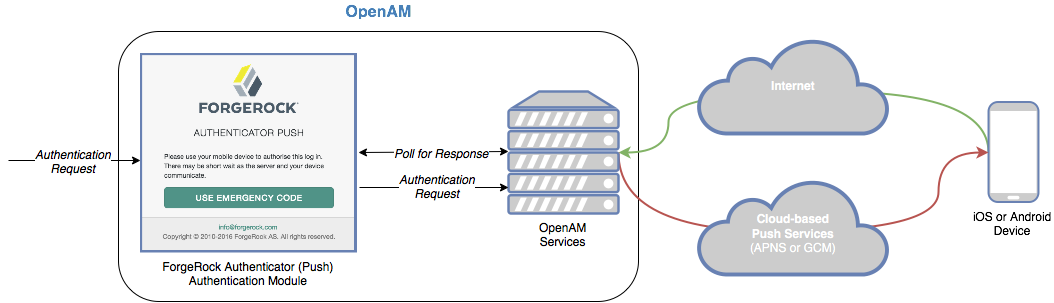
The following steps occur as a user completes a push notification journey:
-
The user provides credentials to enable AM to locate the user profile and determine if they have a registered mobile device.
-
AM prompts the user to register a mobile device if they have not done so already.
The user registers their device through the ForgeRock Authenticator application. The application supports a variety of methods to respond to push notifications from tapping a button to biometrics if the device supports them.
Registering a device stores device metadata in the user profile that is required for push notifications. AM uses the configured ForgeRock Authenticator (Push) service, which supports encrypting the metadata.
For more information, refer to Manage devices for MFA.
-
Once the user has a registered device, AM creates a push message specific to the device.
The message has a unique ID that AM stores while waiting for the response.
AM writes a pending record with the same message ID to the CTS store for redundancy should an individual server go offline during the authentication process.
-
AM sends the push message to the registered device.
AM delivers the message through the configured push notification service.
Depending on the registered device, AM uses either Apple Push Notification Services (APNS) or Google Cloud Messaging (GCM) to deliver the message.
AM begins to poll the CTS for an accepted response from the registered device.
-
The user responds to the notification through the ForgeRock Authenticator application on the device, for example, approving or rejecting the notification.
The application responds to the push notification message with the user’s choice.
-
AM verifies the message is from the correct registered device and has not been tampered with, and marks the pending record as accepted if valid.
AM detects the accepted record and redirects the user to their profile page, completing the authentication.
Implement push
The following table summarizes the tasks to perform to implement push authentication in your environment:
| Task | Resources |
|---|---|
Configure authentication Implement authentication trees where possible. If you are planning to implement passwordless push authentication, also refer to Limitations when using passwordless push authentication. |
|
Test push authentication After configuring AM, download the ForgeRock Authenticator application and test your configuration. |
Push authentication journeys
Configure authentication journeys (trees) for passwordless authentication and to receive push notifications.
When configured for passwordless authentication, the authentication flow requires the user to enter their user ID, but not their password. AM sends a push notification to their registered device to complete authentication with the ForgeRock Authenticator application.
Before implementing passwordless push authentication, consider the Limitations when using passwordless push authentication.
Configure the ForgeRock Authenticator (Push) service
In the AM admin UI, configure the ForgeRock Authenticator (Push) service for the realm where you create the tree.
This service specifies the user profile attribute that stores registered device metadata.
-
In the AM admin UI for the realm, click Services > Add a Service.
-
Select ForgeRock Authenticator (Push) Service in the service type drop-down list, and create the new service configuration.
-
Accept the default configuration unless you must encrypt the device metadata in user profiles:
- Profile Storage Attribute
-
pushDeviceProfiles(default) - Device Profile Encryption Scheme
-
If you choose an encryption scheme, also edit the settings to access the keys. For details about access to AM keys, read Secrets, certificates, and keys.
Default:
No encryption of device settings. - ForgeRock Authenticator (Push) Device Skippable Attribute Name
-
push2faEnabled(default)
For additional details, refer to the reference documentation, ForgeRock Authenticator (Push) Service.
Configure the Push Notification service
In the AM admin UI, configure the Push Notification service for the realm.
|
AM uses an external AWS service to send push notifications. Its configuration requires access keys and other metadata. As a Ping Identity customer, you have streamlined access to the required metadata. Before you start, log in to Backstage, then follow the instructions in How To Configure Service Credentials (Push Auth, Docker) in Backstage. Download the AWS credential data in JSON format and refer to that as you configure the service. |
-
In the AM admin UI for the realm, click Services > Add a Service.
-
Select Push Notification Service in the service type drop-down list.
-
Update the following fields with the data you generated on Backstage, then create the new service configuration:
- SNS Access Key ID
-
The generated Key ID; the
"accessKeyId"in the JSON - SNS Access Key Secret
-
The generated Secret; the
"accessKeySecret"in the JSON - SNS Endpoint for APNS
-
The generated APNS; the
"APNS"in the JSON - SNS Endpoint for GCM
-
The generated GCM; the
"GCM"in the JSON
You can also store the Access Key Secret in a secret store. For additional details, refer to the reference documentation, Push Notification service.
Create a push authentication journey
The procedure assumes the following:
-
Users provide user IDs and passwords as the first step of multi-factor authentication (MFA).
-
AM sends the push notification to the device as an additional factor to complete authentication.
-
You have prepared the prerequisite services, described in Configure the ForgeRock Authenticator (Push) service and Configure the Push Notification service.
-
In the AM admin UI under Realms > Realm Name > Authentication > Trees, create a tree for push notification.
-
Add the following nodes to your tree:
-
Connect the nodes as demonstrated in the following figure:
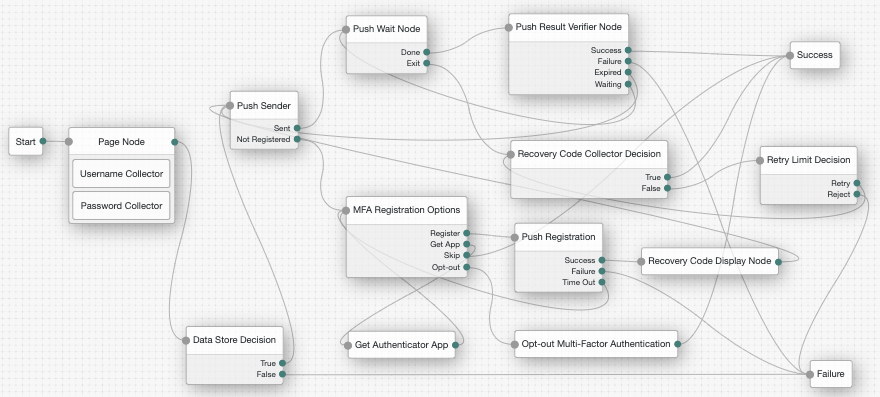 Figure 8. Example push authentication tree
Figure 8. Example push authentication treeNode connections
List of node connections Source node Outcome path Target node Page Node containing:
-
Username Collector / Platform Username
-
Password Collector / Platform Password
→
Data Store Decision
Data Store Decision
True
Push Sender
False
Failure
Push Sender
Sent
Push Wait
Not Registered
MFA Registration Options
Push Wait
Done
Push Result Verifier
Exit
Recovery Code Collector Decision
Push Result Verifier
Success
Success
Failure
Failure
Expired
Push Sender
Waiting
Push Wait
MFA Registration Options
Register
Push Registration
Get App
Get Authenticator App
Skip
Success
Opt-out
Opt-out Multi-Factor Authentication
Recovery Code Collector Decision
True
Success
False
Retry Limit Decision
Push Registration
Success
Recovery Code Display Node
Failure
Failure
Time Out
MFA Registration Options
Get Authenticator App
→
MFA Registration Options
Opt-out Multi-Factor Authentication
→
Success
Retry Limit Decision
Retry
Recovery Code Collector Decision
Reject
Failure
Recovery Code Display Node
→
Push Sender
-
-
Save your changes.
-
Test your authentication tree as follows:
-
Copy and paste the Preview URL into a browser in incognito mode. The URL looks something like:
https://openam.example.com:8443/openam/XUI/?realm=alpha&authIndexType=service&authIndexValue=myPushAuthTree.A login screen prompting you to enter your user ID and password appears.
-
Verify that you can use the ForgeRock Authenticator application to perform MFA.
If the authentication tree is correctly configured, authentication is successful and AM displays the user profile page. For details, refer to Test push authentication.
-
-
Create a passwordless authentication journey
The procedure assumes the following:
-
Users provide only their user IDs as the first step of MFA.
-
Users have pre-registered a device for push authentication.
-
AM sends the push notification to the device as an additional factor to complete authentication, without the need for the user’s password.
-
You have prepared the prerequisite services, described in Configure the ForgeRock Authenticator (Push) service and Configure the Push Notification service.
-
In the AM admin UI under Realms > Realm Name > Authentication > Trees, create a tree for passwordless authentication.
-
Add the following nodes to your tree:
-
Connect the nodes as demonstrated in the following figure:
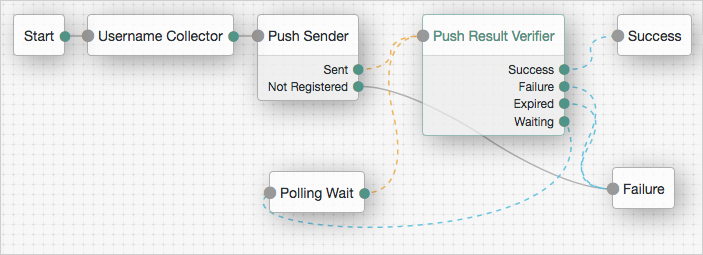 Figure 9. Passwordless push authentication
Figure 9. Passwordless push authentication -
Save your changes.
-
Test your authentication tree as follows:
-
Copy and paste the Preview URL into a browser in incognito mode. The URL looks something like:
https://openam.example.com:8443/openam/XUI/?realm=alpha&authIndexType=service&authIndexValue=myPasswordlessAuthTree.A login screen appears, prompting you to enter your user ID.
-
Verify that you can use the ForgeRock Authenticator application to perform MFA.
If the authentication tree is correctly configured, authentication is successful and AM displays the user profile page without the user entering their password.
For details, refer to Test push authentication.
-
-
Test push authentication
AM presents you with a page for entering only your user ID, or user ID and password. After you provide those credentials, AM verifies them. If your credentials are valid and the account has a device registered for push notifications, AM sends a push notification to the registered device.
If the user does not yet have a device registered for push authentication, refer to Register.
|
The device needs access to the Internet to receive push notifications, and the AM server must be able to receive responses from the device. |
Receive push notifications
On your registered device, you receive a push notification from AM. Depending on the state of the device and the ForgeRock Authenticator application, respond to the notification as follows:
-
Unlock the device, if necessary, when you receive a device notification from the application.
The ForgeRock Authenticator application opens and displays the push notification.
-
If the device is unlocked, but the ForgeRock Authenticator application is not open, select the device notification to open the application and display the push notification.
-
Open the ForgeRock Authenticator application to respond quickly to notifications.
Approve requests
How you approve requests depends on the ForgeRock Authenticator application settings, and on what the device supports.
Default settings for push notifications use a simple pop up in the application, similar to the following:
Deny requests
Deny the request by tapping the cancel icon in the top-right of the screen or, if Touch ID or face recognition are enabled, tap the Reject button.
|
If you do not approve or deny the request on the registered device, the AM Push Authentication page times out and authentication fails. You can configure this through the Message Timeout in the Push Sender node for the tree. |
Register
If your credentials are valid but your profile is missing the metadata for a registered device registered, the MFA Registration Options node of the tree governs what happens:
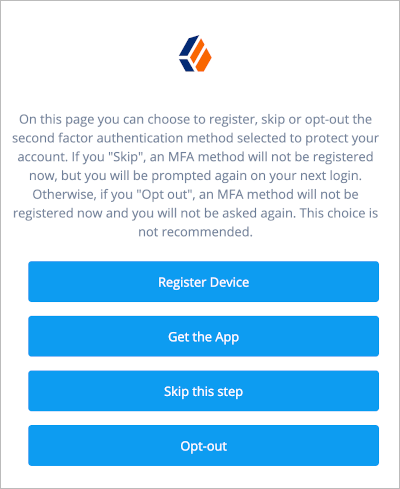
- Register Device
-
Configure the journey to continue to the Push Registration node.
When completing the journey, scan the QR code it displays with the ForgeRock Authenticator application.
For additional details, refer to Register the ForgeRock Authenticator for multi-factor authentication.
- Get the application
-
Configure the journey to continue to the Get Authenticator App node.
When completing the journey, follow the link needed to obtain the ForgeRock Authenticator application for your device.
- Skip this step
-
Displayed only if the node configuration allows the user to skip. (Optional) In the example journey, skipping is linked to the Success node.
- Opt-out
-
Configure the journey to continue to the Opt-out Multi-Factor Authentication node and let the user not use push.
In the example journey, opting out is linked to the Success node.
Configure successful registration to return to the Push Sender node, which starts the actual push notification stage of the journey, and the user can receive push notifications.
Limitations when using passwordless push authentication
When authenticating to a passwordless push authentication journey, the user enters their user ID, but not their password. AM sends a push notification to their device to complete the authentication.
Be aware of the following limitations when you implement passwordless push authentication:
-
Unsolicited push messages could be sent to a user’s registered device by anyone who knew or was able to guess their user ID.
-
If a malicious user attempted to authenticate by using push at the same time as a legitimate user, the legitimate user might unintentionally approve the malicious attempt. This is because push notifications only contain the username and issuer in the text, and it is not easy to determine which notification relates to which authentication attempt.
Consider using push notifications as part of MFA, and not on their own.
MFA: Open Authentication (OATH)
The ForgeRock Authenticator (OATH) module supports HMAC one-time password (HOTP) and time-based one-time password (TOTP) authentication as defined in the OATH standard protocols for HOTP (RFC 4226) and TOTP (RFC 6238). Both HOTP and TOTP authentication require an OATH-compliant device that can provide the password.
About one-time password support
HOTP authentication generates the one-time password (OTP) every time the user requests a new password on their device. The device tracks the number of times the user requests a new one-time password with a counter. The one-time password displays for a period of time you designate in the setup, so the user may be further in the counter on their device than on their account.
AM will resynchronize the counter when the user finally logs in. To accommodate this, you set the number of passwords a user can generate before their device cannot be resynchronized. For example, if you set the number of HOTP Window Size to 50 and someone presses the button 30 times on the user’s device to generate a new password, the counter in AM will review the passwords until it reaches the one-time password entered by the user. If someone presses the button 51 times, you will need to reset the counter to match the number on the device’s counter before the user can log in to AM. HOTP authentication doesn’t check earlier passwords, so if the user attempts to reset the counter on their device, they won’t be able to log in until you reset the counter in AM to match their device. For more information, refer to Reset registered devices over REST.
TOTP authentication constantly generates a new one-time password based on a time interval you specify. The device tracks the last several passwords generated and the current password. The TOTP Time Steps setting configures the number of passwords tracked. The Last Login Time setting monitors the time when a user logs in to make sure that user is not logged in several times within the present time period. The TOTP Time-Step Interval should not be so long as to lock users out, with a recommended time of 30 seconds.
Create a tree for one-time password authentication
To create an example authentication tree that uses OATH authentication, perform the following steps:
-
In the AM admin UI, select the realm that will contain the authentication tree.
-
Select Authentication > Trees, and click +Create Tree.
-
Type a name for your tree in the New Tree page; for example,
myAuthTree, and click Create.The authentication tree designer page is displayed with default Start, Failure, and Success nodes.
For information about using the authentication tree designer, see Create an authentication tree.
-
Add the following nodes to the designer area:
-
Connect the nodes as shown:
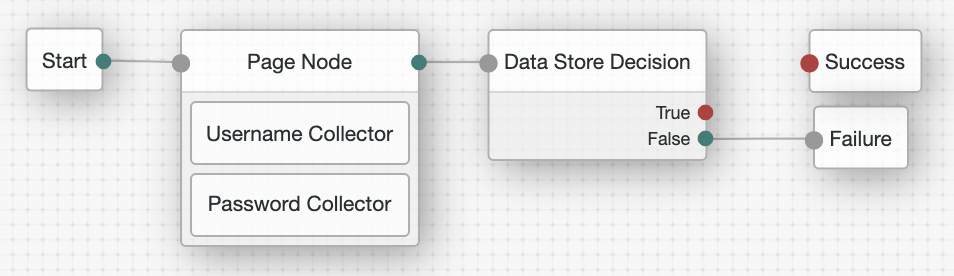
-
Type 'OATH' to filter the list of nodes in the Components panel box:
-
Drag an OATH Token Verifier node and an OATH Registration node onto the designer area.
-
For both OATH nodes, set the OATH Algorithm property to TOTP, and connect to the existing nodes as follows:
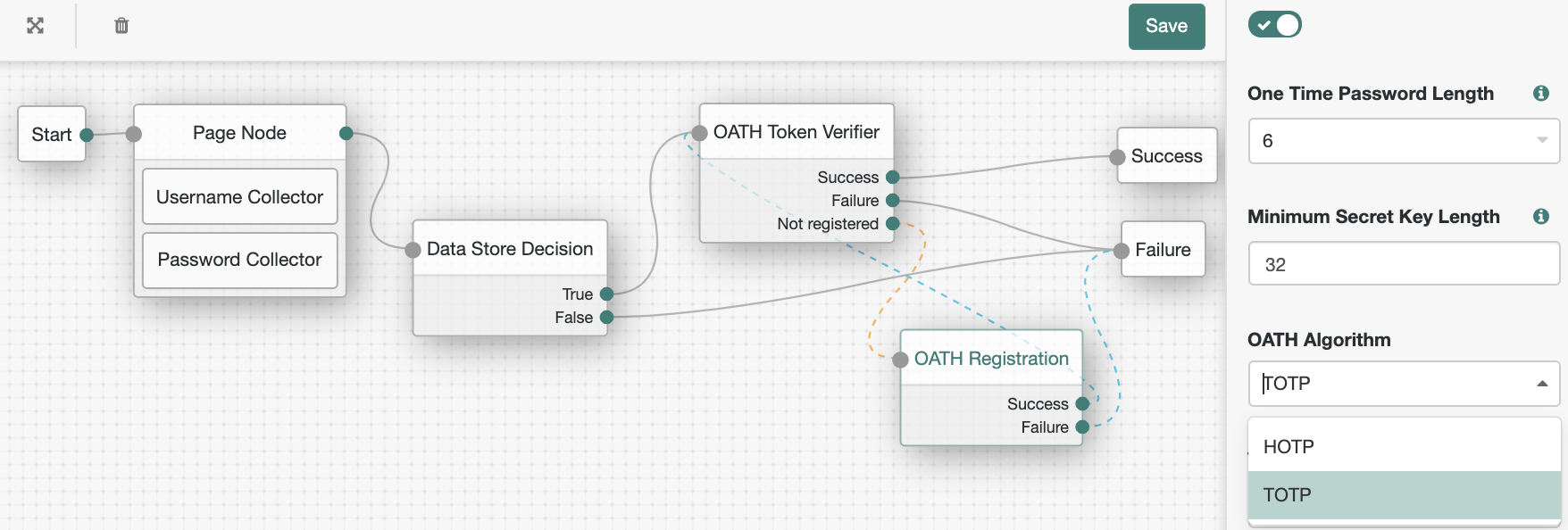
The value for OATH Algorithm must be the same for both nodes. For this example, select TOTP to generate a new OTP at a specified time step interval.
-
Save your changes.
Note that the tree you have created is a simple example for the purposes of demonstrating a basic OATH authentication journey. In a production environment, you could include additional nodes, such as:
- MFA Registration Options node
-
Provides options for users to register a multi-factor authentication device, get the authenticator app, or skip the registration process.
- Opt-out Multi-Factor Authentication node
-
Sets an attribute in the user’s profile which lets them skip multi-factor authentication.
- Recovery Code Display node
-
Lets a user view recovery codes to use in case they have lost or damaged their registered authenticator device.
- Retry Limit Decision node
-
Lets a journey loop a specified number of times, for example, to allow a user to retry entering their OATH token.
For information about how to configure these nodes, see Authentication nodes configuration reference.
-
Test your authentication tree as follows:
-
Log out of AM, and then go to a URL similar to the following:
https://openam.example.com:8443/openam/XUI/?realm=alpha&service=myAuthTree#login -
Log in using the username and password. For example, enter
demo, and the passwordCh4ng31t. -
On successful login, if the screen displays a QR code, you will need to register your device.
To register the device with the ForgeRock Authenticator, follow the instructions in The ForgeRock Authenticator application.
-
Follow the procedure described in Authenticate with a one-time password to verify that you can authenticate using the ForgeRock Authenticator app.
-
Authenticate with a one-time password
This example task assumes the following prerequisites:
-
The authentication tree is set up as described in Create a tree for one-time password authentication.
-
You have successfully logged in with valid credentials.
-
You have registered your device for ForgeRock Authenticator (OATH) authentication.
Follow these steps to complete one-time password (OTP) authentication:
-
On your registered device, open the ForgeRock Authenticator app, and then tap the OTP section for the account matching the user ID:
-
Note the OTP that is displayed on the screen. This is automatically refreshed at an interval defined in the OATH Token Verifier node. If the animated timer indicates the OTP is close to expiry, wait until a new OTP is generated.
-
On the ForgeRock Authenticator (OATH) page in AM, enter the OTP that the authenticator app generated on your phone, and click Submit:

AM displays the user’s profile page.
Manage devices for MFA
Multi-factor authentication requires you to register a device, which is used as an additional factor when you log in to AM.
The following table summarizes different tasks related to devices used for multi-factor authentication:
| Task | Resources |
|---|---|
Learn about the ForgeRock Authenticator Download the ForgeRock Authenticator app, which supports push authentication notifications and one-time passwords, and register it in AM. |
|
Recover user accounts Learn how to recover a user account when the user has lost their registered device, or when their device has become out of sync with AM. |
|
Reset registered devices In some scenarios, for example, when users are not able to access their recovery codes, you can reset their registered devices to allow them to register again. |
|
List registered devices Learn how to list devices registered to a user. |
|
MFA details are stored in the following profile attributes:
You can access these attributes in scripts in the same way you access other profile attributes. |
The ForgeRock Authenticator application
The ForgeRock Authenticator application supports push authentication notifications and one-time passwords.
Download and install the ForgeRock Authenticator application to perform multi-factor authentication. The application is available for both Android and iOS devices, and is free to download from:
|
To build your own authenticator application, integrate the ForgeRock Authenticator module using ForgeRock SDKs. |
Register the ForgeRock Authenticator for MFA
Register the ForgeRock Authenticator application to use it as an additional factor when logging in.
The ForgeRock Authenticator application supports registration of multiple accounts and multiple different authentication methods in each account, such as push notifications and one-time passwords.
For information on registering Web Authentication (WebAuthn) devices with AM, refer to Create trees for WebAuthn.
You register the ForgeRock Authenticator application once per authentication method with an identity provider. For example, if one tree uses push notifications and another uses one-time passwords, you must register the application separately for push notifications and one-time passwords.
The ForgeRock Authenticator application must access the internet to register for push notifications. Registering for one-time password authentication does not require a connection to the internet.
-
When accessing a protected resource that requires multi-factor authentication, AM prompts you to register a device, and displays a QR code screen:

-
If you are logging in on the device and cannot scan the screen, click the On a mobile device? link to launch the application and register the device, bypassing the QR code.
-
If you are logging in on a computer, start the ForgeRock Authenticator application and click its plus icon () to register the device.
The screen on the device changes to an interface similar to your camera app.
Scan the QR code with the ForgeRock authenticator app.
The application displays the account you registered in the list of accounts.
-
-
After registering your device, you MUST make a copy of the recovery codes for the account.
Store the recovery codes separately from your device. The recovery codes will never be displayed again. They serve as one time verification codes to log in if your registered device is lost, stolen, or broken.
When you have safely stored the recovery codes for your newly registered push device, click Done.
-
If prompted, respond to the push notification or enter a one-time password from the app.
Your device is now registered. You can use it to perform multi-factor authentication.
Recover after replacing a lost device
If you register a device with AM and then lose it, you must authenticate to AM using a recovery code. After deleting the lost device, you can register a new device.
-
Access the list of recovery codes you saved when registering the lost device.
If you did not save the recovery codes when you registered the device, contact your administrator to remove the device from your user profile instead of following these steps.
Administrators can refer to Reset registered devices over REST for details.
-
Begin to sign in as you normally would.
When prompted to use a multi-factor option, click the Use Recovery Code link.
-
Enter the recovery code when prompted.
Because recovery codes are valid for a single use only, remove the code you used from your list.
AM lets you sign in to access your profile page.
-
Under Dashboard > Authentication Devices, click the context menu button for the lost device, and click Delete.
-
Register your new device by signing out, then accessing the protected resource that requires MFA.
When registering for push notifications or one-time passwords, refer to The ForgeRock Authenticator application.
Recover after a device becomes out of sync
A device that generates one-time passwords can get out of sync with the OATH authentication service in some cases. If you repeatedly enter valid one-time passwords that appear to be valid passwords, but AM rejects the passwords as unauthorized, your device is likely out of sync.
To resynchronize your device, you must authenticate with a recovery code, and register the device again. Follow the steps in Recover after replacing a lost device.
If you did not save the recovery codes when you registered the device, contact your administrator to remove the device from your user profile instead.
Reset registered devices over REST
As described in Recover after replacing a lost device, a user who has lost a mobile phone registered with AM can register a replacement device by authenticating using a recovery code, deleting their existing device, and then registering a new device.
Additional support is required for users who lose mobile devices but did not save their recovery codes when they initially registered the device, and for users who have used up all their recovery codes.
AM provides a REST API to reset a device profile by deleting information about a user’s registered device. Both the user and administrator accounts can use the REST API to reset a device profile. Administrators can:
-
Provide authenticated users with a self-service page that calls the REST API to reset their devices.
-
Call the REST API themselves to reset a user’s device profiles.
-
Call the REST API themselves to reset a device that is out of sync, where the HOTP counter exceeds the HOTP threshold window and requires a reset.
When making a REST API call, specify the realm in the path component of the endpoint.
You must specify the entire hierarchy of the realm, starting at the Top Level Realm.
Prefix each realm in the hierarchy with the realms/ keyword.
For example, /realms/root/realms/customers/realms/europe.
Reset OATH devices
To reset a user’s OATH device profile,
send an HTTP POST request to the /users/user/devices/2fa/oath?_action=reset endpoint.
The following example resets the OATH devices of a user named myUser in a realm called alpha:
$ curl \
--request POST \
--header "Content-Type: application/json" \
--header "Accept-API-Version: resource=1.0" \
--header "iplanetDirectoryPro: AQIC5w…2NzEz*" \
--data '{}' \
'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/users/myUser/devices/2fa/oath?_action=reset'
{
"result":true
}The reset action deletes the OATH device profile, which by default has a limit of one profile per device,
and sets the Select to Enable Skip option to its default value of Not Set.
Reset push devices
To reset push devices over REST, send an HTTP POST request to the /users/user/devices/2fa/push?_action=reset endpoint.
The following example resets push devices for a user named myUser in a realm called alpha:
$ curl \
--request POST \
--header "Content-Type: application/json" \
--header "Accept-API-Version: resource=1.0" \
--header "iplanetDirectoryPro: AQIC5w…2NzEz*" \
--data '{}' \
'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/users/myUser/devices/2fa/push?_action=reset'
{
"result":true
}Delete WebAuthn devices
The reset action is not implemented on the webauthn endpoint.
You can delete a WebAuthn device over REST as follows:
-
Retrieve a list of WebAuthn devices associated with a user by querying the
users/user/devices/2fa/webauthnendpoint.The following example retrieves a list of WebAuthn devices for a user named
myUserin a realm calledalpha:$ curl \ --request GET \ --header "iplanetDirectoryPro: AQIC5w…2NzEz*" \ 'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/users/myUser/devices/2fa/webauthn?_queryFilter=true' { "result": [ { "_id": "ff1db8bf-d2d7-46e1-926a-568b877f87a5", "_rev": "163664231", "deviceName": "New Security Key", "uuid": "ff1db8bf-d2d7-46e1-926a-568b877f87a5", "deviceManagementStatus": false } ], "resultCount": 1, "pagedResultsCookie": null, "totalPagedResultsPolicy": "NONE", "totalPagedResults": -1, "remainingPagedResults": -1 }bash -
Delete the required WebAuthn device from the user by sending an HTTP DELETE request to the
users/user/devices/2fa/webauthn/device-idendpoint, including the ID of the WebAuthn device you want to delete:$ curl \ --request DELETE \ --header "Accept-API-Version: resource=1.0" \ --header "iplanetDirectoryPro: AQIC5w…2NzEz*" \ 'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/users/myUser/devices/2fa/webauthn/ff1db8bf-d2d7-46e1-926a-568b877f87a5' { "_id": "ff1db8bf-d2d7-46e1-926a-568b877f87a5", "_rev": "1642022518", "uuid": "ff1db8bf-d2d7-46e1-926a-568b877f87a5", "recoveryCodes": [ ... ], "credentialId": "XGJpYNYv4AHG9sHHgxFfTw", "algorithm": "SHA256withECDSA", "deviceName": "New Security Key", "key": { "kty": "EC", "x": "zMDAfFwRQR_5HIGfK1iJQ0kYwtudesx_UXocoBVrWbo", "y": "UgRBOBlpq6QYsXlqfHDzY8XNv-5DEMajRp9_3klkhDU", "crv": "P-256" } }bash -
Repeat step 2 to delete additional WebAuthn devices for the user, if needed.
Reset bound devices
To delete all bound devices for a user, send an HTTP POST request to the /users/user/devices/2fa/binding?_action=reset endpoint. Learn more about binding devices to a user profile in device binding.
The following example deletes bound devices for a user named myUser in a realm called alpha:
$ curl \
--request POST \
--header "Content-Type: application/json" \
--header "Accept-API-Version: resource=1.0" \
--header "iplanetDirectoryPro: AQIC5w…2NzEz*" \
--data '{}' \
'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/users/myUser/devices/2fa/binding?_action=reset'
{
"result":true
}|
Deleting a bound device on the server does not remove the private keys from the device. Instead, you can use the ForgeRock SDKs to remove the bound device from the server, and then remove the keys from the device. Refer to Unbind devices by deleting keys. |
List registered devices over REST
AM provides a REST API to retrieve information about MFA devices registered to a user.
When making a REST API call, specify the realm in the path component of the endpoint.
You must specify the entire hierarchy of the realm, starting at the Top Level Realm.
Prefix each realm in the hierarchy with the realms/ keyword.
For example, /realms/root/realms/customers/realms/europe.
List OATH devices
To return a list of OATH devices registered to a user, query the users/user/devices/2fa/oath endpoint.
The following example lists the OATH devices for a user named myUser in a realm called alpha:
$ curl \
--request GET \
--header "iplanetDirectoryPro: AQIC5w…2NzEz*" \
'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/users/myUser/devices/2fa/oath?_queryFilter=true'
{
"result" : [ {
"_id" : "ff1db8bf-d2d7-46e1-926a-568b877f87a5",
"_rev" : "172031596",
"deviceName" : "OATH Device",
"uuid" : "ff1db8bf-d2d7-46e1-926a-568b877f87a5",
"deviceManagementStatus" : false
} ],
"resultCount" : 1,
"pagedResultsCookie" : null,
"totalPagedResultsPolicy" : "NONE",
"totalPagedResults" : -1,
"remainingPagedResults" : -1
}List push devices
To return a list of push devices registered to a user, query the users/user/devices/2fa/push endpoint.
The following example lists the push devices for a user named myUser in a realm called alpha:
$ curl \
--request GET \
--header "iplanetDirectoryPro: AQIC5w…2NzEz*" \
'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/users/myUser/devices/2fa/push?_queryFilter=true'
{
"result" : [ {
"_id" : "ff1db8bf-d2d7-46e1-926a-568b877f87a5",
"_rev" : "172031596",
"deviceName" : "Push Device",
"uuid" : "ff1db8bf-d2d7-46e1-926a-568b877f87a5",
"deviceManagementStatus" : false
} ],
"resultCount" : 1,
"pagedResultsCookie" : null,
"totalPagedResultsPolicy" : "NONE",
"totalPagedResults" : -1,
"remainingPagedResults" : -1
}List WebAuthn devices
To return a list of WebAuthn devices registered to a user, query the users/user/devices/2fa/webauthn endpoint.
The following example lists the WebAuthn devices for a user named myUser in a realm called alpha:
$ curl \
--request GET \
--header "iplanetDirectoryPro: AQIC5w…2NzEz*" \
'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/users/myUser/devices/2fa/webauthn?_queryFilter=true'
{
"result": [
{
"_id": "ff1db8bf-d2d7-46e1-926a-568b877f87a5",
"_rev": "163664231",
"deviceName": "New Security Key",
"uuid": "ff1db8bf-d2d7-46e1-926a-568b877f87a5",
"deviceManagementStatus": false
}
],
"resultCount": 1,
"pagedResultsCookie": null,
"totalPagedResultsPolicy": "NONE",
"totalPagedResults": -1,
"remainingPagedResults": -1
}List bound devices
To return a list of bound devices for a user, query the users/user/devices/2fa/binding endpoint. Learn more about binding devices to a user profile in device binding.
The following example lists the bound devices for a user named myUser in a realm called alpha:
$ curl \
--request GET \
--header "iplanetDirectoryPro: AQIC5w…2NzEz*" \
'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/users/myUser/devices/2fa/binding?_queryFilter=true'
{
"result": [
{
"_id": "ff1db8bf-d2d7-46e1-926a-568b877f87a5",
"_rev": "192142989",
"createdDate": 1715182923119,
"lastAccessDate": 1715182923183,
"deviceId": "e2e84b5d2a927abdcb85570bac9701c390a92751",
"deviceName": "iOS Device",
"uuid": "ff1db8bf-d2d7-46e1-926a-568b877f87a5",
"key": {
...
},
"deviceManagementStatus": false
}
],
"resultCount": 1,
"pagedResultsCookie": null,
"totalPagedResultsPolicy": "NONE",
"totalPagedResults": -1,
"remainingPagedResults": -1
}CAPTCHA support
CAPTCHA is a way to challenge a user to verify that they are human, and includes a number of different services. Choose the CAPTCHA service that best suits your requirements. The default configuration in the CAPTCHA node is for Google’s reCAPTCHA service. You must provide a CAPTCHA Site Key and CAPTCHA Secret Key to use the node.
Test the CAPTCHA node
ForgeRock provides a Postman collection to configure AM to test the CAPTCHA node. The Postman collection contains the queries to demonstrate the CAPTCHA node with reCAPTCHA V2, V3 and with hCaptcha. Before you start, set up a reCAPTCHA V2 and V3 site, and an hCaptcha site, and copy their site and secret keys.
-
Download and install Postman.
-
Download the ForgeRock CAPTCHA Collection.
-
Import the collection into Postman:
-
Select File > Import … > Upload Files.
-
Select the CAPTCHA collection, and click Open, then click Import.
-
-
Change the collection variables to suit your environment:
-
On the Collections tab, select the ForgeRock CAPTCHA Collection.
-
Click on the Variables tab, and set the value of at least the following variables:
-
URL_base -
admin_password -
demo_username -
demo_password
-
-
Click Update to save your changes.
You are ready to run the collection.
-
-
After creating the authentication trees, visit the following URLs in your browser to demonstrate the login flow for each CAPTCHA type:
-
URL_base/XUI/?realm=sub_realm&service=recaptchav3
-
URL_base/XUI/?realm=sub_realm&service=recaptchav2
-
URL_base/XUI/?realm=sub_realm&service=hcaptcha
Use the demo_username and demo_password to log in.
-
Reference
This reference covers settings and the scripting API for authentication in AM.
For global services and global authentication reference, see Services configuration.
Core authentication attributes
Every AM realm has a set of authentication properties that applies to all authentication performed to that realm. The settings are referred to as core authentication attributes.
To configure core authentication attributes for an entire AM deployment, go to Configure > Authentication in the AM admin UI, and click Core Attributes.
To override the global core authentication configuration in a realm, go to Realms > Realm Name > Authentication > Settings in the AM admin UI.
amster service name: Authentication
ssoadm service name: iPlanetAMAuthService
Global Attributes
The following properties are available under the Global Attributes tab:
- Pluggable Authentication Module Classes
-
Lists the authentication modules classes available to AM. If you have custom authentication modules, add classes to this list that extend from the
com.sun.identity.authentication.spi.AMLoginModuleclass.For more information about custom authentication modules, see Creating a Custom Authentication Module.
This setting applies only to modules within authentication chains.
amsterattribute:authenticatorsssoadmattribute:iplanet-am-auth-authenticators - LDAP Connection Pool Size
-
Sets a minimum and a maximum number of LDAP connections to be used by any authentication module that connects to a specific directory server. This connection pool is different than the SDK connection pool configured in
serverconfig.xmlfile.Format is
host:port:minimum:maximum.This attribute is for LDAP and Membership authentication modules only.
amsterattribute:ldapConnectionPoolSizessoadmattribute:iplanet-am-auth-ldap-connection-pool-size - Default LDAP Connection Pool Size
-
Sets the default minimum and maximum number of LDAP connections to be used by any authentication module that connects to any directory server. This connection pool is different than the SDK connection pool configured in
serverconfig.xmlfile.Format is
minimum:maximum.When tuning for production, start with 10 minimum, 65 maximum. For example,
10:65.This attribute is for LDAP and Membership authentication modules only.
amsterattribute:ldapConnectionPoolDefaultSizessoadmattribute:iplanet-am-auth-ldap-connection-pool-default-size - Remote Auth Security
-
When enabled, AM requires the authenticating application to send its SSO token. This allows AM to obtain the username and password associated with the application.
amsterattribute:remoteAuthSecurityEnabledssoadmattribute:sunRemoteAuthSecurityEnabled - Keep Post Process Objects for Logout Processing
-
When enabled, AM stores instances of post-processing classes into the user session. When the user logs out, the original post-processing classes are called instead of new instances. This may be required for special logout processing.
Enabling this setting increases the memory usage of AM.
amsterattribute:keepPostProcessInstancesssoadmattribute:sunAMAuthKeepPostProcessInstances
Core
The following properties are available under the Core tab:
- Administrator Authentication Configuration
-
Specifies the default authentication chain or tree used when an administrative user, such as
amAdmin, logs in to the AM admin UI.ssoadmattribute:iplanet-am-auth-admin-auth-module - Organization Authentication Configuration
-
Specifies the default authentication chain or tree used when a non-administrative user logs in to AM.
amsterattribute:orgConfigssoadmattribute:iplanet-am-auth-org-config
User Profile
The following properties are available under the User Profile tab:
User Profile-
Specifies whether a user profile needs to exist in the user data store, or should be created on successful authentication. The possible values are:
true. Dynamic.-
After successful authentication, AM creates a user profile if one does not already exist. AM then issues the SSO token. AM creates the user profile in the user data store configured for the realm.
createAlias. Dynamic with User Alias.-
After successful authentication, AM creates a user profile that contains the
User Alias Listattribute, which defines one or more aliases for mapping a user’s multiple profiles. ignore. Ignored.-
After successful authentication, AM issues an SSO token regardless of whether a user profile exists in the data store. The presence of a user profile is not checked.
