PingOne Authorize Connector
This connector lets you use PingOne Authorize for policy-based authorization decisions in your PingOne DaVinci flow.
PingOne Authorize controls what users can see and do inside of applications and APIs. It allows organizations to centrally configure authorization requirements, ranging from simple rules to real-time, fine-grained policies.
PingOne Authorize can integrate with other PingOne services, such as PingOne Protect, and exploit information in a PingOne user profile to augment authorization events in real-time.
Use the PingOne Authorize connector to:
-
Externalize authorization from your DaVinci flows, allowing separation of duties between the team controlling the user experience and the team controlling what users are authorized to see and do.
-
Leverage real-time data in fine-grained policies that go beyond identity and roles.
-
Make adaptive, context-aware authorization decisions that result in permit, deny, or challenge outcomes.
-
Assemble and provide DaVinci with authorized information used in flows, for example, retrieving the list of accounts that a user is authorized to access.
Setup
Resources
For information and setup help, learn more in the following documentation:
-
PingOne Authorize documentation:
-
DaVinci documentation:
Requirements
To use the connector, you’ll need:
-
A PingOne Authorize license
-
A PingOne environment with a configured worker application
Setting up PingOne Authorize
-
Follow the instructions in Getting started with PingOne Authorize.
-
In the Trust Framework, define the resources needed to build policies.
-
Write policies for authorization decisions that you want to include in your flow. Include advice in your policies for statements you want to return to your flows.
-
Publish the policies to a Decision Endpoint.
Setting up the PingOne Authorize connector configuration
In DaVinci, add a PingOne Authorize connection. Learn more in Adding a connector.
Connector configuration
Endpoint
The decision endpoint to which the connector submits decision requests. On the Decision Endpoints page in PingOne Authorize, expand the appropriate endpoint to get the URL or the Endpoint ID.
Using the connector in a flow
The PingOne Authorize connector provides these capabilities:
Make Decision Request
Add authorization decision requests to your flows. Decision requests return permit, deny, indeterminate, or not applicable decisions that you can act on in your flows.
Find Statements
Find statements returned in decision responses and use them as inputs in subsequent nodes. Add multiple PingOne Authorize connector nodes at different points in your flow to use the authorized information returned in statements.
When a statement code is found, you can act on it in your flow. For example, you can use it to determine if multi-factor authentication (MFA) is required or a risk update is needed. You can also extract authorized information from the statement payload, for use in scenarios such as reporting fraud case information or providing a list of authorized IDs or accounts in your flow.
In the following example, the first PingOne Authorize connector uses information about an authenticated user to make an authorization decision. The second PingOne Authorize connector finds a statement code in the decision response to determine if MFA is required.
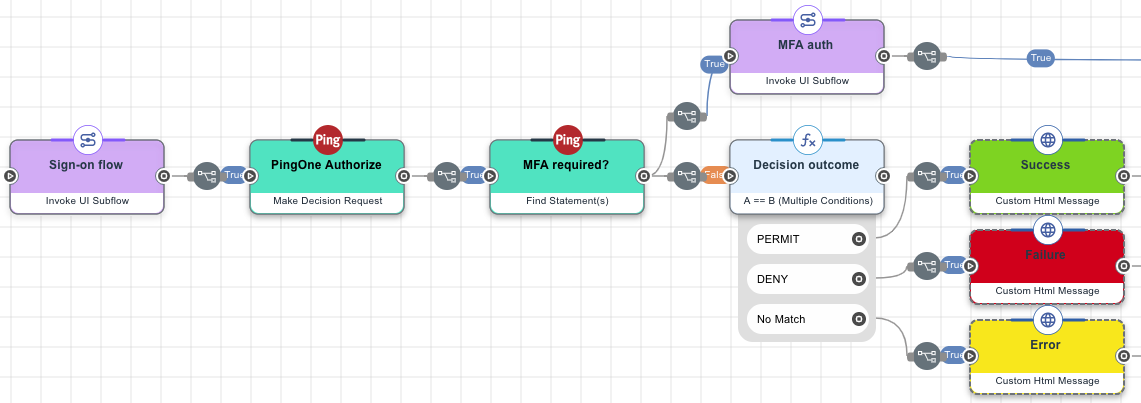
Make a decision request
Collect user information with an HTML form, then use the first PingOne Authorize connector to send the information to PingOne Authorize, and use the decision response in your flow.
-
In your flow, build a sign-on flow that populates a User ID field in an HTTP connector with the HTML Form capability.
-
Send user information to PingOne Authorize:
-
After your sign-on flow, add the PingOne Authorize connector and select the node in your flow.
-
Select the Make Decision Request capability.
-
In the User ID field, click {} and select the User ID variable from your HTML Form node.
-
-
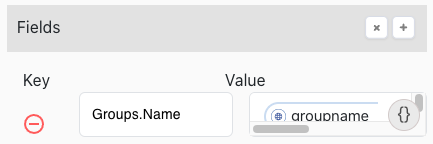
Populate attribute information in the decision request:
-
In the Fields section, click to add one or more key-value pairs. These pairs map to attributes in PingOne Authorize.
-
In the Key field, enter the full name of the attribute that you want to map to the decision request.
-
In the Value field, click {} and select a variable from a node. Alternatively, you can enter a hard-coded value.
