Splunk Connector
The Splunk connector lets you gain real-time operational intelligence through Splunk in your PingOne DaVinci flow.
Setup
Setting up Splunk
To set up Splunk, create an HTTP event collector token:
-
Click on Settings > Data > Data Inputs.
-
Click HTTP Event Collector or click Actions > Add new button.
-
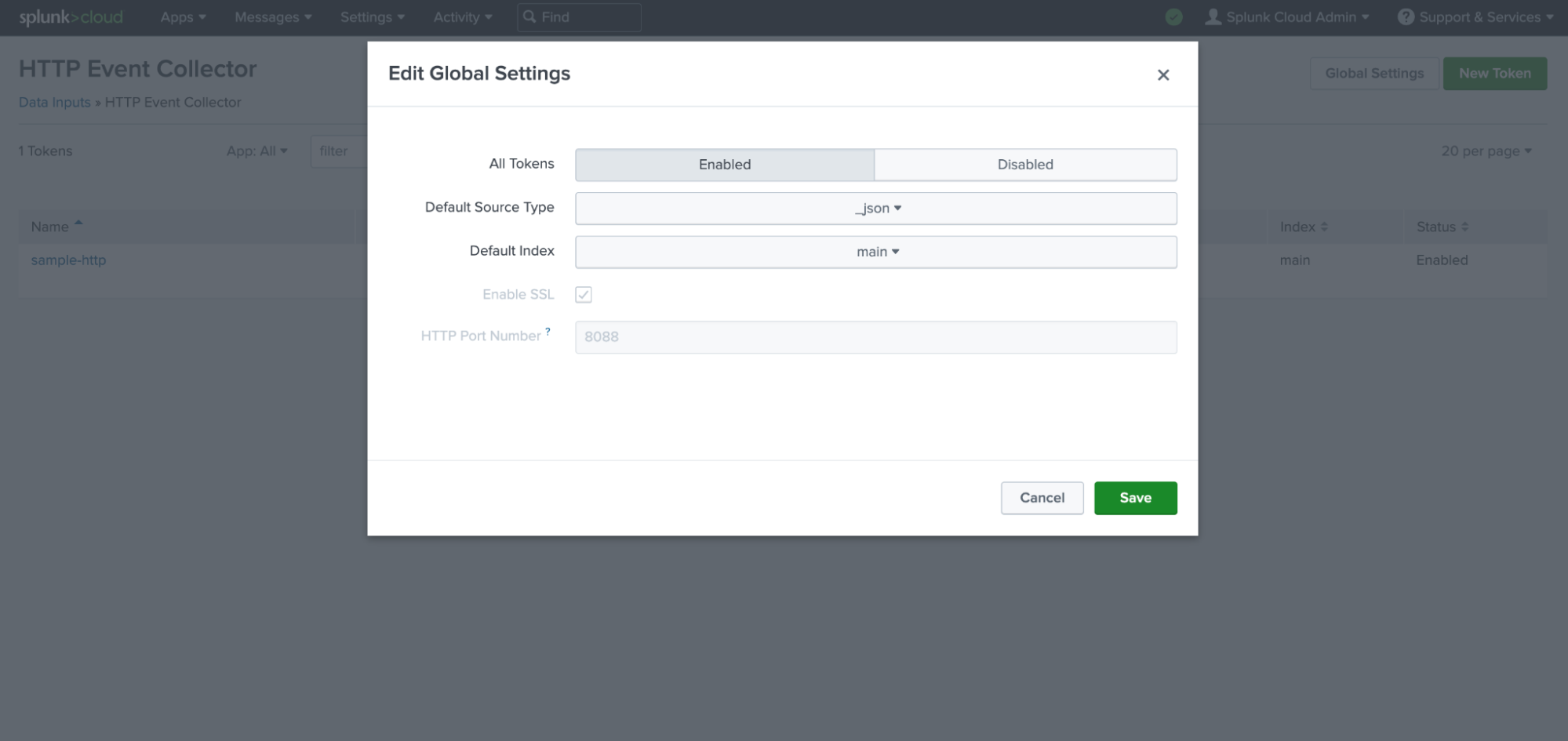
Click Global Settings and use the following configuration:
-
Enable the All Tokens field.
-
Set the Default Source Type to _json.
-
Set the Default Index to Main.
-
Click Save.