Any functionality which needs to map values to profile attributes, such as SAML or OAuth 2.0, will not operate correctly if the User Profile property is set to
ignore. false. Required.-
After successful authentication, the user must have a user profile in the user data store configured for the realm in order for AM to issue an SSO token.
ssoadmattribute:iplanet-am-auth-dynamic-profile-creation. Set this attribute’s value to one of the following:true,createAlias,ignore, orfalse.
- User Profile Dynamic Creation Default Roles
-
Specifies the distinguished name (DN) of a role to be assigned to a new user whose profile is created when either the
trueorcreateAliasoptions are selected under the User Profile property. There are no default values. The role specified must be within the realm for which the authentication process is configured.This role can be either an AM or Sun DSEE role, but it cannot be a filtered role. If you wish to automatically assign specific services to the user, you have to configure the Required Services property in the user profile.
This functionality is deprecated.
amsterattribute:defaultRolessoadmattribute:iplanet-am-auth-default-role - Alias Search Attribute Name
-
After a user is successfully authenticated, the user’s profile is retrieved. AM first searches for the user based on the data store settings. If that fails to find the user, AM will use the attributes listed here to look up the user profile. This setting accepts any data store specific attribute name.
amsterattribute:aliasAttributeNamessoadmattribute:iplanet-am-auth-alias-attr-nameIf the
Alias Search Attribute Nameproperty is empty, AM uses theiplanet-am-auth-user-naming-attrproperty from theiPlanetAmAuthService. Theiplanet-am-auth-user-naming-attrproperty is only configurable through thessoadmcommand-line tool and not through the AM admin UI.$ ssoadm get-realm-svc-attrs \ --adminid uid=amAdmin,ou=People,dc=openam,dc=forgerock,dc=org \ --password-file PATH_TO_PWDFILE \ --realm REALM \ --servicename iPlanetAMAuthService$ ssoadm set-realm-svc-attrs \ --adminid uid=amAdmin,ou=People,dc=openam,dc=forgerock,dc=org \ --password-file PATH_TO_PWDFILE \ --realm REALM \ --servicename iPlanetAMAuthService \ --attributevalues iplanet-am-auth-user-naming-attr=SEARCH_ATTRIBUTEbash
Account Lockout
The following properties are available under the Account Lockout tab:
- Login Failure Lockout Mode
-
When enabled, AM deactivates the LDAP attribute defined in the Lockout Attribute Name property in the user’s profile upon login failure. This attribute works in conjunction with the other account lockout and notification attributes.
amsterattribute:loginFailureLockoutModessoadmattribute:iplanet-am-auth-login-failure-lockout-mode - Login Failure Lockout Count
-
Defines the number of attempts that a user has to authenticate within the time interval defined in Login Failure Lockout Interval before being locked out.
amsterattribute:loginFailureCountssoadmattribute:iplanet-am-auth-login-failure-count - Login Failure Lockout Interval
-
Defines the time in minutes during which failed login attempts are counted. If one failed login attempt is followed by a second failed attempt within this defined lockout interval time, the lockout count starts, and the user is locked out if the number of attempts reaches the number defined by the Login Failure Lockout Count property. If an attempt within the defined lockout interval time proves successful before the number of attempts reaches the number defined by the Login Failure Lockout Count property, the lockout count is reset.
amsterattribute:loginFailureDurationssoadmattribute:iplanet-am-auth-login-failure-duration - Email Address to Send Lockout Notification
-
Specifies one or more email addresses to which notification is sent if a user lockout occurs.
Separate multiple addresses with spaces, and append
|locale|charsetto addresses for recipients in non-English locales.amsterattribute:lockoutEmailAddressssoadmattribute:iplanet-am-auth-lockout-email-address - Warn User After N Failures
-
Specifies the number of authentication failures after which AM displays a warning message that the user will be locked out.
ssoadmattribute:iplanet-am-auth-lockout-warn-user - Login Failure Lockout Duration
-
Defines how many minutes a user must wait after a lockout before attempting to authenticate again. Entering a value greater than 0 enables duration lockout and disables persistent (physical) lockout. Duration lockout means the user’s account is locked for the number of minutes specified. The account is unlocked after the time period has passed.
amsterattribute:lockoutDurationssoadmattribute:iplanet-am-auth-lockout-duration - Lockout Duration Multiplier
-
For duration lockout, this attribute defines a multiplier that is applied to the value of the Login Failure Lockout Duration for each successive lockout. For example, if Login Failure Lockout Duration is set to 3 minutes, and the Lockout Duration Multiplier is set to 2, the user is locked out of the account for 6 minutes. After the 6 minutes has elapsed, if the user again provides the wrong credentials, the lockout duration is then 12 minutes. With the Lockout Duration Multiplier, the lockout duration is incrementally increased based on the number of times the user has been locked out.
amsterattribute:lockoutDurationMultiplierssoadmattribute:sunLockoutDurationMultiplier - Lockout Attribute Name
-
Defines the LDAP attribute used for physical lockout. The default attribute is
inetuserstatus, although the field in the AM admin UI is empty. The Lockout Attribute Value field must also contain an appropriate value.amsterattribute:lockoutAttributeNamessoadmattribute:iplanet-am-auth-lockout-attribute-name - Lockout Attribute Value
-
Specifies the action to take on the attribute defined in Lockout Attribute Name. The default value is
inactive, although the field in the AM admin UI is empty. The Lockout Attribute Name field must also contain an appropriate value.amsterattribute:lockoutAttributeValuessoadmattribute:iplanet-am-auth-lockout-attribute-value - Invalid Attempts Data Attribute Name
-
Specifies the LDAP attribute used to hold the number of failed authentication attempts towards Login Failure Lockout Count. Although the field appears empty in the AM admin UI, AM stores this data in the
sunAMAuthInvalidAttemptsDataAttrNameattribute defined in thesunAMAuthAccountLockoutobjectclass by default.amsterattribute:invalidAttemptsDataAttributeNamessoadmattribute:sunAMAuthInvalidAttemptsDataAttrName - Store Invalid Attempts in Data Store
-
When enabled, AM stores the information regarding failed authentication attempts as the value of the Invalid Attempts Data Attribute Name in the user data store. Information stored includes number of invalid attempts, time of last failed attempt, lockout time and lockout duration. Storing this information in the identity repository allows it to be shared among multiple instances of AM.
Enable this property to track invalid log in attempts when using server-side or client-side authentication sessions.
amsterattribute:storeInvalidAttemptsInDataStoressoadmattribute:sunStoreInvalidAttemptsInDS
General
The following properties are available under the General tab:
- Default Authentication Locale
-
Specifies the default language subtype to be used by the Authentication service. The default value is
en_US.amsterattribute:localessoadmattribute:iplanet-am-auth-locale - Identity Types
-
Lists the type or types of identities used during a profile lookup. You can choose more than one to search on multiple types if you would like AM to conduct a second lookup if the first lookup fails.
This setting applies only to modules within authentication chains.
amsterattribute:identityTypessoadmattribute:sunAMIdentityTypeThe possible values are:
Agent-
Searches for identities under your agents.
agentgroup-
Searches for identities according to your established agent group.
agentonly-
Searches for identities only under your agents.
Group-
Searches for identities according to your established groups.
User-
Searches for identities according to your users.
Default:
AgentandUser. - Pluggable User Status Event Classes
-
Specifies one or more Java classes used to provide a callback mechanism for user status changes during the authentication process. The Java class must implement the
com.sun.identity.authentication.spi.AMAuthCallBackinterface. AM supports account lockout and password changes. AM supports password changes through the LDAP authentication module, and so the feature is only available for the LDAP module.A
.jarfile containing the user status event class belongs in theWEB-INF/libdirectory of the deployed AM instance. If you do not build a.jarfile, add the class files underWEB-INF/classes.amsterattribute:userStatusCallbackPluginsssoadmattribute:sunAMUserStatusCallbackPlugins - Use Client-Side Sessions
-
When enabled, AM assigns client-side sessions to users authenticating to this realm. Otherwise, AM users authenticating to this realm are assigned server-side sessions.
For more information about sessions, see Introduction to sessions.
amsterattribute:statelessSessionsEnabledssoadmattribute:openam-auth-stateless-sessions - Two Factor Authentication Mandatory
-
When enabled, users authenticating to a chain that includes a ForgeRock Authenticator (OATH) module are always required to perform authentication using a registered device before they can access AM. When not selected, users can opt to forego registering a device and providing a token and still successfully authenticate.
Letting users choose not to provide a verification token while authenticating carries implications beyond the
required,optional,requisite, orsufficientflag settings on the ForgeRock Authenticator (OATH) module in the authentication chain.The
Two Factor Authentication Mandatoryproperty only applies to modules within authentication chains, and does not affect nodes within authentication trees.amsterattribute:twoFactorRequiredssoadmattribute:forgerockTwoFactorAuthMandatoryFor example, suppose you configured authentication as follows:
-
The ForgeRock Authenticator (OATH) module is in an authentication chain.
-
The ForgeRock Authenticator (OATH) module has the
requiredflag set. -
Two Factor Authentication Mandatory is not selected.
Users authenticating to the chain can authenticate successfully without providing tokens from their devices. The reason for successful authentication in this case is that the
requiredsetting relates to the execution of the ForgeRock Authenticator (OATH) module itself. Internally, the ForgeRock Authenticator (OATH) module has the ability to forego processing a token while still returning a passing status to the authentication chain. -
- External Login Page URL
-
Specifies the URL of the external login user interface, if the authentication user interface is hosted separately from AM.
When set, AM will use the provided URL as the base of the resume URI, rather than using the Base URL Source Service to obtain the base URL. AM will use this URL when constructing the resume URI if authentication is suspended in an authentication tree.
For more information about the Base URL Source Service, see Configure the Base URL source service.
This setting only applies to nodes within authentication trees, and does not affect modules within authentication chains.
amsterattribute:externalLoginPageUrlssoadmattribute:externalLoginPageUrl - Default Authentication Level
-
Specifies the default authentication level for authentication modules.
This setting applies only to modules within authentication chains.
amsterattribute:defaultAuthLevelssoadmattribute:iplanet-am-auth-default-auth-level
Trees
The following properties are available under the Trees tab, and apply only to authentication nodes and trees:
- Authentication session state management scheme
-
Specifies the location where AM stores authentication sessions.
Possible values are:
-
CTS. AM stores authentication sessions server-side, in the CTS token store. -
JWT. AM sends the authentication session to the client as a JWT. -
In-Memory. AM stores authentication sessions in its memory.
For more information on authentication session storage locations, and the requirements for each, see Introduction to sessions.
Default:
JWT(new installations),In-Memory(after upgrade)amsterattribute:authenticationSessionsStateManagementssoadmattribute:openam-auth-authentication-sessions-state-management-scheme -
- Max duration (minutes)
-
Specifies the maximum allowed duration of an authentication session, including any time spent in the suspended state, in minutes.
Values from
1to2147483647are allowed.Default:
5amsterattribute:authenticationSessionsMaxDurationssoadmattribute:openam-auth-authentication-sessions-max-duration - Suspended authentication duration (minutes)
-
Specifies the length of time an authentication session can be suspended, in minutes.
Suspending an authentication session allows time for out-of-band authentication methods, such as responding to emailed codes or performing an action on an additional device. The value must be less than or equal to the total time allowed for an authentication session, specified in the
Max duration (minutes)property.Values from
1to2147483647are allowed.Default:
5ssoadmattribute:suspendedAuthenticationTimeout - Enable Allowlisting
-
When enabled, AM allowlists authentication sessions to protect them against replay attacks.
Default: Disabled
amsterattribute:authenticationSessionsWhitelistssoadmattribute:openam-auth-authentication-sessions-whitelist - Stops sending tokenId
-
When HttpOnly session cookies are enabled and a client calls the
/json/authenticateendpoint with a valid SSO token, AM returns an emptytokenIdfield.Disable this property to have AM send a valid token ID in this scenario.
For security reasons, you should leave this property enabled. If you have migrated an existing deployment, adjust your clients to expect an empty token ID, then enable this property. Default: Enabled
amsterattribute:authenticationTreeCookieHttpOnlyssoadmattribute:authenticationTreeCookieHttpOnly
Security
The following properties are available under the Security tab:
- Module Based Authentication
-
When enabled, users can authenticate using module-based authentication. Otherwise, all attempts at authentication using the
module=module-namelogin parameter result in failure.Disable module-based authentication in production environments where possible.
This setting applies only to modules within authentication chains.
amsterattribute:moduleBasedAuthEnabledssoadmattribute:sunEnableModuleBasedAuth - Persistent Cookie Encryption Certificate Alias
-
Specifies the key pair alias in the AM keystore to use for encrypting persistent cookies.
This setting applies only to nodes in authentication trees. It doesn’t affect modules in authentication chains.
This property is deprecated. Use the rotatable secret mapping
am.authentication.nodes.persistentcookie.encryptioninstead.If AM finds a matching secret in the secret store for
am.authentication.nodes.persistentcookie.encryption, this alias is ignored.Learn more about rotating secrets in Map and rotate secrets.
Default:
testamsterattribute:keyAliasssoadmattribute:iplanet-am-auth-key-alias - Zero Page Login
-
When enabled, AM allows users to authenticate using only GET request parameters without showing a login screen.
Enable with caution as browsers can cache credentials and servers can log credentials when they are part of the URL.
AM always allows HTTP POST requests for zero page login.
Default: false (disabled)
This setting applies only to modules within authentication chains.
amsterattribute:zeroPageLoginEnabledssoadmattribute:openam.auth.zero.page.login.enabled - Zero Page Login Referer Allowlist
-
Lists the HTTP referer URLs for which AM allows zero page login. These URLs are supplied in the
RefererHTTP request header, allowing clients to specify the web page that provided the link to the requested resource.When zero page login is enabled, including the URLs for the pages from which to allow zero page login will provide some mitigation against Login Cross-Site Request Forgery (CSRF) attacks. Leave this list blank to allow zero page login from any Referer.
This setting applies for both HTTP GET and also HTTP POST requests for zero page login.
This setting applies only to modules within authentication chains.
amsterattribute:zeroPageLoginReferrerWhiteListssoadmattribute:openam.auth.zero.page.login.referer.whitelist - Zero Page Login Allowed Without Referer?
-
When enabled, allows zero page login for requests without an HTTP
Refererrequest header. Zero page login must also be enabled.Enabling this setting reduces the risk of login CSRF attacks with zero page login enabled, but may potentially deny legitimate requests.
amsterattribute:zeroPageLoginAllowedWithoutReferrerssoadmattribute:openam.auth.zero.page.login.allow.null.referer - Add clear-site-data Header on Logout
-
When enabled, AM adds the Clear-Site-Data header to successful logout responses. The
Clear-Site-Datadirective instructs the browser to delete relevant site data on logout. This directive includescache,cookies,storage, andexecutionContexts.Default: true (enabled)
amsterattribute:addClearSiteDataHeader
- Organization Authentication Signing Secret
-
The HMAC shared secret for signing RESTful authentication requests. This secret should be Base64 encoded and at least 128 bits in length. By default, a cryptographically secure, random value is generated.
When users attempt to authenticate to the UI, AM uses this secret to sign a JSON Web Token (JWT). The JWT contains the authentication session ID, realm, and authentication index type value, but does not contain the user’s credentials.
-
This configuration property is deprecated and will be removed in a future release.
If you’re using a secret store of type Keystore, HSM, Google KMS, or Google Secret Manager, map the
am.authn.authid.signing.HMACsecret label to a secret instead. If you map this secret label and set the configuration property, the mapped secret takes precedence. -
You can map multiple secrets to the
am.authn.authid.signing.HMACsecret label to enable secret rotation.AM signs the authentication token with the active secret but checks all mapped secrets when verifying the authentication token signature. Therefore, if you rotate the active secret while an authentication request is in progress, the returned authentication token can still be verified.
If you delete the secret that was used to sign an authentication token, the
authIDreturned in the authentication request can’t be verified and authentication fails.
amsterattribute:sharedSecretssoadmattribute:iplanet-am-auth-hmac-signing-shared-secret -
Post Authentication Processing
The following properties are available under the Post Authentication Processing tab:
- Default Success Login URL
-
Accepts a list of values that specifies where users are directed after successful authentication. The format of this attribute is
client-type|URLalthough the only value you can specify at this time is a URL which assumes the type HTML. The default value is/openam/console. Values that do not specify HTTP have that appended to the deployment URI.amsterattribute:loginSuccessUrlssoadmattribute:iplanet-am-auth-login-success-url - Default Failure Login URL
-
Accepts a list of values that specifies where users are directed after authentication has failed. The format of this attribute is
client-type|URLalthough the only value you can specify at this time is a URL which assumes the type HTML. Values that do not specify HTTP have that appended to the deployment URI.amsterattribute:loginFailureUrlssoadmattribute:iplanet-am-auth-login-failure-url - Authentication Post Processing Classes
-
Specifies one or more Java classes used to customize post-authentication processes for successful or unsuccessful logins. The Java class must implement the
com.sun.identity.authentication.spi.AMPostAuthProcessInterfaceAM interface.A
.jarfile containing the post processing class belongs in theWEB-INF/libdirectory of the deployed AM instance. If you do not build a.jarfile, add the class files underWEB-INF/classes. For deployment, add the.jarfile or classes into a custom AM.warfile.For information on creating post-authentication plugins, see Create Post-Authentication Plugins for Chains.
This setting applies only to modules within authentication chains.
For information about post-authentication processing for trees, see Create post-authentication hooks for trees.
amsterattribute:loginPostProcessClassssoadmattribute:iplanet-am-auth-post-login-process-class - Generate UserID Mode
-
When enabled, the Membership module generates a list of alternate user identifiers if the one entered by a user during the self-registration process is not valid or already exists. The user IDs are generated by the class specified in the Pluggable User Name Generator Class property.
This setting applies only to modules within authentication chains.
amsterattribute:usernameGeneratorEnabledssoadmattribute:iplanet-am-auth-username-generator-enabled - Pluggable User Name Generator Class
-
Specifies the name of the class used to generate alternate user identifiers when Generate UserID Mode is enabled. The default value is
com.sun.identity.authentication.spi.DefaultUserIDGenerator.This setting applies only to modules within authentication chains.
amsterattribute:usernameGeneratorClassssoadmattribute:iplanet-am-auth-username-generator-class - User Attribute Mapping to Session Attribute
-
Enables the authenticating user’s identity attributes (stored in the identity repository) to be set as session properties in the user’s SSO token. The value takes the format
User-Profile-Attribute|Session-Attribute-Name. If Session-Attribute-Name is not specified, the value of User-Profile-Attribute is used. All session attributes contain theam.protectedprefix to ensure that they cannot be edited by the client applications.For example, if you define the user profile attribute as
mailand the user’s email address, available in the user session, asuser.mail, the entry for this attribute would bemail|user.mail. After a successful authentication, theSSOToken.getProperty(String)method is used to retrieve the user profile attribute set in the session. The user’s email address is retrieved from the user’s session using theSSOToken.getProperty("am.protected.user.mail")method call.Properties that are set in the user session using User Attribute Mapping to Session Attributes cannot be modified (for example,
SSOToken.setProperty(String, String)). This results in anSSOException. Multivalued attributes, such asmemberOf, are listed as a single session variable with a|separator.When configuring authentication for a realm configured for client-side sessions, be careful not to add so many session attributes that the session cookie size exceeds the maximum allowable cookie size. For more information about client-side session cookies, see Session cookies and session security.
The
User Attribute Mapping to Session Attributeproperty only applies to modules within authentication chains.For authentication trees, use the Scripted Decision node to retrieve user attributes and session properties, or the Set Session Properties node for session properties only.
amsterattribute:userAttributeSessionMappingssoadmattribute:sunAMUserAttributesSessionMapping
Supported callbacks
For an example using callbacks to authenticate to AM, refer to Returning callback information to AM.
AM supports the following callback types.
| Callback type | Use |
|---|---|
Request information. |
|
Return information to the client application, potentially for display to the user. |
|
Recover additional information from the user’s request. |
Interactive callbacks
Nodes return the following callbacks to request information.
BooleanAttributeInputCallback
Collects a boolean-style confirmation, such as yes/no or true/false.
The Attribute Collector node uses this instead of a ConfirmationCallback to apply IDM policies and validate the response.
| Callback output field | Description |
|---|---|
|
An array of JSON objects describing validation policies that the input failed. The object is empty until the input is provided and validation fails. |
|
A string containing the name of the attribute in the user profile. |
|
An array of JSON objects describing IDM validation policies the input must pass. An empty JSON object if the node does not require validation. The node collects policy information from IDM. For more information about the policies available by default, refer to Default policy for managed objects in the IDM documentation. |
|
A string containing the description of the information required from the user. |
|
A boolean indicating whether input is required for this attribute. |
|
When the node requires validation, this boolean indicates whether to apply validation policies only,
or to validate the input and continue to the next node.
When When |
|
A string containing a default value for the attribute, if required. |
{
"callbacks": [{
"type": "BooleanAttributeInputCallback",
"output": [{
"name": "name",
"value": "preferences/marketing"
}, {
"name": "prompt",
"value": "Send me special offers and services"
}, {
"name": "required",
"value": true
}, {
"name": "policies",
"value": {}
}, {
"name": "failedPolicies",
"value": []
}, {
"name": "validateOnly",
"value": false
}, {
"name": "value",
"value": false
}],
"input": [{
"name": "IDToken1",
"value": false
}, {
"name": "IDToken1validateOnly",
"value": false
}]
}]
}In the input, return the value and a boolean to set validateOnly.
- Class to import
-
org.forgerock.openam.authentication.callbacks.BooleanAttributeInputCallback
ChoiceCallback
Provides a list of choices and collects the selected choice.
In the input, return 0 if the user selected the first choice, 1 for the second choice, and so forth.
{
"callbacks": [{
"type": "ChoiceCallback",
"output": [{
"name": "prompt",
"value": "Choose one"
}, {
"name": "choices",
"value": ["Choice A", "Choice B", "Choice C"]
}, {
"name": "defaultChoice",
"value": 2
}],
"input": [{
"name": "IDToken1",
"value": 0
}]
}]
}- Class to import
-
javax.security.auth.callback.ChoiceCallback
ConfirmationCallback
Collects a boolean-style confirmation, such as yes/no or true/false with an optional "Cancel" choice.
| Callback output field | Description |
|---|---|
|
A number identifying the default option in the array of |
|
A number indicating the severity of the message:
|
|
A number indicating the type of confirmation:
|
|
An array of strings containing the option text for display to the user. |
|
A string containing the description of the choice to display to the user. |
{
"callbacks": [{
"type": "ConfirmationCallback",
"output": [{
"name": "prompt",
"value": ""
}, {
"name": "messageType",
"value": 0
}, {
"name": "options",
"value": ["Submit", "Start Over", "Cancel"]
}, {
"name": "optionType",
"value": -1
}, {
"name": "defaultOption",
"value": 1
}],
"input": [{
"name": "IDToken1",
"value": 0
}]
}]
}In the input, return 0 if the user selected the first choice, 1 for the second choice, and so forth.
- Class to import
-
javax.security.auth.callback.ConfirmationCallback
ConsentMappingCallback
Provides profile attributes that require user consent and collects consent from the user.
| Callback output field | Description |
|---|---|
|
A string containing the access level description for display to the user. |
|
A string containing the name for display to the user. |
|
An array containing names of the attributes to share. |
|
A string containing an icon specification for the privacy and consent notice. |
|
A boolean indicating whether consent is required. |
|
A string containing the privacy and consent notice for display to the user. |
|
A string containing the name of the mapping. |
{
"callbacks": [{
"type": "ConsentMappingCallback",
"output": [{
"name": "name",
"value": "managedUser_managedUser"
}, {
"name": "displayName",
"value": "Test Mapping"
}, {
"name": "icon",
"value": ""
}, {
"name": "accessLevel",
"value": "Actual Profile"
}, {
"name": "isRequired",
"value": true
}, {
"name": "message",
"value": "You consent to your data being shared with external services."
}, {
"name": "fields",
"value": []
}],
"input": [{
"name": "IDToken1",
"value": false
}]
}]
}The user must give consent to all attributes or to none; in the input, return a single boolean value.
- Class to import
-
org.forgerock.openam.authentication.callbacks.ConsentMappingCallback
DeviceBindingCallback
Binds a client device to a user.
| Callback output field | Description |
|---|---|
|
The ID of the user to bind the device to. |
|
The username of the user to bind the device to. |
|
Specifies how the client secures access to the private key. Available options are:
|
|
A string containing the challenge the client should sign with the private key and return for validation. |
|
A string containing an optional title to display when requesting biometric authentication to secure access to the keypair. |
|
A string containing an optional subtitle to display when requesting biometric authentication to secure access to the keypair. |
|
A string containing optional descriptive text to display when requesting biometric authentication to secure access to the keypair. |
|
An integer specifying the number of seconds to wait for device binding to complete before reporting a timeout error. |
{
"authId": "...",
"callbacks": [
{
"type": "DeviceBindingCallback",
"output": [
{
"name": "userId",
"value": "id=demo,ou=user,dc=openam,dc=forgerock,dc=org"
},
{
"name": "username",
"value": "demo"
},
{
"name": "authenticationType",
"value": "BIOMETRIC_ALLOW_FALLBACK"
},
{
"name": "challenge",
"value": "6IBkTEPcMQ0xCghIclmDLost2ssGO5cPDs0AjUhmDTo="
},
{
"name": "title",
"value": "Authentication required"
},
{
"name": "subtitle",
"value": "Cryptography device binding"
},
{
"name": "description",
"value": "Please authenticate with biometrics to proceed"
},
{
"name": "timeout",
"value": 60
}
],
"input": [
{
"name": "IDToken1jws",
"value": ""
},
{
"name": "IDToken1deviceName",
"value": ""
},
{
"name": "IDToken1deviceId",
"value": ""
},
{
"name": "IDToken1clientError",
"value": ""
}
]
}
]
}The client device should perform the following high-level steps to fulfil this callback:
-
Generate a keypair and secure access to it as defined by the
authenticationTypefield. -
Generate a JSON web token (JWT) that has the ID of the user in the subject (
sub) field and the original value of thechallenge.For example:
{ "sub": "id=demo,ou=user,dc=openam,dc=forgerock,dc=org", "challenge": "6IBkTEPcMQ0xCghIclmDLost2ssGO5cPDs0AjUhmDTo=" } -
Sign the JWT using the RS512 algorithm to create a JSON Web Signature (JWS).
-
Complete the callback, returning the JWS, the key ID (
KID) of the keypair, the public key, and the name and the unique ID of the device.
The server verifies the returned information and persists it in the user’s profile if correct.
{
"authId": "...",
"callbacks": [
{
"type": "DeviceBindingCallback",
"output": [...],
"input": [
{
"name": "IDToken1jws",
"value": "eyJhbGciOiJIUzI1NiI....JV_adQssw5cB6aDS6m_kwIiw"
},
{
"name": "IDToken1deviceName",
"value": "Example Brand Version Android Device"
},
{
"name": "IDToken1deviceId",
"value": "ae9573dbbf442e7f-8e0c8b428409e0f1c"
},
{
"name": "IDToken1clientError",
"value": ""
}
]
}
]
}Class to import in scripts: org.forgerock.openam.authentication.callbacks.DeviceBindingCallback
DeviceProfileCallback
Collects information about the device used to authenticate.
| Callback output field | Description |
|---|---|
|
A boolean indicating whether to collect device metadata. |
|
A boolean indicating whether to collect the device location. |
|
A string containing optional text to display while collecting device information. |
{
"callbacks": [{
"type": "DeviceProfileCallback",
"output": [{
"name": "metadata",
"value": true
}, {
"name": "location",
"value": true
}, {
"name": "message",
"value": "Collecting....."
}],
"input": [{
"name": "IDToken1",
"value": ""
}]
}]
}In the input, return escaped JSON resembling the following example response data.
{
"identifier": "aec3fe784...o3Xjiizyb9=",
"alias": "Pixel 3 XL",
"metadata": {
"platform": {
"platform": "Android",
"version": 28,
"device": "generic_x86_arm",
"deviceName": "AOSP on IA Emulator",
"model": "AOSP on IA Emulator",
"brand": "google",
"locale": "en_US",
"timeZone": "America/Vancouver",
"jailBreakScore": 1
},
"hardware": {
"hardware": "ranchu",
"manufacturer": "Google",
"storage": 774,
"memory": 1494,
"cpu": 4,
"display": {
"width": 1440,
"height": 2621,
"orientation": 1
},
"camera": {
"numberOfCameras": 2
}
},
"browser": {
"agent": "Dalvik/2.1.0 (Linux; U; Android 9; AOSP on IA Emulator Build/PSR1.180720.117)"
},
"bluetooth": {
"supported": false
},
"network": {
"connected": true
},
"telephony": {
"networkCountryIso": "us",
"carrierName": "Android"
}
},
"location": {
"latitude": 51.431534,
"Longitude": -2.622353
}
}The location and metadata fields are required when their values are true in the output.
The alias and identifier fields are optional and provided when the client uses the ForgeRock SDKs.
alias-
A friendly name for the device often derived from the make and model.
identifier-
A unique identifier string that can be used to later match the device.
location-
Latitude and longitude of the device.
metadata-
Refer to the example response data for details.
- Class to import
-
org.forgerock.openam.authentication.callbacks.DeviceProfileCallback
DeviceSigningVerifierCallback
Verifies the signature of data from a registered device.
| Callback output field | Description |
|---|---|
|
The ID of the user authenticating, if already determined by the authentication journey. |
|
A string containing the challenge the client should sign with the private key and return for validation. |
|
A string containing an optional title to display when requesting biometric authentication to access the keypair. |
|
A string containing an optional subtitle to display when requesting biometric authentication to access the keypair. |
|
A string containing optional descriptive text to display when requesting biometric authentication to access the keypair. |
|
An integer specifying the number of seconds to wait for device signing to complete before reporting a timeout error. |
{
"authId": "...",
"callbacks": [
{
"type": "DeviceSigningVerifierCallback",
"output": [
{
"name": "userId",
"value": ""
},
{
"name": "challenge",
"value": "Kc4dc14on98DYFzr5SoP2n3TC/JWAcAqTJMjCM+T27Y="
},
{
"name": "title",
"value": "Authentication required"
},
{
"name": "subtitle",
"value": "Cryptography device binding"
},
{
"name": "description",
"value": "Please complete with biometric to proceed"
},
{
"name": "timeout",
"value": 60
}
],
"input": [
{
"name": "IDToken1jws",
"value": ""
},
{
"name": "IDToken1clientError",
"value": ""
}
]
}
]
}The client device should perform the following high-level steps to fulfill this callback:
-
Generate a JSON web token (JWT) that has the ID of the user in the subject (
sub) field) and the original value of thechallenge.For example:
{ "sub": "id=demo,ou=user,dc=openam,dc=forgerock,dc=org", "challenge": "6IBkTEPcMQ0xCghIclmDLost2ssGO5cPDs0AjUhmDTo=" } -
Sign the JWT using the RS512 algorithm to create a JSON Web Signature (JWS).
-
Complete the callback, returning the JWS.
The server verifies the signature against the stored public key.
{
"authId": "...",
"callbacks": [
{
"type": "DeviceSigningVerifierCallback",
"output": [...],
"input": [
{
"name": "IDToken1jws",
"value": "eyJhbGciOiJIUzI1NiI....JV_adQssw5cB6aDS6m_kwIiw"
},
{
"name": "IDToken1clientError",
"value": ""
}
]
}
]
}Class to import in scripts: org.forgerock.openam.authentication.callbacks.DeviceSigningVerifierCallback
HiddenValueCallback
Provides form values that are to remain hidden from the user.
{
"callbacks": [{
"type": "HiddenValueCallback",
"output": [{
"name": "value",
"value": "6186c911-b3be-4dbc-8192-bdf251392072"
}, {
"name": "id",
"value": "jwt"
}],
"input": [{
"name": "IDToken1",
"value": "jwt"
}]
}]
}- Class to import
-
com.sun.identity.authentication.callbacks.HiddenValueCallback
IdPCallback
Collects the result of a native OAuth 2.0 or OpenID Connect request to a social identity provider.
The Social Provider Handler node returns this callback when its Client Type is set to NATIVE.
The output provides the information required to perform the request. Clients built using the ForgeRock SDK for Android or iOS use this to authenticate to the social identity provider with the mobile OS native APIs.
| Callback output field | Description |
|---|---|
|
An array containing the Authentication Context Class Reference values for the native authentication request. |
|
A string containing the identifier for the native authentication request. |
|
A string containing the nonce for the native authentication request. |
|
A string containing a name for the provider. |
|
A string containing the redirection URI for the native authentication request. |
|
A string containing the Request Object for the native authentication request. |
|
A string containing a URL that references a resource containing the Request Object for the native authentication request. |
|
An array containing the scopes for the native authentication request. |
{
"callbacks": [{
"type": "IdPCallback",
"output": [{
"name": "provider",
"value": "amazon"
}, {
"name": "clientId",
"value": "amzn1.application-oa2-client.f0c11aa1f8504f8da26a346ccc55a39e"
}, {
"name": "redirectUri",
"value": "https://localhost:8443/openam"
}, {
"name": "scopes",
"value": ["profile"]
}, {
"name": "nonce",
"value": ""
}, {
"name": "acrValues",
"value": []
}, {
"name": "request",
"value": ""
}, {
"name": "requestUri",
"value": ""
}],
"input": [{
"name": "IDToken1token",
"value": ""
}, {
"name": "IDToken1token_type",
"value": ""
}]
}]
}In the input, return a JWT id_token, access_token or authorization code for the token,
and id_token, access_token or authorization_code for the token type.
- Class to import
-
org.forgerock.openam.authentication.callbacks.IdPCallback
KbaCreateCallback
Collects knowledge-based authentication (KBA) answers to questions defined in the user profile, or user-defined question and answer pairs.
{
"callbacks": [{
"type": "KbaCreateCallback",
"output": [{
"name": "prompt",
"value": "Select a security question"
}, {
"name": "predefinedQuestions",
"value": ["What's your favorite color?"]
}],
"input": [{
"name": "IDToken1question",
"value": ""
}, {
"name": "IDToken1answer",
"value": ""
}]
}]
}In the input, return an empty IDTokenNumberquestion value
when IDTokenNumberanswer corresponds to predefinedQuestions[Number].
For user-provided questions, return both.
- Class to import
-
org.forgerock.openam.authentication.callbacks.KbaCreateCallback
NameCallback
Collects a string entered by the user, such as a username.
{
"callbacks": [{
"type": "NameCallback",
"output": [{
"name": "prompt",
"value": "User Name"
}],
"input": [{
"name": "IDToken1",
"value": ""
}]
}]
}- Class to import
-
javax.security.auth.callback.NameCallback
NumberAttributeInputCallback
Collects a numeric attribute, such as size or age.
The Attribute Collector node uses this to apply IDM policies and validate the response.
| Callback output field | Description |
|---|---|
|
An array of JSON objects describing validation policies that the input failed. The object is empty until the input is provided and validation fails. |
|
A string containing the name of the attribute in the user profile. |
|
An array of JSON objects describing IDM validation policies the input must pass. An empty JSON object if the node does not require validation. The node collects policy information from IDM. For more information about the policies available by default, refer to Default policy for managed objects in the IDM documentation. |
|
A string containing the description of the information required from the user. |
|
A boolean indicating whether input is required for this attribute. |
|
When the node requires validation, this boolean indicates whether to apply validation policies only,
or to validate the input and continue to the next node.
When When |
|
A string containing a default value for the attribute, if required. |
In the input, return the value and a boolean to set validateOnly.
- Class to import
-
org.forgerock.openam.authentication.callbacks.NumberAttributeInputCallback
PasswordCallback
Collects a password value.
{
"callbacks": [{
"type": "PasswordCallback",
"output": [{
"name": "prompt",
"value": "Password"
}],
"input": [{
"name": "IDToken1",
"value": ""
}]
}]
}- Class to import
-
javax.security.auth.callback.PasswordCallback
PingOneProtectEvaluationCallback
Instructs the client to return the data captured by the PingOne Signals SDK so that a risk evaluation can be completed.
| Callback output field | Description |
|---|---|
|
A boolean indicating whether to stop collecting behavioral data after returning the existing data. |
{
"callbacks":[
{
"type":"PingOneProtectEvaluationCallback",
"output":[
{
"name":"pauseBehavioralData",
"value":true
}
],
"input":[
{
"name":"IDToken1signals",
"value":""
},
{
"name":"IDToken1clientError",
"value":""
}
]
}
]
}In the input:
-
In
IDToken1signals, return the data captured by the PingOne Signals SDK. -
In
IDToken1clientError, return an empty string to signal success, or an error string to indicate that the client was unable to process the request.
- Class to import
-
org.forgerock.openam.authentication.callbacks.PingOneProtectEvaluationCallback
PingOneProtectInitializeCallback
Instructs the client to initialize the PingOne Signals SDK to gather information during a transaction.
| Callback output field | Description |
|---|---|
|
A string containing the PingOne environment ID. |
|
A boolean indicating whether to output SDK log messages to the developer console. |
|
An array of device attributes to ignore when collecting device signals. |
|
A string containing a custom host URL from which to retrieve a "Pong" token. Not currently used. |
|
A boolean indicating whether to calculate metadata on demand. When |
|
A boolean indicating whether to collect behavioral data. |
|
A boolean indicating whether the client stores device data in the browser’s localStorage only. When |
|
An integer indicating the number of days that device attestation can rely upon the device fallback key. |
|
A boolean indicating whether to tie the device payload to a non-extractable crypto key stored in the browser for content authenticity verification. |
|
A boolean indicating whether to collect tag data. |
{
"type":"PingOneProtectInitializeCallback",
"output":[
{
"name":"envId",
"value":"3072206d-c6ce-4c19-a366-f87e972c7cc3"
},
{
"name":"consoleLogEnabled",
"value":false
},
{
"name":"deviceAttributesToIgnore",
"value":[
"field1",
"field2"
]
},
{
"name":"customHost",
"value":""
},
{
"name":"lazyMetadata",
"value":false
},
{
"name":"behavioralDataCollection",
"value":true
},
{
"name":"deviceKeyRsyncIntervals",
"value":14
},
{
"name":"enableTrust",
"value":false
},
{
"name":"disableTags",
"value":false
},
{
"name":"disableHub",
"value":false
}
],
"input":[
{
"name":"IDToken1clientError",
"value":""
}
]
}In the input, in the IDToken1clientError field return an empty string to signal success, or any error string to indicate initialization of the SDK failed.
