PingOne RADIUS Gateway Connector
The PingOne RADIUS Gateway connector enables you to integrate PingOne DaVinci flows with a PingOne RADIUS Gateway.
Setup
Resources
For information and setup help, see the following:
-
PingOne documentation:
-
DaVinci documentation:
Requirements
To use the connector, you’ll need:
-
A PingOne license.
-
A PingOne environment.
-
A RADIUS gateway. To create and configure a RADIUS gateway see RADIUS Gateways.
Setting up the connector
In DaVinci, go to Connections and add a PingOne RADIUS gateway connector. For help, see Adding a connector.
Using the connector in a flow
Use the RADIUS Gateway connector to instruct DaVinci to respond to a RADIUS Gateway authentication session request. The connector can send one of the following responses:
-
Accept: Indicates that a user has completed all the required authentication steps. The RADIUS gateway sends an
ACCESS_ACCEPTresponse to the RADIUS client, and grants the user access.You can send user RADIUS attributes back to the RADIUS client, and the connector also provides the option to define vendor-specific attributes.
-
Reject: Indicates that a user failed a required authentication step. The RADIUS gateway sends an
ACCESS_REJECTresponse to the RADIUS client, and rejects the user’s authentication request. -
Challenge: Instructs the gateway to send a challenge to the authenticating user by sending an `ACCESS_CHALLENGE`response to the RADIUS client.
This response type is only supported when using a RADIUS client that supports
ACCESS_CHALLENGErequests. -
Poll: Indicates that the user is authenticating with the PingID mobile app, and the DaVinci flow is waiting for a push response.
RADIUS gateway flow templates
PingOne provides out-of-the-box DaVinci flows that you can integrate into your RADIUS gateway.
|
To use a RADIUS gateway flow template, you first need to add thePingID connector and the PingOne RADIUS Gateway connector. |
The following RADIUS gateway flows are available:
-
RADIUS Gateway Authentication flow: This flow can be used to authenticate users when accessing RADIUS clients that support the RADIUS PAP protocol. You can customize the following options:
-
OTP Fallback: If the PingID server can’t reach the device or the push response can’t be completed, allow users to authenticate with a one-time passcode instead.
-
Newline Character: Select a line separation character to use for RADIUS server challenge messages.
-
RADIUS response attribute.
-
To download this flow, search for RADIUS gateway Authentication flow in Ping Identity Marketplace.
-
RADIUS Gateway - Registration and Authentication flow: This flow can be used to register and authenticate users when accessing RADIUS clients that support Challenge mode. Customization options are the same as those in the RADIUS Gateway - authentication flow.
-
RADIUS Gateway - No Challenge Authentication flow: This flow can be used when accessing RADIUS clients that support the RADIUS PAP protocol to authenticate users with VPN clients that do not support Challenge mode. You can customize the Custom Separator to enable users to enter the OTP with their password. If you define a specific custom separator:
-
When a user wants to authenticate using PingID mobile app they only need to add the custom separator after their password and then the word push.
-
When using other OTP-based authentication methods (such as PingID Desktop app or a YubiKey), the user should add a custom separator after their password and then the OTP. For example
password,123456. -
If the user is registered with multiple devices supported by this mode, an OTP generated by any one of those devices will authenticate the user.
-
This flow does not support on-the-fly registration.
If a custom separator is not defined the user can enter their password followed by the OTP, without a separator. For example
<password>OTP.
-
-
RADIUS Gateway - Advanced Protocols Authentication flow: This flow can be used when accessing RADIUS clients that support advanced protocols (such as MS-CHAPv2) to authenticate users. A comma is defined as the Custom Separator by default to enable users to enter the OTP with their username. The custom separator must be the same as that defined in your NPS, and you can customize it in the Flow settings node, if required. The custom separator enables the following user experience:
-
When a user wants to authenticate using PingID mobile app they only need to add the custom separator after their username and then the word push.
-
When using other OTP-based authentication methods (such as PingID Desktop app or a YubiKey), the user should add a custom separator after their username and then the OTP. For example
John,123456. -
If the user is registered with multiple devices supported by this mode, an OTP generated by any one of those devices will authenticate the user.
-
This flow does not support on-the-fly registration.
To customize the RADIUS Gateway authentication flow template:
-
In the Ping Identity Marketplace search for RADIUS gateway authentication flow and import the flow. For help, see Using DaVinci flow templates.
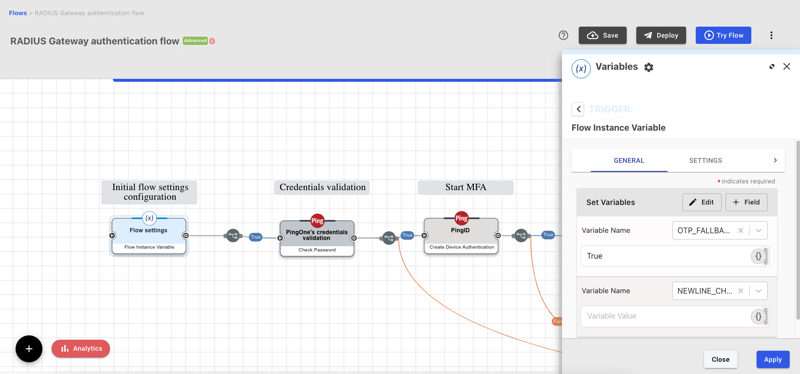
-
To configure an OTP Fallback, select theFlow settings node and modify the
OTP_FALLBACKvariable. Possible values:TrueorFalse. -
To define a Newline Character, select theFlow settings node and modify the
NEWLINE_CHARACTERvariable. Choose from:-
None: (leave the field empty if you do not want to define a newline character).
-
\n: Unix style. -
\r\n: Windows style. -
<br>: HTML
-
-
To add a RADIUS response attribute
: Select the Authentication Approved node`, click Add, and define the attribute properties.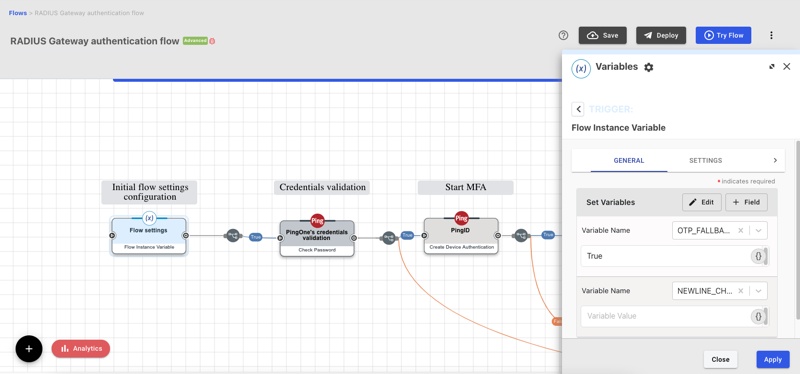
-
-
Capabilities
Radius Response
The returned message sent to the RADIUS client.
Show details
-
Properties
-
Input Schema
-
Output Schema
- Response Type dropDown
-
The type of returned message sent to the RADIUS client. Valid response types are CHALLENGE, POLL, ACCEPT, or REJECT.
-
CHALLENGE
-
POLL
-
ACCEPT
-
REJECT
-
- Response Value textField
-
The text that displays in the Reply-Message, which is sent to the RADIUS client and visible to the user, limited to 253 characters.
- Use the following fields to map values from your flow to RADIUS attributes. label
- Attribute Mapping attributesRulesList
-
default object
-
properties object
-
responseType string required
-
responseValue string
-
description string
-
attributeMapping array
-
-
-
output object
-
text string
-