REST API protection from DoS and DDoS
Flow control protects REST API servers from DoS and DDoS attacks using four control variables, which are independently configured. By default, no flow control is enabled.
The following table shows the control variables that are configured once in every API JSON file.
| Variable | Description |
|---|---|
|
Maximum requests per time-period from a single client IP to a specific REST API. Time can be in seconds, minutes, or hours. |
|
When The default value is |
The following table shows the control variables that are configured for each server in every API JSON file.
| Variable | Description |
|---|---|
|
Maximum number of concurrent connections to a specific REST API on a server. Prevents aggregate connections from one or a cluster of ASE nodes from overloading a REST API running on a specific server. |
|
Maximum requests per time period to the REST API running on the specified server. Prevents the aggregate request rate from one or a cluster of ASE nodes from overloading a REST API running on a specific server. Time can be in seconds, minutes, or hours |
The following diagram shows the effect of the parameters on traffic flow through ASE to backend servers. In the diagram, client-side flow control is managed by client_spike_threshold and server-side flow control is regulated by a combination of server_spike_threshold and server_connection_quota.
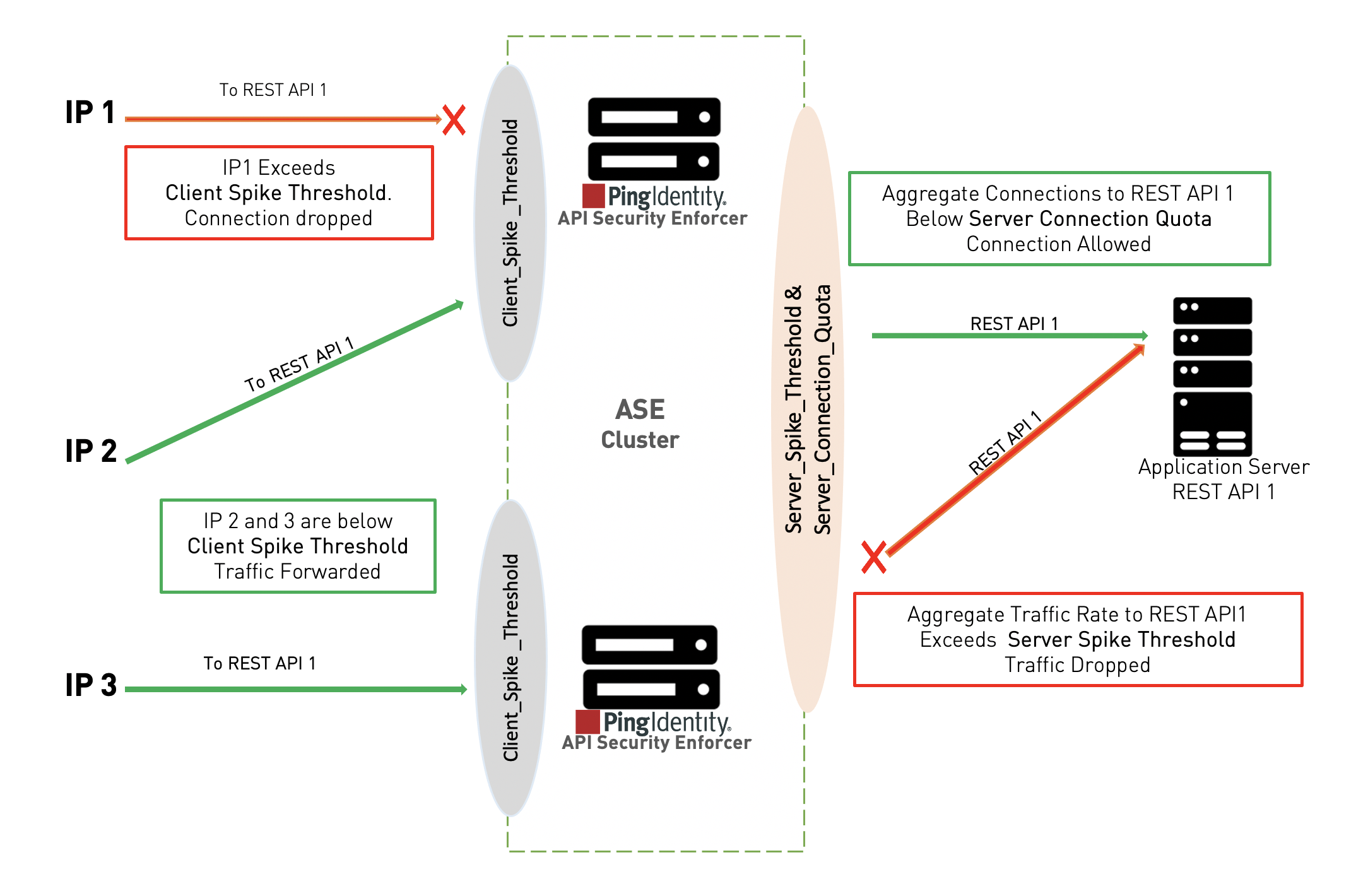
Client flow control monitors incoming traffic from each client connection and drops the session when traffic limits are exceeded. The diagram shows the following client scenarios:
-
IP1 sending request volumes that exceed the
client_spike_thresholdvalue. ASE 1 sends an error message and terminates the session to stop the attack. -
IP2 and IP3 sending request traffic that stays below the
client_spike_thresholdvalue. Requests are passed to the backend API servers.