- Class to import
-
org.forgerock.openam.authentication.callbacks.PingOneProtectInitializeCallback
SelectIdPCallback
Collects a choice of an enabled social identity provider or local authentication.
The Select Identity Provider node returns this callback when multiple social identity providers are enabled, or when Local Authentication is enabled alongside at least one provider.
In the input, return the provider name, such as amazon or localAuthentication.
{
"callbacks": [{
"type": "SelectIdPCallback",
"output": [{
"name": "providers",
"value": [{
"provider": "amazon",
"uiConfig": {
"buttonCustomStyle": "background: linear-gradient(to bottom, #f7e09f 15%,#f5c646 85%);color: black;border-color: #b48c24;",
"buttonImage": "",
"buttonClass": "fa-amazon",
"buttonDisplayName": "Amazon",
"buttonCustomStyleHover": "background: linear-gradient(to bottom, #f6c94e 15%,#f6c94e 85%);color: black;border-color: #b48c24;",
"iconClass": "fa-amazon",
"iconFontColor": "black",
"iconBackground": "#f0c14b"
}
}, {
"provider": "google",
"uiConfig": {
"buttonImage": "images/g-logo.png",
"buttonCustomStyle": "background-color: #fff; color: #757575; border-color: #ddd;",
"buttonClass": "",
"buttonCustomStyleHover": "color: #6d6d6d; background-color: #eee; border-color: #ccc;",
"buttonDisplayName": "Google",
"iconFontColor": "white",
"iconClass": "fa-google",
"iconBackground": "#4184f3"
}
}, {
"provider": "localAuthentication"
}]
}, {
"name": "value",
"value": ""
}],
"input": [{
"name": "IDToken1",
"value": ""
}]
}]
}- Class to import
-
org.forgerock.openam.authentication.callbacks.SelectIdPCallback
StringAttributeInputCallback
Collects string attributes, such as city names, telephone numbers, and postcodes.
The Attribute Collector node uses this instead of a TextInputCallback to apply IDM policies and validate the response.
| Callback output field | Description |
|---|---|
|
An array of JSON objects describing validation policies that the input failed. The object is empty until the input is provided and validation fails. |
|
A string containing the name of the attribute in the user profile. |
|
An array of JSON objects describing IDM validation policies the input must pass. An empty JSON object if the node does not require validation. The node collects policy information from IDM. For more information about the policies available by default, refer to Default policy for managed objects in the IDM documentation. |
|
A string containing the description of the information required from the user. |
|
A boolean indicating whether input is required for this attribute. |
|
When the node requires validation, this boolean indicates whether to apply validation policies only,
or to validate the input and continue to the next node.
When When |
|
A string containing a default value for the attribute, if required. |
{
"callbacks": [{
"type": "StringAttributeInputCallback",
"output": [{
"name": "name",
"value": "givenName"
}, {
"name": "prompt",
"value": "First Name"
}, {
"name": "required",
"value": true
}, {
"name": "policies",
"value": {
"policyRequirements": ["REQUIRED", "VALID_TYPE"],
"fallbackPolicies": null,
"name": "givenName",
"policies": [{
"policyRequirements": ["REQUIRED"],
"policyId": "required"
}, {
"policyRequirements": ["VALID_TYPE"],
"policyId": "valid-type",
"params": {
"types": ["string"]
}
}],
"conditionalPolicies": null
}
}, {
"name": "failedPolicies",
"value": []
}, {
"name": "validateOnly",
"value": false
}, {
"name": "value",
"value": ""
}],
"input": [{
"name": "IDToken1",
"value": ""
}, {
"name": "IDToken1validateOnly",
"value": false
}]
}]
}When input validation is not required, the policies contain an empty object:
{
"name": "policies",
"value": {}
}In the input, return the value and a boolean to set validateOnly.
- Class to import
-
org.forgerock.openam.authentication.callbacks.StringAttributeInputCallback
TermsAndConditionsCallback
Displays the current terms and conditions and collects the user’s agreement to them.
{
"callbacks": [
{
"type": "TermsAndConditionsCallback",
"output": [
{
"name": "version",
"value": "0.0"
},
{
"name": "terms",
"value": "Terms and conditions text that you must agree to."
},
{
"name": "createDate",
"value": "2022-10-28T04:20:11.320Z"
}
],
"input": [
{
"name": "IDToken1",
"value": false
}
]
}
]
}In the input, return true if the user agrees to the terms and conditions.
- Class to import
-
org.forgerock.openam.authentication.callbacks.TermsAndConditionsCallback
TextInputCallback
Collects text input from the user.
{
"callbacks": [{
"type": "TextInputCallback",
"output": [{
"name": "prompt",
"value": "Provide a nickname for this account"
}],
"input": [{
"name": "IDToken1",
"value": ""
}]
}]
}- Class to import
-
javax.security.auth.callback.TextInputCallback
ValidatedPasswordCallback
Collects a password value.
The Platform Password node uses this instead of a PasswordCallback to apply IDM policies and validate the response.
| Callback output field | Description |
|---|---|
|
An array of JSON objects describing validation policies that the input failed. The object is empty until the input is provided and validation fails. |
|
A string containing the name of the attribute in the user profile. |
|
An array of objects describing IDM validation policies the input must pass. An empty JSON object if the node does not require validation. The node collects policy information from IDM. For more information about the policies available by default, refer to Default policy for managed objects in the IDM documentation. |
|
A string containing the description of the information required from the user. |
|
When the node requires validation, this boolean indicates whether to apply validation policies only,
or to validate the input and continue to the next node.
When When |
{
"callbacks": [{
"type": "ValidatedPasswordCallback",
"output": [{
"name": "echoOn",
"value": false
}, {
"name": "policies",
"value": {
"policyRequirements": ["VALID_TYPE", "MIN_LENGTH", "AT_LEAST_X_CAPITAL_LETTERS", "AT_LEAST_X_NUMBERS", "CANNOT_CONTAIN_OTHERS"],
"fallbackPolicies": null,
"name": "password",
"policies": [{
"policyRequirements": ["VALID_TYPE"],
"policyId": "valid-type",
"params": {
"types": ["string"]
}
}, {
"policyId": "minimum-length",
"params": {
"minLength": 8
},
"policyRequirements": ["MIN_LENGTH"]
}, {
"policyId": "at-least-X-capitals",
"params": {
"numCaps": 1
},
"policyRequirements": ["AT_LEAST_X_CAPITAL_LETTERS"]
}, {
"policyId": "at-least-X-numbers",
"params": {
"numNums": 1
},
"policyRequirements": ["AT_LEAST_X_NUMBERS"]
}, {
"policyId": "cannot-contain-others",
"params": {
"disallowedFields": ["userName", "givenName", "sn"]
},
"policyRequirements": ["CANNOT_CONTAIN_OTHERS"]
}],
"conditionalPolicies": null
}
}, {
"name": "failedPolicies",
"value": []
}, {
"name": "validateOnly",
"value": false
}, {
"name": "prompt",
"value": "Password"
}],
"input": [{
"name": "IDToken1",
"value": ""
}, {
"name": "IDToken1validateOnly",
"value": false
}]
}]
}In the input, return the value and a boolean to set validateOnly.
- Class to import
-
org.forgerock.openam.authentication.callbacks.ValidatedPasswordCallback
ValidatedUsernameCallback
Collects a username.
The Platform Username node uses this instead of a NameCallback to apply IDM policies and validate the response.
| Callback output field | Description |
|---|---|
|
An array of JSON objects describing validation policies that the input failed. The object is empty until the input is provided and validation fails. |
|
A string containing the name of the attribute in the user profile. |
|
An array of objects describing IDM validation policies the input must pass. An empty JSON object if the node does not require validation. The node collects policy information from IDM. For more information about the policies available by default, refer to Default policy for managed objects in the IDM documentation. |
|
A string containing the description of the information required from the user. |
|
When the node requires validation, this boolean indicates whether to apply validation policies only,
or to validate the input and continue to the next node.
When When |
{
"callbacks": [{
"type": "ValidatedUsernameCallback",
"output": [{
"name": "policies",
"value": {
"policyRequirements": ["REQUIRED", "VALID_TYPE", "VALID_USERNAME", "CANNOT_CONTAIN_CHARACTERS", "MIN_LENGTH", "MAX_LENGTH"],
"fallbackPolicies": null,
"name": "userName",
"policies": [{
"policyRequirements": ["REQUIRED"],
"policyId": "required"
}, {
"policyRequirements": ["VALID_TYPE"],
"policyId": "valid-type",
"params": {
"types": ["string"]
}
}, {
"policyId": "valid-username",
"policyRequirements": ["VALID_USERNAME"]
}, {
"policyId": "cannot-contain-characters",
"params": {
"forbiddenChars": ["/"]
},
"policyRequirements": ["CANNOT_CONTAIN_CHARACTERS"]
}, {
"policyId": "minimum-length",
"params": {
"minLength": 1
},
"policyRequirements": ["MIN_LENGTH"]
}, {
"policyId": "maximum-length",
"params": {
"maxLength": 255
},
"policyRequirements": ["MAX_LENGTH"]
}],
"conditionalPolicies": null
}
}, {
"name": "failedPolicies",
"value": []
}, {
"name": "validateOnly",
"value": false
}, {
"name": "prompt",
"value": "Username"
}],
"input": [{
"name": "IDToken1",
"value": ""
}, {
"name": "IDToken1validateOnly",
"value": false
}]
}]
}In the input, return the value and a boolean to set validateOnly.
- Class to import
-
org.forgerock.openam.authentication.callbacks.ValidatedUsernameCallback
Read-only callbacks
Nodes use these callbacks to return information to the client application or to display information to the user.
MetadataCallback
Injects key-value pairs into the authentication process by adding extra metadata to the JSON response.
{
"callbacks": [{
"type": "MetadataCallback",
"output": [{
"name": "data",
"value": {
"myParameter": "MyValue"
}
}]
}]
}- Class to import
-
com.sun.identity.authentication.spi.MetadataCallback
PollingWaitCallback
Indicates the number of milliseconds to wait before responding to the callback.
{
"callbacks": [{
"type": "PollingWaitCallback",
"output": [{
"name": "waitTime",
"value": "8000"
}, {
"name": "message",
"value": "Waiting for response..."
}]
}]
}- Class to import
-
org.forgerock.openam.authentication.callbacks.PollingWaitCallback
RedirectCallback
Redirects the user-agent.
The Social Provider Handler node returns this callback when its Client Type is set to BROWSER,
and the client must redirect the user to the social provider for authentication.
{
"callbacks": [{
"type": "RedirectCallback",
"output": [{
"name": "redirectUrl",
"value": "https://accounts.google.com/o/oauth2/v2/auth?nonce..."
}, {
"name": "redirectMethod",
"value": "GET"
}, {
"name": "trackingCookie",
"value": true
}]
}]
}AM uses a trackingCookie to store the authentication identifier
that reflects the client’s place in the authentication process.
- Class to import
-
com.sun.identity.authentication.spi.RedirectCallback
SuspendedTextOutputCallback
Provides a message to display to the user when the authentication journey is suspended.
| Callback output field | Description |
|---|---|
|
A string containing a message to display to the user. |
|
A number indicating the severity of the message:
|
{
"callbacks": [{
"type": "SuspendedTextOutputCallback",
"output": [{
"name": "message",
"value": "An email has been sent to your inbox."
}, {
"name": "messageType",
"value": "0"
}]
}]
}- Class to import
-
org.forgerock.openam.auth.node.api.SuspendedTextOutputCallback
TextOutputCallback
Provides a message to display to the user.
| Callback output field | Description |
|---|---|
|
A string containing a message to display to the user. |
|
A number indicating the severity of the message:
|
{
"callbacks": [{
"type": "TextOutputCallback",
"output": [{
"name": "message",
"value": "Default message"
}, {
"name": "messageType",
"value": "0"
}]
}]
}- Class to import
-
javax.security.auth.callback.TextOutputCallback
Backchannel callbacks
Nodes use these callbacks to recover additional information from the request, such as a header or a certificate.
HttpCallback
Accesses user credentials sent in the Authorization header:
Authorization: Basic bXlDbGllbnQ6Zm9yZ2Vyb2Nr
- Class to import
-
com.sun.identity.authentication.spi.HttpCallback
LanguageCallback
Retrieves the locale from the request header for localizing text presented to the user.
- Class to import
-
javax.security.auth.callback.LanguageCallback
Authenticate endpoint parameters
To authenticate to AM using REST, send an HTTP POST request to the json/authenticate endpoint.
Specify the realm hierarchy, starting at the Top Level Realm and prefix each realm in the hierarchy with the realms/ keyword. For example, /realms/root/realms/customers/realms/europe.
The following list describes the json/authenticate endpoint parameters:
authIndexType
The authIndexType specifies the type of authentication the user will perform.
Always use this parameter in conjunction with the authIndexValue to provide additional information about how the user
is authenticating.
If not specified, AM authenticates the user against the default authentication service configured for the realm.
The authIndexType can be one of the following:
composite_advice-
When the
authIndexTypeiscomposite_advice, theauthIndexValuemust be a URL-encoded composite advice string.Use the
composite_advicetype to indicate which authentication services to use when logging in a user.This example indicates that the user should authenticate with an authentication level of at least 10:
$ curl -G \ --request POST \ --header "Content-Type: application/json" \ --header 'Accept-API-Version: resource=2.0, protocol=1.0' \ --data-urlencode 'authIndexType=composite_advice' \ --data-urlencode 'authIndexValue=<Advices> <AttributeValuePair> <Attribute name="AuthLevelConditionAdvice"/> <Value>10</Value> </AttributeValuePair> </Advices>' \ 'https://openam.example.com:8443/openam/json/realms/root/authenticate'bashThis curlcommand URL-encodes the XML values. The--getoption appends them as query string parameters to the URL.Possible options for
Advicesare:-
TransactionConditionAdvice. Requires the unique ID of a transaction token. For example:<Advices> <AttributeValuePair> <Attribute name="TransactionConditionAdvice"/> <Value>9dae2c80-fe7a-4a36-b57b-4fb1271b0687</Value> </AttributeValuePair> </Advices>xmlFor more information, refer to Transactional authorization.
-
AuthenticateToServiceConditionAdvice. Requires the name of an authentication chain or tree. For example:<Advices> <AttributeValuePair> <Attribute name="AuthenticateToServiceConditionAdvice"/> <Value>myExampleTree</Value> </AttributeValuePair> </Advices>xml -
AuthSchemeConditionAdvice. Requires the name of an authentication module. For example:<Advices> <AttributeValuePair> <Attribute name="AuthSchemeConditionAdvice"/> <Value>DataStoreModule</Value> </AttributeValuePair> </Advices>xml -
AuthenticateToRealmConditionAdvice. Requires the name of a realm. For example:<Advices> <AttributeValuePair> <Attribute name="AuthenticateToRealmConditionAdvice"/> <Value>myRealm</Value> </AttributeValuePair> </Advices>xml -
AuthLevelConditionAdvice. Requires an authentication level.For example:
<Advices> <AttributeValuePair> <Attribute name="AuthLevelConditionAdvice"/> <Value>10</Value> </AttributeValuePair> </Advices>xml -
AuthenticateToTreeConditionAdvice. Requires the name of an authentication tree. For example:<Advices> <AttributeValuePair> <Attribute name="AuthenticateToTreeConditionAdvice"/> <Value>PersistentCookieTree</Value> </AttributeValuePair> </Advices>xml
You can specify multiple advice conditions and combine them. For example:
<Advices> <AttributeValuePair> <Attribute name="AuthenticateToServiceConditionAdvice"/> <Value>ldapService</Value> </AttributeValuePair> <AttributeValuePair> <Attribute name="AuthenticateToServiceConditionAdvice"/> <Value>Example</Value> </AttributeValuePair> <AttributeValuePair> <Attribute name="AuthLevelConditionAdvice"/> <Value>10</Value> </AttributeValuePair> </Advices>xml -
level-
When the
authIndexTypeislevel, theauthIndexValuesets the minimum authentication level an authentication service must satisfy to log in the user.For example, to log into AM using an authentication service that provides a minimum authentication level of 10, you could use the following:
$ curl \ --request POST \ --header 'Accept-API-Version: resource=2.0, protocol=1.0' \ 'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/authenticate?authIndexType=level&authIndexValue=10'bashThis mechanism is supported for authentication chains only. module-
Specifies that the value of the
authIndexValueparameter is the name of the authentication module AM must use to log in the user.For example, to log into AM using the built-in
DataStoreauthentication module, you could use the following:$ curl \ --request POST \ --header 'Accept-API-Version: resource=2.0, protocol=1.0' \ 'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/authenticate?authIndexType=module&authIndexValue=DataStore'bashFor security reasons, you should disable module-based authentication. For more information, refer to Secure realms. resource-
When the
authIndexTypeisresource, theauthIndexValuemust be a URL protected by an AM policy.For example, to log into AM using a policy matching the
https://www.example.comresource, you could use the following:$ curl \ --request POST \ --header 'Accept-API-Version: resource=2.0, protocol=1.0' \ 'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/authenticate?authIndexType=resource&authIndexValue=https%3A%2F%2Fwww.example.com'bashNote that the resource must be URL-encoded. Authentication will fail if no policy matches the resource.
service-
When the
authIndexTypeisservice, theauthIndexValueis the tree or chain AM must use to authenticate the user.For example, to authenticate using the
Loginauthentication tree, you could use the following:$ curl \ --request POST \ --header 'Accept-API-Version: resource=2.0, protocol=1.0' \ 'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/authenticate?authIndexType=service&authIndexValue=Login'bashIf
authIndexType=serviceand noauthIndexValueis specified, the default service is used. This is similar to noauthIndexTypebeing set. user-
When the
authIndexTypeisuser, theauthIndexValuemust be a valid user ID. AM authenticates the user against the authentication chain configured in the User Authentication Configuration field of that user’s profile.Authentication fails if the User Authentication Configuration field is empty for the user.
For example, for user
bjensento log into AM using the chain specified in their user profile, you could use the following:$ curl \ --request POST \ --header 'Accept-API-Version: resource=2.0, protocol=1.0' \ 'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/authenticate?authIndexType=user&authIndexValue=bjensen'bashThis mechanism is supported for authentication chains only. If there are several authentication services that satisfy the authentication requirements, AM presents them as a choice callback to the user. Return the required callbacks to AM to authenticate.
Required: No.
authIndexValue
This parameter sets a value for the specific authIndexType.
Required: Yes, when using the authIndexType parameter.
noSession
When set to true, this parameter specifies that AM should not return a session when authenticating a user.
For example:
$ curl \
--request POST \
--header "Content-Type: application/json" \
--header "Accept-API-Version: resource=2.0, protocol=1.0" \
--header "X-OpenAM-Username: demo" \
--header "X-OpenAM-Password: Ch4ng31t" \
'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/authenticate?noSession=true'
{
"message":"Authentication Successful",
"successUrl":"/openam/console",
"realm":"/"
}Required: No.
Authentication nodes configuration reference
This page covers the configuration of the authentication nodes that are built into AM.
|
A number of additional authentication nodes are available from the Marketplace. |
Basic authentication nodes
Use the following nodes for basic authentication tasks, such as collecting usernames and passwords:
Multi-factor authentication nodes
Use the following nodes to configure trees with multi-factor authentication capabilities, such as web authentication and push authentication:
Risk management authentication nodes
Use the following nodes to examine the perceived risk associated with the authentication and act on it:
Behavioral authentication nodes
Use the following nodes to adjust the behavior of authentication trees:
Contextual authentication nodes
Use the following nodes to authenticate with a digital certificate, change the flow, or set a cookie based on the authentication context:
Federation authentication nodes
Use the following nodes to configure trees with federation capabilities, such as OAuth 2.0, social authentication, and account provisioning:
Identity management authentication nodes
Use the following nodes to perform identity management during an authentication tree flow, such as mapping anonymous users to a session.
Utility authentication nodes
Use the following nodes to perform various tasks during the authentication flow:
Thing authentication nodes
Use the following nodes to perform various tasks related to authenticating IoT things:
Client configuration reference
- Enabled
-
Whether the provider is enabled.
Required: Yes.
- Auth ID Key
-
The attribute the social identity provider uses to identify an authenticated individual. For example,
id,sub, anduser_id.Required: Yes.
- Client ID
-
The
client_idparameter as described in section 2.2 of The OAuth 2.0 Authorization Framework specification.Required: Yes.
- Client Secret
-
The
client_secretparameter as described in section 2.3 of The OAuth 2.0 Authorization Framework specification.This property is deprecated. Use the Client Secret Label Identifier instead.
If you set a Client Secret Label Identifier and AM finds a matching secret in a secret store, the Client Secret is ignored.
Required: No.
- Client Secret Label Identifier
-
An identifier used to create a secret label for mapping to a secret in a secret store.
AM uses this identifier to create a specific secret label for this service instance, using the template
am.social.providers.identifier.secretwhere identifier is the value of Client Secret Label Identifier.The identifier can only contain alphanumeric characters
a-z,A-Z,0-9, and periods (.). It can’t start or end with a period.If you set a Client Secret Label Identifier and AM finds a matching secret in a secret store, the Client Secret is ignored.
Required: No.
- Authentication Endpoint URL
-
The URL to the social provider’s endpoint handling authentication as described in section 3.1 of The OAuth 2.0 Authorization Framework. For example,
https://accounts.google.com/oauth2/v2/auth.Required: Yes.
- Access Token Endpoint URL
-
The URL to the endpoint handling access tokens as described in section 3.2 of The OAuth 2.0 Authorization Framework specification. For example,
https://www.googleapis.com/oauth2/v4/token.Required: Yes.
- User Profile Service URL
-
The user profile URL that returns profile information. For example,
https://www.googleapis.com/oauth2/v3/userinfo.This URL should return JSON objects in its response.
Required: No.
- Token Introspection Endpoint URL
-
The URL to the endpoint handling access token validation, as described in the OAuth 2.0 Token Introspection specification. For example,
https://oauth2.googleapis.com/tokeninfo.Required: No.
- Redirect URL
-
The URL the identity provider will redirect the user to after authenticating, as described in Section 3.1.2 of The OAuth 2.0 Authorization Framework specification.
This URL is usually a page or path in AM; for example,
https://am.example.com:8443/am?_realm=alpha, The URL is also registered in the IDP’s service.If you’re using an app built with the ForgeRock SDKs for Android or iOS, you can also use a custom URI scheme as the redirect; for example,
com.example.sdkapp:redirect_uri_pathorfrauth://com.forgerock.ios.sdkapp.When using the
FORM_POSTResponse Mode, you must specify theform_postendpoint in the redirection URL. Refer to Response Mode for more information.Required: Yes.
- Redirect after form post URL
-
The URL of a custom login page or application. AM will send processed form post data related to social login authentication to that URL as the value of the
form_post_entryquery parameter.To continue the authentication journey, the custom login page is responsible for making a call to the AM
/json/authenticateendpoint with the authentication ID (authID) and the processed form data (form_post_entry).Configure this property when the following is true:
-
The
FORM_POSTResponse Mode is configured. -
Your users log in to AM using custom login pages, such as apps using the ForgeRock SDKs, instead of the AM UI.
Required: No.
-
- Scope Delimiter
-
The delimiter used to separate scope values. For example, a blank space (), or a comma character (,).
Most providers use a blank space.
Required: Yes.
- OAuth Scopes
-
The list of scopes to request from the provider.
The scopes that the provider returns depends on the permissions that the resource owner, such as the end user, grants to the client application.
For example, Google exposes its supported scopes in their OAuth 2.0 Scopes for Google APIs documentation.
Required: Yes.
- Client Authentication Method
-
Specifies how the client should authenticate to the provider. Possible values are:
CLIENT_SECRET_POST-
The client sends the client ID and the secret in the
client_IDand theclient_secretparameters in the body of the request. CLIENT_SECRET_BASIC-
The client sends the client ID and the secret in a basic authorization header with the base64-encoded value of client-id:client-secret.
PRIVATE_KEY_JWT-
The client sends its credentials to the provider in a signed JWT as specified in the JSON Web Token (JWT) Profile for OAuth 2.0 Client Authentication and Authorization Grants.
ENCRYPTED_PRIVATE_KEY_JWT-
The client sends its credentials to the provider in a signed, then encrypted JWT as specified in the JSON Web Token (JWT) Profile for OAuth 2.0 Client Authentication and Authorization Grants.
TLS_CLIENT_AUTH-
The client presents a X.509 certificate that uses public key infrastructure (PKI), as specified in the OAuth 2.0 Mutual TLS (mTLS) Client Authentication and Certificate Bound Access Tokens.
SELF_SIGNED_TLS_CLIENT_AUTH-
The client presents a X.509 self-signed certificate, as specified in the OAuth 2.0 Mutual TLS (mTLS) Client Authentication and Certificate Bound Access Tokens.
Some authentication methods require additional configuration:
How do I configure JWT authentication with signed JWTs?
-
Obtain a list of supported signing algorithms from the provider’s
.well-knownendpoint, and decide which one you will use. -
In the Private Key JWT Signing Algorithm field, enter the signing algorithm that AM will use to sign the JWT. For example,
RSA256.This field may already be configured if the client is sending request objects.
-
Create a signing secret, and map it to the
am.services.oauth2.oidc.rp.jwt.authenticity.signingsecret label in an AM secret store.The secret label may already have secrets mapped to it if the client is sending signed request objects to the provider, or if another client in the realm is already using it.
For more information, refer to Secret stores, and /oauth2/connect/rp/jwk_uri.
-
Provide a JWK with the public key to the identity provider. Refer to their documentation for more information.
For example, you could copy the contents of the public JWK in a field in the provider’s service configuration, or you could configure the realm’s
/oauth2/connect/rp/jwk_uriendpoint, which exposes the client’s public keys.Configure the realm’s
/oauth2/connect/rp/jwk_uriendpoint in the provider, which exposes the client’s public keys. Refer to the provider’s documentation for more information. -
Change the value in the Private Key JWT Expiration Time (seconds) field, if needed. It has a sensible value preconfigured, but you may need to tune it for your provider.
How do I configure JWT authentication with signed and encrypted JWTs?
-
Follow the steps in How do I configure JWT authentication with signed JWTs? to configure AM to sign authentication JWTs.
Now you are ready to configure AM to encrypted authentication JWTs.
-
Obtain a list of supported encryption algorithms and methods from the provider’s
.well-knownendpoint, and decide which one you will use. -
In the JWT Encryption Algorithm field, select the encryption algorithm.
If the required encryption algorithm does not appear in the drop-down, check the reference entry for the JWT Encryption Algorithm field for information on how to add it.
This field may already be configured if the client is encrypting request objects.
-
In the JWT Encryption Method field, select the encryption method.
This field may already be configured if the client is encrypting request objects.
-
In the JWKS URI Endpoint field, configure the URI containing the provider’s public JWK set.
Obtain the URI from the provider’s
.well-knownendpoint, or their documentation.AM will use the JWK URI to fetch the provider’s public encryption key.
-
Perform one of the following steps depending on the encryption method you configured:
-
If you chose Direct AES Encryption method, select
NONEin the JWT Signing Algorithm field. Signing is redundant with this encryption method. -
If you chose an encryption method different from the Direct AES Encryption method, configure signing. For more information, refer to How do I configure JWT authentication with signed JWTs?.
-
How do I configure mTLS authentication with PKI?
-
Obtain a certificate for AM to use as a client. This certificate must be signed by a certificate authority (CA).
You can use the same certificate for different social identity provider client configurations, and you can only have one mTLS certificate by realm (either PKI-related, or self-signed).
-
Make the certificate available to AM by configuring it in a secret store. Map its alias to the
am.services.oauth2.mtls.client.authenticationsecret label.For example, you can create a
PKCS12keystore secret store.For more information, refer to Secret stores.
Even though the identity provider should trust the CA certificate automatically, the client certificate will appear in the /oauth2/connect/rp/jwk_uri endpoint.
How do I configure mTLS authentication with self-signed certificates?
-
Obtain a self-signed certificate that AM will use as a client.
You can use the same certificate for different social identity provider client configurations, and you can only have one mTLS certificate by realm (either PKI-related, or self-signed).
-
Make the certificate available to AM by configuring it in a secret store. Map its alias to the
am.services.oauth2.mtls.client.authenticationsecret label.For example, you can create a
PKCS12keystore secret store.For more information, refer to Secret stores.
To trust the self-signed certificate, the social identity provider must be able to access its public key and certificate. Social identity providers may have different ways of accessing public keys; for example, you may be able to configure the public JWK directly in the provider, or you may be able to provide AM’s /oauth2/connect/rp/jwk_uri endpoint, which exposes it.
Refer to your social identity provider documentation for more information.
Required: Yes.
-
- PKCE Method
-
The PKCE transformation method AM uses when making requests to the provider’s authorization endpoint, as specified in Section 4.2 of the Proof Key for Code Exchange by OAuth Public Clients specification.
Select
NONEto disable PKCE transformations.Required: No.
- Request Parameter JWT Option
-
(OpenID Connect providers only) Specifies whether AM should provide a request object JWT to the provider. Possible values are:
NONE-
AM does not send a request object to the provider.
REFERENCE-
The request object JWT is stored in AM’s CTS token store, and AM exposes a unique identifier for it using the
oauth2/request_uriendpoint for the realm. The URL to the endpoint and the JWT’s unique identifier are passed to the provider in therequest_uriparameter of the request.Ensure that the provider can reach the endpoint.
An example of the URL is
https://platform.example.com:8443/am/realms/root/realms/myRealm/oauth2/request_uri/requestobjectIDWhen integrating with itsme, ensure that the base URL of AM contains the
443port. For example,https://platform.example.com:443/am.To do this, configure the reverse proxy or load balancer to expose the port, or the Base URL Source Service:
-
In the AM admin UI, go to Realms > Realm Name > Services.
-
Add a Base URL Source service if one is not already configured, or select it to change its properties:
-
VALUE-
AM appends the JWT as the value of the
requestparameter of the request.How do I configure the client to send signed request objects?
-
In the Request Parameter JWT Option field, select either
VALUEorREFERENCE.Refer to your identity provider’s documentation for more information.
-
Obtain a list of supported signing algorithms from the provider’s
.well-knownendpoint, and decide which one you will use. -
In the JWT Signing Algorithm field, select the signing algorithm that AM will use to sign the request object. For example,
RS256.This field may already be configured if the client is using JWT client authentication.
-
Create a signing secret that uses the algorithm you selected previously, and map it to the`am.services.oauth2.oidc.rp.jwt.authenticity.signing` secret label in an AM secret store.
The secret label may already have secrets mapped to it if the client is using JWT client authentication, or if another client in the realm is already using it.
For more information, refer to Secret stores, and /oauth2/connect/rp/jwk_uri.
-
Provide a JWK with the public key to the identity provider. Refer to their documentation for more information.
For example, you could copy the contents of the public JWK in a field in the provider’s service configuration, or you could configure the realm’s
/oauth2/connect/rp/jwk_uriendpoint, which exposes the client’s public keys.Configure the realm’s
/oauth2/connect/rp/jwk_uriendpoint in the provider, which exposes the client’s public keys. Refer to the provider’s documentation for more information.
How do I configure the client to send signed and encrypted request objects?
-
Follow the steps in How do I configure the client to send signed request objects? to configure AM to send signed request objects.
Now you are ready to configure AM to send encrypted request objects.
-
Enable Encrypt Request Parameter JWT.
-
Obtain a list of supported encryption algorithms and methods from the provider’s
.well-knownendpoint, and decide which one you will use. -
In the JWT Encryption Algorithm field, select the encryption algorithm.
If the required encryption algorithm does not appear in the drop-down, check the reference entry for the JWT Encryption Algorithm field for information on how to add it.
This field may already be configured if the client is encrypting authentication JWTs.
-
In the JWT Encryption Method field, select the encryption method.
This field may already be configured if the client is encrypting authentication JWTs.
-
In the JWKS URI Endpoint field, configure the URI containing the provider’s public JWK set.
Obtain the URI from the provider’s
.well-knownendpoint.AM will use the JWK URI to fetch the provider’s public encryption key.
-
Perform one of the following steps depending on the encryption method you configured:
-
If you chose Direct AES Encryption method, select
NONEin the JWT Signing Algorithm field. Signing is redundant with this encryption method. -
If you chose an encryption method different from the Direct AES Encryption method, configure signing. For more information, refer to How do I configure the client to send signed request objects?.
-
-
- Encrypt Request Parameter JWT
-
Specifies whether the request parameter must be encrypted when Request Parameter JWT Option is set to
REFERENCEorVALUE. - ACR Values
-
(OpenID Connect providers only) Specifies a space-separated list, in order of preference, of the client’s
acrvalues.Required: No.
- Well Known Endpoint
-
(OpenID Connect providers only) The URL for retrieving information about the provider, such as endpoints, and public keys. For example,
https://accounts.google.com/.well-known/openid-configuration.Required: Yes.
- Request Object Audience
-
(OpenID Connect providers only) The intended audience (
aud) of the request object when the Request Parameter JWT Option field is set toVALUEorREFERENCE.When not configured, the value of the Issuer field will be used as the audience of the request object.
- OP Encrypts ID Tokens
-
(OpenID Connect providers only) Specifies whether the provider encrypts ID Tokens.
How do I configure the AM to receive encrypted tokens?
-
Obtain a list of supported ID token encryption algorithms from the provider’s
.well-knownendpoint, and decide which one the client will use. -
Create a suitable secret for the algorithm that you chose and map it to the
am.services.oauth2.oidc.rp.idtoken.encryptionsecret label in a secret store.The secret label may have existing secrets mapped if another client in the realm is using it.
For more information, refer to Secret stores and /oauth2/connect/rp/jwk_uri.
-
Provide a JWK with the public key to the identity provider. Refer to their documentation for more information.
For example, you could copy the contents of the public JWK in a field in the provider’s service configuration, or you could configure the realm’s
/oauth2/connect/rp/jwk_uriendpoint, which exposes the client’s public keys.Configure the realm’s
/oauth2/connect/rp/jwk_uriendpoint in the provider, which exposes the client’s public keys. Refer to the provider’s documentation for more information.
Required: No.
-
- Issuer
-
(OpenID Connect providers only) The issuer of ID Tokens.
Either specify a regular expression or a string value that must exactly match the value returned in the ID token, depending on the configuration of the Issuer comparison check setting.
Obtain the
issuervalue from the provider’s.well-knownendpoint.Required: Yes.
- Enable Native Nonce
-
(OpenID Connect providers only) When enabled, the provider native SDK must include a
nonceclaim in the ID token. The value of the claim must be the value of thenonceclaim sent in the Authentication Request.Required: No.
- User Info Response Format
-
(OpenID Connect providers only) The format in which the provider’s
userinfoendpoint returns data.Some of the options require additional configuration:
How do I configure the client to receive signed userinfo JWTs?
-
In the JWKS URI Endpoint field, configure the URL containing the provider’s public JWK set. Obtain it from the provider’s
.well-knownendpoint, or their documentation.AM will use this URL to fetch the provider’s public signing key.
How do I configure the client to receive signed, then encrypted userinfo JWTs?
-
Follow the steps in How do I configure the client to receive signed userinfo JWTs? to configure AM to receive signed JWTs.
Now you are ready to configure AM to receive encrypted JWTs.
-
Obtain a list of supported ID token encryption algorithms from the provider’s
.well-knownendpoint, and decide which one the client will use. -
Create a suitable secret for the algorithm that you chose and map it to the
am.services.oauth2.oidc.rp.idtoken.encryptionsecret label in an AM secret store.The secret label may have existing secrets mapped if another client in the realm is using it, or if the provider encrypts ID tokens.
For more information, refer to Secret stores and /oauth2/connect/rp/jwk_uri.
-
Provide a JWK with the public key to the identity provider. Refer to the identity provider’s documentation for more information.
For example, you could copy the contents of the public JWK in a field in the provider’s service configuration, or you could configure the realm’s
/oauth2/connect/rp/jwk_uriendpoint, which exposes the client’s public keys.Configure the realm’s
/oauth2/connect/rp/jwk_uriendpoint in the provider, which exposes the client’s public keys. Refer to the provider’s documentation for more information.
Possible values are:
JSON-
The provider’s
userinfoendpoint returns a JSON object. SIGNED_JWT-
The provider’s
userinfoendpoint returns a signed JWT. SIGNED_THEN_ENCRYPTED_JWT-
The provider’s
userinfoendpoint returns a signed, then encrypted JWT.
-
- JWKS URI Endpoint
-
The URI that contains the public keys of the identity provider. AM will use these keys to verify signatures, or to encrypt objects.
Configure this field when:
-
Client Authentication Method is set to
ENCRYPTED_PRIVATE_KEY_JWT. -
Encrypt Request Parameter JWT is enabled.
-
User Info Response Format is set to
SIGNED_JWTorSIGNED_THEN_ENCRYPTED_JWT.
Required: No.
-
- Claims
-
Any claims on the request object, in JSON format. These claims must conform to the claims request parameter, as defined in the OpenID Connect specification.
- JWT Signing Algorithm
-
The signing algorithm supported by the provider that AM use to sign the following:
-
Client authentication JWTs when Client Authentication Method is set to
PRIVATE_KEY_JWT. -
(OpenID Connect providers only) Request JWTs when Request Parameter JWT Option is set to
VALUEorREFERENCE.
Obtain a list of the supported algorithms from the provider’s
.well-knownendpoint. SelectNONEif the client will encrypt the JWT with the Direct AES Encryption method, because the signature will be redundant.
Required: No. -
- JWT Encryption Algorithm
-
The encryption algorithm supported by the provider that AM should use to encrypt client authentication JWTs when Client Authentication Method is set to
PRIVATE_KEY_JWT, and (OpenID Connect providers only) request JWTs when Request Parameter JWT Option is set toVALUEorREFERENCE.If set to
NONE, AM will not encrypt the JWTs. Obtain a list of the supported algorithms from the provider’s.well-knownendpoint. Configure the algorithms exposed in this field using the AM advanced server property, openam.private.key.jwt.encryption.algorithm.whitelist.How do I configure advanced server properties?
-
To configure advanced server properties for all instances in the AM environment, go to Configure > Server Defaults > Advanced in the AM admin UI.
-
To configure advanced server properties for a specific instance, go to Deployment > Servers > Server Name > Advanced.
If the property you want to add or edit is already configured, click on the pencil () button to edit it. When you are finished, click on the tick () button.
Save your changes.
Required: No.
-
- JWT Encryption Method
-
The encryption algorithm supported by the provider that AM should use to encrypt the following:
-
Client authentication JWTs when Client Authentication Method is set to
PRIVATE_KEY_JWT. -
(OpenID Connect providers only) Request JWTs when Request Parameter JWT Option is set to
VALUEorREFERENCE.
