Security Token Service (STS)
These topics cover concepts, configuration, and usage procedures for working with the Security Token Service (STS) provided by PingAM.
This information is intended for anyone using the STS in PingAM to manage token exchange.
Name changes for ForgeRock products
Product names changed when ForgeRock became part of Ping Identity.
The following name changes have been in effect since early 2024:
| Old name | New name |
|---|---|
ForgeRock Identity Cloud |
PingOne Advanced Identity Cloud |
ForgeRock Access Management |
PingAM |
ForgeRock Directory Services |
PingDS |
ForgeRock Identity Management |
PingIDM |
ForgeRock Identity Gateway |
PingGateway |
Learn more about the name changes in New names for ForgeRock products in the Knowledge Base.
Introduction to STS
The Security Token Service (STS) lets AM bridge identities across existing federated environments to establish cross-domain trust relationships using token transformations. For example, you can federate two different environments by transforming OIDC ID tokens into SAML v2.0 assertions.
To do this, AM provides a REST STS framework for token transformations. This framework is loosely based on the SOAP WS-Trust specification.
A WS-Trust model involves communication between the components, a requestor, web service, and the STS:
-
The requestor is a web client or programmatic agent that wants to use a service offered by the web service.
-
The web service lets authenticated and authorized clients access resources or applications.
-
The identity provider stores claims about subjects and works with the STS to issue security tokens.
-
The STS acts as a trusted third-party web service. It asserts the identity of a requestor across different security domains through the exchange of security tokens and brokers a trust relationship between the requestor and the web service provider. The STS issues tokens based on its configurations, which model the identity of a given identity provider, and issues tokens to a specific relying party.
-
A security token is an STS data structure representing a set of claims that assert the identity of a subject. A single claim is identity information, such as a subject’s name, age, gender, and email address.
Web services and requestors (that is, consumers or clients) are typically deployed across different security domains and topologies. Each domain may require a specific security token type to assert authenticated identities. The STS provides a way to exchange tokens across these different domains without re-authenticating or re-establishing trust relationships while allowing the requestor access to a web service’s protected resources.
Supported features
The STS supports the following features:
- REST endpoints
-
REST endpoints are exposed upon instance creation.
- Token transformations
-
The STS issues OpenID Connect V1.0 (OIDC) and SAML V2.0 tokens (bearer, holder-of-key, sender vouches).
- OIDC
-
Username token → OIDC
OIDC → OIDC
X.509 token → OIDC
AM Session token → OIDC - SAML V2.0
-
Username token → SAML v2.0
X.509 token → SAML v2.0
OIDC token → SAML v2.0
AM Session token → SAML v2.0
- Publish service
-
You can configure STS instances using the AM admin UI or programmatically. AM provides an STS publish service that lets you publish these instances with a POST request to the endpoints. Because a published instance can have only a single encryption key, you need one published instance per service provider that the web service invoking the STS intends to call.
- Custom SAML assertion plugins
-
AM supports customizable SAML assertion statements. You can create custom plug-ins for
Conditions,Subject,AuthenticationStatements,AttributeStatements, andAuthorizationDecisionStatementsstatements. - Custom token validators and providers
-
The STS provides the ability to customize tokens. For example, you can configure STS to transform a token of type CUSTOM to a SAML V2.0 token.
STS instances
AM’s Security Token Service (STS) issues OpenID Connect v1.0 (OIDC) or SAML v2.0 tokens for a single service provider. An STS instance has the following mandatory configuration:
-
Issuer. The issuer corresponds to the IdP
EntityID. -
SP EntityID. The SP
EntityIDis used in theAudienceRestrictionelement of theConditionsstatement of the issued assertion. -
SP assertion consumer service URL. The SP assertion consumer service URL is used as the
Recipientattribute of thesubjectConfirmationelement in theSubjectstatement, which is required for bearer assertions according to the Web SSO profile.
To support signing and encryption, each STS instance has a configuration state that specifies the location of the signing and encryption keys:
-
If you use assertion signature, you must specify the keystore path and password and the alias and password of the
PrivateKeyused to sign the assertion. -
If you use assertion encryption, you must specify the keystore path and password. You must also must specify the alias of the SP’s X509 certificate that includes the
PublicKeyused to encrypt the symmetric key that encrypts the generated assertion.The keystore location can be an absolute path on the local filesystem or a path relative to the AM classpath. You can choose to encrypt only the
NameIDandAttributeStatementattributes or the entire assertion.
