PingFederate sideband integration
You can deploy PingIntelligence for APIs in a sideband configuration with PingFederate server.
PingIntelligence provides a sideband policy that extracts metadata from an authentication request or response processed by PingFederate. This metadata is passed to PingIntelligence to detect anomalous behavior and attacks by the client. PingIntelligence provides key metrics and forensics around such attacks. It also gives insights into normal traffic patterns by providing detailed client activity reports
The PingIntelligence policy for PingFederate is executed when a client requests an access token or refresh token from PingFederate. The policy secures the token endpoint /as/token.oauth2. For more information on the OAuth endpoints exposed by PingFederate, see PingFederate OAuth 2.0 endpoints.
The PingIntelligence policy supports attack detection and reporting based on IP addresses of the clients. It is deployed in PingFederate as a servlet filter. It supports both OpenID Connect (OIDC) and Security Assertion Markup Language (SAML) V2 standards. The policy deployment does not require any reconfiguration of password credential validator (PCV).
The following diagram shows the architecture of PingIntelligence for APIs components and the interaction flow with PingFederate. The Lightweight Directory Access Protocol (LDAP) directory component in the diagram is used for illustrative purposes. PingFederate also supports other directories and user data-stores through PCVs. For more information, see Password Credential Validators.
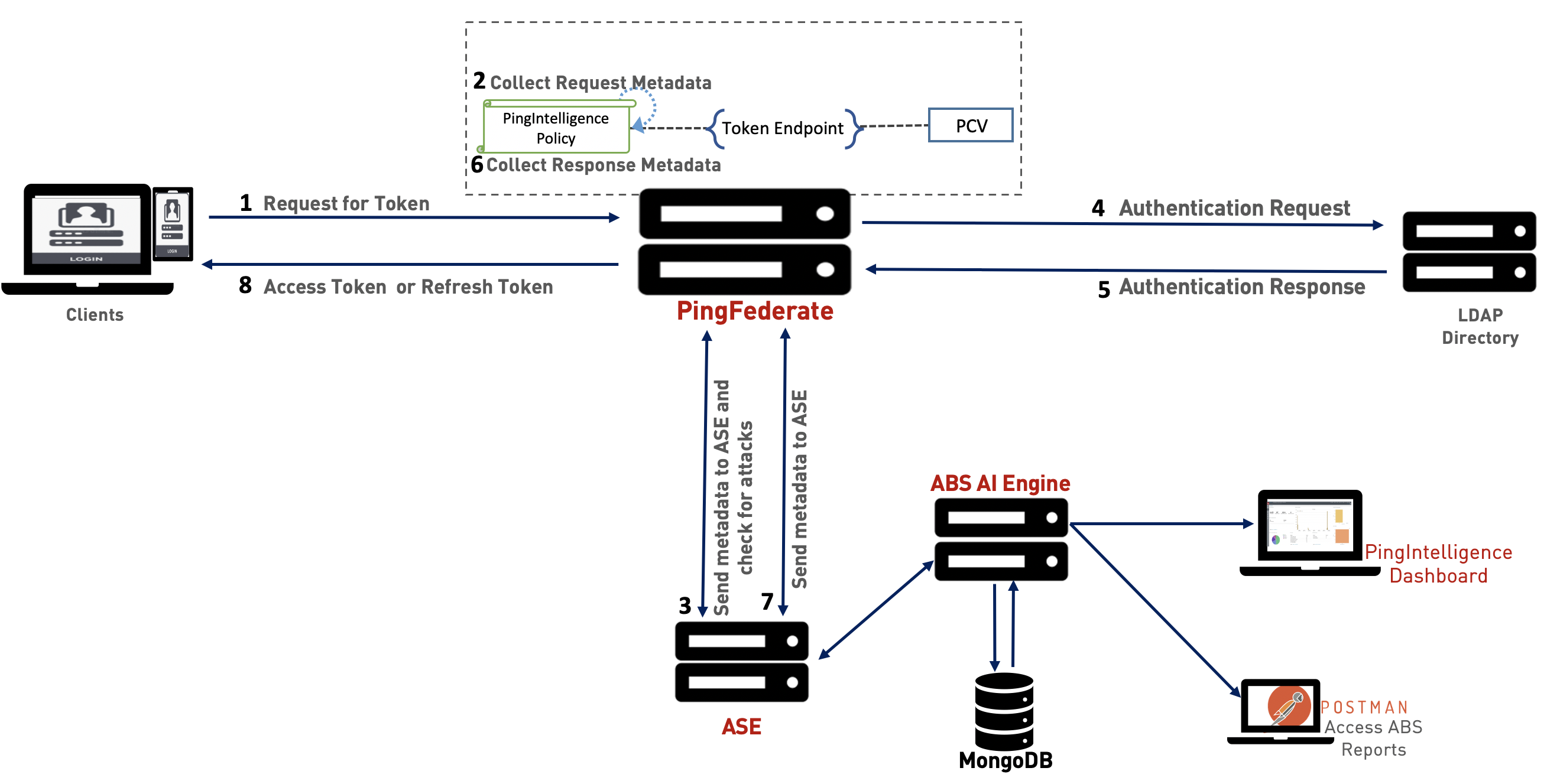
The traffic flow through the PingFederate and PingIntelligence for APIs components is as follows:
-
A client sends a request with its authorization grant to PingFederate to obtain an access or refresh token.
-
The PingIntelligence policy deployed in PingFederate intercepts this request and extracts metadata such as origin IP address, and so on.
-
PingFederate makes an API call to send the metadata to API Security Enforcer (ASE). ASE checks the client identifiers such as IP addresses against its blacklist. A blacklist is a list of client identifiers that were detected executing an attack. If all checks pass, ASE returns a
200-OKresponse to PingFederate. If the checks do not pass, ASE sends a403-Forbiddenresponse code to PingFederate and optionally blocks the client. In both the cases, ASE logs the request information and sends it to the API Behavioral Security (ABS) AI engine to analyze the traffic patterns. -
PingFederate forwards the client authentication request to the supported directory server.
-
PingFederate receives the response from the server.
-
The PingIntelligence for APIs policy intercepts the response and extracts the metadata.
-
PingFederate makes a second API call to pass the response information to ASE, which sends the information to the ABS AI engine for processing.
-
PingFederate sends the requested token to the client.