Use in conjunction with
JWT Encryption Algorithm. Obtain a list of the supported methods from the provider’s.well-knownendpoint.Required: No.
-
- Private Key JWT Expiration Time (seconds)
-
The amount of time, in seconds, that AM will cache the client authentication JWT before creating a new one.
Caching the JWT avoids creating a new one for every client authentication. However, it may also become invalid if the provider changes it configuration.
Required: No.
- Response Mode
-
(OpenID Connect providers only) Specify the way the provider will return ID tokens to AM. Possible values are:
-
DEFAULT. The provider returns the ID token as query parameters, as explained in the OpenID Connect Core 1.0 incorporating errata set 1 specification.Most preconfigured providers use the
DEFAULTresponse mode. -
FORM_POST. The provider returns the ID token by submitting an HTML form using the HTTP POST method, as explained in the OAuth 2.0 Form Post Response Mode specification.When using this response mode, add the
/oauth2/client/form_post/ClientConfigNameURI to the Redirect URL, where ClientConfigName is the name of the social identity provider client that you are configuring. For example,https://platform.example.com:8443/am/oauth2/client/form_post/myAppleClient.By default, the
form_postendpoint processes the post data, encrypts it, and redirects with it back to the authentication tree to resume authentication.However, environments using custom login pages need to configure the Redirect after form post URL property to redirect back to the custom login pages.
The
/oauth2/client/form_postdoes not require authentication. Protect it from denial of service (DoS) attacks by limiting the rate at which it can take connections in your load balancer or proxy.If you configured AM with AES Key Wrap encryption, you must configure the
org.forgerock.openam.encryption.useextractandexpandproperty.For more information, refer to Use stronger encryption algorithms.
Required: Yes.
-
- Certificate Revocation Checking Options
-
Specify one or more options to be used by the TLS certificate revocation checking mechanism.
The possible values are:
-
ONLY_END_ENTITY: Only check the revocation status of end-entity certificates. -
PREFER_CRLS: Prefer certificate revocation lists (CRLs) to Online Certificate Status Protocol (OCSP). -
NO_FALLBACK: Disable the fallback mechanism. -
SOFT_FAIL: Allow revocation check to succeed if the revocation status cannot be determined due to a network error. -
DISABLE_REVOCATION_CHECKING: Disable all revocation checking.
Including
DISABLE_REVOCATION_CHECKINGas one of the options will prevent any revocation checking. For further details of the other options, refer to: PKIXRevocationChecker.Option.If no options are selected, the default behavior is to enable revocation checking with
SOFT_FAIL.If the certificate does not specify any OCSP or CRL endpoints, the revocation checking will hard fail even if the
SOFT_FAILoption is enabled. In this case, an administrator could disable revocation checking. -
- Use custom trust store
-
Specifies whether a custom truststore is used to verify the server certificate of the
.well-knownendpoint or JWKs URI of an OpenID provider (OP) in a TLS handshake.If enabled, a secret label is dynamically generated using the alphanumeric characters of the client configuration name. For example, a client configuration named
sampleOidcConfigresults in a secret label ofam.services.oidc.reliant.party.sampleOidcConfig.truststore.Note that the generated secret label must then be mapped to an alias that exists in the realm secret store.
If this setting isn’t enabled, AM uses the default truststore to verify the server certificate.
- Request Native App for UserInfo
-
(Apple SSO) When enabled, this flag indicates that the native app can send the user’s
userinfoin JSON format.Apple returns the
userinfoonly once, when the user first consents to send their details, and not on subsequent authentication attempts. In addition, the user has the option not to consent to Apple sending theiruserinfo.If you are progressively profiling the
userinfowith data from other social providers—usually, using a Patch Object node--there is a risk of overwriting the user’s details with blank values when the user authenticates through Apple SSO.To mitigate this risk, you can add a Scripted Decision node to your authentication journey to assess whether
userinfois provided.How do I use a Scripted Decision node to check
userinfo?The normalized-profile-to-managed-user.js and normalized-profile-to-managed-user.groovy scripts set a boolean flag (
nameEmptyOrNull) that indicates whether Apple returned the user’sfirstNameandlastName.Add a Scripted Decision node to your journey that evaluates the flag and sets the outcome accordingly; for example:
-
Next-generation
-
Legacy
if (nodeState.get('nameEmptyOrNull')) { action.goTo("true"); } else { action.goTo("false"); }javascriptvar fr = JavaImporter(org.forgerock.openam.auth.node.api.Action); if (nodeState.get('nameEmptyOrNull')) { action = fr.Action.goTo("true").build(); } else { action = fr.Action.goTo("false").build(); }javascriptYou can now configure your journey to patch the
userinfoobject based on the outcome of the Scripted Decision node.If you need to progressively profile the user information on every authentication, regardless of whether the user’s first name and last name are returned by the OIDC provider, you can use another Scripted Decision node that does the following:
-
If the user details aren’t present, route the
userinfopatch through a Patch Object node configured to ignore thefirstNameandlastName. (In the Ignored Fields list, addgivenNameto ignore thefirstNameandsnto ignore thelastName.) -
If the user details are present, route the
userinfopatch through a Patch Object node that patches the full object.
Learn more in First name and last name get blanked out when signing in to Advanced Identity Cloud or PingAM using Apple social sign-on in the Knowledge Base.
Required: No.
-
- UI Config Properties
-
Specifies a map of properties defined and consumed in the UI. The map affects how the identity provider’s logo will show on the login page.
AM common end user UI properties
-
buttonImage: A relative path to an image in the End User UI. -
buttonCustomStyle: Any custom CSS you wish to apply to the button outside of normal End User UI styling. -
buttonClass: Adds the specified class to the identity provider button, for any additional styling you want to apply. -
buttonCustomStyleHover: Adds custom styling when the cursor is hovering over the button. -
buttonDisplayName: The name of the identity provider, which will be included either on the button or in the button’saltattribute, depending on styling. -
iconFontColor: The color of the icon. You can use methods supported in CSS (such aswhite, or#ffffff). -
iconClass: Adds the specified class to the identity provider icon, for any additional styling you want to apply. -
iconBackground: The color for the background of the icon. You can use methods supported in CSS (such aswhite, or#ffffff).
Required: Yes.
-
- Transform Script
-
A script to convert the provider’s raw profile object into a normalized object.
Each social identity provider returns different user profile information using their own attribute names.
For example, Google’s OIDC
/userinfoendpoint returns claims, which AM stores in arawProfileobject. The followinggoogle-profile-normalization.groovyscript maps the attributes of this object to AM profile attributes:import static org.forgerock.json.JsonValue.field import static org.forgerock.json.JsonValue.json import static org.forgerock.json.JsonValue.object return json(object( field("id", rawProfile.sub), field("displayName", rawProfile.name), field("givenName", rawProfile.given_name), field("familyName", rawProfile.family_name), field("photoUrl", rawProfile.picture), field("email", rawProfile.email), field("username", rawProfile.email), field("locale", rawProfile.locale)))groovyThe script returns a JSON object containing normalized attributes in the following format:
("<platformAttributeName>", rawProfile.<providerAttributeName>)For example,
idis the platform attribute name, whilerawProfile.subis the field received from the provider.Even if field names are the same, such as
emailandrawProfile.email, they still need to be mapped for them to be included in the returned JSON object.AM provides default scripts for other preconfigured identity providers. To view the bindings and expected return values, find the
<identity provider>-profile-normalization.*scripts in Sample scripts.To write your own script in Groovy or Javascript for an identity provider, go to Realms > Realm Name > Scripts, and use the provided scripts as a reference.
When a user authenticates, the social authentication journey calls another transformation script set in the Social Provider Handler node to convert the attributes again; this time into an identity object that AM can process.
Social authentication nodes expect every attribute to have a value. In other words, the attributes returned by the identity provider cannot be empty or
null, or the journey will end with an error.For example, if a user tries to log in using Google as the identity provider, but they did not configure a surname in their account, Google returns
nullas the value of thefamilyNamefor the identity, and social authentication fails.Ensure all users have their social profiles configured correctly, or modify the transformation scripts so that they don’t collect null or empty attributes.
Required: Yes
- Issuer comparison check
-
(OpenID Connect providers only) Determines how the expected issuer value should match the actual value of the
issclaim:-
EXACT: AM performs a string comparison between the expected and actual issuer values, which must result in an exact match. -
REGEX: AM evaluates the expected issuer value as a regular expression, against which the actual value must match.This lets social identity providers use a common issuer value for multiple tenants, which is replaced with a unique value during the OpenID Connection authentication flow. For example,
^https://login.microsoftonline.com/(.*)/v2.0$is successfully matched againsthttps://login.microsoftonline.com/tenant-d5c6a592-eec6-47f0/v2.0.Consider the performance impact when constructing regular expressions as the comparison is performed for each social identity provider interaction.
Also, ensure the regular expression is as specific as possible to avoid matching against incorrect issuer values.
-
Authentication module properties
This page provides a reference to configuration properties for AM authentication modules.
Active Directory module properties
amster service name: ActiveDirectoryModule
ssoadm service name: sunAMAuthADService
- Primary ActiveDirectory Server, Secondary ActiveDirectory Server
-
Specify the primary and secondary directory server(s).
Both properties take more than one value, allowing more than one primary or secondary remote server, respectively.
Directory servers generally use built-in data replication for high availability. Thus, a directory service typically consists of a pool of replicas to which AM can connect to retrieve and update directory data. AM attempts to contact the primary server(s) first, but if unavailable, AM attempts to contact the secondary servers.
For the current AM server, specify each directory server in the format
server:port. For other AM servers in the deployment, define each server aslocal_server_name | server:port. For example, if theserverishttps://openam.example.com:8443/openam, and the directory server is accessible atopendj.example.com:1636, enter the value asopenam.example.com|opendj.example.com:1636.Assuming a multi-data center environment, AM determines priority within the primary and secondary remote servers as follows:
-
LDAP servers that are mapped to the current AM instance have the highest priority.
For example, if you are connected to
openam1.example.comandldap1.example.comis mapped to that AM instance, then AM usesldap1.example.com. -
LDAP servers that are not specifically mapped to a given AM instance have the next highest priority.
For example, if you have another LDAP server,
ldap2.example.com, that is not connected to a specific AM server and ifldap1.example.comis unavailable, AM connects to the next highest priority LDAP server,ldap2.example.com. -
LDAP servers that are mapped to different AM instances have the lowest priority.
For example, if
ldap3.example.comis connected toopenam3.example.comandldap1.example.comandldap2.example.comare unavailable, thenopenam1.example.comconnects toldap3.example.com.ssoadmattributes are: primary isiplanet-am-auth-ldap-server; secondary isiplanet-am-auth-ldap-server2.
-
- DN to Start User Search
-
Specifies the base DN from which AM searches for users to authenticate.
LDAP data is organized hierarchically, similar to a file system on Windows or UNIX. More specific DNs likely result in better performance. When configuring the module for a particular part of the organization, you can start searches from a specific organizational unit, such as
OU=sales,DC=example,DC=com.If multiple entries exist with identical search attribute values, ensure this value is specific enough to return a single entry.
amsterattribute:userSearchStartDNssoadmattribute:iplanet-am-auth-ldap-base-dn
- Bind User DN, Bind User Password
-
Specify the user and password of the administration account used for authentication to the directory server.
If AM stores attributes in the directory, for example, to manage account lockout, or if the directory requires that AM authenticate in order to read users' attributes, then AM needs the DN and password to authenticate to the directory.
Make sure that the password is correct before you logout. If it is incorrect, you will be locked out and you will need to log in with the superuser DN. By default, this is
uid=amAdmin,ou=People,AM-deploy-base, whereAM-deploy-basewas set during AM configuration.amsterattributes:userBindDNanduserBindPasswordssoadmattributes:iplanet-am-auth-ldap-bind-dnandiplanet-am-auth-ldap-bind-passwd
- Attribute Used to Retrieve User Profile
-
LDAP uses this attribute to search for the profile of an authenticated user. Usually, this is the same attribute used to find the user account, such as the value set as the
uidin AM. For example, where the attribute is set tomail, the LDAP module searchesCN=Users,DC=example,DC=comwith a filter"(MAIL=bjensen@example.com)", and the directory returns the user profile that matchesMAIL=bjensen@example.com.The attribute is only used if User Profile is set to
RequiredandReturn User DN to DataStoreis not enabled.amsterattribute:userProfileRetrievalAttributessoadmattribute:iplanet-am-auth-ldap-user-naming-attribute
- Attributes Used to Search for a User to be Authenticated
-
The attributes specified in this list define the LDAP search filter. Multiple attribute values mean the user can authenticate with any one of the values. For example, if you have both
uidandmail, then Barbara Jensen can authenticate with eitherbjensenorbjensen@example.com.amsterattribute:userSearchAttributesssoadmattribute:iplanet-am-auth-ldap-user-search-attributes
- User Search Filter
-
The User Search Filter text box provides a more complex filter. For example, if you search using
mailand add the User Search Filter(objectClass=inetOrgPerson), then AM uses the resulting search filter(&(mail=address)(objectClass=inetOrgPerson)), where address is the mail address provided by the user.amsterattribute:userSearchAttributesssoadmattribute:iplanet-am-auth-ldap-search-filter
- Search Scope
-
This attribute defines the level of directory that will be searched for a matching profile. You can set the search to run at a high level or against a specific area:
-
OBJECT searches only for the entry specified as the 'DN to Start User Search'.
-
ONELEVEL searches only the entries that are direct children of that object.
-
SUBTREE searches the entry specified and all entries at levels below.
ssoadmattribute:iplanet-am-auth-ldap-search-scope -
- LDAP Connection Mode
-
If you want to initiate secure communications to data stores using SSL or StartTLS, AM must be able to trust the server’s certificates, either because the certificates were signed by a CA whose certificate is already included in the trust store used by the container where AM runs, or because you imported the certificates into the trust store.
To let users change passwords through AM, Active Directory requires that you connect over SSL. The default LDAP port is 389. If you are connecting to Active Directory over SSL, the default LDAPS port is 636.
For SSL or TLS security, enable the SSL/TLS Access to Active Directory Server property.
ssoadmattribute:openam-auth-ldap-connection-modePossible values:
LDAP,LDAPS, andStartTLS
- Return User DN to DataStore
-
If User Profile is set to
Required, this attribute determines whether the DN or the username is returned as the authentication principal.When enabled, the module returns the DN rather than the User ID or the value set in
Attribute Used to Retrieve User Profile. The returned value is then used to make the request to retrieve the profile attributes from the user store.amsterattribute:returnUserDNssoadmattribute:iplanet-am-auth-ldap-return-user-dn
- User Creation Attributes
-
This list of attributes defines the mapping of internal attribute names to external attribute names for dynamic profile creation. The attributes retrieved from the user’s authenticated profile are mapped against the values that will be provisioned into their matching account in the data store. This list does not include
uidmappings.The format of the list is
internal_attr1|external_attr1.amsterattribute:profileAttributeMappingsssoadmattribute:iplanet-am-ldap-user-creation-attr-list
- Trust All Server Certificates
-
When enabled, the module trusts all server certificates, including self-signed certificates.
amsterattribute:trustAllServerCertificatesssoadmattribute:iplanet-am-auth-ldap-ssl-trust-all
- LDAP Connection Heartbeat Interval
-
Specifies how often AM should send a heartbeat request to the directory server to ensure that the connection does not remain idle. Some network administrators configure firewalls and load balancers to drop connections that are idle for too long. You can turn this off by setting the value to 0. To set the units for the interval, use LDAP Connection Heartbeat Time Unit.
Default: 1
amsterattribute:connectionHeartbeatIntervalssoadmattribute:openam-auth-ldap-heartbeat-interval
- LDAP Connection Heartbeat Time Unit
-
Specifies the time unit corresponding to LDAP Connection Heartbeat Interval. Possible values are
SECONDS,MINUTES, andHOURS.amsterattribute:connectionHeartbeatTimeUnitssoadmattribute:openam-auth-ldap-heartbeat-timeunit
- LDAP operations timeout
-
Defines the timeout, in seconds, that AM should wait for a response from the directory server.
Default: 0 (means no timeout)
amsterattribute:operationTimeoutssoadmattribute:openam-auth-ldap-operation-timeout
- Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:iplanet-am-auth-ldap-auth-level
- Stop LDAP Binds after in-memory lockout
-
If enabled, prevent AM from sending further bind requests to the LDAP Server when the user is locked out through a duration lockout.
amsterattribute:stopLdapbindAfterInmemoryLockedEnabledssoadmattribute:openam-auth-stop-ldap-bind-after-inmemory-locked-enabled
Adaptive Risk authentication module properties
amster service name: AdaptiveRiskModule
ssoadm service name: sunAMAuthAdaptiveService
General
The following properties are available under the General tab:
- Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:openam-auth-adaptive-auth-level - Risk Threshold
-
Sets the risk threshold score. If the sum of the scores is greater than the threshold, the Adaptive Risk module fails.
Default: 1
amsterattribute:riskThresholdssoadmattribute:openam-auth-adaptive-auth-threshold
Failed Authentications
The following properties are available under the Failed Authentications tab:
- Failed Authentication Check
-
When enabled, checks the user profile for authentication failures since the last successful login. This check therefore requires AM to have access to the user profile, and Account Lockout to be enabled (otherwise, AM does not record authentication failures).
amsterattribute:failedAuthenticationCheckEnabledssoadmattribute:openam-auth-adaptive-failure-check - Score
-
Sets the value to add to the total score if the user fails the Failed Authentication Check. Default: 1
amsterattribute:failureScoressoadmattribute:openam-auth-adaptive-failure-score - Invert Result
-
When enabled, adds the score to the total score if the user passes the Failed Authentication Check.
amsterattribute:invertFailureScoressoadmattribute:openam-auth-adaptive-failure-invert
IP Address Range
The following properties are available under the IP Address Range tab:
- IP Range Check
-
When enabled, checks whether the client IP address is within one of the specified IP Ranges.
amsterattribute:ipRangeCheckEnabledssoadmattribute:openam-auth-adaptive-ip-range-check - IP Range
-
For IPv4, specifies a list of IP ranges either in CIDR-style notation (
x.x.x.x/YY) or as a range from one address to another (x.x.x.x-y.y.y.y, meaning from x.x.x.x to y.y.y.y).For IPv6, specifies a list of IP ranges either in CIDR-style notation (
X:X:X:X:X:X:X:X/YY) or as a range from one address to another (X:X:X:X:X:X:X:X-Y:Y:Y:Y:Y:Y:Y:Y, meaning from X:X:X:X:X:X:X:X to Y:Y:Y:Y:Y:Y:Y:Y).amsterattribute:ipRangessoadmattribute:openam-auth-adaptive-ip-range-range - Score
-
Sets the value to add to the total score if the user fails the IP Range Check.
amsterattribute:ipRangeScoressoadmattribute:openam-auth-adaptive-ip-range-score - Invert Result
-
When enabled, adds the Score to the total score if the user passes the IP Range Check.
amsterattribute:invertIPRangeScoreEnabledssoadmattribute:openam-auth-adaptive-ip-range-invert
IP Address History
The following properties are available under the IP Address History tab:
- IP History Check
-
When enabled, checks whether the client IP address matches one of the known values stored on the profile attribute you specify. This check therefore requires that AM have access to the user profile.
amsterattribute:ipHistoryCheckEnabledssoadmattribute:openam-auth-adaptive-ip-history-check - History size
-
Specifies how many IP address values to retain on the profile attribute you specify.
Default: 5
amsterattribute:ipHistoryCountssoadmattribute:openam-auth-ip-adaptive-history-count - Profile Attribute Name
-
Specifies the name of the user profile attribute in which to store known IP addresses. Ensure the specified attribute exists in your user data store; the
iphistoryattribute does not exist by default, and it is not created when performing AM schema updates.Default:
iphistoryamsterattribute:ipHistoryProfileAttributessoadmattribute:openam-auth-adaptive-ip-history-attribute - Save Successful IP Address
-
When enabled, saves new client IP addresses to the known IP address list following successful authentication.
amsterattribute:saveSuccessfulIPssoadmattribute:openam-auth-adaptive-ip-history-save - Score
-
Sets the value to add to the total score if the user fails the IP History Check.
Default: 1
amsterattribute:ipHistoryScoressoadmattribute:openam-auth-adaptive-ip-history-score - Invert Result
-
When enabled, adds the Score to the total score if the user passes the IP History Check.
amsterattribute:invertIPHistoryScoressoadmattribute:openam-auth-adaptive-ip-history-invert
Known Cookie
The following properties are available under the Known Cookie tab:
- Cookie Value Check
-
When enabled, checks whether the client browser request has the specified cookie and optional cookie value.
amsterattribute:knownCookieCheckEnabledssoadmattribute:openam-auth-adaptive-known-cookie-check - Cookie Name
-
Specifies the name of the cookie for which AM checks when you enable the Cookie Value Check.
amsterattribute:knownCookieNamessoadmattribute:openam-auth-adaptive-known-cookie-name - Cookie Value
-
Specifies the value of the cookie for which AM checks. If no value is specified, AM does not check the cookie value.
amsterattribute:knownCookieValuessoadmattribute:openam-auth-adaptive-known-cookie-value - Save Cookie Value on Successful Login
-
When enabled, saves the cookie as specified in the client’s browser following successful authentication. If no Cookie Value is specified, the value is set to 1.
amsterattribute:createKnownCookieOnSuccessfulLoginssoadmattribute:openam-auth-adaptive-known-cookie-save - Score
-
Sets the value to add to the total score if user passes the Cookie Value Check.
Default: 1
amsterattribute:knownCookieScoressoadmattribute:openam-auth-adaptive-known-cookie-score - Invert Result
-
When enabled, adds the Score to the total score if the user passes the Cookie Value Check.
amsterattribute:invertKnownCookieScoressoadmattribute:openam-auth-adaptive-known-cookie-invert
Device Cookie
The following properties are available under the Device Cookie tab:
- Device Registration Cookie Check
-
When enabled, the cookie check passes if the client request contains the cookie specified in Cookie Name.
amsterattribute:deviceCookieCheckEnabledssoadmattribute:openam-auth-adaptive-device-cookie-check - Cookie Name
-
Specifies the name of the cookie for the Device Registration Cookie Check.
Default: Device
amsterattribute:deviceCookieNamessoadmattribute:openam-auth-adaptive-device-cookie-name - Save Device Registration on Successful Login
-
When enabled, saves the specified cookie with a hashed device identifier value in the client’s browser following successful authentication.
amsterattribute:saveDeviceCookieValueOnSuccessfulLoginssoadmattribute:openam-auth-adaptive-device-cookie-save - Score
-
Sets the value to add to the total score if the user fails the Device Registration Cookie Check.
Default: 1
amsterattribute:deviceCookieScoressoadmattribute:openam-auth-adaptive-device-cookie-score - Invert Result
-
When enabled, adds the Score to the total score if the user passes the Device Registration Cookie Check.
amsterattribute:invertDeviceCookieScoressoadmattribute:openam-auth-adaptive-device-cookie-invert
Time Since Last Login
The following properties are available under the Time Since Last Login tab:
- Time since Last login Check
-
When enabled, checks whether the client browser request has the specified cookie that holds the encrypted last login time, and check that the last login time is more recent than a maximum number of days you specify.
amsterattribute:timeSinceLastLoginCheckEnabledssoadmattribute:openam-auth-adaptive-time-since-last-login-check - Cookie Name
-
Specifies the name of the cookie holding the encrypted last login time value.
amsterattribute:timeSinceLastLoginCookieNamessoadmattribute:openam-auth-adaptive-time-since-last-login-cookie-name - Max Time since Last login
-
Specifies a threshold age of the last login time in days. If the client’s last login time is more recent than the number of days specified, then the client successfully passes the check.
amsterattribute:maxTimeSinceLastLoginssoadmattribute:openam-auth-adaptive-time-since-last-login-value - Save time of Successful Login
-
When enabled, saves the specified cookie with the current time encrypted as the last login value in the client’s browser following successful authentication.
amsterattribute:saveLastLoginTimeOnSuccessfulLoginssoadmattribute:openam-auth-adaptive-time-since-last-login-save - Score
-
Sets the value to add to the total score if the user fails the Time Since Last Login Check.
Default: 1
amsterattribute:timeSinceLastLoginScoressoadmattribute:openam-auth-adaptive-time-since-last-login-score - Invert Result
-
When enabled, adds the Score to the total score if the user passes the Time Since Last Login Check.
amsterattribute:invertTimeSinceLastLoginScoressoadmattribute:openam-auth-adaptive-time-since-last-login-invert
Profile Attribute
The following properties are available under the Profile Attribute tab:
- Profile Risk Attribute check
-
When enabled, checks whether the user profile contains the specified attribute and value.
amsterattribute:profileRiskAttributeCheckEnabledssoadmattribute:openam-auth-adaptive-risk-attribute-check - Attribute Name
-
Specifies the attribute to check on the user profile for the specified value.
amsterattribute:profileRiskAttributeNamessoadmattribute:openam-auth-adaptive-risk-attribute-name - Attribute Value
-
Specifies the value to match on the profile attribute. If the attribute is multi-valued, a single match is sufficient to pass the check.
amsterattribute:profileRiskAttributeValuessoadmattribute:openam-auth-adaptive-risk-attribute-value - Score
-
Sets the value to add to the total score if the user fails the Profile Risk Attribute Check.
Default: 1
amsterattribute:profileRiskAttributeScoressoadmattribute:openam-auth-adaptive-risk-attribute-score - Invert Result
-
When enabled, adds the Score to the total score if the user passes the Profile Risk Attribute Check.
amsterattribute:invertProfileRiskAttributeScoressoadmattribute:openam-auth-adaptive-risk-attribute-invert
Geo Location
The following properties are available under the Geo Location tab:
- Geolocation Country Code Check
-
When enabled, checks whether the client IP address location matches a country specified in the Valid Country Codes list.
ssoadmattribute:forgerock-am-auth-adaptive-geo-location-check - Geolocation Database Location
-
Path to GeoIP data file used to convert IP addresses to country locations. The geolocation database is not packaged with AM. You can download the GeoIP Country database from MaxMind. Use the binary
.mmdbfile format, rather than.csv. You can use the GeoLite Country database for testing.amsterattribute:geolocationDatabaseLocationssoadmattribute:openam-auth-adaptive-geo-location-database - Valid Country Codes
-
Specifies the list of country codes to match. Use
|to separate multiple values.ssoadmattribute:openam-auth-adaptive-geo-location-values. - Score
-
Value to add to the total score if the user fails the Geolocation Country Code Check.
Default: 1
amsterattribute:geolocationScoressoadmattribute:openam-auth-adaptive-geo-location-score - Invert Result
-
When enabled, adds the Score to the total score if the user passes the Geolocation Country Code Check.
amsterattribute:invertGeolocationScoressoadmattribute:openam-auth-adaptive-geo-location-invert
Request Header
The following properties are available under the Request Header tab:
- Request Header Check
-
When enabled, checks whether the client browser request has the specified header with the correct value.
amsterattribute:requestHeaderCheckEnabledssoadmattribute:openam-auth-adaptive-req-header-check - Request Header Name
-
Specifies the name of the request header for the Request Header Check.
amsterattribute:requestHeaderNamessoadmattribute:openam-auth-adaptive-req-header-name - Request Header Value
-
Specifies the value of the request header for the Request Header Check.
amsterattribute:requestHeaderValuessoadmattribute:openam-auth-adaptive-req-header-value - Score
-
Value to add to the total score if the user fails the Request Header Check.
Default: 1
amsterattribute:requestHeaderScoressoadmattribute:openam-auth-adaptive-req-header-score - Invert Result
-
When enabled, adds the Score to the total score if the user passes the Request Header Check.
amsterattribute:invertRequestHeaderScoressoadmattribute:openam-auth-adaptive-req-header-invert
Amster authentication module properties
amster service name: AmsterModule
ssoadm service name: iPlanetAMAuthAmsterService
- Authorized Keys
-
Specifies the location of the
authorized_keysfile that contains the private and public keys used to validate remoteamsterclient connections.The default location for the
authorized_keysfile is the/path/to/openam/security/keys/amster/directory. Its content is similar to an OpenSSHauthorized_keysfile.amsterattribute:forgerock-am-auth-amster-authorized-keys - Enabled
-
When enabled, allows
amsterclients to authenticate using PKI. When disabled, allowsamsterclients to authenticate using interactive login only.amsterattribute:forgerock-am-auth-amster-enabled - Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:forgerock-am-auth-amster-auth-level
Anonymous authentication module properties
amster service name: AnonymousModule
ssoadm service name: iPlanetAMAuthAnonymousService
- Valid Anonymous Users
-
Specifies the list of valid anonymous user IDs that can log in without submitting a password.
amsterattribute:validAnonymousUsersssoadmattribute:iplanet-am-auth-anonymous-users-listWhen a user accesses the default module instance login URL, the module prompts the user to enter a valid anonymous user name.
The default module instance login URL is defined as follows:
protocol://hostname:port/deploy_URI/XUI/?module=Anonymous&org=org_name#login
- Default Anonymous User Name
-
Specifies the user ID assigned by the module if the Valid Anonymous Users list is empty. The default value is
anonymous. Note that the anonymous user must be defined in the realm, and its user status must beActive.amsterattribute:defaultAnonymousUsernamessoadmattribute:iplanet-am-auth-anonymous-default-user-name - Case Sensitive User IDs
-
When enabled, determines whether case matters for anonymous user IDs.
amsterattribute:caseSensitiveUsernameMatchingEnabledssoadmattribute:iplanet-am-auth-anonymous-case-sensitive - Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 (default) to any positive integer and is set for each authentication method. The higher number corresponds to a higher level of authentication. If you configured your authentication levels from a 0 to 5 scale, then an authentication level of 5 will require the highest level of authentication.
After a user has authenticated, AM stores the authentication level in the session token. When the user attempts to access a protected resource, the token is presented to the application. The application uses the token’s value to determine if the user has the correct authentication level required to access the resource. If the user does not have the required authentication level, the application can prompt the user to authenticate with a higher authentication level.
amsterattribute:authenticationLevelssoadmattribute:iplanet-am-auth-anonymous-auth-level
Certificate authentication module properties
amster service name: CertificateModule
ssoadm service name: iPlanetAMAuthCertService
- Match Certificate in LDAP
-
When enabled, AM searches for a match for the user’s certificate in the LDAP directory. If a match is found and not revoked according to a CRL or OCSP validation, then authentication succeeds.
amsterattribute:matchCertificateInLdapssoadmattribute:iplanet-am-auth-cert-check-cert-in-ldap - Subject DN Attribute Used to Search LDAP for Certificates
-
Indicates which attribute and value in the certificate Subject DN is used to find the LDAP entry holding the certificate.
Default: CN
amsterattribute:ldapCertificateAttributessoadmattribute:iplanet-am-auth-cert-attr-check-ldap - Match Certificate to CRL
-
When enabled, AM checks whether the certificate has been revoked according to a CRL in the LDAP directory.
amsterattribute:matchCertificateToCRLssoadmattribute:iplanet-am-auth-cert-check-crl - Issuer DN Attribute Used to Search LDAP for CRLs
-
Indicates which attribute and value in the certificate Issuer DN is used to find the CRL in the LDAP directory.
Default: CN
If only one attribute is specified, the LDAP search filter used to find the CRL based on the Subject DN of the CA certificate is
(attr-name=attr-value-in-subject-DN).For example, if the subject DN of the issuer certificate is
C=US, CN=Some CA, serialNumber=123456, and the attribute specified isCN, then the LDAP search filter used to find the CRL is(CN=Some CA).In order to distinguish among different CRLs for the same CA issuer, specify multiple attributes separated by commas (
,) in the same order they occur in the subject DN. When multiple attribute names are provided in a comma-separated list, the LDAP search filter used is(cn=attr1=attr1-value-in-subject-DN,attr2=attr2-value-in-subject-DN,…,attrN=attrN-value-in-subject-DN).For example, if the subject DN of the issuer certificate is
C=US, CN=Some CA, serialNumber=123456, and the attributes specified areCN,serialNumber, then the LDAP search filter used to find the CRL is(cn=CN=Some CA,serialNumber=123456).amsterattribute:crlMatchingCertificateAttributessoadmattribute:iplanet-am-auth-cert-attr-check-crl - HTTP Parameters for CRL Update
-
Specifies parameters to be included in any HTTP CRL call to the CA that issued the certificate.
This property supports key pairs of values separated by commas, for example,
param1=value1,param2=value2.If the client or CA contains the Issuing Distribution Point Extension, AM uses this information to retrieve the CRL from the distribution point.
amsterattribute:crlHttpParametersssoadmattribute:iplanet-am-auth-cert-param-get-crl - Match CA Certificate to CRL
-
When enabled, AM checks the CRL against the CA certificate to ensure it has not been compromised.
amsterattribute:matchCACertificateToCRLssoadmattribute:sunAMValidateCACert - Cache CRLs in memory
-
(LDAP distribution points only) When enabled, AM caches CRLs.
amsterattribute:cacheCRLsInMemoryssoadmattribute:openam-am-auth-cert-attr-cache-crl - Update CA CRLs from CRLDistributionPoint
-
When enabled, AM updates the CRLs stored in the LDAP directory store.
amsterattribute:updateCRLsFromDistributionPointssoadmattribute:openam-am-auth-cert-update-crl - OCSP Validation
-
When enabled, AM checks the revocation status of certificates using the Online Certificate Status Protocol (OCSP).
You must configure OSCP for AM under Configure > Server Defaults or Deployment > Servers > Server Name > Security.
amsterattribute:ocspValidationEnabledssoadmattribute:iplanet-am-auth-cert-check-ocsp - LDAP Server Where Certificates are Stored
-
Identifies the LDAP server that holds users; certificates. The property has the format
ldap-server:port, for example,ldap1.example.com:636. To configure a secure connection, enable the Use SSL/TLS for LDAP Access property.AM servers can be associated with LDAP servers by writing multiple chains with the format
openam_server|ldap-server:port, for example,openam.example.com|ldap1.example.com:636.amsterattribute:certificateLdapServersssoadmattribute:iplanet-am-auth-cert-ldap-provider-url - LDAP Search Start or Base DN
-
Valid base DN for the LDAP search, such as
dc=example,dc=com. To associate AM servers with§ different search base DNs, use the formatopenam_server|base_dn, for example,openam.example.com|dc=example,dc=com openam1.test.com|dc=test,dc=com.`amsterattribute:ldapSearchStartDNssoadmattribute:iplanet-am-auth-cert-start-search-loc - LDAP Server Authentication User, LDAP Server Authentication Password
-
If AM stores attributes in the LDAP directory, for example to manage account lockout, or if the LDAP directory requires that AM authenticate in order to read users' attributes, then AM needs the DN and password to authenticate to the LDAP directory.
ssoadmattributes:iplanet-am-auth-cert-principal-user, andiplanet-am-auth-cert-principal-passwd - Use SSL/TLS for LDAP Access
-
If you use SSL/TLS for LDAP access, AM must be able to trust the LDAP server certificate.
amsterattribute:sslEnabledssoadmattribute:iplanet-am-auth-cert-use-ssl - Certificate Field Used to Access User Profile
-
If the user profile is in a different entry from the user certificate, then this can be different from subject DN attribute used to find the entry with the certificate. When you select other, provide an attribute name in the Other Certificate Field Used to Access User Profile text box.
amsterattribute:certificateAttributeToProfileMappingssoadmattribute:iplanet-am-auth-cert-user-profile-mapperValid values:
subject DN,subject CN,subject UID,email address,other, andnone. - Other Certificate Field Used to Access User Profile
-
This field is only used if the Certificate Field Used to Access User Profile attribute is set to other. This field allows a custom certificate field to be used as the basis of the user search.
amsterattribute:otherCertificateAttributeToProfileMappingssoadmattribute:iplanet-am-auth-cert-user-profile-mapper-other - SubjectAltNameExt Value Type to Access User Profile
-
Specifies how to look up the user profile:
-
Let the property default to
noneto give preference to the Certificate Field Used to Access User Profile or Other Certificate Field Used to Access User Profile attributes when looking up the user profile. -
Select
RFC822Nameif you want AM to look up the user profile from an RFC 822 style name. -
Select
UPNif you want AM to look up the user profile as the User Principal Name attribute used in Active Directory.
amsterattribute:certificateAttributeProfileMappingExtensionssoadmattribute:iplanet-am-auth-cert-user-profile-mapper-ext -
- Trusted Remote Hosts
-
Defines a list of hosts trusted to send certificates to AM, such as load balancers doing SSL termination.
Valid values are
none,any, andIP_ADDR, whereIP_ADDRis one or more IP addresses of trusted hosts that can send client certificates to AM.amsterattribute:trustedRemoteHostsssoadmattribute:iplanet-am-auth-cert-gw-cert-auth-enabled - HTTP Header Name for Client Certificates
-
Specifies the name of the HTTP request header containing the certificate, which can be in one of the following formats:
-
Raw PEM-encoded.
-
PEM-encoded first, and then URL-encoded.
If Trusted Remote Hosts is set to
anyor specifies the IP address of the trusted host (for example, an SSL-terminated load balancer) that can supply client certificates to AM, the administrator must specify the header name in this attribute.amsterattribute:clientCertificateHttpHeaderNamessoadmattribute:sunAMHttpParamName -
- Use only Certificate from HTTP request header
-
When enabled, AM always uses the client certificate from the HTTP header rather than the certificate the servlet container receives during the SSL handshake.
Default: false
ssoadmattribute:iplanet-am-auth-cert-gw-cert-preferred - Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:iplanet-am-auth-cert-auth-level
Data Store authentication module properties
amster service name: DataStoreModule
ssoadm service name: sunAMAuthDataStoreService
- Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:sunAMAuthDataStoreAuthLevel
Device ID (Match) authentication module properties
amster service name: DeviceIdMatchModule
ssoadm service name: iPlanetAMAuthDeviceIdMatchService
- Client-Side Script Enabled
-
Enable Device ID (Match) to send JavaScript in an authentication page to the device to collect data about the device by a self-submitting form.
amsterattribute:clientScriptEnabledssoadmattribute:iplanet-am-auth-scripted-client-script-enabled - Client-Side Script, Server-Side Script
-
Specify the client-side and server-side Javascript scripts to use with the Device Id (Match) module.
To view and modify the contents of the scripts, go to Realms > Realm Name > Scripts and select the name of the script.