Any statement that constitutes a SAML v2.0 assertion can be customized.
For each STS instance, you can provide custom plug-ins for
Conditions, Subject, AuthenticationStatements, AttributeStatements, and AuthorizationDecisionStatements.
If you specify custom plug-ins in the configuration state of the published STS instance,
the custom classes are consulted to provide the specific statements.
Learn more in org.forgerock.openam.sts.tokengeneration.saml2.statements.
Each STS instance must specify the authentication context (AuthnContext) that will be included in the
AuthenticationStatements of the generated assertion. The AuthnContext lets the generated SAML v2.0 assertion
specify how the assertion’s subject was authenticated. For a token transformation, the AuthnContext is a function of
the input token type.
By default, the following AuthnContext strings are included in the SAML v2.0 assertion generated
as part of the transformation of the following input token types:
| Input token type | AuthnContext string |
|---|---|
AM |
|
Username Token and OIDC Token |
|
X.509 Token |
|
To override these default mappings, implement the org.forgerock.openam.sts.token.provider.AuthnContextMapper
interface and specify the name of the implementation in the configuration of the published STS instance.
|
Read the following specifications before you implement the STS:
The STS model illustrates a simple STS topology between a requestor, a web service, and an STS instance. The STS instance is set up with the identity provider, which has a trust relationship with the web service:
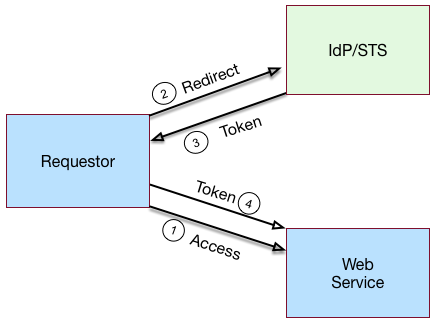
STS process flow
-
A requestor makes an access request to a web resource.
-
The web service redirects the requestor to the STS.
-
The requestor sends an HTTP(S) POST request to the STS endpoint. The request includes credentials, token input type, and desired token output type.
The following example generates a bearer token:
$ curl \ --request POST \ --header "Content-Type: application/json" \ --data '{ "input_token_state": { "token_type": "USERNAME", "username": "bjensen", "password": "Ch4ng31t" }, "output_token_state": { "token_type": "SAML2", "subject_confirmation": "BEARER" } }' \ https://am.example.com:8443/am/rest-sts/username-transformer?_action=translatebashThe following example generates an OIDC token:
$ curl \ --request POST \ --header "Content-Type: application/json" \ --data '{ "input_token_state": { "token_type": "USERNAME", "username": "bjensen", "password": "Ch4ng31t" }, "output_token_state": { "token_type": "OPENIDCONNECT", "nonce":"12345678", "allow_access":true } }' \ https://am.example.com:8443/am/rest-sts/username-transformer?_action=translatebash -
The STS does the following:
-
Validates the signature.
-
Decodes the payload and verifies that the requestor issued the transaction.
-
Validates the requestor’s credentials.
-
Creates an interim AM session and, optionally, creates a CTS token for the session.
-
Issues a token to the requestor.
-
Invalidates the interim AM session, if configured.
-
-
The requestor is redirected to the web service and presents its token to the web service.
-
The web service does the following:
-
Validates the signature and decodes the payload.
-
Verifies that the requestor issued the request.
-
Extracts and validates the token and processes the request.
-
-
If a CTS token was created for the session, the web service can call the STS to invalidate the token and the corresponding AM session.
Validate input tokens
STS token transformations validate input tokens before generating output tokens. The STS uses authentication trees to perform token validation. When deploying STS, you must configure an appropriate authentication tree to validate input tokens.
This section describes authentication configuration requirements for username, X.509, and OIDC tokens. No special authentication configuration is required when using AM session tokens as the input tokens in token transformations.
Because STS instances aren’t part of a secure framework like WS-Trust, this section also discusses security considerations when sending tokens across a network to an STS instance.
In addition to configuring AM authentication to support input token validation, you must identify the authentication tree that will validate each input token type. To do so, configure the Authentication Target Mappings property in the STS instance configuration. Learn more in the STS configuration properties.
Validate username tokens
Username tokens passed to an STS instance contain the username/password combination in cleartext. Tokens can be validated using any tree that supports username/password authentication.
With usernames and passwords in cleartext, be sure to configure your deployment with an appropriate level of security. Deploy STS instances that support input username token transformations over TLS.