-
-
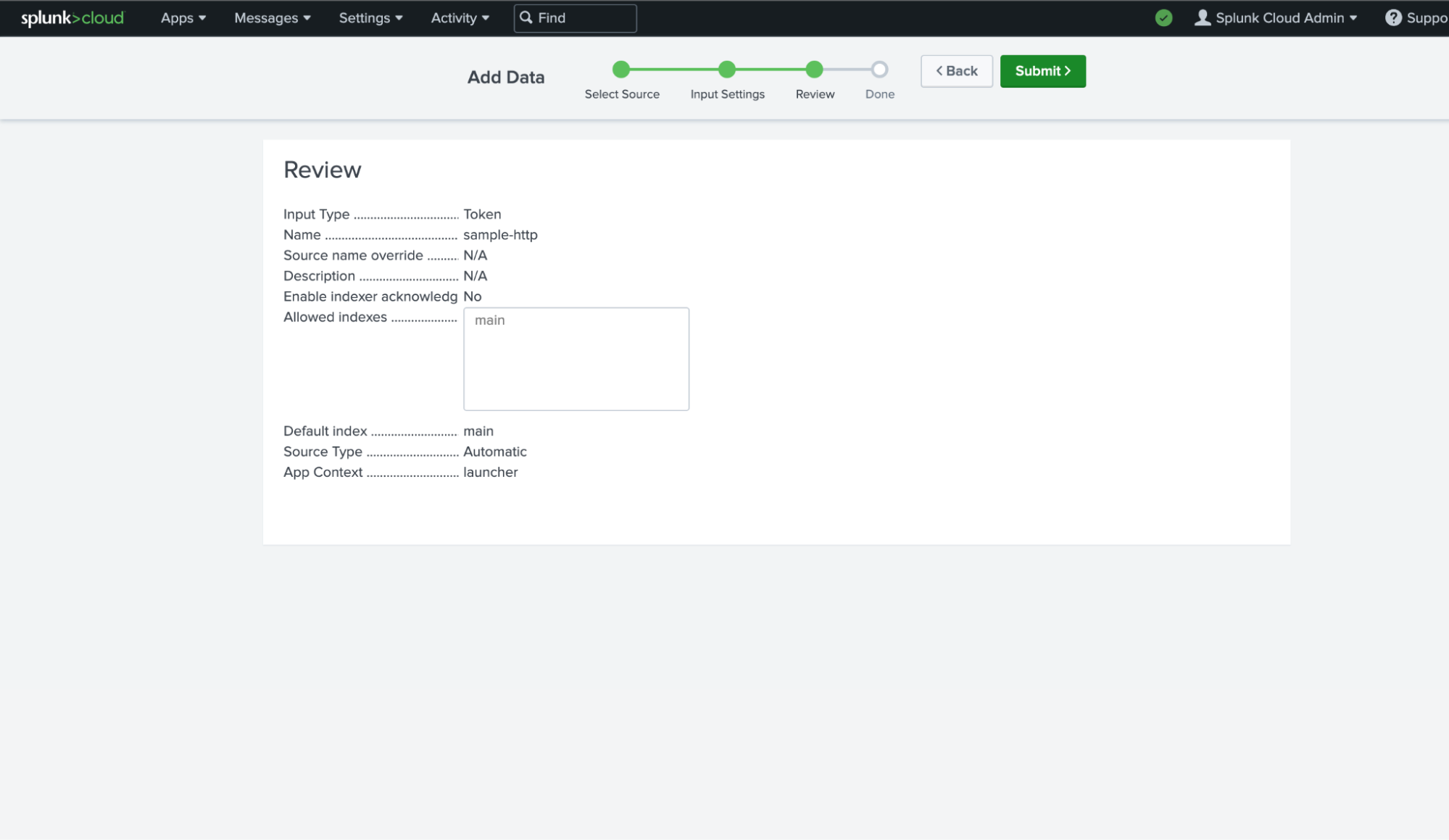
Provide the Token Name, then click Next.
-
Select Source Type as Automatic and Selected Allowed Indexes. Click Review.
-
Click Submit.
-
Copy the generated token.
Configuring the Splunk connector
Add the connector in DaVinci as shown in Adding a connector, then configure it as follows.
Capabilities
Post Splunk Event
Create a new Splunk event.
Show details
-
Properties
-
Input Schema
-
Output Schema
- Time textField
-
The event time in the format {sec}.{ms}.
- Host textField
-
The host value to assign to the event data.
- Source textField
-
The source value to assign to the event data.
- Source Type textField
-
The sourcetype value to assign to the event data.
- Index textField
-
The name of the index by which the event data is to be indexed.
- Event (String) textField
-
Event in raw text.
- Event (JSON) codeEditor
-
Event in raw JSON.
- Fields keyValueList
-
Metadata in Key-Value format.
-
default object
-
properties object
-
apiUrl string required
-
token string required
-
time string
-
host string required
-
source string required
-
sourcetype string required
-
index string required
-
event string
-
-
-
output object
-
rawResponse object
-
code number
-
text string
-
-
Output Example
{
"rawResponse": {
"code": 0,
"text": "Success"
}
}