If you change the client-side script, you must make a corresponding change in the server-side script to account for the specific addition or removal of an element.
ssoadmattribute:iplanet-am-auth-scripted-client-scriptandiplanet-am-auth-scripted-server-script - Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:iplanet-am-auth-scripted-auth-level
Device ID (Save) authentication module properties
amster service name: DeviceIdSaveModule
ssoadm service name: iPlanetAMAuthDeviceIdSaveService
- Automatically store new profiles
-
When enabled, AM assumes user consent to store new profiles. After successful HOTP confirmation, AM stores the new profile automatically.
amsterattribute:autoStoreProfilesssoadmattribute:iplanet-am-auth-device-id-save-auto-store-profile - Maximum stored profile quantity
-
Sets the maximum number of stored profiles on the user’s record.
amsterattribute:maxProfilesAllowedssoadmattribute:iplanet-am-auth-device-id-save-max-profiles-allowed - Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:iplanet-am-auth-device-id-save-auth-level
Federation authentication module properties
amster service name: FederationModule
ssoadm service name: sunAMAuthFederationService
- Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:sunAMAuthFederationAuthLevel
ForgeRock Authenticator (OATH) authentication module properties
amster service name: AuthenticatorOathModule
ssoadm service name: iPlanetAMAuthAuthenticatorOATHService
Also refer to Differences between authentication modules that support HOTP.
- Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
ssoadmattribute:iplanet-am-auth-fr-oath-auth-level - One-Time Password Length
-
Sets the length of the OTP to six digits or longer. The default value is six.
amsterattribute:passwordLengthssoadmattribute:iplanet-am-auth-fr-oath-password-length - Minimum Secret Key Length
-
The minimum number of hexadecimal characters allowed for the secret key.
amsterattribute:minimumSecretKeyLengthssoadmattribute:iplanet-am-auth-fr-oath-min-secret-key-length - OATH Algorithm to Use
-
Select whether to use HOTP or TOTP. You can create an authentication chain to allow for a greater variety of devices. The default value is HOTP.
amsterattribute:oathAlgorithmssoadmattribute:iplanet-am-auth-fr-oath-algorithm - HOTP Window Size
-
The window that the OTP device and the server counter can be out of sync. For example, if the window size is 100 and the server’s last successful login was at counter value 2, then the server will accept an OTP from device counter 3 to 102. The default value is 100.
amsterattribute:hotpWindowSizessoadmattribute:iplanet-am-auth-fr-oath-hotp-window-size - Add Checksum Digit
-
Adds a checksum digit at the end of the HOTP password to verify the OTP was generated correctly. This is in addition to the actual password length. Set this only if your device supports it. The default value is No.
amsterattribute:addChecksumToOtpEnabledssoadmattribute:iplanet-am-auth-fr-oath-add-checksum - Truncation Offset
-
Advanced feature that is device-specific. Let this value default unless you know your device uses a truncation offset. The default value is -1.
amsterattribute:truncationOffsetssoadmattribute:iplanet-am-auth-fr-oath-truncation-offset - TOTP Time Step Interval
-
The time interval for which an OTP is valid. For example, if the time step interval is 30 seconds, a new OTP will be generated every 30 seconds, and an OTP will be valid for 30 seconds. The default value is 30 seconds.
amsterattribute:totpTimeStepIntervalssoadmattribute:iplanet-am-auth-fr-oath-size-of-time-step - TOTP Time Steps
-
The number of time step intervals that the system and the device can be off before password resynchronization is required. For example, if the number of TOTP time steps is 2 and the TOTP time step interval is 30 seconds, the server will allow an 89 second clock skew between the client and the server—two 30 second steps plus 29 seconds for the interval in which the OTP arrived. The default value is 2.
amsterattribute:totpTimeStepsInWindowssoadmattribute:iplanet-am-auth-fr-oath-steps-in-window - One Time Password Max Retry
-
The number of times entry of the OTP may be attempted. Minimum is 1, maximum is 10.
Default: 3
amsterattribute:oathOtpMaxRetryssoadmattribute:forgerock-oath-max-retry - Maximum Allowed Clock Drift
-
The maximum acceptable clock skew before authentication fails. When this value is exceeded, the user must re-register the device.
amsterattribute:totpMaximumClockDriftssoadmattribute:openam-auth-fr-oath-maximum-clock-drift - Name of the Issuer
-
A value that appears as an identifier on the user’s device. Common choices are a company name, a web site, or an AM realm.
amsterattribute:oathIssuerNamessoadmattribute:openam-auth-fr-oath-issuer-name
ForgeRock Authenticator (Push) authentication module properties
amster service name: AuthenticatorPushModule
ssoadm service name: iPlanetAMAuthAuthenticatorPushService
- Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:forgerock-am-auth-authenticatorpush-auth-level - Return Message Timeout (ms)
-
The period of time (in milliseconds) within which a push notification should be replied to.
Default:
120000amsterattribute:timeoutInMilliSeccondsssoadmattribute:forgerock-am-auth-push-message-response-timeout - Login Message
-
Text content of the push message, which is used for the notification displayed on the registered device. The following variables can be used in the message:
{{user}}-
Replaced with the username value of the account registered in the ForgeRock Authenticator app, for example Demo.
{{issuer}}-
Replaced with the issuer value of the account registered in the ForgeRock Authenticator app, for example ForgeRock.
Default:
Login attempt from {{user}} at {{issuer}}amsterattribute:pushMessagessoadmattribute:forgerock-am-auth-push-message
ForgeRock Authenticator (Push) registration authentication module properties
amster service name: AuthenticatorPushRegistrationModule
ssoadm service name: iPlanetAMAuthAuthenticatorPushRegistrationService
- Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:forgerock-am-auth-push-reg-auth-level - Issuer Name
-
A value that appears as an identifier on the user’s device. Common choices are a company name, a web site, or an AM realm.
amsterattribute:issuerssoadmattribute:forgerock-am-auth-push-reg-issuer - Registration Response Timeout (ms)
-
The period of time (in milliseconds) to wait for a response to the registration QR code. If no response is received during this time the QR code times out and the registration process fails.
Default:
120000amsterattribute:timeoutInMilliSeccondsssoadmattribute:forgerock-am-auth-push-message-registration-response-timeout - Background Color
-
The background color in hex notation to display behind the issuer’s logo within the ForgeRock Authenticator app.
Default:
#519387amsterattribute:bgcolourssoadmattribute:forgerock-am-auth-hex-bgcolour - Image URL
-
The location of an image to download and display as the issuer’s logo within the ForgeRock Authenticator app.
amsterattribute:imgUrlssoadmattribute:forgerock-am-auth-img-url - App Store App URL
-
URL of the app to download on the App Store.
Default:
https://itunes.apple.com/app/forgerock-authenticator/id1038442926(the ForgeRock Authenticator app)amsterattribute:appleLinkssoadmattribute:forgerock-am-auth-apple-link - Google Play URL
-
URL of the app to download on Google Play.
Default:
https://play.google.com/store/apps/details?id=com.forgerock.authenticator(the ForgeRock Authenticator app)amsterattribute:googleLinkssoadmattribute:forgerock-am-auth-google-link
HOTP authentication module properties
amster service name: HotpModule
ssoadm service name: sunAMAuthHOTPService
- Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:sunAMAuthHOTPAuthLevel - SMS Gateway Implementation Class
-
Specifies the class the HOTP module uses to send SMS or email messages. Specify a class that implements the
com.sun.identity.authentication.modules.hotp.SMSGatewayinterface to customize the SMS gateway implementation.amsterattribute:smsGatewayClassssoadmattribute:sunAMAuthHOTPSMSGatewayImplClassName - Mail Server Host Name
-
Specifies the hostname of the mail server supporting SMTP for electronic mail.
amsterattribute:smtpHostnamessoadmattribute:sunAMAuthHOTPSMTPHostName - Mail Server Host Port
-
Specifies the outgoing mail server port. The default port is 25, 465 (when connecting over SSL), or 587 (for StartTLS).
amsterattribute:smtpHostPortssoadmattribute:sunAMAuthHOTPSMTPHostPort - Mail Server Authentication Username
-
Specifies the username for AM to connect to the mail server.
amsterattribute:smtpUsernamessoadmattribute:sunAMAuthHOTPSMTPUserName - Mail Server Authentication Password
-
Specifies the password for AM to connect to the mail server.
amsterattribute:smtpUserPasswordssoadmattribute:sunAMAuthHOTPSMTPUserPassword - Mail Server Secure Connection
-
Specifies whether to connect to the mail server securely. If enabled, AM must be able to trust the server certificate.
The possible values for this property are:
SSL
Non SSL
Start TLSamsterattribute:smtpSslEnabledssoadmattribute:sunAMAuthHOTPSMTPSSLEnabled - Email From Address
-
Specifies the
From:address when sending a one-time password by mail.amsterattribute:smtpFromAddressssoadmattribute:sunAMAuthHOTPSMTPFromAddress - One-Time Password Validity Length (in minutes)
-
Specifies the amount of time, in minutes, the one-time passwords are valid after they are generated. The default is
5minutes.amsterattribute:otpValidityDurationssoadmattribute:sunAMAuthHOTPPasswordValidityDuration - One-Time Password Length
-
Sets the length of one-time passwords.
amsterattribute:otpLengthssoadmattribute:sunAMAuthHOTPPasswordLengthValid values:
6and8. - One Time Password Max Retry
-
The number of times entry of the OTP may be attempted. Minimum is 1, maximum is 10.
Default: 3
amsterattribute:oathOtpMaxRetryssoadmattribute:forgerock-oath-max-retry - One-Time Password Delivery
-
Specifies whether to send the one-time password by SMS, by mail, or both.
amsterattribute:otpDeliveryMethodssoadmattribute:sunAMAuthHOTPasswordDeliveryValid values:
SMS,E-mail, andSMS and E-mail. - Mobile Phone Number Attribute Name
-
Provides the attribute name used for the text message. The default value is
telephoneNumber.amsterattribute:userProfileTelephoneAttributessoadmattribute:openamTelephoneAttribute - Mobile Carrier Attribute Name
-
Specifies a user profile attribute that contains a mobile carrier domain for sending SMS messages.
The uncustomized AM user profile does not have an attribute for the mobile carrier domain. You can:
-
Customize the AM user profile by adding a new attribute to it. Then you can populate the new attribute with users' SMS messaging domains.
All mobile carriers and bulk SMS messaging services have associated SMS messaging domains. For example, Verizon uses
vtext.com, T-Mobile usestmomail.net, and the TextMagic service usestextmagic.com. If you plan to send text messages internationally, determine whether the messaging service requires a country code. -
Leave the value for Mobile Carrier Attribute Name blank, and let AM default to sending SMS messages using
txt.att.netfor all users.
amsterattribute:mobileCarrierAttributessoadmattribute:openamSMSCarrierAttribute -
- Email Attribute Name
-
Provides the attribute name used to email the OTP. The default value is
mail(email).amsterattribute:userProfileEmailAttributessoadmattribute:openamEmailAttribute - Auto Send OTP Code
-
When enabled, configures the HOTP module to automatically generate an email or text message when users begin the login process.
ssoadmattribute:sunAMAuthHOTPAutoClicking
HTTP Basic authentication module properties
amster service name: HttpBasicModule
ssoadm service name: iPlanetAMAuthHTTPBasicService
- Backend Module Name
-
Specifies the module that checks the user credentials. The credentials are then supplied to either a data store or other identity repository module for authentication.
amsterattribute:backendModuleNamessoadmattribute:iplanet-am-auth-http-basic-module-configuredValid values:
LDAPandDataStore. - Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:iplanet-am-auth-httpbasic-auth-level
JDBC authentication module properties
amster service name: JdbcModule
ssoadm service name: sunAMAuthJDBCService
- Connection Type
-
Determines how the module obtains the connection to the database.
amsterattribute:connectionTypessoadmattribute:sunAMAuthJDBCConnectionTypeValid values:
JNDIandJDBC. - Connection Pool JNDI Name
-
Specifies the URL of the connection pool for JNDI connections. Refer to your web container’s documentation for instructions on setting up the connection pool.
amsterattribute:connectionPoolJndiNamessoadmattribute:sunAMAuthJDBCJndiName - JDBC Driver
-
Specifies the JDBC driver to use for JDBC connections.
Install a suitable Oracle or MySQL driver in the container where AM is installed, for example in the
/path/to/tomcat/webapps/openam/WEB-INF/libpath. You can add it to the AM.warfile when you deploy AM.amsterattribute:jdbcDriverssoadmattribute:sunAMAuthJDBCDriver - JDBC URL
-
Specifies the URL to connect to the database when using a JDBC connection.
amsterattribute:jdbcUrlssoadmattribute:sunAMAuthJDBCUrl - Database Username, Database Password
-
Specifies the user name and password used to authenticate to the database when using a JDBC connection.
ssoadmattribute:sunAMAuthJDBCDbuserandsunAMAuthJDBCDbpassword - Password Column Name
-
Specifies the database column name where passwords are stored.
amsterattribute:passwordColumnssoadmattribute:sunAMAuthJDBCPasswordColumn - Prepared Statement
-
Specifies the SQL query to return the password corresponding to the user to authenticate.
amsterattribute:passwordStatementssoadmattribute:sunAMAuthJDBCStatement - Class to Transform Password Syntax
-
Specifies the class that transforms the password retrieved to the same format as provided by the user.
The default class expects the password in cleartext. Custom classes must implement the
JDBCPasswordSyntaxTransforminterface.amsterattribute:passwordTransformClassssoadmattribute:sunAMAuthJDBCPasswordSyntaxTransformPlugin - Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:sunAMAuthJDBCAuthLevel
|
AM provides two properties, When using JDBC databases, consider adding the |
LDAP authentication module properties
amster service name: LdapModule
ssoadm service name: iPlanetAMAuthLDAPService
- Primary LDAP Server, Secondary LDAP Server
-
Specify the primary and secondary directory server(s).
Both properties take more than one value, allowing more than one primary or secondary remote server, respectively.
Directory servers generally use built-in data replication for high availability. Thus, a directory service typically consists of a pool of replicas to which AM can connect to retrieve and update directory data. AM attempts to contact the primary server(s) first, but if unavailable, AM attempts to contact the secondary servers.
For the current AM server, specify each directory server in the format
server:port. For other AM servers in the deployment, define each server aslocal_server_name | server:port. For example, if theserverishttps://openam.example.com:8443/openam, and the directory server is accessible atopendj.example.com:1636, enter the value asopenam.example.com|opendj.example.com:1636.Assuming a multi-data center environment, AM determines priority within the primary and secondary remote servers as follows:
-
LDAP servers that are mapped to the current AM instance have the highest priority.
For example, if you are connected to
openam1.example.comandldap1.example.comis mapped to that AM instance, then AM usesldap1.example.com. -
LDAP servers that are not specifically mapped to a given AM instance have the next highest priority.
For example, if you have another LDAP server,
ldap2.example.com, that is not connected to a specific AM server and ifldap1.example.comis unavailable, AM connects to the next highest priority LDAP server,ldap2.example.com. -
LDAP servers that are mapped to different AM instances have the lowest priority.
For example, if
ldap3.example.comis connected toopenam3.example.comandldap1.example.comandldap2.example.comare unavailable, thenopenam1.example.comconnects toldap3.example.com.ssoadmattributes are: primary isiplanet-am-auth-ldap-server; secondary isiplanet-am-auth-ldap-server2.
-
- DN to Start User Search
-
Specifies the base DN from which AM searches for users to authenticate.
LDAP data is organized hierarchically, similar to a file system on Windows or UNIX. More specific DNs likely result in better performance. When configuring the module for a particular part of the organization, you can start searches from a specific organizational unit, such as
OU=sales,DC=example,DC=com.If multiple entries exist with identical search attribute values, ensure this value is specific enough to return a single entry.
amsterattribute:userSearchStartDNssoadmattribute:iplanet-am-auth-ldap-base-dn - Bind User DN, Bind User Password
-
Specify the user and password of the administration account used for authentication to the directory server.
If AM stores attributes in the directory, for example, to manage account lockout, or if the directory requires that AM authenticate in order to read users' attributes, then AM needs the DN and password to authenticate to the directory.
Make sure that the password is correct before you logout. If it is incorrect, you will be locked out and you will need to log in with the superuser DN. By default, this is
uid=amAdmin,ou=People,AM-deploy-base, whereAM-deploy-basewas set during AM configuration.amsterattributes:userBindDNanduserBindPasswordssoadmattributes:iplanet-am-auth-ldap-bind-dnandiplanet-am-auth-ldap-bind-passwd - Attribute Used to Retrieve User Profile
-
LDAP uses this attribute to search for the profile of an authenticated user. Usually, this is the same attribute used to find the user account, such as the value set as the
uidin AM. For example, where the attribute is set tomail, the LDAP module searchesCN=Users,DC=example,DC=comwith a filter"(MAIL=bjensen@example.com)", and the directory returns the user profile that matchesMAIL=bjensen@example.com.The attribute is only used if User Profile is set to
RequiredandReturn User DN to DataStoreis not enabled.amsterattribute:userProfileRetrievalAttributessoadmattribute:iplanet-am-auth-ldap-user-naming-attribute - Attributes Used to Search for a User to be Authenticated
-
The attributes specified in this list define the LDAP search filter. Multiple attribute values mean the user can authenticate with any one of the values. For example, if you have both
uidandmail, then Barbara Jensen can authenticate with eitherbjensenorbjensen@example.com.amsterattribute:userSearchAttributesssoadmattribute:iplanet-am-auth-ldap-user-search-attributes - User Search Filter
-
The User Search Filter text box provides a more complex filter. For example, if you search using
mailand add the User Search Filter(objectClass=inetOrgPerson), then AM uses the resulting search filter(&(mail=address)(objectClass=inetOrgPerson)), where address is the mail address provided by the user.amsterattribute:userSearchAttributesssoadmattribute:iplanet-am-auth-ldap-search-filter - Search Scope
-
This attribute defines the level of directory that will be searched for a matching profile. You can set the search to run at a high level or against a specific area:
-
OBJECT searches only for the entry specified as the 'DN to Start User Search'.
-
ONELEVEL searches only the entries that are direct children of that object.
-
SUBTREE searches the entry specified and all entries at levels below.
ssoadmattribute:iplanet-am-auth-ldap-search-scope -
- LDAP Connection Mode
-
If you want to initiate secure communications to data stores using SSL or StartTLS, AM must be able to trust the server’s certificates, either because the certificates were signed by a CA whose certificate is already included in the trust store used by the container where AM runs, or because you imported the certificates into the trust store.
ssoadmattribute:openam-auth-ldap-connection-modePossible values:
LDAP,LDAPS, andStartTLS - Return User DN to DataStore
-
If User Profile is set to
Required, this attribute determines whether the DN or the username is returned as the authentication principal.When enabled, the module returns the DN rather than the User ID or the value set in
Attribute Used to Retrieve User Profile. The returned value is then used to make the request to retrieve the profile attributes from the user store.amsterattribute:returnUserDNssoadmattribute:iplanet-am-auth-ldap-return-user-dn - User Creation Attributes
-
This list of attributes defines the mapping of internal attribute names to external attribute names for dynamic profile creation. The attributes retrieved from the user’s authenticated profile are mapped against the values that will be provisioned into their matching account in the data store. This list does not include
uidmappings.The format of the list is
internal_attr1|external_attr1.amsterattribute:profileAttributeMappingsssoadmattribute:iplanet-am-ldap-user-creation-attr-list - Minimum Password Length
-
Set the minimum length required for a valid password when a user needs to reset their password during authentication.
This value is distinct from password requirements set by the underlying directory server. To avoid confusion, set the value to 0 if an external LDAP server is enforcing password policy.
amsterattribute:minimumPasswordLengthssoadmattribute:iplanet-am-auth-ldap-min-password-length - LDAP Behera Password Policy Support
-
Determines whether LDAP Behera password policies are supported by a directory server such as PingDS. If the property is set to false, then only the older Netscape VCHU password policy standard will be enforced.
amsterattribute:beheraPasswordPolicySupportEnabledssoadmattribute:iplanet-am-auth-ldap-behera-password-policy-enabled - Trust All Server Certificates
-
When enabled, the module trusts all server certificates, including self-signed certificates.
amsterattribute:trustAllServerCertificatesssoadmattribute:iplanet-am-auth-ldap-ssl-trust-all - LDAP Connection Heartbeat Interval
-
Specifies how often AM should send a heartbeat request to the directory server to ensure that the connection does not remain idle. Some network administrators configure firewalls and load balancers to drop connections that are idle for too long. You can turn this off by setting the value to 0. To set the units for the interval, use LDAP Connection Heartbeat Time Unit.
Default: 1
amsterattribute:connectionHeartbeatIntervalssoadmattribute:openam-auth-ldap-heartbeat-interval - LDAP Connection Heartbeat Time Unit
-
Specifies the time unit corresponding to LDAP Connection Heartbeat Interval. Possible values are
SECONDS,MINUTES, andHOURS.amsterattribute:connectionHeartbeatTimeUnitssoadmattribute:openam-auth-ldap-heartbeat-timeunit - LDAP operations timeout
-
Defines the timeout, in seconds, that AM should wait for a response from the directory server.
Default: 0 (means no timeout)
amsterattribute:operationTimeoutssoadmattribute:openam-auth-ldap-operation-timeout - Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:iplanet-am-auth-ldap-auth-level - Stop LDAP Binds after in-memory lockout
-
If enabled, prevent AM from sending further bind requests to the LDAP Server when the user is locked out through a duration lockout.
amsterattribute:stopLdapbindAfterInmemoryLockedEnabledssoadmattribute:openam-auth-stop-ldap-bind-after-inmemory-locked-enabled
Legacy OAuth 2.0/OpenID Connect authentication module properties
|
This authentication module is labelled as legacy. Equivalent functionality is provided by the following authentication modules: The Legacy OAuth 2.0/OpenID Connect Authentication Module will only be available in AM when upgrading from a previous version that was making use of the module in a chain. It is not available in new, clean installations since AM 5.5. |
The default settings are for Facebook.
amster service name: OAuth2Module
ssoadm service name: sunAMAuthOAuthService
- Client id
-
Specifies the OAuth 2.0
client_idparameter as described in section 2.2 of RFC 6749.amsterattribute:clientIdssoadmattribute:iplanet-am-auth-oauth-client-id - Client Secret
-
Specifies the OAuth 2.0
client_secretparameter as described in section 2.3 of RFC 6749.amsterattribute:clientSecretssoadmattribute:iplanet-am-auth-oauth-client-secret - Authentication Endpoint URL
-
Specifies the URL to the endpoint handling OAuth 2.0 authentication as described in section 3.1 of RFC 6749.
amsterattribute:authenticationEndpointUrlssoadmattribute:iplanet-am-auth-oauth-auth-service - Access Token Endpoint URL
-
Specifies the URL to the endpoint handling access tokens as described in section 3.2 of RFC 6749.
amsterattribute:accessTokenEndpointUrlssoadmattribute:iplanet-am-auth-oauth-token-service - User Profile Service URL
-
Specifies the user profile URL that returns profile information in JSON format.
Default:
https://graph.facebook.com/me.amsterattribute:userProfileServiceUrlssoadmattribute:iplanet-am-auth-oauth-user-profile-service - Scope
-
Specifies a space-delimited list of user profile attributes that the client application requires, according to The OAuth 2.0 Authorization Framework. The list depends on the permissions that the resource owner, such as the end user, grants to the client application.
Some authorization servers use non-standard separators for scopes. Facebook, for example, takes a comma-separated list.
Default:
email,read_stream(Facebook example)amsterattribute:scopessoadmattribute:iplanet-am-auth-oauth-scope - OAuth2 Access Token Profile Service Parameter name
-
Specifies the name of the parameter that contains the access token value when accessing the profile service.
Default:
access_token.amsterattribute:accessTokenParameterNamessoadmattribute:iplanet-am-auth-oauth-user-profile-param - Proxy URL
-
Sets the URL to the
/oauth2c/OAuthProxy.jspfile, which provides AM with GET to POST proxying capabilities. Change this URL only if an external server performs the GET to POST proxying.Default:
@SERVER_PROTO@://@SERVER_HOST@:@SERVER_PORT@/@SERVER_URI@/oauth2c/OAuthProxy.jsp.amsterattribute:ssoProxyUrlssoadmattribute:iplanet-am-auth-oauth-sso-proxy-url - Account Provider
-
Specifies the name of the class that implements the account provider.
Default:
org.forgerock.openam.authentication.modules.common.mapping.DefaultAccountProvideramsterattribute:accountProviderClassssoadmattribute:org-forgerock-auth-oauth-account-provider - Account Mapper
-
Specifies the name of the class that implements the attribute mapping for the account search.
For Google implementations, use
_org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapper|*|Google-+.For Facebook implementations, use
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper|*|facebook-.Default:
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapperamsterattribute:accountMapperClassssoadmattribute:org-forgerock-auth-oauth-account-mapper - Account Mapper Configuration
-
Specifies the attribute configuration used to map the account of the user authenticated in the OAuth 2.0 provider to the local data store in AM. Valid values are in the form
provider-attr=local-attr.When using the
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapperclass, you can parse JSON objects in mappings, by using dot notation.For example, given a JSON payload of:
{ "sub" : "12345", "name" : { "first_name" : "Demo", "last_name" : "User" } }jsonYou can create a mapper, such as
name.first_name=cn.Default:
email=mailandid=facebook-id.amsterattribute:accountMapperConfigurationssoadmattribute:org-forgerock-auth-oauth-account-mapper-configuration - Attribute Mapper
-
Specifies the list of fully qualified class names for implementations that map attributes from the OAuth 2.0 authorization server or OpenID Connect provider to AM profile attributes.
Default:
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapperProvided implementations are:
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper,org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapper(can only be used when using theopenidscope)You can provide string constructor parameters by appending pipe (
|) separated values.For example, the
org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapperclass can take two constructor parameters: a comma-separated list of attributes and a prefix to apply to their values. Specify these as follows:org.forgerock.openam.authentication.modules.oidc.JsonAttributeMapper
amsterattribute:attributeMappingClassesssoadmattribute:org-forgerock-auth-oauth-attribute-mapper - Attribute Mapper Configuration
-
Map of OAuth 2.0 provider user account attributes to local user profile attributes, with values in the form
provider-attr=local-attr.When using the
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapperclass, you can parse JSON objects in mappings, by using dot notation.For example, given a JSON payload of:
{ "sub" : "12345", "name" : { "first_name" : "Demo", "last_name" : "User" } }jsonYou can create a mapper, such as
name.first_name=cn.Default:
first_name=givenname,last_name=sn,name=cn,email=mail,id=facebook-id,first_name=facebook-fname,last_name=facebook-lname,email=facebook-email.amsterattribute:attributeMapperConfigurationssoadmattribute:org-forgerock-auth-oauth-attribute-mapper-configuration - Save attributes in the session
-
When enabled, saves the attributes in the Attribute Mapper Configuration field to the AM session.
amsterattribute:saveAttributesInSessionssoadmattribute:org-forgerock-auth-oauth-save-attributes-to-session-flag - Email attribute in OAuth2 Response
-
Specifies the attribute identifying the authenticated user’s email address in the response from the profile service in the OAuth 2.0 provider. This setting is used to send an email message with an activation code for accounts created dynamically.
amsterattribute:oauth2EmailAttributessoadmattribute:org-forgerock-auth-oauth-mail-attribute - Create account if it does not exist
-
When enabled, AM creates an account for the user if the user profile does not exist. If the Prompt for password setting and activation code attribute is enabled, AM prompts the user for a password and activation code before creating the account.
When the OAuth 2.0/OpenID Connect client is configured to create new accounts, the SMTP settings must also be valid. As part of account creation, the OAuth 2.0/OpenID Connect client authentication module sends the resource owner an email with an account activation code. To send the mail, AM uses the SMTP settings you provide here in the OAuth 2.0/OpenID Connect client configuration.
When disabled, a user without a profile may still log into AM if the Ignore Profile attribute is set in the authentication service of the realm, or if the account is mapped to an anonymous account.
amsterattribute:createAccountssoadmattribute:org-forgerock-auth-oauth-createaccount-flag - Prompt for password setting and activation code
-
When enabled, the user must set a password before AM creates an account dynamically. An activation code is also sent to the user’s email address. Both the password and the code are required before the account is created.
amsterattribute:promptForPasswordssoadmattribute:org-forgerock-auth-oauth-prompt-password-flag - Map to anonymous user
-
When enabled, maps the OAuth 2.0 authenticated user to the specified anonymous user. If the Create account if it does not exist property is enabled, AM creates an account for the authenticated user instead of mapping the account to the anonymous user.
amsterattribute:mapToAnonymousUserssoadmattribute:org-forgerock-auth-oauth-map-to-anonymous-flag - Anonymous User
-
Specifies an anonymous user that exists in the current realm. The user status of this anonymous user must be
Active. TheMap to anonymous userproperty maps authorized users without a profile to this anonyomus user, if enabled.Default:
anonymous.amsterattribute:anonymousUserNamessoadmattribute:org-forgerock-auth-oauth-anonymous-user - OAuth 2.0 Provider logout service
-
Specifies the optional URL of the OAuth 2.0 provider’s logout service, if required.
amsterattribute:oauth2LogoutServiceUrlssoadmattribute:org-forgerock-auth-oauth-logout-service-url - Logout options
-
Specifies whether not to log the user out without prompting from the OAuth 2.0 provider on logout, to log the user out without prompting, or to prompt the user regarding whether to log out from the OAuth 2.0 provider.
Valid values are:
-
prompt, to ask the user whether or not to log out from the OAuth 2.0 provider. -
logout, to log the user out of the OAuth 2.0 provider without prompting. -
donotlogout, to keep the user logged in to the OAuth 2.0 provider. There is no prompt to the user.
Default:
prompt.amsterattribute:logoutBehaviourssoadmattribute:org-forgerock-auth-oauth-logout-behaviour -
- Mail Server Gateway implementation class
-
Specifies the class used by the module to send email. A custom subclass of
org.forgerock.openam.authentication.modules.oauth2.EmailGatewayclass can be provided.Default:
org.forgerock.openam.authentication.modules.oauth2.DefaultEmailGatewayImplamsterattribute:mailGatewayClassssoadmattribute:org-forgerock-auth-oauth-email-gwy-impl - SMTP host
-
Specifies the host name of the mail server.
Default:
localhost.amsterattribute:smtpHostNamessoadmattribute:org-forgerock-auth-oauth-smtp-hostname - SMTP port
-
Specifies the SMTP port number for the mail server.
Default:
25.amsterattribute:smtpHostPortssoadmattribute:org-forgerock-auth-oauth-smtp-port - SMTP User Name, SMTP User Password
-
Specifies the username and password AM uses to authenticate to the mail server.
ssoadmattribute:org-forgerock-auth-oauth-smtp-usernameandorg-forgerock-auth-oauth-smtp-password. - SMTP SSL Enabled
-
When enabled, connects to the mail server over SSL. AM must be able to trust the SMTP server certificate.
amsterattribute:smtpSslEnabledssoadmattribute:org-forgerock-auth-oauth-smtp-ssl_enabled - SMTP From address
-
Specifies the address of the email sender, such as
no-reply@example.com.Default:
info@forgerock.com.amsterattribute:smtpFromAddressssoadmattribute:org-forgerock-auth-oauth-smtp-email-from - Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
Default: 0.
amsterattribute:authenticationLevelssoadmattribute:iplanet-am-auth-oauth-auth-level - OpenID Connect validation configuration type
-
Validates the ID token from the OpenID Connect provider. The module needs either a URL to get the public keys for the provider or the symmetric key for an ID token signed with a HMAC-based algorithm.
By default, the configuration type is
.well-known/openid-configuration_url. This means the module should retrieve the keys based on information in the OpenID Connect provider configuration document.You can instead configure the authentication module to validate the ID token signature with the client secret key you provide, or to validate the ID token with the keys retrieved from the URL to the OpenID Connect provider’s JSON web key set.
/oauth2/realms/root/.well-known/openid-configuration_url(Default)-
Retrieve the provider keys based on the information provided in the OpenID Connect Provider Configuration Document.
Specify the URL to the document as the discovery URL.
client_secret-
Use the client secret that you specify as the key to validate the ID token signature according to the HMAC by using the client secret to the decrypt the hash, and then checking that the hash matches the hash of the ID token JWT.
jwk_url-
Retrieve the provider’s JSON web key set as the URL that you specify.
amsterattribute:cryptoContextTypessoadmattribute:openam-auth-openidconnect-crypto-context-type - OpenID Connect validation configuration value
-
Edit this field depending on the Configuration type you specified in the OpenId Connect validation configuration type field.
amsterattribute:cryptoContextValuessoadmattribute:openam-auth-openidconnect-crypto-context-value - Token Issuer
-
Required when the
openidscope is included. Value must match theissfield in the issued ID token. For example,accounts.google.com.The issuer value MUST be provided when OAuth 2.0 Mix-Up Mitigation is enabled. For more information, see OAuth 2.0 Mix-Up Mitigation.
amsterattribute:idTokenIssuerssoadmattribute:openam-auth-openidconnect-issuer-name
|
Old uses of |
The following table shows endpoint URLs for AM when configured as an OAuth 2.0 provider. For details, see OAuth 2.0. The default endpoints are for Facebook as the OAuth 2.0 provider.
In addition to the endpoint URLs you can set other fields, like scope and attribute mapping, depending on the provider you use:
| AM Field | Details |
|---|---|
Authorization Endpoint URL |
This AM endpoint can take additional parameters. In particular, you must specify the realm if the AM OAuth 2.0 provider is configured for a subrealm rather than the Top Level Realm. When making a REST API call, specify the realm in the path component of the endpoint.
You must specify the entire hierarchy of the realm, starting at the Top Level Realm.
Prefix each realm in the hierarchy with the For example, if the OAuth 2.0 provider is configured for the subrealm The Example: |
Access Token Endpoint URL |
This AM endpoint can take additional parameters. In particular, you must specify the realm if the AM OAuth 2.0 provider is configured for a subrealm rather than the Top Level Realm. When making a REST API call, specify the realm in the path component of the endpoint.
You must specify the entire hierarchy of the realm, starting at the Top Level Realm.
Prefix each realm in the hierarchy with the For example, if the OAuth 2.0 provider is configured for the subrealm The Example: |
User Profile Service URL |
Example: |
OAuth 2.0 Mix-Up Mitigation
AM has added a new property to the OAuth 2.0 authentication module,
openam-auth-oauth-mix-up-mitigation-enabled.
This OAuth 2.0 Mix-Up Mitigation property controls
whether the OAuth 2.0 authentication module carries out additional verification steps
when it receives the authorization code from the authorization server.
This setting should be only enabled when the authorization server also supports OAuth 2.0 Mix-Up Mitigation.
- OAuth 2.0 Mix-Up Mitigation Enabled
-
Specifies that the client must compare the issuer identifier of the authorization server upon registration with the issuer value returned in the
issresponse parameter. If they do not match, the client must abort the authorization process. The client must also confirm that the authorization server’s response is intended for the client by comparing the client’s client identifier to the value of theclient_idresponse parameter.For more information, see section 4 of OAuth 2.0 Mix-Up Mitigation Draft.
At the time of this release, Facebook, Google, and Microsoft identity providers do not support this draft. amsterattribute:mixUpMitigationssoadmattribute:openam-auth-oauth-mix-up-mitigation-enabledIn the AM admin UI, the field Token Issuer must be provided when the OAuth 2.0 Mix-Up Mitigation feature is enabled. The authorization code response will contain an issuer value (
iss) that will be validated by the client. When the module is an OAuth2-only module (that is, OIDC is not used), the issuer value needs to be explicitly set in the Token Issuer field, so that the validation can succeed.Consult with the authorization server’s documentation on what value it uses for the issuer field.
MSISDN authentication module properties
amster service name: MsisdnModule
ssoadm service name: sunAMAuthMSISDNService
- Trusted Gateway IP Address
-
Specifies a list of IP addresses of trusted clients that can access MSISDN modules. Either restrict the clients allowed to access the MSISDN module by adding each IPv4 or IPv6 address here, or leave the list empty to allow all clients to access the module. If you specify the value
none, no clients are allowed access.amsterattribute:trustedGatewayIPAddressesssoadmattribute:sunAMAuthMSISDNTrustedGatewayList - MSISDN Number Search Parameter Name
-
Specifies a list of parameter names that identify which parameters to search in the request header or cookie header for the MSISDN number. For example, if you define x-Cookie-Param, AM_NUMBER, and COOKIE-ID, the MSISDN authentication service checks those parameters for the MSISDN number.
amsterattribute:msisdnParameterNamesssoadmattribute:sunAMAuthMSISDNParameterNameList - LDAP Server and Port
-
Specifies the LDAP server FQDN and its port in the format
ldap-server:port. AM servers can be paired with LDAP servers and ports by adding entries of the formAM-server|ldap_server:port, for example,openam.example.com|ldap1.example.com:649.To use SSL or TLS for security, enable the SSL/TLS Access to LDAP property. Make sure that AM can trust the servers' certificates when using this option.
amsterattribute:ldapProviderUrlssoadmattribute:sunAMAuthMSISDNLdapProviderUrl - LDAP Start Search DN
-
Specifies the DN of the entry where the search for the user’s MSISDN number should start. AM servers can be paired with search base DNs by adding entries with the format
AM-server|base-dn. For example,openam.example.com|dc=openam,dc=forgerock,dc=com.amsterattribute:baseSearchDNssoadmattribute:sunAMAuthMSISDNBaseDn - Attribute To Use To Search LDAP
-
Specifies the name of the attribute in the user’s profile that contains the MSISDN number to search for the user. The default is
sunIdentityMSISDNNumber.amsterattribute:userProfileMsisdnAttributessoadmattribute:sunAMAuthMSISDNUserSearchAttribute - LDAP Server Authentication User, LDAP Server Authentication Password
-
Specifies the bind DN and password of the service account AM uses to authenticate to the directory server. The default is
uid=admin.ssoadmattribute:sunAMAuthMSISDNPrincipalUserandsunAMAuthMSISDNPrincipalPasswd. - SSL/TLS for LDAP Access
-
When enabled, AM uses LDAPS or StartTLS to connect to the directory server. If you choose to enable SSL or TLS, then make sure that AM can trust the servers' certificates.
amsterattribute:ldapSslEnabledssoadmattribute:sunAMAuthMSISDNUseSsl - MSISDN Header Search Attribute
-
Specifies which elements are searched for the MSISDN number. The possible values are:
searchCookie-
To search the cookie.
searchRequest-
To search the request header.
searchParam-
To search the request parameters.
amsterattribute:msisdnRequestSearchLocationsssoadmattribute:sunAMAuthMSISDNHeaderSearch - LDAP Attribute Used to Retrieve User Profile
-
Specify the LDAP attribute that is used during a search to return the user profile for MSISDN authentication service. The default is
uid.amsterattribute:msisdnUserNamingAttributessoadmattribute:sunAMAuthMSISDNUserNamingAttribute - Return User DN to DataStore
-
When enabled, this option allows the authentication module to return the DN instead of the User ID. AM thus does not need to perform an additional search with the user ID to find the user’s entry.