Validate X.509 certificate tokens
STS instances can obtain X.509 certificates used as input tokens in two ways:
-
From the header key defined in the STS instance’s Client Certificate Header Key property. In this case, STS also confirms the request came from a host specified in the Trusted Remote Hosts property.
-
From the
jakarta.servlet.request.X509Certificateattribute in the ServletRequest. If you don’t set a header key in the Client Certificate Header Key property, the STS instance obtains the X.509 certificate from the ServletRequest.
To validate X.509 certificate tokens, an STS instance must reference a tree that includes the Certificate Collector node and the Certificate Validation node in the Authentication Target Mappings property.
The Certificate Validation node validates the X.509 certificate input token. The node optionally performs Certificate Revocation List (CRL) or Online Certificate Status Protocol (OCSP) checking, and can check that the specified certificate is in an LDAP datastore.
If certificates are passed to the STS using HTTP headers, you must configure the HTTP Header Name for the Client Certificate and the Trusted Remote Hosts properties in the Certificate Collector node to match the configuration of your STS instance.
Validate OIDC tokens
To validate OIDC input tokens, an STS instance must reference a tree that includes the OIDC ID Token Validator node in the Authentication Target Mappings property.
Configure the OIDC ID Token Validator node as follows:
- ID Token Header Name
-
Specify a header. The STS instance’s Target Authentication Mapping property must reference the same header.
- Token Issuer
-
Specify the issuer name. Set the token issuer’s discovery URL, JWK URL, or client secret in the OpenID Connect validation configuration value property.
- Audience name
-
If incoming OIDC tokens contains
audclaims, specify the valid claims in this property. - Authorized parties
-
If incoming OIDC tokens contain
azpclaims, specify valid claims in this property. - Transformation Script
-
Select a
Social Identity Provider Profile Transformationscript to map JWK claims to attributes in the identity store.
Configure STS instances
You configure Security Token Service (STS) instances to perform one or more token transformations. Each instance provides configuration details about how SAML v2.0 and/or OIDC output tokens are encrypted or signed. Deployments that support multiple SAML v2.0 and/or OIDC service providers require multiple STS instances.
When you publish an STS instance, you create an STS instance with a given configuration. You can publish instances using the AM admin UI or the REST API.
When you publish an STS instance, AM exposes a REST endpoint for accessing the instance, and the instance is immediately available for use to callers.
Configure an STS instance in the UI
To configure an STS instance using the AM admin UI, go to Realms > Realm Name > STS, and click Add Rest STS.
Read STS configuration properties for detailed information about STS configuration properties.
Configure an STS instance over REST
To publish an STS instance programmatically, use the Publish service. This service is a collection of endpoints you can use to publish instances instead of accessing the AM admin UI.
Learn more in The Publish service.
Consume STS instances
You consume a Security Token Service (STS) instance by sending REST API calls to the instance’s endpoint.
STS instance endpoint
An STS instance endpoint is composed of the following:
-
The AM context
-
The string
rest-sts -
The realm in which the STS instance is configured
-
The deployment URL element (a configuration property of the STS instance)
For example, an STS instance configured in the alpha realm
with the deployment URL element username-transformer exposes the endpoint /rest-sts/alpha/username-transformer.
JSON representation of token transformations
Token transformations are represented in JSON as follows:
{
"input_token_state": {
"token_type": "INPUT_TOKEN_TYPE"
…INPUT_TOKEN_TYPE_PROPERTIES…
},
"output_token_state": {
"token_type": "OUTPUT_TOKEN_TYPE"
…OUTPUT_TOKEN_TYPE_PROPERTIES…
}
}The STS supports the following token types and properties:
- Input token types
-
-
USERNAMERequires the
usernameandpasswordproperties. -
OPENAMRequires the
session_idproperty, with an SSO token as its value. -
X509No properties are required because input X.509 tokens are presented in HTTP headers or through TLS.
Find information about X.509 tokens in the Authentication Target Mappings and Client Certificate Header Key properties in the STS configuration properties.
-
OPENIDCONNECTRequires the
oidc_id_tokenproperty with the OIDC token as its value.
-
- Output token types
-
-
SAML2Requires the
subject_confirmationproperty, the value of which determines the<saml:ConfirmationMethod>element for the generated SAML v2.0 assertion. Valid values areBEARER,SENDER_VOUCHES, andHOLDER_OF_KEY.When generating an assertion with a holder-of-key subject confirmation method, the
proof_token_stateproperty is required. The value for this property is an object that contains thebase64EncodedCertificateproperty. -
OPENIDCONNECTRequires the
nonceandallow_accessproperties.
