Deploying the PingIntelligence policy
Integrate PingAccess with the PingIntelligence components.
About this task
|
We recommend that you increase the default heap size in PingAccess before deploying the PingIntelligence policy for PingAccess 6.x. Refer to the instructions in Modifying the Java heap size for changing the default heap size. For more information, contact Ping Identity support. |
To integrate PingAccess with the PingIntelligence components:
Steps
-
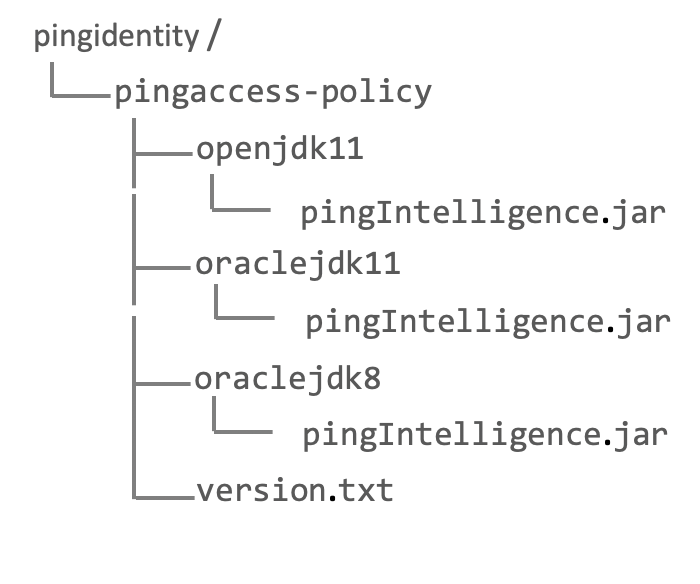
Download the PingIntelligence policy from the Ping Identity download site and unzip it.
The zip file contains three policy files based on the Java Development Kit (JDK) version. Use the policy based on your deployment environment.
-
Copy the
PingIntelligence.jarfile into thelibdirectory inPA_home. -
Restart PingAccess.
-
Sign on to PingAccess.
To support fail-over, a secondary ASE is provisioned. Complete the following steps for both primary and secondary ASEs.
-
Add the primary ASE as a third-party service:
-
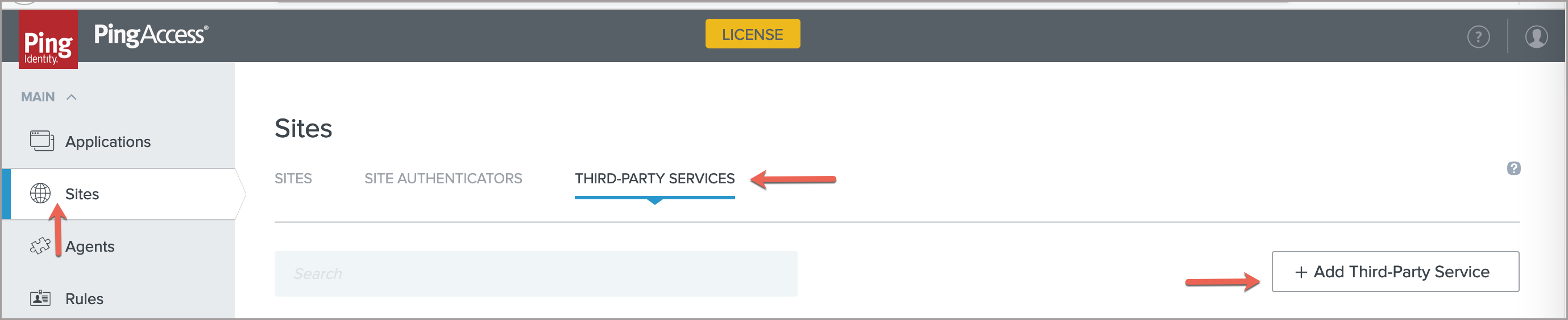
In the left pane, click Sites.
-
Navigate to THIRD-PARTY SERVICES and click Add Third-Party Service to add the Primary ASE.