Server-side flow control manages traffic volumes and session count for an API on an application server. server_connection_quota sets the maximum number of concurrent connections that can be established to each API on a server. server_spike_threshold controls the aggregate traffic rate to an API on a server.
The concurrent connections and request rate consist of the aggregate traffic from all ASE nodes forwarding traffic to an API on a server. The diagram shows two server scenarios:
-
A new connection request from ASE 1 is allowed because it’s within the
server_connection_quotathreshold. -
ASE 2 detects that the combined traffic rate from ASE 1 and ASE 2 will exceed the
server_spike_thresholdfor REST API 1. It drops IP 3 traffic and sends an error message to the client.
The following is an example for an application server that explains the scenarios depicted by the previous diagram.
| Variable | Configured value |
|---|---|
|
50,000 requests per second per IP |
|
30,0000 requests per second per server |
|
20,000 concurrent connections per server |
|
|
-
Client flow control permits a maximum of 50,000 requests per second from an individual IP. If IP 1, 2, or 3 exceeds the 50,000 per second limit, ASE drops the client session. Otherwise, all requests are passed to the backend servers.
-
Server flow control allows 30,000 requests per second to REST API 1 on the application server. If the sum of requests per second from the ASE cluster nodes (ASE 1 + ASE 2 request rate) to REST API1 exceeds 30,000/second, then traffic is dropped from the client causing aggregate traffic to exceed the maximum request rate. Otherwise, ASE 1 and ASE 2 forward all traffic.
-
Server flow control allows 20,000 concurrent connections to REST API1 on the application server. If the sum of connections from the ASE cluster nodes (ASE 1 + ASE 2 connection count) to REST API1 exceeds 20,000, then ASE will queue the request for a time because
server_connection_queuingis enabled. If queuing is not enabled, then the request is dropped.
| Parameter | Notes |
|---|---|
|
Maximum request rate from a client to an API |
|
Maximum aggregate request rate through ASE cluster nodes to an API on a specific server |
|
Maximum number of concurrent sessions from ASE cluster nodes to an API on a specific server |
|
You can also configure server connection quota and server spike threshold separately for each backend server. |
JSON configuration for REST API flow control
ASE flow control is configured separately for each API using the API JSON file. The following example shows the flow control related definitions in an API JSON file.
{
"api_metadata": {
"protocol": "http",
"flow_control": {
"client_spike_threshold": "0/second",
"server_connection_queueing" : false
},
"servers": [
{
"host": "127.0.0.1",
"port": 8080,
"server_spike_threshold": "100/second",
"server_connection_quota": 20
},
{
"host": "127.0.0.1",
"port": 8081,
"server_spike_threshold": "200/second",
"server_connection_quota": 40
}
]
}
}The flow control section includes definitions that apply globally across the API definition and include client_spike_threshold and server_connection_queueing. Server specific definitions include server_spike_threshold and server_connection_quota, which are configured on each individual server. The default is no flow control with all values set to 0.
You can specify different values for each server for server_connection_quota and server_spike_threshold.
|
If server connection quota is set to 0 for one server, then it must be 0 for all other servers in the API JSON definition. |
Flow control CLI for REST API
You can use the ASE CLI to update flow control parameters.
- Update client spike threshold
-
Enter the following command to update the client spike threshold, for example,
update_client_spike_threshold shop_api 5000/second.
update_client_spike_threshold {api_id} {+ve digit/(second|minute|hour)}
- Update server spike threshold
-
Enter the following command to update the server spike threshold, for example,
update_server_spike_threshold shop_api 5000/second.
update_server_spike_threshold {api_id} {host:port} {+ve digit/(second|minute|hour)}
- Update server connection quota
-
Enter the following command to update the server connection quota, for example,
update_server_connection_quota shop_api 5000.
update_server_connection_quota {api_id} {host:port}{+ve digit}
|
API security must be enabled for ASE flow control to work. For more information on enabling API security, see Enable API security. |