AWS API gateway integration
This integration guide discusses the deployment of PingIntelligence for APIs in a sideband configuration with AWS API Gateway through CloudFront.
PingIntelligence for APIs provides a sideband policy that can be installed in CloudFront. The policy uses AWS Lambda functions to pass API metadata to PingIntelligence for detailed API activity reporting and attack detection with optional client blocking.
PingIntelligence for APIs provides an automated tool to deploy a the policy, which is implemented using the AWS Lambda functions. The policy requires AWS CloudFront to be present with all caching disabled. AWS Lambda functions must be initially deployed in the US-East-1 region, and the policy definition is pushed to any region with your API Gateways after the PingIntelligence policy is added.
The PingIntelligence sideband policy requires a CloudFront instance, which can be an existing or new instance.
|
The default AWS Lambda memory is sufficient for up to 1000 QPS. For a larger QPS, contact PingIdentity support. See the aws.properties file for default origin response value. |
The following diagram shows the logical setup of PingIntelligence ASE (API Security Enforcer) and CloudFront.
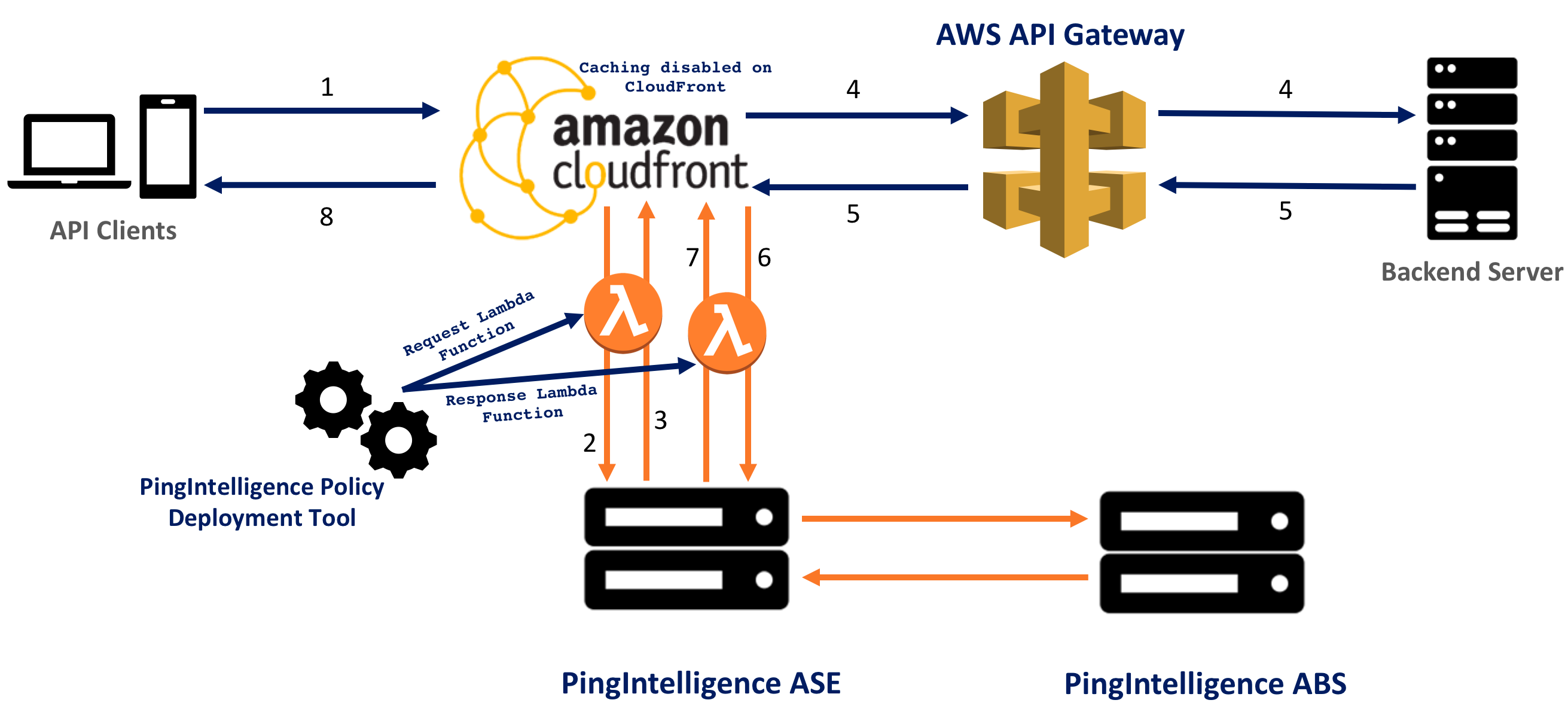
The traffic flow through the CloudFront and PingIntelligence for APIs components is as follows:
-
An incoming API client request destined for the API Gateway arrives at CloudFront.
-
A PingIntelligence AWS Lambda policy makes an API call to send the request metadata to PingIntelligence ASE.
-
ASE checks the request against a registered set of APIs and looks for the origin IP, cookie, OAuth2 token, or API key in the ABS (API Behavioral Security) AI engine generated blacklist. If all checks pass, ASE returns a
200-OKresponse to AWS Lambda. If the checks don’t pass, ASE sends a403response code to AWS Lambda. The request information is also logged by ASE and sent to the ABS AI Engine for processing. -
If CloudFront receives a
200-OKresponse from ASE, it forwards the client request to the backend server. Otherwise, the CloudFront blocks the client when blocking is enabled for the API. -
CloudFront receives the response from the backend server.
-
The Lambda response function makes a second API call to pass the response information to ASE.
-
ASE receives the response information and sends a
200-OKto AWS Lambda. The response information is also logged by ASE and sent to the ABS AI Engine for processing. -
CloudFront sends the response received from the backend server to the client.