-
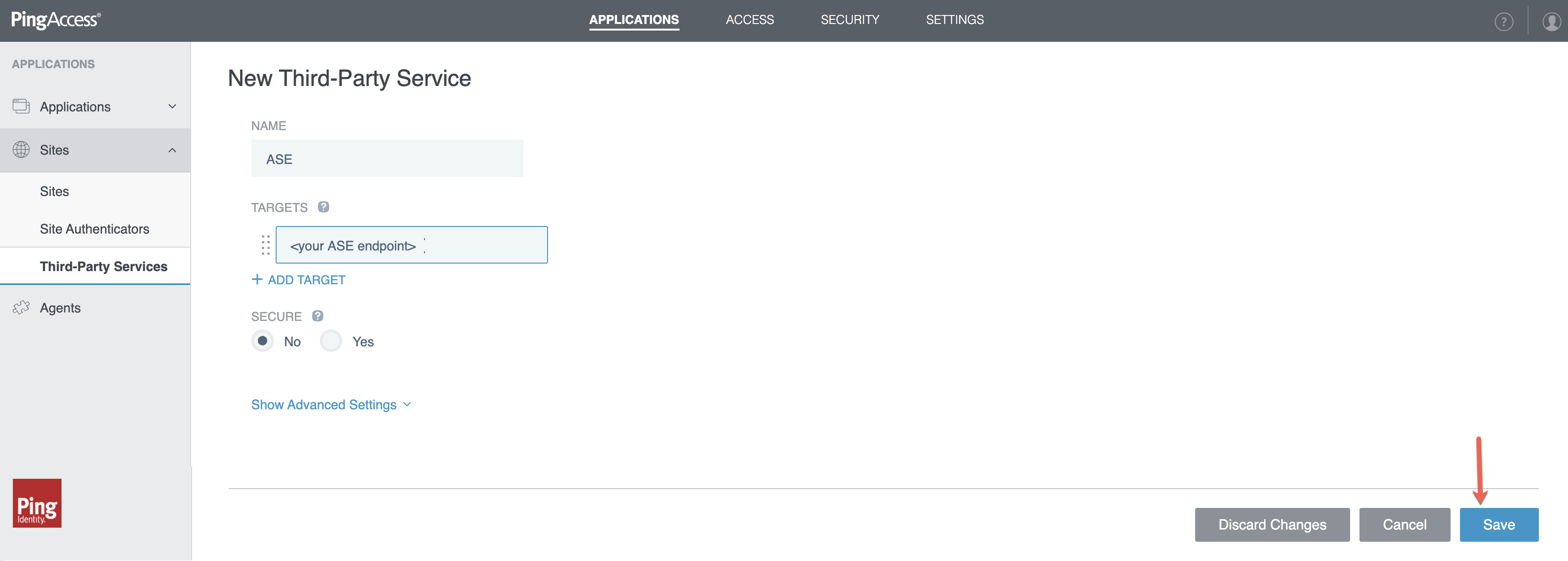
In the New Third-Party Service page, enter a name that identifies the Primary ASE in NAME and enter the endpoint used to reach the Primary ASE inTARGET.
Select options under SECURE to connect PingAccess to PingIntelligence ASE using HTTPS.
-
Click Save.
-
-
Repeat step 5 to add the secondary ASE as a third-party service. Enter the name and endpoint specific to the secondary ASE.
-
Add PingIntelligence sideband rule:
-
In the left pane, click Rules.
-
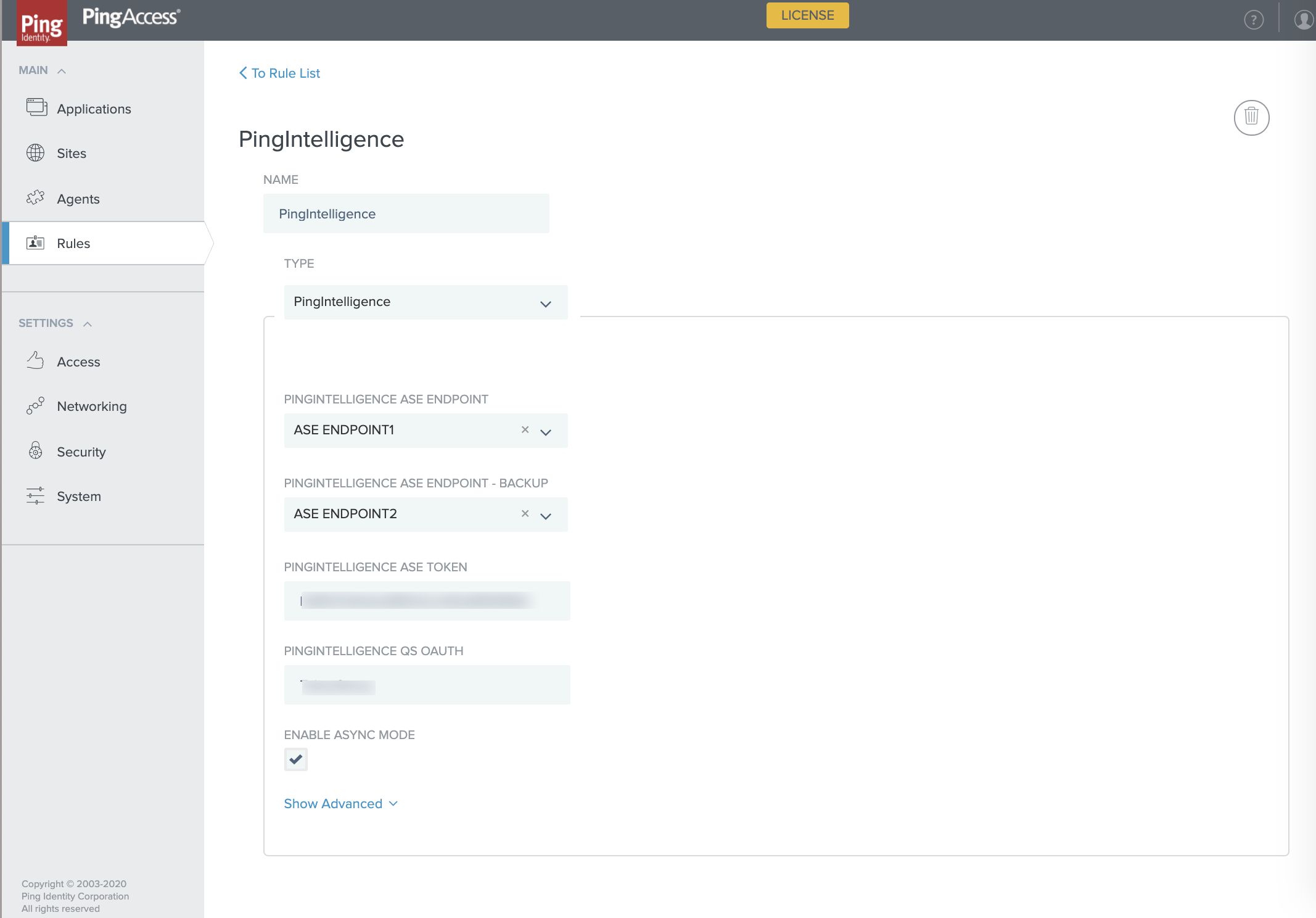
In the new Rule page in the NAME field, enter the name of the rule for PingIntelligence.
-
In the TYPE drop-down list, select PingIntelligence.
This appears in the drop-down list after adding
PingIntelligence.jarinPA_homein step 2.-
Select the ASE endpoint for primary ASE in the PINGINTELLIGENCE ASE ENDPOINT drop-down list.
-
Select the ASE endpoint for S\secondary ASE inPINGINTELLIGENCE ASE ENDPOINT-BACKUP drop-down list.
If the secondary ASE is not installed, you can choose Primary ASE Endpoint in PINGINTELLIGENCE ASE ENDPOINT-BACKUP drop-down list.
-
In the PINGINTELLIGENCE ASE TOKEN field, enter the ASE sideband token that was generated for authentication between PingAccess and ASE.
-
If an OAuth token comes as part of a query string, enter the name of the query string in the PINGINTELLIGENCE QS OAUTH field.