To edit key-value pairs, click the Pencil icon. In edit mode, the icon turns into an X icon. Click the X icon to leave edit mode. To delete a Key-Value pair in edit mode, click the - icon under Key.
-
Click Apply.
-
-
Add a node to capture the decision response from PingOne Authorize:
-
After the PingOne Authorize node, add a Function connector and select the node in your flow.
-
Select the A == B (Multiple Conditions) trigger.
-
In the Value A field, click {} and select the decision variable from your PingOne Authorize node.
-
Click Add and enter
PERMITin the Value 1 field. -
Click Add and enter
DENYin the Value 2 field.In this example flow, Not Applicable and Indeterminate decisions fall under No Match and connect to an Error node.
-
Click Apply.
-
-
Add nodes to your flow that act on the Permit, Deny, and No Match decision responses.
-
Test your flow:
-
Click Save, Deploy, then Run.
-
Review status messages.
-
Find statements
Use the second PingOne Authorize connector to find a statement code that matches advice in a policy, then use the code in your flow to determine if MFA is required. If the code is found in decision response statements, then the outcome of the node is true.
-
Find a statement code in the decision response from the first PingOne Authorize node:
-
After the first PingOne Authorize node in your flow, add another PingOne Authorize connector and select the node in your flow.
-
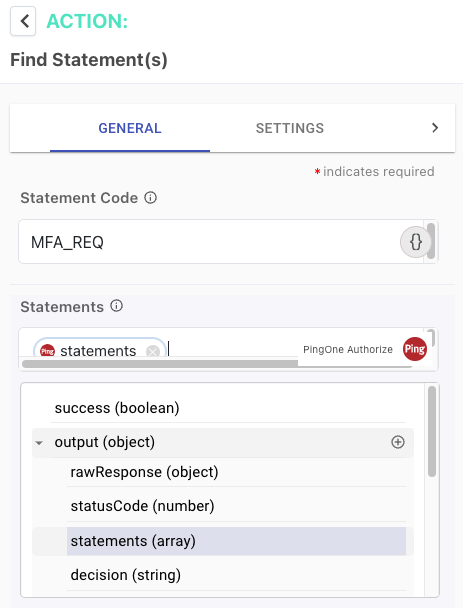
Select the Find Statement(s) capability.
-
In the Statement Code field, enter the statement Code from Advice and Obligations in your policy rule. For example, the following image shows the
MFA_REQadvice code in a PingOne Authorize rule.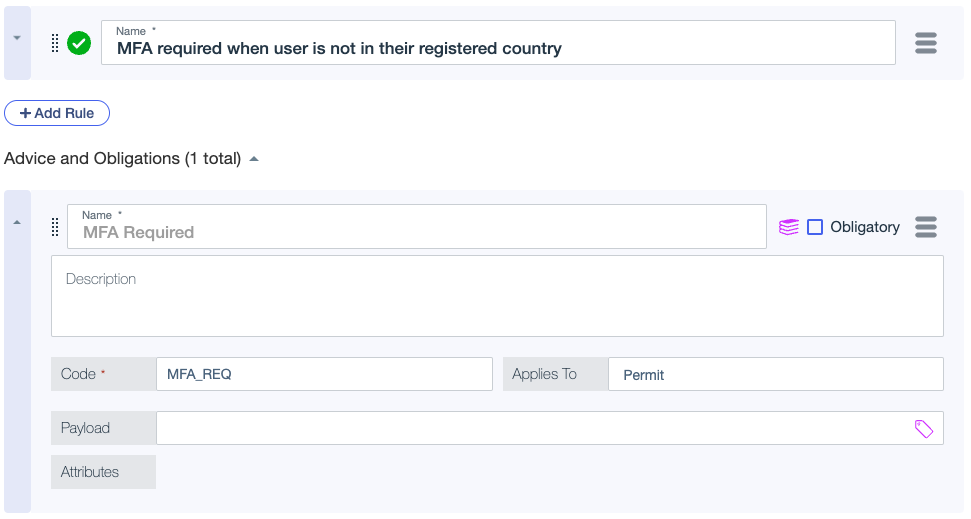
-
In the Statements field, click {} and select the statements (array) output variable from the first PingOne Authorize node in your flow.
-
Click Apply.
-
-
After the second PingOne Authorize node in your flow, add nodes for an MFA flow.
-
Test your flow:
-
Click Save, Deploy, then Run.
-
Review status messages.
-
Capabilities
Make Decision Request
Submit a decision request to a PingOne Authorize endpoint
Show details
-
Properties
-
Input Schema
-
Output Schema
- Parameters keyValueList
-
Input parameters for the decision request
- User ID textField
-
The ID of the PingOne user on whose behalf the connector is making a decision request
-
default object
-
properties object
-
parameters array
-
userId string
-
clientId string
-
clientSecret string
-
endpointUrl string
-
-
-
output object
-
rawResponse object
-
statusCode number
-
statements array
-
decision string
-
headers object
-
Find Statement(s)
Filter decision response statements by code
Show details
-
Properties
-
Input Schema
-
Output Schema
- Statement Code textField
-
The advice code from a PingOne Authorize policy rule to search for in an array of statements from a decision response
- Statements textField
-
The array of statements to search through in a decision response
-
default object
-
properties object
-
statements string
-
code string
-
-
-
output object
-
statements array
-