Enable this option only when the AM directory is the same as the directory configured for MSISDN searches.
amsterattribute:returnUserDNssoadmattribute:sunAMAuthMSISDNReturnUserDN - Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:sunAMAuthMSISDNAuthLevel
OATH authentication module properties
amster service name: OathModule
ssoadm service name: iPlanetAMAuthOATHService
Also refer to Differences between authentication modules that support HOTP.
- Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:iplanet-am-auth-oath-auth-level - One Time Password Length
-
Sets the length of the OTP to six digits or longer. The default value is six.
amsterattribute:passwordLengthssoadmattribute:iplanet-am-auth-oath-password-length - Minimum Secret Key Length
-
The minimum number of hexadecimal characters allowed for the secret key.
amsterattribute:minimumSecretKeyLengthssoadmattribute:iplanet-am-auth-oath-min-secret-key-length - Secret Key Attribute Name
-
The name of the attribute where the key will be stored in the user profile.
amsterattribute:secretKeyAttributessoadmattribute:iplanet-am-auth-oath-secret-key-attribute - OATH Algorithm to Use
-
Select whether to use HOTP or TOTP. You can create an authentication chain to allow for a greater variety of devices. The default value is HOTP.
amsterattribute:oathAlgorithmssoadmattribute:iplanet-am-auth-oath-algorithm - HOTP Window Size
-
The window that the OTP device and the server counter can be out of sync. For example, if the window size is 100 and the server’s last successful login was at counter value 2, then the server will accept an OTP from device counter 3 to 102. The default value is 100.
amsterattribute:hotpWindowSizessoadmattribute:iplanet-am-auth-oath-hotp-window-sizeFor information on resetting the HOTP counter, see Reset registered devices over REST. - Counter Attribute Name
-
The name of the HOTP attribute where the counter will be stored in the user profile.
amsterattribute:hotpCounterAttributessoadmattribute:iplanet-am-auth-oath-hotp-counter-attribute - Add Checksum Digit
-
Adds a checksum digit at the end of the HOTP password to verify the OTP was generated correctly. This is in addition to the actual password length. Set this only if your device supports it. The default value is No.
amsterattribute:addChecksumssoadmattribute:iplanet-am-auth-oath-add-checksum - Truncation Offset
-
Advanced feature that is device-specific. Let this value default unless you know your device uses a truncation offset. The default value is -1.
amsterattribute:truncationOffsetssoadmattribute:iplanet-am-auth-oath-truncation-offset - TOTP Time Step Interval
-
The time interval for which an OTP is valid. For example, if the time step interval is 30 seconds, a new OTP will be generated every 30 seconds, and an OTP will be valid for 30 seconds. The default value is 30 seconds.
amsterattribute:timeStepSizessoadmattribute:iplanet-am-auth-oath-size-of-time-step - One Time Password Max Retry
-
The number of times entry of the OTP may be attempted. Minimum is 1, maximum is 10.
Default: 3
amsterattribute:oathOtpMaxRetryssoadmattribute:forgerock-oath-max-retry - TOTP Time Steps
-
The number of time step intervals that the system and the device can be off before password resynchronization is required. For example, if the number of TOTP time steps is 2 and the TOTP time step interval is 30 seconds, the server will allow an 89 second clock skew between the client and the server—two 30 second steps plus 29 seconds for the interval in which the OTP arrived. The default value is 2.
amsterattribute:stepsInWindowssoadmattribute:iplanet-am-auth-oath-steps-in-window - Last Login Time Attribute
-
The name of the attribute where both HOTP and TOTP authentication will store information on when a person last logged in.
amsterattribute:lastLoginTimeAttributessoadmattribute:iplanet-am-auth-oath-last-login-time-attribute-name - The Shared Secret Provider Class
-
The class that processes the user profile attribute where the user’s secret key is stored. The name of this attribute is specified in the Secret Key Attribute Name property.
Default:
org.forgerock.openam.authentication.modules.oath.plugins.DefaultSharedSecretProviderssoadmattribute:forgerock-oath-sharedsecret-implementation-class - Clock Drift Attribute Name
-
The user profile attribute where the clock drift is stored. If this field is not specified, then AM does not check for clock drift.
ssoadmattribute:forgerock-oath-observed-clock-drift-attribute-name - Maximum Allowed Clock Drift
-
The maximum acceptable clock drift before authentication fails. If this value is exceeded, the user must register their device again.
The Maximum Allowed Clock Drift value should be greater than the TOTP Time Steps value.
ssoadmattribute:forgerock-oath-maximum-clock-drift
OpenID Connect id_token bearer authentication module properties
The default settings are for Google’s provider.
amster service name: SocialAuthOpenIDModule
ssoadm service name: amAuthOpenIdConnect
- Account provider class
-
The account provider provides the means to search for and create OpenID Connect users given a set of attributes.
Default:
org.forgerock.openam.authentication.modules.common.mapping.DefaultAccountProvideramsterattribute:accountProviderClassssoadmattribute:openam-auth-openidconnect-account-provider-class - OpenID Connect validation configuration type
-
In order to validate the ID token from the OpenID Connect provider, the module needs either a URL to get the public keys for the provider, or the symmetric key for an ID token signed with a HMAC-based algorithm; AM ignores keys specified in JWT headers, such as `jku` and `jwe`.
By default, the configuration type is
.well-known/openid-configuration_url. This means the module should retrieve the keys based on information in the OpenID Connect Provider Configuration Document.You can instead configure the authentication module to validate the ID token signature with the client secret key you provide, or to validate the ID token with the keys retrieved from the URL to the OpenID Connect provider’s JSON web key set.
.well-known/openid-configuration_url(Default)-
Retrieve the provider keys based on the information provided in the OpenID Connect Provider Configuration Document.
Specify the URL to the document as the discovery URL.
client_secret-
Use the client secret that you specify as the key to validate the ID token signature according to the HMAC, using the client secret to the decrypt the hash and checking that the hash matches the hash of the ID token JWT.
jwk_url-
Retrieve the provider’s JSON web key set at the URL that you specify.
amsterattribute:cryptoContextTypessoadmattribute:openam-auth-openidconnect-crypto-context-type - OpenID Connect validation configuration value
-
Specifies the discovery URL, JWK or the client secret corresponding to the configuration type selected in the OpenID Connect validation configuration type property.
amsterattribute:cryptoContextValuessoadmattribute:openam-auth-openidconnect-crypto-context-value - Name of header referencing the ID Token
-
Specifies the name of the HTTP request header to search for the ID token.
Default:
oidc_id_tokenamsterattribute:idTokenHeaderNamessoadmattribute:openam-auth-openidconnect-header-name - Name of OpenID Connect ID Token Issuer
-
Corresponds to the expected issue identifier value in the
issfield of the ID token.Default:
accounts.google.comamsterattribute:idTokenIssuerssoadmattribute:openam-auth-openidconnect-issuer-name - Mapping of jwt attributes to local LDAP attributes
-
Maps OpenID Connect ID token claims to local user profile attributes, allowing the module to retrieve the user profile based on the ID token.
In OpenID Connect, an ID token is represented as a JSON Web Token (JWT). The ID Token section of the OpenID Connect Core 1.0 specification defines a number of claims included in the ID token for all flows. Additional claims depend on the scopes requested of the OpenID Connect provider.
For each item in the map, the key is the ID token field name and the value is the local user profile attribute name.
Default:
mail=email,uid=subssoadmattribute:openam-auth-openidconnect-jwt-to-local-attribute-mappings - Audience name
-
Specifies a case-sensitive audience name for this OpenID Connect authentication module. Used to check that the ID token received is intended for this module as an audience.
Default:
exampleamsterattribute:audienceNamessoadmattribute:openam-auth-openidconnect-audience-name - List of accepted authorized parties
-
Specifies a list of case-sensitive strings and/or URIs from which this authentication module accepts ID tokens. This list is checked against the authorized party claim of the ID token.
Default:
AuthorizedPartyExample http://www.example.com/authorized/partyamsterattribute:acceptedAuthorizedPartiesssoadmattribute:openam-auth-openidconnect-accepted-authorized-parties - Principal Mapper class
-
Specifies the class that implements the mapping of the OpenID Connect end user to an AM account. The default principal mapper uses the mapping of local attributes to ID token attributes to find a user profile.
Default:
org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapperamsterattribute:principalMapperClassssoadmattribute:openam-auth-openidconnect-principal-mapper-class
Persistent Cookie authentication module properties
amster service name: PersistentCookieModule
ssoadm service name: iPlanetAMAuthPersistentCookieService
- Idle Timeout
-
Specifies the maximum idle time between requests in hours. If that time is exceeded, the cookie is no longer valid.
ssoadmattribute:openam-auth-persistent-cookie-idle-time - Max Life
-
Specifies the maximum life of the cookie in hours.
ssoadmattribute:openam-auth-persistent-cookie-max-life - Enforce Client IP
-
When enabled, enforces that the persistent cookie can only be used from the same client IP to which the cookie was issued.
ssoadmattribute:openam-auth-persistent-cookie-enforce-ip - Use secure cookie
-
When enabled, adds the "Secure" attribute to the persistent cookie.
ssoadmattribute:openam-auth-persistent-cookie-secure-cookie - Use HTTP only cookie
-
When enabled, adds the
HttpOnlyattribute to the persistent cookie.ssoadmattribute:openam-auth-persistent-cookie-http-only-cookie - Persistent Cookie Name
-
Set the name of the persistent cookie.
Default:
session-jwtssoadmattribute:openam-auth-persistent-cookie-name
RADIUS authentication module properties
amster service name: RadiusModule
ssoadm service name: iPlanetAMAuthRadiusService
- Primary Radius Servers, Secondary Radius Servers
-
Specify one or more primary and secondary RADIUS servers.
When configuring RADIUS servers, specify their IP address or FQDN. Configuring multiple servers allows you to map a RADIUS server to a specific AM instance of the form
AM-instance | RADIUS-server, where the AM instance is also specified by its IP address or FQDN.Ensure each RADIUS server listens to the port specified in the Port Number field. When authenticating users from a directory server that is remote to AM, set the primary values and, optionally, the secondary server values. Assuming a multi-data center environment, AM determines priority within the primary and secondary remote servers, respectively, as follows:
-
Every RADIUS server that is mapped to the current AM instance has highest priority.
-
Every RADIUS server that was not specifically mapped to a given AM instance has the next highest priority.
-
RADIUS servers that are mapped to different AM instances have the lowest priority.
AM does not use round-robin load balancing to set priority. AM uses an active-passive algorithm, determining the highest priority to the first available server within the primary server list. If no primary servers are available, AM uses the secondary remote server.
ssoadmattribute:primary is iplanet-am-auth-radius-server1; secondary isiplanet-am-auth-radius-server2 -
- Shared Secret
-
Specify the shared secret for RADIUS authentication. The shared secret should be as secure as a well-chosen password.
amsterattribute:sharedSecretssoadmattribute:iplanet-am-auth-radius-secret - Port Number
-
Specify the RADIUS server port.
Default is 1645.
amsterattribute:serverPortNumberssoadmattribute:iplanet-am-auth-radius-server-port - Timeout
-
Specify how many seconds to wait for the RADIUS server to respond. The default value is 3 seconds.
amsterattribute:serverTimeoutssoadmattribute:iplanet-am-auth-radius-timeout - Health Check Interval
-
Used for failover. Specify how often AM performs a health check on a previously unavailable RADIUS server by sending an invalid authentication request.
Default: 5 minutes
amsterattribute:healthCheckIntervalssoadmattribute:openam-auth-radius-healthcheck-interval - Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:iplanet-am-auth-radius-auth-level
SAE authentication module properties
amster service name: SaeModule
ssoadm service name: sunAMAuthSAEService
- Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
ssoadmservice name:sunAMAuthSAEAuthLevel
SAML2 authentication module properties
amster service name: Saml2Module
ssoadm service name: iPlanetAMAuthSAML2Service
- Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
ssoadmattribute:iplanet-am-auth-saml2-auth-level - IDP Entity ID
-
Specifies the identity provider (IDP) for authentication requests to this module. Specify the name of a SAML v2.0 entity provider that is defined in the SAML2 authentication module’s realm.
You can find configured entity providers in the AM admin UI under Federation. The Realm column identifies the realm in which an entity provider has been configured.
amsterattribute:entityNamessoadmattribute:forgerock-am-auth-saml2-entity-name - SP MetaAlias
-
Specifies the local alias for the service provider (SP).
For service providers configured in the Top Level Realm, use the format
/SP Name.For service providers configured in subrealms, use the format
/Realm Name/SP Name.To find the local aliases for entity providers in the AM admin UI, go to Realms > Realm Name > Applications > Federation > Entity Providers > Entity Provider Name > Services.
amsterattribute:metaAliasssoadmattribute:forgerock-am-auth-saml2-meta-alias - Allow IDP to Create NameID
-
Specifies whether the IDP should create a new identifier for the authenticating user if none exists.
A value of
truepermits the IDP to create an identifier for the authenticating user if none exists. A value offalseindicates a request to constrain the IDP from creating an identifier.For detailed information, see the section on the
AllowCreateproperty in SAML Version 2.0 Errata 05.Default:
trueamsterattribute:allowCreatessoadmattribute:forgerock-am-auth-saml2-allow-create - Linking Authentication Chain
-
Specifies an authentication chain that is invoked when a user requires authentication to the SP.
Authentication to the SP is required when the authentication module running on the SP is unable to determine the user’s identity based on the assertion received from the IDP. In this case, the linking authentication chain is invoked to allow the end user to link their remote and local accounts.
amsterattribute:loginChainssoadmattribute:forgerock-am-auth-saml2-login-chain - Comparison Type
-
Specifies a comparison method to evaluate authentication context classes or statements. The value specified in this property overrides the value set in the SP configuration under Realms > Realm Name > Applications > Federation > Entity Providers > Service Provider Name > Assertion Content > Authentication Context > Comparison Type.
Valid comparison methods are
exact,minimum,maximum, orbetter.For more information about the comparison methods, see the section on the
<RequestedAuthnContext>element in Assertions and Protocols for the OASIS Security Assertion Markup Language (SAML) V2.0.Default:
exactamsterattribute:authComparisonssoadmattribute:forgerock-am-auth-saml2-auth-comparison - Authentication Context Class Reference
-
Specifies one or more URIs for authentication context classes to be included in the SAML request. Authentication context classes are unique identifiers for an authentication mechanism. The SAML v2.0 protocol supports a standard set of authentication context classes, defined in Authentication Context for the OASIS Security Assertion Markup Language (SAML) V2.0. In addition to the standard authentication context classes, you can specify customized authentication context classes.
Any authentication context class that you specify in this field must be supported for the service provider. To determine which authentication context classes are supported, locate the list of authentication context classes that are available to the SP under Realms > Realm Name > Applications > Federation > Entity Providers > Service Provider Name > Assertion Content > Authentication Context, and then review the values in the Supported column.
When specifying multiple authentication context classes, use the | character to separate the classes.
Example value:
urn:oasis:names:tc:SAML:2.0:ac:classes:Password|urn:oasis:names:tc:SAML:2.0:ac:classes:TimesyncTokenamsterattribute:authnContextClassRefssoadmattribute:forgerock-am-auth-saml2-authn-context-class-ref - Authentication Context Declaration Reference
-
Specifies one or more URIs that identify authentication context declarations.
This field is optional.
When specifying multiple URIs, use the | character to separate the URIs.
For more information, see the section on the
<RequestedAuthnContext>element in Assertions and Protocols for the OASIS Security Assertion Markup Language (SAML) V2.0.amsterattribute:authnContextDeclRefssoadmattribute:forgerock-am-auth-saml2-authn-context-decl-ref - Request Binding
-
Specifies the format used to send the authentication request from the SP to the IDP.
Valid values are
HTTP-RedirectandHTTP-POST.Default:
HTTP-Redirectssoadmattribute:forgerock-am-auth-saml2-req-binding.When using the
ssoadmcommand, set this attribute’s value tourn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirectorurn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST. - Response Binding
-
Specifies the format used to send the response from the IDP to the SP.
A value of
HTTP-POSTindicates that the HTTP POST binding with a self-submitting form should be used in assertion processing. A value ofHTTP-Artifactindicates that the HTTP Artifact binding should be used.Default:
HTTP-Artifactssoadmattribute:forgerock-am-auth-saml2-binding.When using the
ssoadmcommand, set this attribute’s value tourn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifactorurn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST. - Force IDP Authentication
-
Specifies whether the IDP should force authentication or can reuse existing security contexts.
A value of
trueindicates that the IDP should force authentication. A value offalseindicates that the IDP can reuse existing security contexts.amsterattribute:forceAuthnssoadmattribute:forgerock-am-auth-saml2-force-authn - Passive Authentication
-
Specifies whether the IDP should use passive authentication or not. Passive authentication requires the IDP to only use authentication methods that do not require user interaction. For example, authenticating using an X.509 certificate.
A value of
trueindicates that the IDP should authenticate passively. A value offalseindicates that the IDP should not authenticate passively.amsterattribute:isPassivessoadmattribute:forgerock-am-auth-saml2-is-passive - NameID Format
-
Specifies a SAML name ID format to be requested in the SAML authentication request.
Default:
urn:oasis:names:tc:SAML:2.0:nameid-format:persistentamsterattribute:nameIdFormatssoadmattribute:forgerock-am-auth-saml2-name-id-format - Single Logout Enabled
-
Specifies whether AM should attempt to log out of the user’s IDP session during session logout.
When enabling SAML v2.0 single logout, you must also configure the post-authentication processing class for the authentication chain containing the SAML2 authentication module to
org.forgerock.openam.authentication.modules.saml2.SAML2PostAuthenticationPlugin.For more information about configuring single logout when implementing SAML v2.0 federation using the SAML2 authentication module, see Configuring SLO in Integrated Mode (Chains).
Default:
falseamsterattribute:sloEnabledssoadmattribute:forgerock-am-auth-saml2-slo-enabled - Single Logout URL
-
Specifies the URL to which the user is forwarded after successful IDP logout. Configure this property only if you have enabled SAML v2.0 single logout by selecting the Single Logout Enabled check box.
amsterattribute:sloRelayssoadmattribute:forgerock-am-auth-saml2-slo-relay
Scripted authentication module properties
amster service name: scripted
ssoadm service name: iPlanetAMAuthScriptedService
Use the following settings at the realm level when configuring an individual scripted authentication module, in the AM admin UI under Realms > Realm Name > Authentication > Modules.
- Client-side Script Enabled
-
When enabled, the module includes the specified client-side script in the login page to be executed on the user-agent prior to the server-side script.
amsterattribute:clientScriptEnabledssoadmattribute:iplanet-am-auth-scripted-client-script-enabled - Client-side Script
-
Specifies the ID of the script to include in the login page. This script is run on the user-agent prior to the server-side script. This script must be written in a language the user-agent can interpret, such as JavaScript, even if the server-side script is written in Groovy.
To create, view, or modify the content of the scripts, go to Realms > Realm Name > Scripts.
amsterattribute:clientScriptssoadmattribute:iplanet-am-auth-scripted-client-script - Server-side Script
-
Specifies the ID of the script to run in AM after the client-side script has completed.
To create, view, or modify the content of the scripts, go to Realms > Realm Name > Scripts.
amsterattribute:serverScriptssoadmattribute:iplanet-am-auth-scripted-server-script - Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the scripted authentication module.
The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:iplanet-am-auth-scripted-auth-levelIn the AM admin UI, go to Configure > Global Services > Scripting > Secondary Configurations > Server-Side Script Type > Secondary Configurations > engineConfiguration.
On the engineConfiguration page, configure the following settings for the scripting engine of the selected type:
- Server-side Script Timeout
-
Specifies the maximum execution time any individual script should take on the server (in seconds). AM terminates scripts which take longer to run than this value.
ssoadmattribute:serverTimeout - Core thread pool size
-
Specifies the initial number of threads in the thread pool from which scripts operate. AM will ensure the pool contains at least this many threads.
ssoadmattribute:coreThreads - Maximum thread pool size
-
Specifies the maximum number of threads in the thread pool from which scripts operate. If no free thread is available in the pool, AM creates new threads in the pool for script execution up to the configured maximum. It is recommended to set the maximum number of threads to 300.
ssoadmattribute:maxThreads - Thread pool queue size
-
Specifies the number of threads to use for buffering script execution requests when the maximum thread pool size is reached.
For short, CPU-bound scripts, consider a small pool size and larger queue length. For I/O-bound scripts, for example, REST calls, consider a larger maximum pool size and a smaller queue.
Not hot-swappable: restart server for changes to take effect.
ssoadmattribute:queueSize - Thread idle timeout (seconds)
-
Specifies the length of time (in seconds) for a thread to be idle before AM terminates created threads. If the current pool size contains the number of threads set in
Core thread pool size, then idle threads will not be terminated, maintaining the initial pool size.ssoadmattribute:idleTimeout - Java class whitelist
-
Specifies the list of class name patterns allowed to be invoked by the script. Every class accessed by the script must match at least one of these patterns.
You can specify the class name as-is or use a regular expression.
ssoadmattribute:whiteList - Java class blacklist
-
Specifies the list of class name patterns that are NOT allowed to be invoked by the script. The denylist is applied AFTER the allowlist to exclude those classes. Access to a class specified in both the allowlist and the denylist will be denied.
You can specify the class name to exclude as-is or use a regular expression.
ssoadmattribute:blackList - Use system SecurityManager
-
When enabled, AM makes a call to the
System.getSecurityManager().checkPackageAccess(…)method for each class that is accessed. The method throwsSecurityExceptionif the calling thread is not allowed to access the package.This feature only takes effect if the security manager is enabled for the JVM. ssoadmattribute:useSecurityManager
SecurID Authentication Module Properties
|
To use the SecurID authentication module,
you must first build an AM By default, the module uses the following TCP/IP ports: |
amster service name: securid
ssoadm service name: iPlanetAMAuthSecurIDService
- ACE/Server Configuration Path
-
Specify the directory where the SecurID ACE/Server
sdconf.recfile is located, which by default is expected under the AM configuration directory, such as/path/to/openam/config/auth/ace/data. The directory must exist before AM can use SecurID authentication.amsterattribute:serverConfigPathssoadmattribute:iplanet-am-auth-securid-server-config-path - Authentication Level
-
Sets the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:iplanet-am-auth-securid-auth-level
Social authentication module properties - Instagram
amster service name: SocialAuthInstagramModule
ssoadm service name: iPlanetAMAuthSocialAuthInstagramService
Core
The following properties are available under the Core tab:
- Authentication Level
-
Specifies the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
Default:
0amsterdata attribute:authenticationLevel - Social Provider
-
Specifies the name of the social provider for which this module is being set up.
Default:
Instagramamsterdata attribute:provider - Client Id
-
Specifies the
client_idparameter as described in section 2.2 of The OAuth 2.0 Authorization Framework (RFC 6749).To register an application with Instagram and obtain an OAuth 2.0
client_idandclient_secret, visit https://www.instagram.com/developer/.amsterattribute:clientId - Client Secret
-
Specifies the
client_secretparameter as described in section 2.3 of The OAuth 2.0 Authorization Framework (RFC 6749).amsterattribute:clientSecret - Authentication Endpoint URL
-
Specifies the URL to the social provider’s endpoint handling authentication as described in section 3.1 of The OAuth 2.0 Authorization Framework (RFC 6749).
amsterattribute:authorizeEndpoint - Access Token Endpoint URL
-
Specifies the URL to the endpoint handling access tokens as described in section 3.2 of The OAuth 2.0 Authorization Framework (RFC 6749).
amsterattribute:tokenEndpoint - User Profile Service URL
-
Specifies the user profile URL that returns profile information in JSON format.
amsterattribute:userInfoEndpoint - Scope
-
Specifies a list of user profile attributes that the client application requires, according to The OAuth 2.0 Authorization Framework (RFC 6749). The list depends on the permissions that the resource owner, such as the end user, grants to the client application.
Default:
basicamsterattribute:scope - Scope Delimiter
-
Specifies the delimiter used to separate scope values.
Some authorization servers use non-standard separators for scopes. Facebook, for example, uses commas.
Default: space character
amsterattribute:scopeDelimiter - Subject Property
-
Specifies the attribute the social provider uses to identify a user.
Default:
idamsterattribute:subjectProperty - Use Basic Auth
-
Specifies that the client uses HTTP Basic authentication when authenticating to the social provider.
Valid values are:
-
true -
false
Default:
falseamsterattribute:usesBasicAuth -
- Proxy URL
-
Specifies the URL to the
/oauth2c/OAuthProxy.jspfile, which provides AM with GET to POST proxying capabilities. Change this URL only if an external server performs the GET to POST proxying.Default:
@SERVER_PROTO@://@SERVER_HOST@:@SERVER_PORT@/@SERVER_URI@/oauth2c/OAuthProxy.jspExample:
https://openam.example.com:8443/openam/oauth2c/OAuthProxy.jspamsterattribute:ssoProxyUrl - OAuth 2.0 Provider Logout Service
-
Specifies the URL of the social provider’s logout service.
To enable logout of the social authentication provider when logging out of AM, you must add
org.forgerock.openam.authentication.modules.oauth2.OAuth2PostAuthnPluginto the Authentication Post Processing Classes property. To add the class, go to Authentication > Settings > Post Authentication Processing.amsterattribute:logoutServiceUrl - Logout Options
-
Specifies the social provider logout actions to take when logging out of AM.
Valid options are:
prompt-
Asks the user whether or not to log out from the social provider.
logout-
Logs the user out of the social provider without prompting.
donotlogout-
Keeps the user logged in to the social provider. There is no prompt to the user.
Default:
promptamsterattribute:logoutBehaviour
Account Provisioning
The following properties are available under the Account Provisioning tab:
- Use IDM as Registration Service
-
Whether to use IDM as an external registration service to complete registration for new users. You must configure and enable the IDM Provisioning service to use this option. See IDM Provisioning.
AM passes IDM these parameters:
-
clientToken: Signed, encrypted JWT of the OAuth 2.0 authentication state. -
returnParams: Encoded URL parameters, required to be returned to AM to resume authentication after registration in IDM is complete.
Default:
Falseamsterattribute:enableRegistrationService -
- Create account if it does not exist
-
When enabled, AM creates an account for the user if the user profile does not exist.
When disabled, a user without a profile may still log into AM if the Ignore Profile attribute is set in the authentication service of the realm, or if the account is mapped to an anonymous account.
Valid values are:
-
true -
false
Default:
trueamsterattribute:createAccount -
- Account Provider
-
Specifies the name of the class that implements the account provider.
Default:
org.forgerock.openam.authentication.modules.common.mapping.DefaultAccountProvideramsterattribute:accountProviderClass - Account Mapper
-
Specifies the name of the class that implements the attribute mapping for the account search.
You can provide string constructor parameters by appending pipe-separated (|) values. Default:
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper|*|instagram-amsterattribute:accountMapperClass - Account Mapper Configuration
-
Specifies the attribute configuration used to map the account of the user authenticated in the social provider to the local data store in AM. Valid values take the form
provider-attr=local-attr`.When using the
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapperclass, you can parse JSON objects in mappings, by using dot notation.For example, given a JSON payload of:
{ "sub" : "12345", "name" : { "first_name" : "Demo", "last_name" : "User" } }jsonYou can create a mapper, such as
name.first_name=cn.Default:
id=uidamsterattribute:accountMapperConfiguration - Attribute Mapper
-
Specifies the list of fully qualified class names for implementations that map attributes from the social provider to AM profile attributes.
You can provide a custom attribute mapper. A custom attribute mapper must implement the
org.forgerock.openam.authentication.modules.common.mapping.AttributeMapperinterface.Provided implementations are:
-
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper -
org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapper- can only be used when using theopenidscope
You can provide string constructor parameters by appending pipe-separated (|) values.
For example, the
org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapperclass can take two constructor parameters:a comma-separated list of attributes, and a prefix to apply to their values. Specify these as follows:org.forgerock.openam.authentication.modules.oidc.JsonAttributeMapper|uid|instagram-
Default:
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper|uid|instagram-amsterattribute:attributeMappingClasses -
- Attribute Mapper Configuration
-
Specifies a map of social provider user account attributes to local user profile attributes with values in the form
provider-attr=local-attr.
|
When using the For example, given a JSON payload of: json You can create a mapper, such as |
Default:
id=uid
full_name=sn
username=cn
username=givenName
amster attribute: attributeMapperConfiguration
- Map to anonymous user
-
When enabled, maps the social provider authenticated user to a specified anonymous user. If the Create account if it does not exist property is enabled, AM creates an account for the authenticated user instead of mapping the account to an anonymous user.
Valid values are:
-
true -
false
Default:
falseamsterattribute:mapToAnonymousUser -
- Anonymous User
-
Specifies an anonymous user that exists in the current realm. The user status of this anonymous user must be
Active. TheMap to anonymous user propertymaps authorized users without a profile to this anonyomus user, if enabled.Default:
anonymousamsterattribute:anonymousUserName - Save attributes in the session
-
When enabled, saves the values of attributes specified in the Attribute Mapper Configuration property in the AM session.
Valid values are:
-
true -
false
Default:
trueamsterattribute:saveAttributesInSession -
Social authentication module properties - OAuth 2.0
amster service name: SocialAuthOAuth2Module
ssoadm service name: iPlanetAMAuthSocialAuthOAuth2Service
Core
The following properties are available under the Core tab:
- Authentication Level
-
Specifies the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
Default:
0amsterdata attribute:authenticationLevel - Social Provider
-
Specifies the name of the social provider for which this module is being set up.
Example:
Googleamsterdata attribute:provider - Client Id
-
Specifies the
client_idparameter as described in section 2.2 of The OAuth 2.0 Authorization Framework (RFC 6749).amsterattribute:clientId - Client Secret
-
Specifies the
client_secretparameter as described in section 2.3 of The OAuth 2.0 Authorization Framework (RFC 6749).amsterattribute:clientSecret - Authentication Endpoint URL
-
Specifies the URL to the social provider’s endpoint handling authentication as described in section 3.1 of The OAuth 2.0 Authorization Framework (RFC 6749).
Example:
https://accounts.google.com/o/oauth2/v2/authamsterattribute:authorizeEndpoint - Access Token Endpoint URL
-
Specifies the URL to the endpoint handling access tokens as described in section 3.2 of The OAuth 2.0 Authorization Framework (RFC 6749).
Example:
https://www.googleapis.com/oauth2/v4/tokenamsterattribute:tokenEndpoint - User Profile Service URL
-
Specifies the user profile URL that returns profile information in JSON format.
amsterattribute:userInfoEndpoint - Scope
-
Specifies a list of user profile attributes that the client application requires, according to The OAuth 2.0 Authorization Framework (RFC 6749). The list depends on the permissions that the resource owner, such as the end user, grants to the client application.
amsterattribute:scope - Scope Delimiter
-
Specifies the delimiter used to separate scope values.
Some authorization servers use non-standard separators for scopes. Facebook, for example, uses commas.
amsterattribute:scopeDelimiter - Subject Property
-
Specifies the attribute the social provider uses to identify a user.
Example:
subamsterattribute:subjectProperty - Use Basic Auth
-
Specifies that the client uses HTTP Basic authentication when authenticating to the social provider.
Valid values are:
-
true -
false
Default:
trueamsterattribute:usesBasicAuth -
- Proxy URL
-
Specifies the URL to the
/oauth2c/OAuthProxy.jspfile, which provides AM with GET to POST proxying capabilities. Change this URL only if an external server performs the GET to POST proxying.Default:
@SERVER_PROTO@://@SERVER_HOST@:@SERVER_PORT@/@SERVER_URI@/oauth2c/OAuthProxy.jspExample:
https://openam.example.com:8443/openam/oauth2c/OAuthProxy.jspamsterattribute:ssoProxyUrl - OAuth 2.0 Provider Logout Service
-
Specifies the URL of the social provider’s logout service.
To enable logout of the social authentication provider when logging out of AM, you must add
org.forgerock.openam.authentication.modules.oauth2.OAuth2PostAuthnPluginto the Authentication Post Processing Classes property. To add the class, go to Authentication > Settings > Post Authentication Processing.amsterattribute:logoutServiceUrl - Logout Options
-
Specifies the social provider logout actions to take when logging out of AM.
Valid options are:
prompt-
Asks the user whether or not to log out from the social provider.
logout-
Logs the user out of the social provider without prompting.
donotlogout-
Keeps the user logged in to the social provider. There is no prompt to the user.
Default:
promptamsterattribute:logoutBehaviour - Token Issuer
-
Corresponds to the expected issue identifier value in the
issfield of the ID token.Example:
https://accounts.google.comamsterattribute:issuerName - OAuth 2.0 Mix-Up Mitigation Enabled
-
Controls whether the OAuth 2.0 authentication module carries out additional verification steps when it receives the authorization code from the authorization server.
Specifies that the client must compare the issuer identifier of the authorization server upon registration with the issuer value returned in the
issresponse parameter. If they do not match, the client must abort the authorization process. The client must also confirm that the authorization server’s response is intended for the client by comparing the client’s client identifier to the value of theclient_idresponse parameter.The Token Issuer property must be entered when the OAuth 2.0 Mix-Up Mitigation feature is enabled, so that the validation can succeed. The authorization code response will contain an issuer value (
iss) that will be validated by the client.Consult with the authorization server’s documentation on what value it uses for the issuer field. For more information, see section 4 of OAuth 2.0 Mix-Up Mitigation Draft.
amsterattribute:mixUpMitigation
Account Provisioning
The following properties are available under the Account Provisioning tab:
- Use IDM as Registration Service
-
Whether to use IDM as an external registration service to complete registration for new users. You must configure and enable the IDM Provisioning service to use this option. See IDM Provisioning
AM passes IDM these parameters:
-
clientToken: Signed, encrypted JWT of the OAuth 2.0 authentication state. -
returnParams: Encoded URL parameters, required to be returned to AM to resume authentication after registration in IDM is complete.
Default:
Falseamsterattribute:enableRegistrationService -
- Create account if it does not exist
-
When enabled, AM creates an account for the user if the user profile does not exist. If the Prompt for password setting and activation code attribute is enabled, AM prompts the user for a password and activation code before creating the account.
When configured to create new accounts, the SMTP settings must also be valid. As part of account creation, the authentication module sends the resource owner an email with an account activation code. To send the mail, AM uses the SMTP settings you provide in the module configuration.
When disabled, a user without a profile may still log into AM if the Ignore Profile attribute is set in the authentication service of the realm, or if the account is mapped to an anonymous account.
Valid values are:
-
true -
false
Default:
trueamsterattribute:createAccount -
- Account Provider
-
Specifies the name of the class that implements the account provider.
Default:
org.forgerock.openam.authentication.modules.common.mapping.DefaultAccountProvideramsterattribute:accountProviderClass - Account Mapper
-
Specifies the name of the class that implements the attribute mapping for the account search.
Example:
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper|*|google-amsterattribute:accountMapperClass - Account Mapper Configuration
-
Specifies the attribute configuration used to map the account of the user authenticated in the social provider to the local data store in AM. Valid values take the form
provider-attr=local-attr.When using the
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapperclass, you can parse JSON objects in mappings, by using dot notation.For example, given a JSON payload of:
{ "sub" : "12345", "name" : { "first_name" : "Demo", "last_name" : "User" } }jsonYou can create a mapper, such as
name.first_name=cn.amsterattribute:accountMapperConfiguration - Attribute Mapper
-
Specifies the list of fully qualified class names for implementations that map attributes from the social provider to AM profile attributes.
You can provide a custom attribute mapper. A custom attribute mapper must implement the
org.forgerock.openam.authentication.modules.common.mapping.AttributeMapperinterface.Provided implementations are:
-
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper -
org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapper- can only be used when using theopenidscope
You can provide string constructor parameters by appending pipe-separated (|) values.
For example, the
org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapperclass can take two constructor parameters: a comma-separated list of attributes, and a prefix to apply to their values. Specify these as follows:org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapper|*|google-
amsterattribute:attributeMappingClasses -
- Attribute Mapper Configuration
-
Specifies a map of social provider user account attributes to local user profile attributes with values in the form
provider-attr=local-attr.When using the
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapperclass, you can parse JSON objects in mappings, by using dot notation.For example, given a JSON payload of:
{ "sub" : "12345", "name" : { "first_name" : "Demo", "last_name" : "User" } }jsonYou can create a mapper, such as
name.first_name=cn.amsterattribute:attributeMapperConfiguration - Prompt for password setting and activation code
-
When enabled, the user must set a password before AM creates an account dynamically. An activation code is also sent to the user’s email address. Both the password and the code are required before the account is created.
Valid values are:
-
true -
false
Default:
falseamsterattribute:promptPasswordFlag -
- Map to anonymous user
-
When enabled, maps the social provider authenticated user to a specified anonymous user. If the Create account if it does not exist property is enabled, AM creates an account for the authenticated user instead of mapping the account to an anonymous user.
Valid values are:
-
true -
false
Default:
falseamsterattribute:mapToAnonymousUser -
- Anonymous User
-
Specifies an anonymous user that exists in the current realm. The user status of this anonymous user must be
Active. TheMap to anonymous userproperty maps authorized users without a profile to this anonymous user, if enabled.Default:
anonymousamsterattribute:anonymousUserName - Save attributes in the session
-
When enabled, saves the values of attributes specified in the Attribute Mapper Configuration property in the AM session.
Valid values are:
-
true -
false
Default:
trueamsterattribute:saveAttributesInSession -
The following properties are available under the Email tab:
- Email attribute in the Response
-
Specifies the attribute identifying the authenticated user’s email address in the response from the profile service in the social provider. This setting is used to send an email message with an activation code for accounts created dynamically.
amsterattribute:emailAttribute - Mail Server Gateway implementation class
-
Specifies the class used by the module to send email. A custom subclass of
org.forgerock.openam.authentication.modules.oauth2.EmailGatewayclass can be provided.Default:
org.forgerock.openam.authentication.modules.oauth2.DefaultEmailGatewayImplamsterattribute:emailGateway - SMTP host
-
Specifies the host name of the mail server.
Default:
localhostamsterattribute:smtpHost - SMTP port
-
Specifies the SMTP port number for the mail server.
Default:
25amsterattribute:smtpPort - SMTP User Name
-
Specifies the username AM uses to authenticate to the mail server.
amsterattribute:smtpUsername - SMTP User Password
-
Specifies the password AM uses to authenticate to the mail server.
amsterattribute:smtpPassword - SMTP SSL Enabled
-
When enabled, connects to the mail server over SSL. AM must be able to trust the SMTP server certificate.
Valid values are:
-
true -
false
Default:
falseamsterattribute:smtpSslEnabled -
- SMTP From address
-
Specifies the address of the email sender, such as
no-reply@example.com.amsterattribute:smtpFromAddress
Social authentication module properties - OpenID Connect 1.0
The example settings are for Google.
amster service name: SocialAuthOpenIDModule
ssoadm service name: iPlanetAMAuthSocialAuthOpenIDService
Core
The following properties are available under the Core tab:
- Social Provider
-
Specifies the name of the social provider for which this module is being set up.