The PingIntelligence policy extracts the OAuth token from the query string configured in PINGINTELLIGENCE QS OAUTH. A new Authorization header-
Authorization: Bearer <OAuth token>is added to the metadata sent to ASE. If there is an existing Authorization header, the token is prepended so that ABS AI engine can analyse it. If the query string has multiple query parameters with the same name, the first parameter is intercepted by the policy. -
Select the ENABLE ASYNC MODE to choose Asynchronous mode between PingAccess and ASE.
The PingIntelligence policy supports both synchronous and asynchronous modes of communication between PingAccess and ASE. By default, the communication mode is synchronous. When the asynchronous mode is enabled, the PingAccess gateway does not wait for a response from ASE and sends the request to backend server. ASE performs attack detection without blocking of attacks in asynchronous mode.
-
-
Apply the rule:
-
Edit the existing application.
-
In the edit application page, click API Policy.
-
Under Available Rules, click the + button for the PingIntelligence rule.
Result:
After clicking the
 button, the PingIntelligence rule moves under the API APPLICATION POLICY as shown in the screen capture below.
button, the PingIntelligence rule moves under the API APPLICATION POLICY as shown in the screen capture below.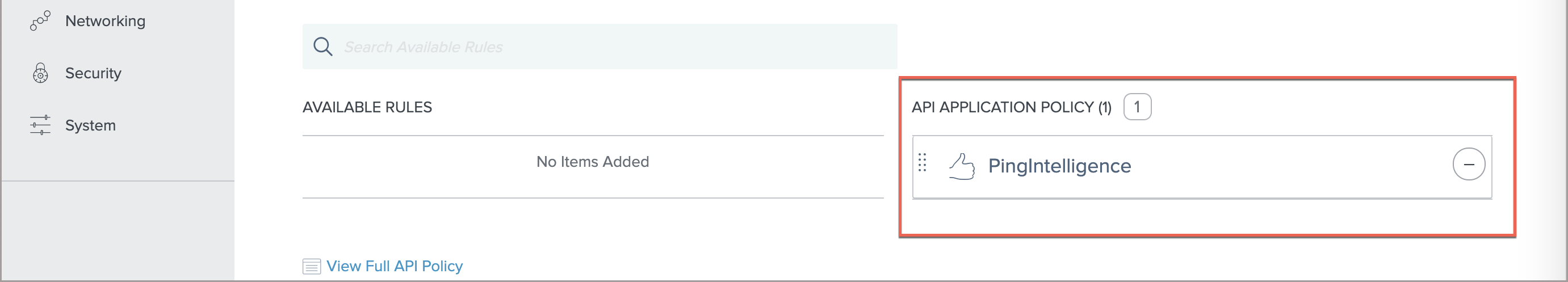
-
Click Save to save the rule.
