Installing and configuring Splunk for PingIntelligence
Before you begin
To complete the configuration of Splunk for PingIntelligence, you need to create a source type. Creating a source type helps Splunk to understand the event format.
About this task
The source type is one of the default fields that Splunk assigns to all the incoming data. Configuring the source type informs Splunk about the type of data ABS provides. This helps Splunk in formatting data intelligently during indexing.
To create a source type:
Steps
-
Configure a new source type by navigating to Splunk Enterprise → Settings → Source Types → New Source type. The source type events page is displayed.
-
Configure the New Source type.
The fields are defined in the following table.
Name Value Source type name
pi_events_source_typeDestination app
Search and reporting (Can change for your apps)
Category
Structures
Indexed extractions
jsonSEDCMD-alter
s/pi-attack-info-//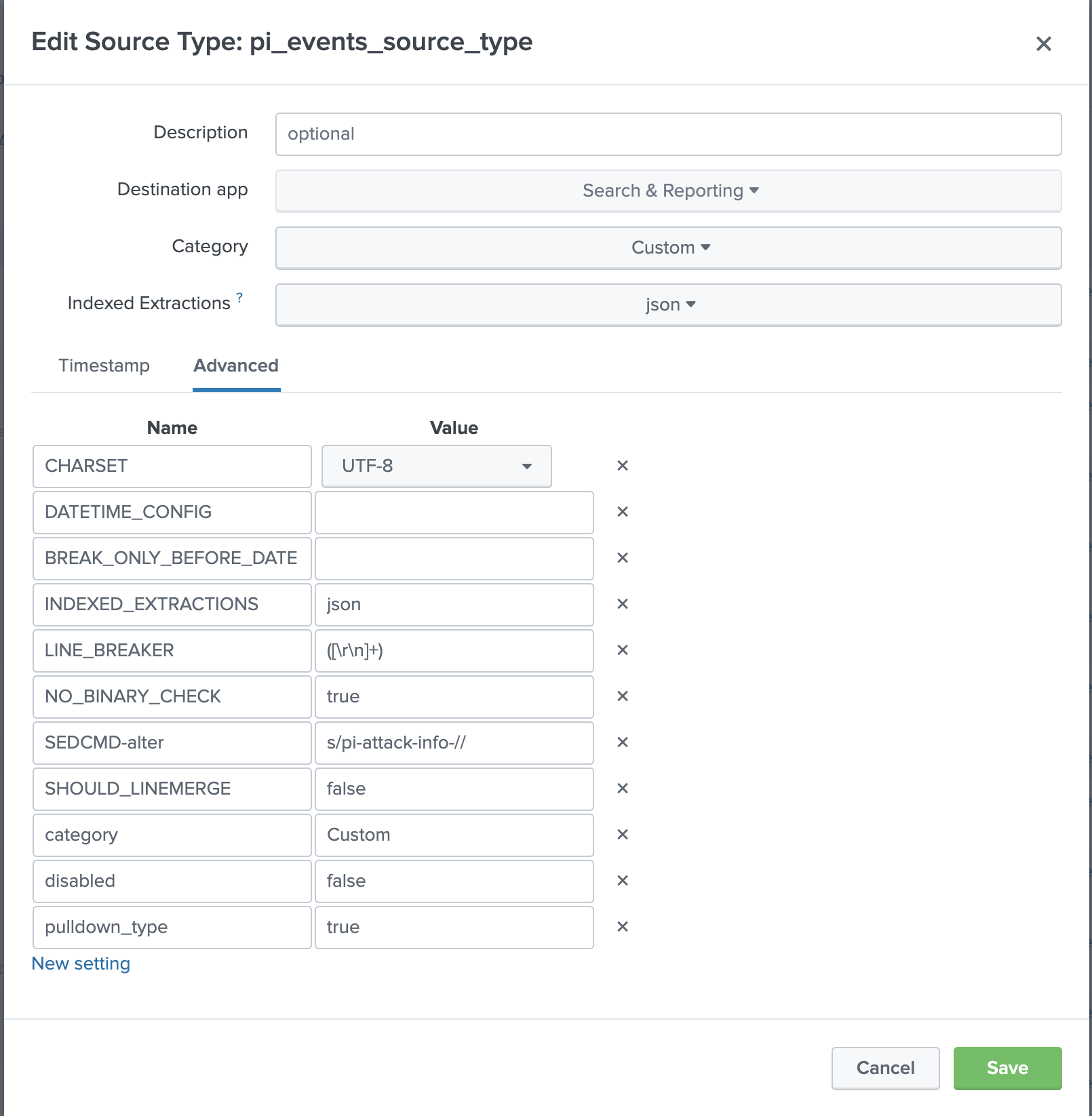
-
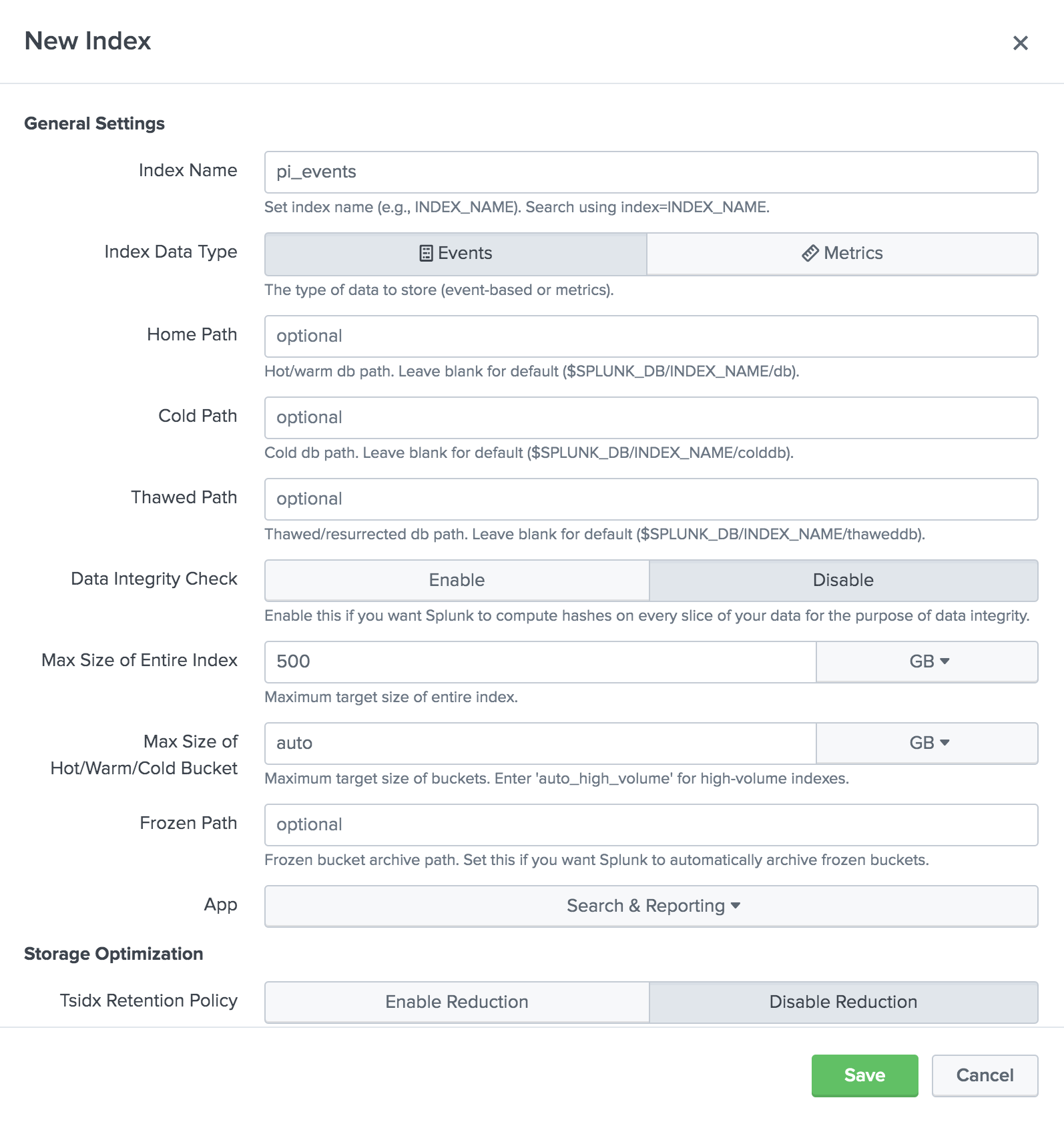
Create a new index
pi_eventsby navigating to Enterprise → Settings → Indexes → New Index.