Example:
Googleamsterdata attribute:provider - Client Id
-
Specifies the
client_idparameter as described in section 2.2 of The OAuth 2.0 Authorization Framework (RFC 6749).amsterattribute:clientId - Client Secret
-
Specifies the
client_secretparameter as described in section 2.3 of The OAuth 2.0 Authorization Framework (RFC 6749).amsterattribute:clientSecret - Authentication Level
-
Specifies the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
Default:
0amsterdata attribute:authenticationLevel - Authentication Endpoint URL
-
Specifies the URL to the social provider’s endpoint handling authentication as described in section 3.1 of The OAuth 2.0 Authorization Framework (RFC 6749).
amsterattribute:authorizeEndpoint - Access Token Endpoint URL
-
Specifies the URL to the endpoint handling access tokens as described in section 3.2 of The OAuth 2.0 Authorization Framework (RFC 6749).
amsterattribute:tokenEndpoint - User Profile Service URL
-
Specifies the user profile URL that returns profile information in JSON format.
amsterattribute:userInfoEndpoint - Scope
-
Specifies a list of user profile attributes that the client application requires, according to The OAuth 2.0 Authorization Framework (RFC 6749). The list depends on the permissions that the resource owner, such as the end user, grants to the client application.
Default:
openidamsterattribute:scope - Scope Delimiter
-
Specifies the delimiter used to separate scope values.
Some authorization servers use non-standard separators for scopes. Facebook, for example, uses commas.
amsterattribute:scopeDelimiter - Subject Property
-
Specifies the attribute the social provider uses to identify a user.
Example:
subamsterattribute:subjectProperty - Use Basic Auth
-
Specifies that the client uses HTTP Basic authentication when authenticating to the social provider.
Valid values are:
-
true -
false
Default:
trueamsterattribute:usesBasicAuth -
- Proxy URL
-
Specifies the URL to the
/oauth2c/OAuthProxy.jspfile, which provides AM with GET to POST proxying capabilities. Change this URL only if an external server performs the GET to POST proxying.Default:
@SERVER_PROTO@://@SERVER_HOST@:@SERVER_PORT@/@SERVER_URI@/oauth2c/OAuthProxy.jspExample:
https://openam.example.com:8443/openam/oauth2c/OAuthProxy.jspamsterattribute:ssoProxyUrl - OAuth 2.0 Provider Logout Service
-
Specifies the URL of the social provider’s logout service.
To enable logout of the social authentication provider when logging out of AM, you must add
org.forgerock.openam.authentication.modules.oauth2.OAuth2PostAuthnPluginto the Authentication Post Processing Classes property. To add the class, go to Authentication > Settings > Post Authentication Processing.amsterattribute:logoutServiceUrl - Logout Options
-
Specifies the social provider logout actions to take when logging out of AM.
Valid options are:
prompt-
Asks the user whether or not to log out from the social provider.
logout-
Logs the user out of the social provider without prompting.
donotlogout-
Keeps the user logged in to the social provider. There is no prompt to the user.
Default:
promptamsterattribute:logoutBehaviour - Token Issuer
-
Corresponds to the expected issue identifier value in the
issfield of the ID token.Example:
https://accounts.google.comamsterattribute:issuerName - OAuth 2.0 Mix-Up Mitigation Enabled
-
Controls whether the OAuth 2.0 authentication module carries out additional verification steps when it receives the authorization code from the authorization server.
Specifies that the client must compare the issuer identifier of the authorization server upon registration with the issuer value returned in the
issresponse parameter. If they do not match, the client must abort the authorization process. The client must also confirm that the authorization server’s response is intended for the client by comparing the client’s client identifier to the value of theclient_idresponse parameter.The Token Issuer property must be entered when the OAuth 2.0 Mix-Up Mitigation feature is enabled, so that the validation can succeed. The authorization code response will contain an issuer value (
iss) that will be validated by the client.Consult with the authorization server’s documentation on what value it uses for the issuer field. For more information, see section 4 of OAuth 2.0 Mix-Up Mitigation Draft.
amsterattribute:mixUpMitigation
OpenID Connect
The following properties are available under the OpenID Connect tab:
- OpenID Connect validation configuration type
-
In order to validate the ID token from the OpenID Connect provider, the module needs either a URL to get the public keys for the provider, or the symmetric key for an ID token signed with a HMAC-based algorithm.
By default, the configuration type is .well-known/openid-configuration_url.
This means the module should retrieve the keys
based on information in the OpenID Connect Provider Configuration Document.
You can instead configure the authentication module to validate the ID token signature with the client secret key you provide, or to validate the ID token with the keys retrieved from the URL to the OpenID Connect provider’s JSON web key set.
.well-known/openid-configuration_url(Default)-
Retrieve the provider keys based on the information provided in the OpenID Connect Provider Configuration Document.
Specify the URL to the document in the OpenID Connect validation configuration value property
client_secret-
Use the client secret that you specify in the Client Secret property (not the OpenID Connect validation configuration value property, which is ignored) as the key to validate the ID token signature according to the HMAC, using the client secret to the decrypt the hash and then checking that the hash matches the hash of the ID token JWT.
jwk_url-
Retrieve the provider’s JSON web key set at the URL that you specify in the OpenID Connect validation configuration value property.
amsterattribute:cryptoContextType- OpenID Connect validation configuration value
-
Specifies the full URL to the discovery or JWK location, corresponding to the configuration type selected in the OpenID Connect validation configuration type property.
amsterattribute:cryptoContextValue
Account Provisioning
The following properties are available under the Account Provisioning tab:
- Use IDM as Registration Service
-
Whether to use IDM as an external registration service to complete registration for new users. You must configure and enable the IDM Provisioning service to use this option. See IDM Provisioning.
AM passes IDM these parameters:
-
clientToken: Signed, encrypted JWT of the OAuth 2.0 authentication state. -
returnParams: Encoded URL parameters, required to be returned to AM to resume authentication after registration in IDM is complete.
Default:
Falseamsterattribute:enableRegistrationService -
- Create account if it does not exist
-
When enabled, AM creates an account for the user if the user profile does not exist. If the Prompt for password setting and activation code attribute is enabled, AM prompts the user for a password and activation code before creating the account.
When configured to create new accounts, the SMTP settings must also be valid. As part of account creation, the authentication module sends the resource owner an email with an account activation code. To send the mail, AM uses the SMTP settings you provide in the module configuration.
When disabled, a user without a profile may still log into AM if the Ignore Profile attribute is set in the authentication service of the realm, or if the account is mapped to an anonymous account.
Valid values are:
-
true -
false
Default:
trueamsterattribute:createAccount -
- Account Provider
-
Specifies the name of the class that implements the account provider.
Default:
org.forgerock.openam.authentication.modules.common.mapping.DefaultAccountProvideramsterattribute:accountProviderClass - Account Mapper
-
Specifies the name of the class that implements the attribute mapping for the account search.
You can provide string constructor parameters by appending pipe-separated (|) values. Example:
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper|*|google-amsterattribute:accountMapperClass - Account Mapper Configuration
-
Specifies the attribute configuration used to map the account of the user authenticated in the social provider to the local data store in AM. Valid values take the form
provider-attr=local-attr.When using the
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapperclass, you can parse JSON objects in mappings, by using dot notation.For example, given a JSON payload of:
{ "sub" : "12345", "name" : { "first_name" : "Demo", "last_name" : "User" } }jsonYou can create a mapper, such as
name.first_name=cn.amsterattribute:accountMapperConfiguration - Attribute Mapper
-
Specifies the list of fully qualified class names for implementations that map attributes from the social provider to AM profile attributes.
You can provide a custom attribute mapper. A custom attribute mapper must implement the
org.forgerock.openam.authentication.modules.common.mapping.AttributeMapperinterface.Provided implementations are:
-
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper -
org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapper- can only be used when using theopenidscope
You can provide string constructor parameters by appending pipe-separated (|) values.
For example, the
org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapperclass can take two constructor parameters: a comma-separated list of attributes, and a prefix to apply to their values. Specify these as follows:org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapper|*|google-
amsterattribute:attributeMappingClasses -
- Attribute Mapper Configuration
-
Specifies a map of social provider user account attributes to local user profile attributes with values in the form
provider-attr=local-attr.When using the
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapperclass, you can parse JSON objects in mappings, by using dot notation.For example, given a JSON payload of:
{ "sub" : "12345", "name" : { "first_name" : "Demo", "last_name" : "User" } }jsonYou can create a mapper, such as
name.first_name=cn.amsterattribute:attributeMapperConfiguration - Prompt for password setting and activation code
-
When enabled, the user must set a password before AM creates an account dynamically. An activation code is also sent to the user’s email address. Both the password and the code are required before the account is created.
Valid values are:
-
true -
false
Default:
falseamsterattribute:promptPasswordFlag -
- Map to anonymous user
-
When enabled, maps the social provider authenticated user to a specified anonymous user. If the Create account if it does not exist property is enabled, AM creates an account for the authenticated user instead of mapping the account to an anonymous user.
Valid values are:
-
true -
false
Default:
falseamsterattribute:mapToAnonymousUser -
- Anonymous User
-
Specifies an anonymous user that exists in the current realm. The user status of this anonymous user must be
Active. TheMap to anonymous userproperty maps authorized users without a profile to this anonyomus user, if enabled.Default:
anonymousamsterattribute:anonymousUserName - Save attributes in the session
-
When enabled, saves the values of attributes specified in the Attribute Mapper Configuration property in the AM session.
Valid values are:
-
true -
false
Default:
trueamsterattribute:saveAttributesInSession -
The following properties are available under the Email tab:
- Email attribute in the Response
-
Specifies the attribute identifying the authenticated user’s email address in the response from the profile service in the social provider. This setting is used to send an email message with an activation code for accounts created dynamically.
amsterattribute:emailAttribute - Mail Server Gateway implementation class
-
Specifies the class used by the module to send email. A custom subclass of
org.forgerock.openam.authentication.modules.oauth2.EmailGatewayclass can be provided.Default:
org.forgerock.openam.authentication.modules.oauth2.DefaultEmailGatewayImplamsterattribute:emailGateway - SMTP host
-
Specifies the host name of the mail server.
Default:
localhostamsterattribute:smtpHost - SMTP port
-
Specifies the SMTP port number for the mail server.
Default:
25amsterattribute:smtpPort - SMTP User Name
-
Specifies the username AM uses to authenticate to the mail server.
amsterattribute:smtpUsername - SMTP User Password
-
Specifies the password AM uses to authenticate to the mail server.
amsterattribute:smtpPassword - SMTP SSL Enabled
-
When enabled, connects to the mail server over SSL. AM must be able to trust the SMTP server certificate.
Valid values are:
-
true -
false
Default:
falseamsterattribute:smtpSslEnabled -
- SMTP From address
-
Specifies the address of the email sender, such as
no-reply@example.com.amsterattribute:smtpFromAddress
Social authentication module properties - VKontakte
amster service name: SocialAuthVKontakteModule
ssoadm service name: iPlanetAMAuthSocialAuthVKService
Core
The following properties are available under the Core tab:
- Social Provider
-
Specifies the name of the social provider for which this module is being set up.
Default:
VKontakteamsterdata attribute:provider - Client Id
-
Specifies the
client_idparameter as described in section 2.2 of The OAuth 2.0 Authorization Framework (RFC 6749).To register an application with VKontakte and obtain an OAuth 2.0
client_idandclient_secret, visit https://vk.com/apps?act=manage.amsterattribute:clientId - Client Secret
-
Specifies the
client_secretparameter as described in section 2.3 of The OAuth 2.0 Authorization Framework (RFC 6749).amsterattribute:clientSecret - Authentication Level
-
Specifies the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
Default:
0amsterdata attribute:authenticationLevel - Authentication Endpoint URL
-
Specifies the URL to the endpoint handling authentication as described in section 3.1 of The OAuth 2.0 Authorization Framework (RFC 6749).
Default:
https://oauth.vk.com/authorizeamsterattribute:authorizeEndpoint - Access Token Endpoint URL
-
Specifies the URL to the social provider’s endpoint handling access tokens as described in section 3.2 of The OAuth 2.0 Authorization Framework (RFC 6749).
Default:
https://oauth.vk.com/access_tokenamsterattribute:tokenEndpoint - User Profile Service URL
-
Specifies the user profile URL that returns profile information in JSON format.
Default:
https://api.vk.com/method/users.getamsterattribute:userInfoEndpoint - Scope
-
Specifies a list of user profile attributes that the client application requires, according to The OAuth 2.0 Authorization Framework (RFC 6749). The list depends on the permissions that the resource owner, such as the end user, grants to the client application.
amsterattribute:scope - Proxy URL
-
Specifies the URL to the
/oauth2c/OAuthProxy.jspfile, which provides AM with GET to POST proxying capabilities. Change this URL only if an external server performs the GET to POST proxying.Default:
@SERVER_PROTO@://@SERVER_HOST@:@SERVER_PORT@/@SERVER_URI@/oauth2c/OAuthProxy.jspExample:
https://openam.example.com:8443/openam/oauth2c/OAuthProxy.jspamsterattribute:ssoProxyUrl - Subject Property
-
Specifies the attribute the social provider uses to identify a user.
Default:
idamsterattribute:subjectProperty
Account Provisioning
The following properties are available under the Account Provisioning tab:
- Account Provider
-
Specifies the name of the class that implements the account provider.
Default:
org.forgerock.openam.authentication.modules.common.mapping.DefaultAccountProvideramsterattribute:accountProviderClass - Use IDM as Registration Service
-
Whether to use IDM as an external registration service to complete registration for new users. You must configure and enable the IDM Provisioning service to use this option. See IDM Provisioning.
AM passes IDM these parameters:
-
clientToken: Signed, encrypted JWT of the OAuth 2.0 authentication state. -
returnParams: Encoded URL parameters, required to be returned to AM to resume authentication after registration in IDM is complete.
Default:
Falseamsterattribute:enableRegistrationService -
- Create account if it does not exist
-
When enabled, AM creates an account for the user if the user profile does not exist. If the Prompt for password setting and activation code attribute is enabled, AM prompts the user for a password and activation code before creating the account.
When configured to create new accounts, the SMTP settings must also be valid. As part of account creation, the authentication module sends the resource owner an email with an account activation code. To send the mail, AM uses the SMTP settings you provide in the module configuration.
When disabled, a user without a profile may still log into AM if the Ignore Profile attribute is set in the authentication service of the realm, or if the account is mapped to an anonymous account.
Valid values are:
-
true -
false
Default:
trueamsterattribute:createAccount -
- Account Mapper
-
Specifies the name of the class that implements the attribute mapping for the account search.
Default:
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper|uid|vkontakte-amsterattribute:accountMapperClass - Account Mapper Configuration
-
Specifies the attribute configuration used to map the account of the user authenticated in the social provider to the local data store in AM. Valid values take the form
provider-attr=local-attr.When using the
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapperclass, you can parse JSON objects in mappings, by using dot notation.For example, given a JSON payload of:
{ "sub" : "12345", "name" : { "first_name" : "Demo", "last_name" : "User" } }jsonYou can create a mapper, such as
name.first_name=cn.Default:
uid=uidamsterattribute:accountMapperConfiguration - Attribute Mapper
-
Specifies the list of fully qualified class names for implementations that map attributes from the social provider to AM profile attributes.
You can provide a custom attribute mapper. A custom attribute mapper must implement the
org.forgerock.openam.authentication.modules.common.mapping.AttributeMapperinterface.Provided implementations are:
-
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper -
org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapper- can only be used when using theopenidscope
You can provide string constructor parameters by appending pipe-separated (|) values.
For example, the
org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapperclass can take two constructor parameters: a comma-separated list of attributes, and a prefix to apply to their values. Specify these as follows:org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapper|uid|vkontakte-
Default:
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper|uid|vkontakte-amsterattribute:attributeMappingClasses -
- Attribute Mapper Configuration
-
Specifies a map of social provider user account attributes to local user profile attributes with values in the form
provider-attr=local-attr.When using the
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapperclass, you can parse JSON objects in mappings, by using dot notation.For example, given a JSON payload of:
{ "sub" : "12345", "name" : { "first_name" : "Demo", "last_name" : "User" } }jsonYou can create a mapper, such as
name.first_name=cn.Default:
uid=uid
full_name=givenName
first_name=cn
last_name=sn
email=mailamsterattribute:attributeMapperConfiguration - Prompt for password setting and activation code
-
When enabled, the user must set a password before AM creates an account dynamically. An activation code is also sent to the user’s email address. Both the password and the code are required before the account is created.
Valid values are:
-
true -
false
Default:
falseamsterattribute:promptPasswordFlag -
- Map to anonymous user
-
When enabled, maps the social provider authenticated user to a specified anonymous user. If the Create account if it does not exist property is enabled, AM creates an account for the authenticated user instead of mapping the account to an anonymous user.
Valid values are:
-
true -
false
Default:
falseamsterattribute:mapToAnonymousUser -
- Anonymous User
-
Specifies an anonymous user that exists in the current realm. The user status of this anonymous user must be
Active. TheMap to anonymous userproperty maps authorized users without a profile to this anonyomus user, if enabled.Default:
anonymousamsterattribute:anonymousUserName - Save attributes in the session
-
When enabled, saves the values of attributes specified in the Attribute Mapper Configuration property in the AM session.
Valid values are:
-
true -
false
Default:
trueamsterattribute:saveAttributesInSession -
The following properties are available under the Email tab:
- Email attribute in the Response
-
Specifies the attribute identifying the authenticated user’s email address in the response from the profile service in the social provider. This setting is used to send an email message with an activation code for accounts created dynamically.
amsterattribute:emailAttribute - Mail Server Gateway implementation class
-
Specifies the class used by the module to send email. A custom subclass of
org.forgerock.openam.authentication.modules.oauth2.EmailGatewayclass can be provided.Default:
org.forgerock.openam.authentication.modules.oauth2.DefaultEmailGatewayImplamsterattribute:emailGateway - SMTP host
-
Specifies the host name of the mail server.
Default:
localhostamsterattribute:smtpHost - SMTP port
-
Specifies the SMTP port number for the mail server.
Default:
25amsterattribute:smtpPort - SMTP User Name
-
Specifies the username AM uses to authenticate to the mail server.
amsterattribute:smtpUsername - SMTP User Password
-
Specifies the password AM uses to authenticate to the mail server.
amsterattribute:smtpPassword - SMTP SSL Enabled
-
When enabled, connects to the mail server over SSL. AM must be able to trust the SMTP server certificate.
Valid values are:
-
true -
false
Default:
falseamsterattribute:smtpSslEnabled -
- SMTP From address
-
Specifies the address of the email sender, such as
no-reply@example.com.Default:
info@forgerock.comamsterattribute:smtpFromAddress
Social authentication module properties - WeChat
amster service name: SocialAuthWeChatModule
ssoadm service name: iPlanetAMAuthSocialAuthWeChatService
Core
The following properties are available under the Core tab:
- Authentication Level
-
Specifies the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
Default:
0amsterdata attribute:authenticationLevel - Social Provider
-
Specifies the name of the social provider for which this module is being set up.
Default:
WeChatamsterdata attribute:provider - Client Id
-
Specifies the
client_idparameter as described in section 2.2 of The OAuth 2.0 Authorization Framework (RFC 6749).To register an application with WeChat and obtain an OAuth 2.0
client_idandclient_secret, visit https://open.weixin.qq.com/cgi-bin/frame?t=home/web_tmpl.amsterattribute:clientId - Client Secret
-
Specifies the
client_secretparameter as described in section 2.3 of The OAuth 2.0 Authorization Framework (RFC 6749).amsterattribute:clientSecret - Authentication Endpoint URL
-
Specifies the URL to the social provider’s endpoint handling authentication as described in section 3.1 of The OAuth 2.0 Authorization Framework (RFC 6749).
Default:
https://open.weixin.qq.com/connect/qrconnectamsterattribute:authorizeEndpoint - Access Token Endpoint URL
-
Specifies the URL to the endpoint handling access tokens as described in section 3.2 of The OAuth 2.0 Authorization Framework (RFC 6749).
amsterattribute:tokenEndpoint - User Profile Service URL
-
Specifies the user profile URL that returns profile information in JSON format.
Default:
https://api.wechat.com/sns/userinfoamsterattribute:userInfoEndpoint - Scope
-
Specifies a list of user profile attributes that the client application requires, according to The OAuth 2.0 Authorization Framework (RFC 6749). The list depends on the permissions that the resource owner, such as the end user, grants to the client application.
amsterattribute:scope - Scope Delimiter
-
Specifies the delimiter used to separate scope values.
Some authorization servers use non-standard separators for scopes. Facebook, for example, uses commas.
Default: space character
amsterattribute:scopeDelimiter - Subject Property
-
Specifies the attribute the social provider uses to identify a user.
Default:
openidamsterattribute:subjectProperty - Use Basic Auth
-
Specifies that the client uses HTTP Basic authentication when authenticating to the social provider.
Valid values are:
-
true -
false
Default:
falseamsterattribute:usesBasicAuth -
- Proxy URL
-
Specifies the URL to the
/oauth2c/OAuthProxy.jspfile, which provides AM with GET to POST proxying capabilities. Change this URL only if an external server performs the GET to POST proxying.Default:
@SERVER_PROTO@://@SERVER_HOST@:@SERVER_PORT@/@SERVER_URI@/oauth2c/OAuthProxy.jspExample:
https://openam.example.com:8443/openam/oauth2c/OAuthProxy.jspamsterattribute:ssoProxyUrl
Account Provisioning
The following properties are available under the Account Provisioning tab:
- Use IDM as Registration Service
-
Whether to use IDM as an external registration service to complete registration for new users. You must configure and enable the IDM Provisioning service to use this option. See IDM Provisioning.
AM passes IDM these parameters:
-
clientToken: Signed, encrypted JWT of the OAuth 2.0 authentication state. -
returnParams: Encoded URL parameters, required to be returned to AM to resume authentication after registration in IDM is complete.
Default:
Falseamsterattribute:enableRegistrationService -
- Create account if it does not exist
-
When enabled, AM creates an account for the user if the user profile does not exist. If the Prompt for password setting and activation code attribute is enabled, AM prompts the user for a password and activation code before creating the account.
When configured to create new accounts, the SMTP settings must also be valid. As part of account creation, the authentication module sends the resource owner an email with an account activation code. To send the mail, AM uses the SMTP settings you provide in the module configuration.
When disabled, a user without a profile may still log into AM if the Ignore Profile attribute is set in the authentication service of the realm, or if the account is mapped to an anonymous account.
Valid values are:
-
true -
false
Default:
trueamsterattribute:createAccount -
- Account Provider
-
Specifies the name of the class that implements the account provider.
Default:
org.forgerock.openam.authentication.modules.common.mapping.DefaultAccountProvideramsterattribute:accountProviderClass - Account Mapper
-
Specifies the name of the class that implements the attribute mapping for the account search.
Default:
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper|*|wechat-amsterattribute:accountMapperClass - Account Mapper Configuration
-
Specifies the attribute configuration used to map the account of the user authenticated in the social provider to the local data store in AM. Valid values take the form
provider-attr=local-attr.When using the
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapperclass, you can parse JSON objects in mappings, by using dot notation.For example, given a JSON payload of:
{ "sub" : "12345", "name" : { "first_name" : "Demo", "last_name" : "User" } }jsonYou can create a mapper, such as
name.first_name=cn.Default:
openid=uidamsterattribute:accountMapperConfiguration - Attribute Mapper
-
Specifies the list of fully qualified class names for implementations that map attributes from the social provider to AM profile attributes.
You can provide a custom attribute mapper. A custom attribute mapper must implement the
org.forgerock.openam.authentication.modules.common.mapping.AttributeMapperinterface.Provided implementations are:
-
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper -
org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapper- can only be used when using theopenidscope
You can provide string constructor parameters by appending pipe-separated (|) values.
For example, the
org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapperclass can take two constructor parameters: a comma-separated list of attributes, and a prefix to apply to their values. Specify these as follows:org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapper|*|wechat-
Default:
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper|*|wechat-amsterattribute:attributeMappingClasses -
- Attribute Mapper Configuration
-
Specifies a map of social provider user account attributes to local user profile attributes with values in the form
provider-attr=local-attr.When using the
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapperclass, you can parse JSON objects in mappings, by using dot notation.For example, given a JSON payload of:
{ "sub" : "12345", "name" : { "first_name" : "Demo", "last_name" : "User" } }jsonYou can create a mapper, such as
name.first_name=cn.Default:
openid=uid
nickname=sn
nickname=cn
nickname=givenNameamsterattribute:attributeMapperConfiguration - Prompt for password setting and activation code
-
When enabled, the user must set a password before AM creates an account dynamically. An activation code is also sent to the user’s email address. Both the password and the code are required before the account is created.
Valid values are:
-
true -
false
Default:
falseamsterattribute:promptPasswordFlag -
- Map to anonymous user
-
When enabled, maps the social provider authenticated user to a specified anonymous user. If the Create account if it does not exist property is enabled, AM creates an account for the authenticated user instead of mapping the account to an anonymous user.
Valid values are:
-
true -
false
Default:
falseamsterattribute:mapToAnonymousUser -
- Anonymous User
-
Specifies an anonymous user that exists in the current realm. The user status of this anonymous user must be
Active. TheMap to anonymous userproperty maps authorized users without a profile to this anonyomus user, if enabled.Default:
anonymousamsterattribute:anonymousUserName - Save attributes in the session
-
When enabled, saves the values of attributes specified in the Attribute Mapper Configuration property in the AM session.
Valid values are:
-
true -
false
Default:
trueamsterattribute:saveAttributesInSession -
The following properties are available under the Email tab:
- Email attribute in the Response
-
Specifies the attribute identifying the authenticated user’s email address in the response from the profile service in the social provider. This setting is used to send an email message with an activation code for accounts created dynamically.
amsterattribute:emailAttribute - Mail Server Gateway implementation class
-
Specifies the class used by the module to send email. A custom subclass of
org.forgerock.openam.authentication.modules.oauth2.EmailGatewayclass can be provided.Default:
org.forgerock.openam.authentication.modules.oauth2.DefaultEmailGatewayImplamsterattribute:emailGateway - SMTP host
-
Specifies the host name of the mail server.
Default:
localhostamsterattribute:smtpHost - SMTP port
-
Specifies the SMTP port number for the mail server.
Default:
25amsterattribute:smtpPort - SMTP User Name
-
Specifies the username AM uses to authenticate to the mail server.
amsterattribute:smtpUsername - SMTP User Password
-
Specifies the password AM uses to authenticate to the mail server.
amsterattribute:smtpPassword - SMTP SSL Enabled
-
When enabled, connects to the mail server over SSL. AM must be able to trust the SMTP server certificate.
Valid values are:
-
true -
false
Default:
falseamsterattribute:smtpSslEnabled -
- SMTP From address
-
Specifies the address of the email sender, such as
no-reply@example.com.Default:
info@forgerock.comamsterattribute:smtpFromAddress
Social authentication module properties - WeChat Mobile
amster service name: SocialAuthWeChatMobileModule
ssoadm service name: iPlanetAMAuthSocialAuthWeChatMobileService
Core
The following properties are available under the Core tab:
- Authentication Level
-
Specifies the authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
Default:
0amsterdata attribute:authenticationLevel - Social Provider
-
Specifies the name of the social provider for which this module is being set up.
Default:
WeChatamsterdata attribute:provider - User Profile Service URL
-
Specifies the user profile URL that returns profile information in JSON format.
Default:
https://api.wechat.com/sns/userinfoamsterattribute:userInfoEndpoint - Scope
-
Specifies a list of user profile attributes that the client application requires, according to The OAuth 2.0 Authorization Framework (RFC 6749). The list depends on the permissions that the resource owner, such as the end user, grants to the client application.
Default:
snsapi_userinfoamsterattribute:scope - Subject Property
-
Specifies the attribute the social provider uses to identify a user.
Default:
openidamsterattribute:subjectProperty - Proxy URL
-
Specifies the URL to the
/oauth2c/OAuthProxy.jspfile, which provides AM with GET to POST proxying capabilities. Change this URL only if an external server performs the GET to POST proxying.Default:
@SERVER_PROTO@://@SERVER_HOST@:@SERVER_PORT@/@SERVER_URI@/oauth2c/OAuthProxy.jspExample:
https://openam.example.com:8443/openam/oauth2c/OAuthProxy.jspamsterattribute:ssoProxyUrl
Account Provisioning
The following properties are available under the Account Provisioning tab:
- Use IDM as Registration Service
-
Whether to use IDM as an external registration service to complete registration for new users. You must configure and enable the IDM Provisioning service to use this option. See IDM Provisioning.
AM passes IDM these parameters:
-
clientToken: Signed, encrypted JWT of the OAuth 2.0 authentication state. -
returnParams: Encoded URL parameters, required to be returned to AM to resume authentication after registration in IDM is complete.
Default:
Falseamsterattribute:enableRegistrationService -
- Create account if it does not exist
-
When enabled, AM creates an account for the user if the user profile does not exist. If the Prompt for password setting and activation code attribute is enabled, AM prompts the user for a password and activation code before creating the account.
When configured to create new accounts, the SMTP settings must also be valid. As part of account creation, the authentication module sends the resource owner an email with an account activation code. To send the mail, AM uses the SMTP settings you provide in the module configuration.
When disabled, a user without a profile may still log into AM if the Ignore Profile attribute is set in the authentication service of the realm, or if the account is mapped to an anonymous account.
Valid values are:
-
true -
false
Default:
trueamsterattribute:createAccount -
- Account Provider
-
Specifies the name of the class that implements the account provider.
Default:
org.forgerock.openam.authentication.modules.common.mapping.DefaultAccountProvideramsterattribute:accountProviderClass - Account Mapper
-
Specifies the name of the class that implements the attribute mapping for the account search.
Default:
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper|*|wechat-amsterattribute:accountMapperClass - Account Mapper Configuration
-
Specifies the attribute configuration used to map the account of the user authenticated in the social provider to the local data store in AM. Valid values take the form
provider-attr=local-attr.When using the
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapperclass, you can parse JSON objects in mappings, by using dot notation.For example, given a JSON payload of:
{ "sub" : "12345", "name" : { "first_name" : "Demo", "last_name" : "User" } }jsonYou can create a mapper, such as
name.first_name=cn.Default:
openid=uidamsterattribute:accountMapperConfiguration - Attribute Mapper
-
Specifies the list of fully qualified class names for implementations that map attributes from the social provider to AM profile attributes.
You can provide a custom attribute mapper. A custom attribute mapper must implement the
org.forgerock.openam.authentication.modules.common.mapping.AttributeMapperinterface.Provided implementations are:
-
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper -
org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapper- can only be used when using theopenidscope
You can provide string constructor parameters by appending pipe-separated (|) values.
For example, the
org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapperclass can take two constructor parameters: a comma-separated list of attributes, and a prefix to apply to their values. Specify these as follows:org.forgerock.openam.authentication.modules.oidc.JwtAttributeMapper|*|wechat-
Default:
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapper|*|wechat-amsterattribute:attributeMappingClasses -
- Attribute Mapper Configuration
-
Specifies a map of social provider user account attributes to local user profile attributes with values in the form
provider-attr=local-attr.When using the
org.forgerock.openam.authentication.modules.common.mapping.JsonAttributeMapperclass, you can parse JSON objects in mappings, by using dot notation.For example, given a JSON payload of:
{ "sub" : "12345", "name" : { "first_name" : "Demo", "last_name" : "User" } }jsonYou can create a mapper, such as
name.first_name=cn.Default:
openid=uid
nickname=sn
nickname=cn
nickname=givenNameamsterattribute:attributeMapperConfiguration - Prompt for password setting and activation code
-
When enabled, the user must set a password before AM creates an account dynamically. An activation code is also sent to the user’s email address. Both the password and the code are required before the account is created.
Valid values are:
-
true -
false
Default:
falseamsterattribute:promptPasswordFlag -
- Map to anonymous user
-
When enabled, maps the social provider authenticated user to a specified anonymous user. If the Create account if it does not exist property is enabled, AM creates an account for the authenticated user instead of mapping the account to an anonymous user.
Valid values are:
-
true -
false
Default:
falseamsterattribute:mapToAnonymousUser -
- Anonymous User
-
Specifies an anonymous user that exists in the current realm. The user status of this anonymous user must be
Active. TheMap to anonymous user propertymaps authorized users without a profile to this anonyomus user, if enabled.Default:
anonymousamsterattribute:anonymousUserName - Save attributes in the session
-
When enabled, saves the values of attributes specified in the Attribute Mapper Configuration property in the AM session.
Valid values are:
-
true -
false
Default:
trueamsterattribute:saveAttributesInSession -
The following properties are available under the Email tab:
- Email attribute in the Response
-
Specifies the attribute identifying the authenticated user’s email address in the response from the profile service in the social provider. This setting is used to send an email message with an activation code for accounts created dynamically.
amsterattribute:emailAttribute - Mail Server Gateway implementation class
-
Specifies the class used by the module to send email. A custom subclass of
org.forgerock.openam.authentication.modules.oauth2.EmailGatewayclass can be provided.Default:
org.forgerock.openam.authentication.modules.oauth2.DefaultEmailGatewayImplamsterattribute:emailGateway - SMTP host
-
Specifies the host name of the mail server.
Default:
localhostamsterattribute:smtpHost - SMTP port
-
Specifies the SMTP port number for the mail server.
Default:
25amsterattribute:smtpPort - SMTP User Name
-
Specifies the username AM uses to authenticate to the mail server.
amsterattribute:smtpUsername - SMTP User Password
-
Specifies the password AM uses to authenticate to the mail server.
amsterattribute:smtpPassword - SMTP SSL Enabled
-
When enabled, connects to the mail server over SSL. AM must be able to trust the SMTP server certificate.
Valid values are:
-
true -
false
Default:
falseamsterattribute:smtpSslEnabled -
- SMTP From address
-
Specifies the address of the email sender, such as
no-reply@example.com.Default:
info@forgerock.comamsterattribute:smtpFromAddress
Windows Desktop SSO authentication module properties
amster service name: WindowsDesktopSsoModule
ssoadm service name: iPlanetAMAuthWindowsDesktopSSOService
|
Before configuring the authentication module, create an Active Directory account and a |
- Service Principal
-
The Kerberos principal for authentication in the format
HTTP/host.domain@DC-DOMAIN-NAME.host.domain corresponds to the host and domain names of the AM instance and DC-DOMAIN-NAME is the domain name of the Kerberos realm (the FQDN of the Active Directory domain).
DC-DOMAIN-NAME can differ from the domain name for AM.
In multi-server deployments, configure host.domain as the load balancer FQDN or IP address in front of the AM instances. For example,
HTTP/openamLB.example.com@KERBEROSREALM.INTERNAL.COM.Learn more in How do I set up the WDSSO authentication module in PingAM in a load-balanced environment?.
amsterattribute:principalNamessoadmattribute:iplanet-am-auth-windowsdesktopsso-principal-name - Keytab File Name
-
The full path to the keytab file for the Service Principal. Generate the keytab file using the Windows
ktpassutility.amsterattribute:keytabFileNamessoadmattribute:iplanet-am-auth-windowsdesktopsso-keytab-file - Kerberos Realm
-
The Kerberos Key Distribution Center realm. For the Windows Kerberos service, this is the domain controller server domain name.
amsterattribute:kerberosRealmssoadmattribute:iplanet-am-auth-windowsdesktopsso-kerberos-realm - Kerberos Server Name
-
The FQDN of the Kerberos Key Distribution Center server; for example, the FQDN of the domain controller server.
amsterattribute:kerberosServerNamessoadmattribute:iplanet-am-auth-windowsdesktopsso-kdc - Return Principal with Domain Name
-
When enabled, AM automatically returns the Kerberos principal with the domain controller’s domain name during authentication.
amsterattribute:returnPrincipalWithDomainNamessoadmattribute:iplanet-am-auth-windowsdesktopsso-returnRealm - Authentication Level
-
The authentication level used to indicate the level of security associated with the module. The value can range from 0 to any positive integer.
amsterattribute:authenticationLevelssoadmattribute:iplanet-am-auth-windowsdesktopsso-auth-level - Trusted Kerberos realms
-
List of trusted Kerberos realms for user Kerberos tickets. When realms are configured, Kerberos tickets are only accepted if the realm part of the user principal name of the user’s Kerberos ticket matches a realm from the list.
amsterattribute:trustedKerberosRealmsssoadmattribute:iplanet-am-auth-windowsdesktopsso-kerberos-realms-trusted - isInitiator
-
Configuration used for the JDK Kerberos LoginModule (
Krb5LoginModule), which authenticates users using Kerberos principals. Possible values aretruefor initiator credentials, andfalsefor acceptor credentials.Default value:
trueamsterattribute:kerberosServiceIsinitiatorssoadmattribute:iplanet-am-auth-windowsdesktopsso-kerberos-isinitiator - Search for the user in the realm
-
Validates the user against the configured data stores. If the user from the Kerberos token isn’t found, authentication fails. If an authentication chain is set, the user can authenticate through another module. This search uses the
Alias Search Attribute Namefrom the core realm attributes. For details, refer to User Profile.amsterattribute:lookupUserInRealmssoadmattribute:iplanet-am-auth-windowsdesktopsso-lookupUserInRealm
Authenticating with Windows Desktop SSO over REST
To authenticate with Windows Desktop SSO over REST, add an Authorization header containing the string Basic,
followed by a base64-encoded string of the username, a colon character, and the password.
For example, if the credentials demo:Ch4ng31t are base64-encoded, the resulting string is ZGVtbzpDaDRuZzMxdA==.
The REST request would then be as follows:
$ curl \
--request POST \
--header "Content-Type: application/json" \
--header "Accept-API-Version: resource=2.0, protocol=1.0" \
--header "Authorization: Basic ZGVtbzpDaDRuZzMxdA==" \
'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/authenticate'
{
"tokenId":"AQIC5w…NTcy*",
"successUrl":"/openam/console",
"realm":"/alpha"
}Differences between authentication modules that support HOTP
|
AM provides two authentication modules that support OATH:
We recommend using the ForgeRock Authenticator (OATH) authentication module when possible. |
The ForgeRock Authenticator (OATH), OATH, and HOTP authentication modules let you configure authentication that prompts users to enter HMAC one-time passwords. It is important that administrators understand the differences among these authentication modules:
-
The ForgeRock Authenticator (OATH) and OATH authentication modules accept one-time passwords generated by the end user’s device, while the HOTP authentication module generates passwords and sends them to users by e-mail or SMS.
-
All three of the authentication modules support HOTP passwords. The ForgeRock Authenticator (OATH) and OATH authentication modules also support TOTP passwords.