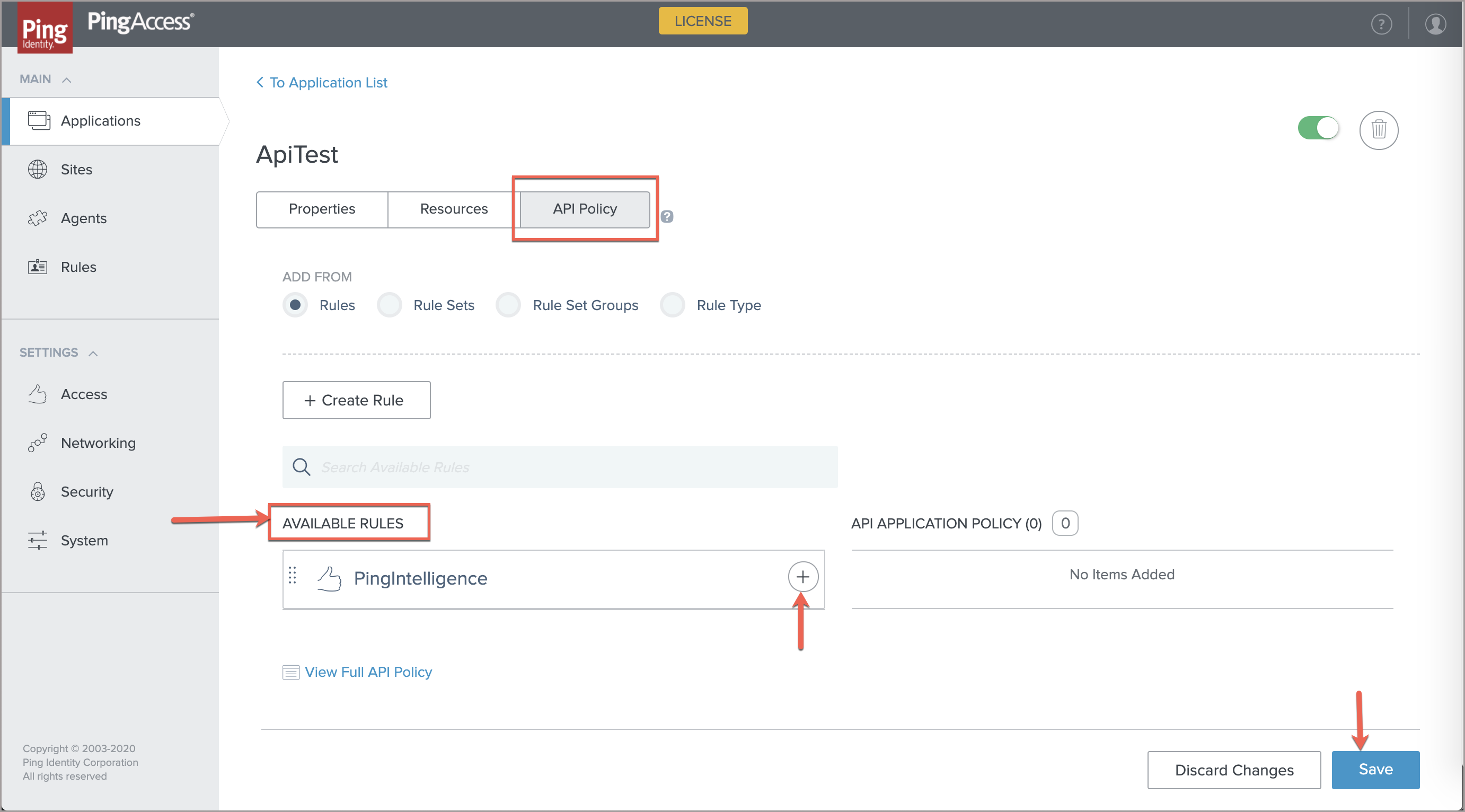
You can selectively apply the PingIntelligence sideband rule to individual resources as well. To apply the sideband rule, click the RESOURCES tab and move the rule from AVAILABLE RULES onto the policy bar. For more information, see Applying rules to applications and resources.
-