-
The ForgeRock Authenticator (OATH) and OATH authentication modules require users to register their devices, and store the device registration details in the user profile. The HOTP authentication module requires the presence of mobile phone numbers and/or e-mail addresses in user profiles.
-
The ForgeRock Authenticator (OATH) authentication module can encrypt stored device registration details.
Before deciding on an implementation strategy, assess your requirements against the following capabilities in AM:
| Requirement | Available With the ForgeRock Authenticator (OATH) Authentication Module? | Available With the HOTP Authentication Module? |
|---|---|---|
End users can authenticate using a HOTP password |
✔ |
✔ |
AM can generate a HOTP password and send it to end users in a text message or an e-mail |
✖ |
✔ |
End users can register a mobile phone with AM, and an authenticator app on the phone can generate a HOTP or TOTP password that AM accepts as proof of authentication |
✔ |
✖ |
End users can authenticate with a TOTP password |
✔ |
✖ |
End users can opt out of providing a one-time password |
✔ |
✖ |
End users can authenticate using XUI |
✔ |
✔ |
Authentication modules configuration reference
The AM admin UI provides two places where you can configure authentication modules:
-
Under Configure > Authentication, you configure default properties for global authentication modules.
-
Under Realms > Realm Name > Authentication > Modules, you configure modules for your realm.
The configuration of individual modules depend on its function. The configuration of an Active Directory instead of the LDAP authentication module requires connection information and details about where to search for users. In contrast, the configuration of the HOTP module for OTP authentication requires data about the password length and the mail server or SMS gateway to send the password during authentication.
Account Active Check module
The Account Active Check module lets you determine whether an account is marked as active, or locked.
By default, AM checks if a user account is active or locked after processing an entire authentication chain. This means users with locked accounts may be asked to perform unnecessary authentication steps, such as providing a one-time password before authentication fails.
Use the Account Active Check module to check for active or locked status immediately after determining the user account; for example, after a DataStore or LDAP module. If the account is locked, the chain fails early without processing modules that appear after the Account Active Check module.
For more information, refer to Account lockout.
Active Directory authentication module
AM connects to Active Directory over Lightweight Directory Access Protocol (LDAP). AM provides separate Active Directory and LDAP modules to support the use of both Active Directory and another directory service in an authentication chain.
For detailed information about this module’s configuration properties, refer to Active Directory Module properties.
Adaptive Risk authentication module
The Adaptive Risk module is designed to assess risk during authentication, so that AM can determine whether to require the user to complete further authentication steps. After configuring the Adaptive Risk module, insert it in your authentication chain with criteria set to Sufficient as shown in the following example:
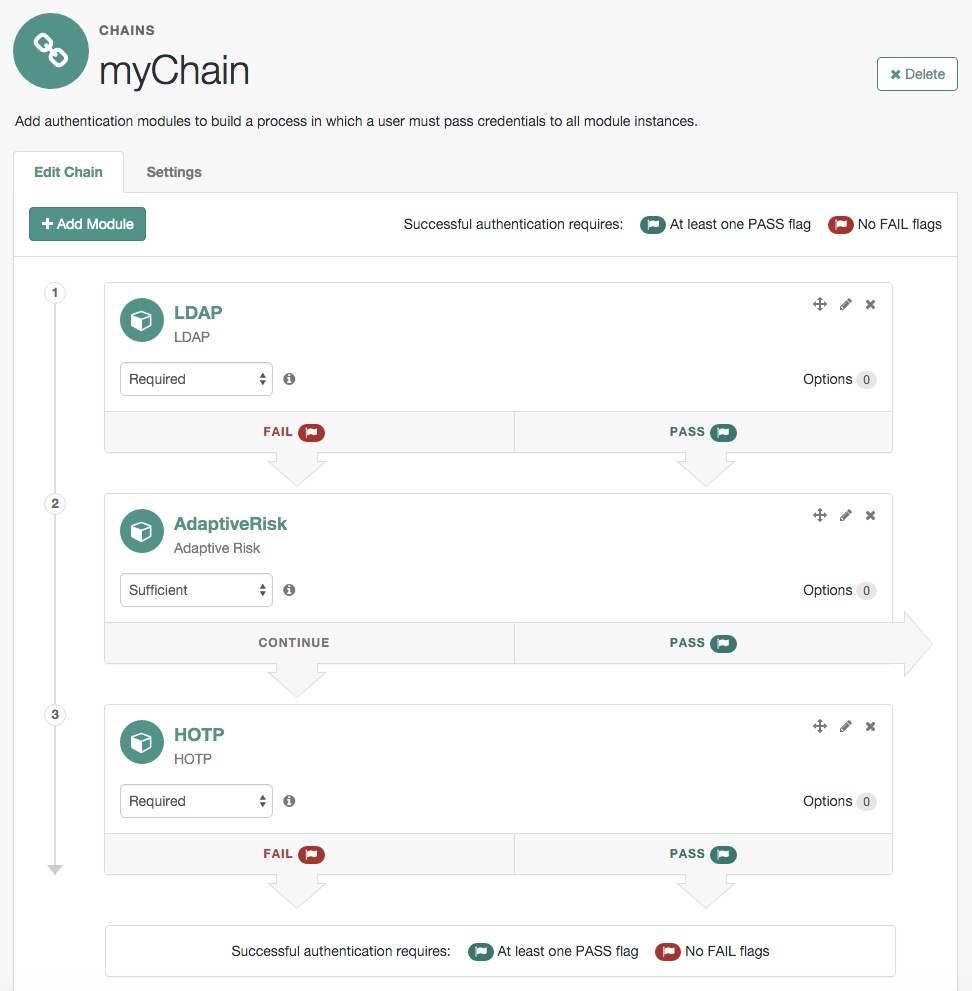
In the example authentication chain shown, AM has users authenticate first using the LDAP module providing a user ID and password combination. Upon success, AM calls the Adaptive Risk module. The Adaptive Risk module assesses the risk based on your configured parameters. If the Adaptive Risk module calculates a total score below the threshold you set, the module returns success, and AM finishes authentication processing without requiring further credentials. Otherwise, the Adaptive Risk module evaluates the score to be above the risk threshold, and returns failure. AM then calls the HOTP module, requiring the user to authenticate with a one-time password delivered to her by email or by SMS to her mobile phone.
When you configure the Adaptive Risk module to save cookies and profile attributes after successful authentication,
AM performs the save as post-authentication processing,
only after the entire authentication chain returns success.
You must set up AM to save the data as part of post-authentication processing
by editing the authentication chain to add
org.forgerock.openam.authentication.modules.adaptive.AdaptivePostAuthenticationPlugin
to the list of post-authentication plugins.
When the Adaptive Risk module relies on the client IP address,
and AM lies behind a load balancer or proxy layer,
configure the load balancer or proxy to send the address by using the X-Forwarded-For header,
and configure AM to consume and forward the header as necessary.
For details, refer to Handling HTTP Request Headers.
For detailed information about this module’s configuration properties, refer to Adaptive Risk authentication module properties.
Amster authentication module
This module lets Amster clients authenticate using established SSH keys.
The Amster client signs a JWT (containing subject and expiration claims) using a local private key. The subject claim is
interpreted as the username of the principal. AM verifies the signature, using the list of public keys in its
authorized keys file, and finding a key that matches the JWT’s key identifier claim. If the entry in the authorized keys
file contains a from parameter, only connections that originate from the qualifying host are permitted.
For detailed information about this module’s configuration properties, refer to Amster authentication module properties.
Anonymous authentication module
This module lets you configure and track anonymous users, who can log in to your application or web site without login credentials. Typically, you would provide these users with very limited access, for example, an anonymous user may have access to public downloads on your site. When the user attempts to access resources that require more protection, the module can force further authentication for those resources.
For detailed information about this module’s configuration properties, refer to Anonymous authentication module properties.
Certificate authentication module
X.509 digital certificates can enable secure authentication without the need for usernames and passwords or other credentials. Certificate authentication can be used to manage authentication by applications. If all certificates are signed by a recognized Certificate Authority (CA), then you might not need additional configuration. If you need to look up public keys of AM clients, this module can also look up public keys in an LDAP directory server.
When you store certificates and certificate revocation lists (CRL) in an LDAP directory service, you must configure:
-
How to access the directory service.
-
How to look up the certificates and CRLs, based on the fields in the certificates that AM clients present to authenticate.
Access to the LDAP server and how to search for users is similar to LDAP module configuration
as in LDAP authentication module.
The primary difference is that unlike LDAP configuration,
AM retrieves the user identifier from a field in the certificate that the client application presents,
then uses that identifier to search for the LDAP directory entry that holds the certificate,
which should match the certificate presented.
For example, if the Subject field of a typical certificate has a DN C=FR, O=Example Corp, CN=Barbara Jensen,
and Barbara Jensen’s entry in the directory has cn=Barbara Jensen,
then you can use CN=Barbara Jensen from the Subject DN
to search for the entry with cn=Barbara Jensen in the directory.
You can find more information on configuring certificate authentication in How do I configure certificate-based authentication in PingAM? and How do I troubleshoot certificate-based authentication issues in PingAM?
Learn more about this module’s configuration properties in Certificate authentication module properties.
Data Store authentication module
The Data Store authentication module allows a login using the identity repository of the realm to authenticate users. The Data Store module removes the requirement to write an authentication plugin module, load, and then configure the authentication module if you need to authenticate against the same data store repository. Additionally, you do not need to write a custom authentication module where flat file authentication is needed for the corresponding repository in that realm.
The Data Store module is generic. It does not implement data store-specific capabilities, such as the password policy and password reset features provided by LDAP modules. Therefore, the Data Store module returns failure when such capabilities are invoked.
For detailed information about this module’s configuration properties, refer to Data Store authentication module properties.
Device ID (Match) authentication module
The Device ID (Match) module provides device fingerprinting functionality for risk-based authentication. The Device ID (Match) module collects the unique characteristics of a remote user’s computing device and compares them to characteristics on a saved device profile. The module computes any variances between the collected characteristics to those stored on the saved device profile and assigns penalty points for each difference.
For detailed information about this module’s configuration properties, refer to Device ID (Match) authentication module properties.
In general, you can configure and gather the following device characteristics:
-
User agents associated with the configuration of a web browser
-
Installed fonts
-
Plugins installed for the web browser
-
Resolution and color depth associated with a display
-
Timezone or geolocation of a device
For example, when a user who typically authenticates to AM using Firefox and then logs on using Chrome, the Device ID (Match) module notes the difference and assigns penalty points to this change in behavior. If the module detects additional differences in behavior, such as browser fonts, geolocation, and so forth, then additional points are assessed and calculated.
If the total number of penalty points exceeds a pre-configured threshold value, the Device ID (Match) module fails and control is determined by how you configured your authentication chain. If you include the HOTP module in your authentication chain, and if the Device ID (Match) module fails after the maximum number of penalty points have been exceeded, then the authentication chain issues a HOTP request to the user, requiring the user to identify themselves using two-factor authentication.
|
By default, the maximum penalty points is set to 0, which you can adjust in the server-side script. |
The Device ID (Match) module comes pre-configured with default client-side and server-side JavaScript code, supplying the logic necessary to fingerprint the user agent and computer. Scripting allows you to customize the code, providing more control over the device fingerprint elements that you would like to collect. While AM scripting supports both the JavaScript (default) and Groovy languages, only server-side scripts can be written in either language. The client-side scripts must be written in the JavaScript language.
|
The Device ID (Match) module’s default JavaScript client-side and server-side scripts are fully functional. If you change the client-side script, you must also make a corresponding change to the server-side script. For a safer option, if you want to change the behavior of the module, you can make a copy of the scripts, customize the behavior, and update the Device ID (Match) modules to use the new scripts. |
The Device ID (Match) module does not stand on its own within an authentication chain and requires additional modules. For example, you can have any module that identifies the user (for example, DataStore, Active Directory or others), Device ID (Match), any module that provides two-factor authentication, for example the ForgeRock Authenticator (OATH) or ForgeRock Authenticator (Push) authentication modules, and Device ID (Save) within your authentication chain.
As an example, you can configure the following modules with the specified criteria:
- DataStore - Requisite
-
The Device ID (Match) module requires user authentication information to validate the username. You can also use other modules that identify the username, such as LDAP, Active Directory, or RADIUS.
- Device ID (Match) - Sufficient
-
The Device ID (Match) runs the client-side script, which invokes the device fingerprint collectors, captures the data, and converts it into a JSON string. It then auto-submits the data in a JSP page to the server-side scripting engine.
The server-side script calculates the penalty points based on differences between the client device and stored device profile, and whether the client device successfully "matches" the stored profile. If a match is successful, AM determines that the client’s device has the required attributes for a successful authentication.
If the device does not have a match, then the module fails and falls through to the HOTP module for further processing.
- HOTP - Requisite
-
If the user’s device does not match a stored profile, AM presents the user with a HMAC One-Time Password (HOTP) screen either by SMS or email, prompting the user to enter a password.
You can also use any other module that provides two-factor authentication.
After the HOTP has successfully validated the user, the Device ID (Save) module gathers additional data from the user. For specific information about the HOTP module, refer to HOTP authentication module.
- Device ID (Save) - Required
-
The Device ID (Save) module provides configuration options to enable an auto-save feature on the device profile as well as set a maximum number of stored device profiles on the user entry or record. Once the maximum number of stored device profiles is reached, AM deletes the old data from the user record as new ones are added. User records could thus contain both old and new device profiles.
If the auto-save feature is not enabled, AM presents the user with a screen to save the new device profile.
The module also takes the device print and creates a JSON object that includes the ID, name, last selected date, selection counter, and device print. For specific information about the Device ID (Save) module, refer to Device ID (Save) module.
If a user has multiple device profiles, the profile that is the closest match to the current client details is used for the comparison result.
Configure the Device ID (Match) authentication module
-
In the AM admin UI, go to Realms > Realm Name > Authentication > Modules.
-
Click Add Module.
-
In the Module Name box, enter
Device-ID-Match. -
In the Type box, select
Device Id (Match), and click Create. -
Save your changes.
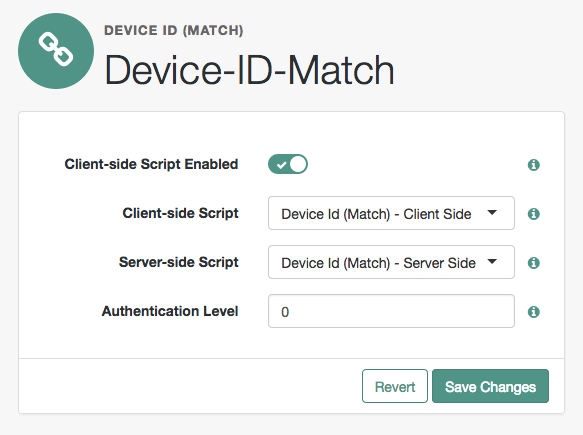 Figure 11. Device ID (Match) Module
Figure 11. Device ID (Match) Module
-
-
To make adjustments to the default scripts, click the Scripts drop-down list, and click Device Id (Match) - Client Side.
-
To make corresponding changes to the server-side script, click the Scripts drop-down list, and click
Device Id (Match) - Server Side.For more information, refer to Manage scripts (UI).
Configure an authentication chain with a Device ID (Match) authentication module
-
In the AM admin UI, go to Realms > Realm Name > Authentication > Chains.
-
On the Authentication Chains page, do the following steps:
-
Click Add Chain. In the Chain Name box, enter a descriptive label for your authentication chain, and click Create.
-
Click Add Module.
-
On the New Module dialog, select the authentication module, select the criteria, and click OK to save your changes. Repeat the last two steps to enter each module to your chain.
For example, you can enter the following modules and criteria:
Device ID Chain Module Criteria DataStore
REQUISITE
Device-ID-Match
SUFFICIENT
HOTP
REQUISITE
Device-ID-Save
REQUIRED
It is assumed that you have added the Device Id (Match) and Device Id (Save) modules. If you have not added these modules, refer to Configure the Device ID (Match) authentication module and To Configure the Device ID (Save) authentication module.
-
-
Review your authentication chain, and save your changes.
What the user sees during authentication
When the user logs on to the AM admin UI, AM determines if the user’s device differs from that of the stored profile. If the differences exceed the maximum number of penalty points or a device profile has not yet been stored, AM sends an "Enter OTP" page, requiring the user to enter a one-time password, which is sent to the user via email or SMS. The user also has the option to request a one-time password.
Next, because the Device ID (Save) module is present, AM presents the user with a "Add to Trusted Devices?" page, asking if the user wants to add the device to the list of trusted device profiles. If the user clicks "Yes", AM prompts the user to enter a descriptive name for the trusted device.
Next, AM presents the user with the User Profile page, where the user can click the Dashboard link at top to access the My Applications and Authentication Devices page. Once on the Dashboard, the user can view the list of trusted devices or remove the device by clicking the Delete Device link.
Device ID (Save) module
The Device ID (Save) module saves a user’s device profile. The module can save the profile upon request, requiring the user to provide a name for the device and explicitly save it or it can save the profile automatically. If a user has multiple device profiles, the profile that is the closest match to the current client details is used for the comparison result.
For detailed information about this module’s configuration properties, refer to Device ID (Save) authentication module properties.
Within its configured authentication chain, the Device ID (Save) module also takes the device print and creates a JSON object that consists of the ID, name, last selected date, selection counter, and device print itself.
To Configure the Device ID (Save) authentication module
-
In the AM admin UI, go to Realms > Realm Name, > Authentication > Modules.
-
To add the Device ID (Save) module, click Add Module.
-
In the Module Name box, enter
Device-ID-Save. -
In the Type box, select
Device Id (Save), and click Create. -
To configure the Device-Id (Save) module, do the following:
-
Click the Automatically store new profiles checkbox. If this box is left unchecked, the user will be prompted to give consent to store new profiles.
-
In the Maximum stored profile quantity box, enter the max number of stored profiles. Any profile that exceeds this number will not be stored.
-
In the Authentication Level box, enter a number corresponding to the authentication level of the module.
-
Click Save Changes.
 Figure 12. Device ID (Save) Module
Figure 12. Device ID (Save) Module
-
Federation authentication module
The Federation authentication module is used by a service provider to create a user session after validating single sign-on protocol messages. This authentication module is used by the SAML, SAMLv2, ID-FF, and WS-Federation protocols.
For detailed information about this module’s configuration properties, refer to Federation authentication module properties.
|
When configuring AM to use WS-Federation, add the hosted and remote entity SP/RP
token issuer endpoint URLs to the hosted IDP’s You can find information on implementing authentication using WS-Federation in How do I configure PingAM as an Identity Provider for Microsoft Office 365 and Azure using WS-Federation? in the Knowledge Base. |
ForgeRock Authenticator (OATH) authentication module
The ForgeRock Authenticator (OATH) module provides a more secure method for users to access their accounts with the help of a device such as a mobile phone.
For detailed information about this module’s configuration properties, refer to ForgeRock Authenticator (OATH) authentication module properties.
|
AM provides two authentication modules that support OATH:
We recommend using the ForgeRock Authenticator (OATH) authentication module when possible. Also, the ForgeRock Authenticator (OATH), HOTP, and OATH authentication modules all support HOTP passwords, but the way that users obtain passwords differs. Refer to Comparing the ForgeRock Authenticator (OATH) to the HOTP authentication module for more information. |
ForgeRock Authenticator (Push) authentication module
The ForgeRock Authenticator (Push) module provides a way to send push notification messages to a device, such as a mobile phone, enabling multi-factor authentication. For detailed information about multi-factor authentication with the ForgeRock Authenticator (Push) module in AM, refer to Multi-factor authentication.
For detailed information about this module’s configuration properties, refer to ForgeRock Authenticator (Push) authentication module properties.
ForgeRock Authenticator (Push) Registration authentication module
The ForgeRock Authenticator (Push) Registration module provides a way to register a device such as a mobile phone for multi-factor authentication. For detailed information about multi-factor authentication with the ForgeRock Authenticator (Push) module in AM, refer to Manage devices for MFA.
For detailed information about this module’s configuration properties, refer to ForgeRock Authenticator (Push) Registration authentication module properties.
HOTP authentication module
The HOTP authentication module works with an authentication chain with any module that stores the username attribute.
The module uses the username from the sharedState set by the previous module in the chain
and retrieves the user’s email address or telephone number to send a one-time password to the user.
The user then enters the password on a Login page and completes the authentication process if successful.
For example, to set up HOTP in an authentication chain,
you can configure the Data Store module (or any module that stores the user’s username)
as the requisite first module, and the HOTP module as the second requisite module.
When authentication succeeds against the Data Store module,
the HOTP module retrieves the Email Address and Telephone Number attributes from the data store
based on the username value.
For the HOTP module to use either attribute, the Email Address must contain a valid email address,
or the Telephone Number must contain a valid SMS telephone number.
You can set the HOTP module to generate a password when users begin logging into the system. You can also set up mobile phone, mobile carrier, and email attributes for tighter controls over where the messages are generated and what provider the messages go through to reach the user.
For detailed information about this module’s configuration properties, refer to HOTP authentication module properties.
|
The ForgeRock Authenticator (OATH), HOTP, and OATH authentication modules all support HOTP passwords, but the way that users obtain passwords differs. Refer to Comparing the ForgeRock Authenticator (OATH) to the HOTP authentication module for more information. |
HTTP Basic authentication module
HTTP basic authentication takes a user name and password from HTTP authentication and tries authentication against the backend module in AM, depending on what you configure as the Backend module Name.
For detailed information about this module’s configuration properties, refer to HTTP Basic authentication module properties.
JDBC authentication module
The Java Database Connectivity (JDBC) module lets AM connect to a database, such as MySQL or Oracle DB to authenticate users.
For detailed information about this module’s configuration properties, refer to JDBC authentication module properties.
LDAP authentication module
AM connects to directory servers using Lightweight Directory Access Protocol (LDAP). To build an easy-to-manage, high-performance, pure Java directory service, try PingDS.
For detailed information about this module’s configuration properties, refer to LDAP authentication module properties.
Legacy OAuth 2.0/OpenID Connect authentication module
|
This authentication module is labeled as legacy. Use the replacements instead, as described in Social authentication modules. |
The Legacy OAuth 2.0/OpenID Connect authentication module lets AM authenticate clients of OAuth resource servers. References in this section are to RFC 6749, The OAuth 2.0 Authorization Framework.
If the module is configured to create an account if none exists, then you must provide valid SMTP settings. As part of account creation, the OAuth 2.0/OpenID Connect client authentication module sends the resource owner an email with an account activation code. To send an email, AM uses the SMTP settings from the configuration for the OAuth 2.0/OpenID Connect authentication module.
For detailed information about this module’s configuration properties, refer to Legacy OAuth 2.0/OpenID Connect authentication module properties.
MSISDN authentication module
The Mobile Station Integrated Services Digital Network (MSISDN) authentication module enables non-interactive authentication using a mobile subscriber ISDN associated with a terminal, such as a mobile phone. The module checks the subscriber ISDN against the value found on a user’s entry in an LDAP directory service.
For detailed information about this module’s configuration properties, refer to MSISDN authentication module properties.
OATH authentication module
The Open Authentication (OATH) module provides a more secure method for users to access their accounts with the help of a device, such as their mobile phone or Yubikey. Users can log into AM and update their information more securely from a one-time password (OTP) displayed on their device. The OATH module includes the OATH standard protocols (RFC 4226 and RFC 6238). The OATH module has several enhancements to the HMAC One-Time Password (HOTP) authentication module, but does not replace the original module for those already using HOTP prior to the 10.1.0 release. The OATH module includes HOTP authentication and Time-Based One-Time Password (TOTP) authentication. Both types of authentication require an OATH compliant device that can provide the OTP.
HOTP authentication generates the OTP every time the user requests a new OTP on their device. The device tracks the number of times the user requests a new OTP, called the counter. The OTP displays for a period of time you designate in the setup, so the user may be further in the counter on their device than on their account. AM resynchronizes the counter when the user finally logs in. To accommodate this, you set the number of passwords a user can generate before their device cannot be resynchronized. For example, if you set the number of HOTP Window Size to 50 and someone presses the button 30 on the user’s device to generate a new OTP, the counter in AM review the OTPs until it reaches the OTP entered by the user. If someone presses the button 51 times, you will need to reset the counter to match the number on the device’s counter before the user can log in to AM. HOTP authentication does not check earlier passwords, so if the user attempts to reset the counter on their device, they will not be able to log in until you reset the counter in AM to match their device. Refer to Reset registered devices over REST for more information.
TOTP authentication constantly generates a new OTP based on a time interval you specify. The device tracks the last two passwords generated and the current password. The Last Login Time monitors the time when a user logs in to make sure that user is not logged in several times within the present time period. Once a user logs into AM, they must wait for the time it takes TOTP to generate the next two passwords and display them. This prevents others from being able to access the user’s account using the OTP they entered. The user’s account can be accessed again after the generation of the third new OTP is generated and displayed on their device. For this reason, the TOTP Time-Step Interval should not be so long as to lock users out, with a recommended time of 30 seconds.
An authentication chain can be created to generate an OTP from HOTP or TOTP.
For detailed information about this module’s configuration properties, refer to OATH authentication module properties.
|
AM provides two authentication modules that support OATH:
We recommend using the ForgeRock Authenticator (OATH) authentication module when possible. Also, the ForgeRock Authenticator (OATH), HOTP, and OATH authentication modules all support HOTP passwords, but the way that users obtain passwords differs. Refer to Comparing the ForgeRock Authenticator (OATH) to the HOTP authentication module for more information. |
OpenID Connect id_token bearer module
The OpenID Connect id_token bearer module lets AM rely on an OpenID Connect 1.0 provider’s ID Token to authenticate an end user.
|
This module validates an OpenID Connect ID token and matches it with a user profile. You should not use this module if you want AM to act as a client in the full OpenID Connect authentication flow. To provision AM as an OpenID Connect client, you should instead configure an OAuth 2.0 or OpenID Connect social auth module. For more information, refer to Social authentication. |
The OpenID Connect id_token bearer module expects an OpenID Connect ID Token in an HTTP request header. It validates the ID Token, and if successful, looks up the AM user profile corresponding to the end user for whom the ID Token was issued. Assuming the ID Token is valid, and the profile is found, the module authenticates the AM user.
You configure the OpenID Connect id_token bearer module to specify how AM gets the information needed to validate the ID Token, which request header contains the ID Token, the issuer identifier for the provider who issued the ID Token, and how to map the ID Token claims to an AM user profile.
OpenID Connect id_token bearer example
The OpenID Connect id_token bearer module configuration
must match the claims returned in the id_token JWT used to authenticate.
Before configuring the module, use an OpenID Connect client to obtain an id_token.
Decode the id_token value to see the claims in the middle portion of the JWT.
The claims in the decoded id_token look something like the following example:
{
"at_hash":"GZofHqaewBJ2hRjkKiT8Ew",
"sub":"demo",
"auditTrackingId":"0d836a8d-af4c-4b33-a3a2-bf06cd590b91-3937",
"iss":"https://openam.example.com:8443/openam/oauth2",
"tokenName":"id_token",
"aud":"myClientID",
"azp":"myClientID",
"auth_time":1538675226,
"name":"demo",
"realm":"/",
"exp":1538733152,
"tokenType":"JWTToken",
"family_name":"demo",
"iat":1538675226,
"jti":"bb18a404-f08c-446e-8e01-8b70c8d48192"
}The azp, aud, and iss values are literally reused in the module configuration.
The following figure shows an example configuration for this id_token format.
The following example command demonstrates a REST call that authenticates the user using the module:
$ curl \
--request POST \
--header "Content-Type: application/json" \
--header "Accept-API-Version: resource=2.0, protocol=1.0" \
--header "oidc_id_token: eyJ…ifQ.eyJ…In0.BT1…iZA" \
'https://openam.example.com:8443/openam/json/realms/root/realms/alpha/authenticate?authIndexType=module&authIndexValue=OIDC'
{
"tokenId": "nIq…AA*",
"successUrl": "/openam/console",
"realm": "/alpha"
}The id_token value, abbreviated as eyJ…ifQ.eyJ…In0.BT1…iZA,
is the value of the oidc_id_token header in the configuration.
The request targets a module named OIDC as specified by the authIndexType and authIndexValue parameters.
For detailed information about the authentication REST API, refer to Authenticate over REST.
For detailed information about this module’s configuration properties, refer to OpenID Connect id_token bearer authentication module properties.
Persistent Cookie module
The Persistent Cookie module supports the configuration of cookie lifetimes based on requests and a maximum time.
By default, the persistent cookie is called session-jwt.
|
If you enable Secure Cookie (Deployment > Servers > Server Name > Security > Cookie), the Persistent Cookie module only works over HTTPS. |
The module signs and encrypts the JSON Web Token (JWT) that’s inserted as the value of the persistent cookie. The following table shows the relevant secret labels and the default public key and HMAC key aliases:
For information on mapping certificate aliases to secret labels in secret stores, refer to Mapping and Rotating Secrets.
When the Persistent Cookie module enforces the client IP address,
and AM lies behind a load balancer or proxy layer,
configure the load balancer or proxy to send the address by using the X-Forwarded-For header,
and configure AM to consume and forward the header as necessary.
For details, refer to Handling HTTP Request Headers.
The Persistent Cookie module belongs with a second module in an authentication chain. To understand how this works, go to Realms > Realm Name > Authentication > Chains. Create a new chain and add modules, as shown in the figure. The following example shows how a Persistent Cookie module is sufficient. If the persistent cookie does not yet exist, authentication relies on LDAP:
Select the Settings tab and locate settings for the post-authentication processing class.
Set the Class Name to
org.forgerock.openam.authentication.modules.persistentcookie.PersistentCookieAuthModulePostAuthenticationPlugin,
as shown in the following figure:
You should now be able to authenticate automatically, as long as the cookie exists for the associated domain.
|
To configure the Persistent Cookie module globally in the AM admin UI, go to Configure > Authentication, and click Persistent Cookie. |
For detailed information about this module’s configuration properties, refer to Persistent Cookie authentication module properties.
RADIUS authentication module
The Remote Authentication Dial-In User Service (RADIUS) module lets AM authenticate users against RADIUS servers.
For detailed information about this module’s configuration properties, refer to RADIUS authentication module properties.
SAE authentication module
The Secure Attribute Exchange (SAE) module lets AM authenticate a user who has already authenticated with an entity that can vouch for the user to AM, so that AM creates a session for the user. This module is useful in virtual federation, where an existing entity instructs the local AM instance to use federation protocols to transfer authentication and attribute information to a partner application.
For detailed information about this module’s configuration properties, refer to SAE authentication module properties.
SAML2 authentication module
The SAML2 authentication module lets administrators integrate SAML v2.0 single sign-on and single logout into an AM authentication chain.
You use the SAML2 authentication module when deploying SAML v2.0 single sign-on in integrated mode. In addition to configuring SAML2 authentication module properties, integrated mode deployment requires that you make several changes to service provider configurations. Before attempting to configure a SAML2 authentication module instance, review Implement SSO in integrated mode (chains) and make sure you have made all required changes to your service provider configuration.
For detailed information about this module’s configuration properties, refer to SAML2 authentication module properties.
Scripted authentication module
A scripted authentication module runs scripts to authenticate a user. The configuration for the module can hold two scripts, one to include in the web page run on the client user-agent, and another to run in AM on the server side.
The client-side script is intended to retrieve data from the user-agent. This must be in a language the user-agent can run, such as JavaScript, even if the server-side script is written in Groovy.
The server-side script is intended to handle authentication.
Scripts are stored not as files, but instead as AM configuration data. This makes it easy to update a script on one AM server, and then to allow replication to copy it to other servers. You can manage the scripts through the AM admin UI, where you can write them in the text boxes provided or upload them from files.
You can also upload scripts and associate them with a scripted authentication module
by using the ssoadm command.
The following example shows how to upload a server-side script from a file, create a scripted authentication module, and then associate the uploaded script with the new module.
#
# Upload a server-side script from a script file, myscript.groovy.
#
ssoadm create-sub-cfg \
--realm / \
--adminid uid=amAdmin,ou=People,dc=openam,dc=forgerock,dc=org \
--password-file /tmp/pwd.txt \
--servicename ScriptingService \
--subconfigname scriptConfigurations/scriptConfiguration \
--subconfigid myScriptId \
--attributevalues \
"name=My Scripted Auth Module Script" \
"script-file=myscript.groovy" \
"context=AUTHENTICATION_SERVER_SIDE" \
"language=GROOVY"
#
# Create a scripted authentication module, myScriptedAuthModule.
#
ssoadm create-auth-instance \
--realm / \
--adminid uid=amAdmin,ou=People,dc=openam,dc=forgerock,dc=org \
--password-file /tmp/pwd.txt \
--authtype Scripted \
--name myScriptedAuthModule
#
# Associate the script with the auth module, and disable client-side scripts.
#
ssoadm update-auth-instance \
--realm / \
--adminid uid=amAdmin,ou=People,dc=openam,dc=forgerock,dc=org \
--password-file /tmp/pwd.txt \
--name myScriptedAuthModule \
--attributevalues \
"iplanet-am-auth-scripted-server-script=myScriptId" \
"iplanet-am-auth-scripted-client-script-enabled=false"If you have multiple separate sets of client-side and server-side scripts, then configure multiple modules, one for each set of scripts.
For details on writing authentication module scripts, refer to Using server-side authentication Scripts in authentication modules.
For detailed information about this module’s configuration properties, refer to Scripted authentication module properties.
SecurID Authentication Module
The SecurID module lets AM authenticate users with RSA Authentication Manager software and RSA SecurID authenticators.
|
To use the SecurID authentication module,
you must first build an AM |
For detailed information about this module’s configuration properties, see SecurID Authentication Module Properties.
Social authentication modules
The social authentication modules let AM authenticate clients of OAuth 2.0 or OpenID Connect 1.0 resource servers. References in this section are to RFC 6749, The OAuth 2.0 Authorization Framework.
AM provides pre-configured authentication modules for the following social identity providers:
-
Instagram
-
VKontakte
-
WeChat
AM provides two authentication modules for the WeChat social identity provider. The Social Auth WeChat authentication module implements a login flow that requires the user to scan an on-screen QR code with the WeChat app. The Social Auth WeChat Mobile authentication module implements an alternative login flow for users authenticating on their mobile device, who would not be able to scan a QR code displayed on the mobile device’s screen.
AM provides two generic authentication modules, one for OAuth 2.0, and another for OpenID Connect 1.0, for authenticating users of standards-compliant social identity providers, for example Facebook and Google.
If the social authentication module is configured to create an account when none exists, then you must provide valid SMTP settings in the Email tab. The social identity provider must also provide the user’s email address. As part of account creation, the social authentication module sends the resource owner an email with an account activation code. To send email, AM uses the SMTP settings from the Email tab of the configuration of the social authentication module.
For detailed information about the social authentication module’s configuration properties, refer to the following sections:
Windows Desktop SSO authentication module
The Windows Desktop SSO module uses Kerberos authentication. The user presents a Kerberos token to AM through the Simple and Protected GSS-API Negotiation Mechanism (SPNEGO) protocol. The Windows Desktop SSO authentication module enables desktop single sign-on such that a user who has already authenticated with a Kerberos Key Distribution Center can authenticate to AM without having to provide the login information again. Users might need to set up Integrated Windows Authentication in Microsoft Edge to benefit from single sign-on when logged on to a Windows desktop.
For detailed information about this module’s configuration properties, refer to Windows Desktop SSO authentication module properties.
|
If you are using the Windows Desktop SSO module as part of an authentication chain and Windows Desktop SSO fails,
you may no longer be able to |
Scripted module API (deprecated)
In addition to the functionality provided by the HTTP client and the logging API, authentication modules that use server-side scripts can access the authentication state of a request, information about the session, and the login request itself.
| Authentication modules and chains are deprecated and will be removed in a future release. Convert existing authentication journeys that use modules and chains to authentication nodes and trees when possible. |
Client-side scripts in modules gather data into a string that’s returned to AM in a self-submitting form.
If you’re developing server-side scripts, it can be useful to increase the debug level
of the org.apache.http.wire and org.apache.http.headers appenders to Message.
By default, these appenders are always set to the Warning level unless logging is disabled.
Learn more in the org.forgerock.allow.http.client.debug advanced server property.
Authentication state
AM passes authState and sharedState objects to server-side scripts
in order for the scripts to access authentication state.
Server-side scripts can access the current authentication state through the authState object.
The authState value is SUCCESS if the authentication is currently successful,
or FAILED if authentication has failed.
Server-side scripts must set a value for authState before completing.
If an earlier authentication module in the authentication chain has set the login name of the user,
server-side scripts can access the login name through username.
The following authentication modules set the login name of the user:
-
Anonymous
-
Certificate
-
Data Store
-
Federation
-
HTTP Basic
-
JDBC
-
LDAP
-
Membership
-
RADIUS
-
SecurID
-
Windows Desktop SSO
Profile data
Server-side authentication scripts can access profile data through the methods of the idRepository object.
| Method | Parameters | Return Type | Description |
|---|---|---|---|
|
|
|
Return the values of the named attribute for the named user. |
|
|
|
Set the named attribute as specified by the attribute value for the named user, and persist the result in the user’s profile. |
|
|
|
Add an attribute value to the list of attribute values associated with the attribute name for a particular user. |
Client-side script output data
Client-side scripts add data they gather into a string object named clientScriptOutputData.
Client-side scripts then cause the user-agent automatically to return the data to AM
by HTTP POST of a self-submitting form.
Request data
Server-side scripts can access the login request by using the methods of the requestData object.
The following table lists the methods of the requestData object.
Note that this object differs from the client-side requestData object
and contains information about the original authentication request made by the user.
| Method | Parameters | Return Type | Description |
|---|---|---|---|
|
|
|
Return the String value of the named request header, or |
|
|
|
Return the array of String values of the named request header, or |
|
|
|
Return the String value of the named request parameter, or |
|
|
|
Return the array of String values of the named request parameter, or |
Redirect users after authentication failure
Server-side scripts can redirect the user to a specific URL in case of authentication failure
by adding a gotoOnFailureUrl property to the chain’s shared state.
When the script reaches a FAILED authentication state (defined by the authState variable),
it checks if the gotoOnFailureUrl property is stored in the shared state.
If so, the script redirects the user to the specified URL.
You can redirect the user to a page relative to AM’s URL, or to an absolute URL:
-
Relative URL
-
Absolute URL
...
sharedState.put("gotoOnFailureUrl","/am/XUI/?service=testChain#failedLogin");
authState = FAILED;
......
sharedState.put("gotoOnFailureUrl","http://www.example.com");
authState = FAILED;
...Note that the failure URL relative to AM’s domain includes the authentication service; this is so that when the user clicks on the link to log in again, AM constructs the login page with the appropriate service instead of with the default one for the realm.
When redirecting the user to an absolute URL different from AM’s scheme, FQDN, and port, you must configure the URL in the validation service of the realm; otherwise, AM ignores the redirect.