-
The following are examples of JSON payloads that define STS token transformations:
-
Transform a username token to a SAML v2.0 token with the
BEARERsubject confirmation method:{ "input_token_state": { "token_type": "USERNAME", "username": "bjensen", "password": "Ch4ng31t" }, "output_token_state": { "token_type": "SAML2", "subject_confirmation": "BEARER" } }json -
Transform an X.509 token to a SAML v2.0 token with the
SENDER_VOUCHESsubject confirmation method:{ "input_token_state": { "token_type": "X509" }, "output_token_state": { "token_type": "SAML2", "subject_confirmation": "SENDER_VOUCHES" } }json -
Transform an OIDC token to a SAML v2.0 token with the
HOLDER_OF_KEYsubject confirmation method:{ "input_token_state": { "token_type": "OPENIDCONNECT", "oidc_id_token": "eyAiYWxQ.euTNnNDExNTkyMjEyIH0.kuNlKwyvZJqaC8EYpDyPJMiEcII" }, "output_token_state": { "token_type": "SAML2", "subject_confirmation": "HOLDER_OF_KEY", "proof_token_state": { "base64EncodedCertificate": "MIMbFAAOBjQAwgYkCgYEArSQ…c/U75GB2AtKhbGS5pimrW0Y0Q==" } } }json -
Transform an AM SSO token to an OIDC token:
{ "input_token_state": { "token_type": "OPENAM", "session_id": "AQIC5wM2…TMQAA*" }, "output_token_state": { "token_type": "OPENIDCONNECT", "nonce": "471564333", "allow_access": true } }json
Find more examples of JSON payloads you can send to STS instances in the comments in the Java example sample code.
Command-line example
You can use the curl command to check that a published STS instance is working as expected.
For example, if you publish a REST instance with a deployment URL element username-transformer
that supports username to SAML v2.0 bearer assertion token transformation,
you can send an HTTP POST request to the /rest-sts/username-transformer endpoint,
setting the _action parameter to translate as follows:
$ curl \
--request POST \
--header "Content-Type: application/json" \
--data '{
"input_token_state": {
"token_type": "USERNAME",
"username": "bjensen",
"password": "Ch4ng31t"
},
"output_token_state": {
"token_type": "SAML2",
"subject_confirmation": "BEARER"
}
}' \
https://am.example.com:8443/am/rest-sts/username-transformer?_action=translate
{
"issued_token":
"<saml:Assertion
xmlns:saml=\"urn:oasis:names:tc:SAML:2.0:assertion\"
Version=\"2.0\"
ID=\"s2c51ebd0ad10aae44fb76e4b400164497c63b4ce6\"
IssueInstant=\"2016-03-02T00:14:47Z\">\n
<saml:Issuer>saml2-issuer</saml:Issuer>
<saml:Subject>\n
<saml:NameID
Format=\"urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress\">bjensen
</saml:NameID>
<saml:SubjectConfirmation
Method=\"urn:oasis:names:tc:SAML:2.0:cm:bearer\">\n
<saml:SubjectConfirmationData
NotOnOrAfter=\"2016-03-02T00:24:47Z\" >
</saml:SubjectConfirmationData>
</saml:SubjectConfirmation>\n
</saml:Subject>
<saml:Conditions
NotBefore=\"2016-03-02T00:14:47Z\"
NotOnOrAfter=\"2016-03-02T00:24:47Z\">\n
<saml:AudienceRestriction>\n
<saml:Audience>saml2-issuer-entity</saml:Audience>\n
</saml:AudienceRestriction>\n</saml:Conditions>\n
<saml:AuthnStatement
AuthnInstant=\"2016-03-02T00:14:47Z\">
<saml:AuthnContext>
<saml:AuthnContextClassRef>
urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport
</saml:AuthnContextClassRef>
</saml:AuthnContext>
</saml:AuthnStatement>
</saml:Assertion>\n"
}The iPlanetDirectoryPro header is required and should contain the SSO token of an administrative user,
such as amAdmin, who has access to perform the operation.
Java example
The RestSTSConsumer.java sample code provides an example
of how to consume a published STS instance programmatically.
Tailor this example as required to provide programmatic consumption of your own STS instances.
|
Learn about downloading and building PingAM sample source code in the following Knowledge Base article: How do I access and build the sample code provided for PingAM?. You can find the STS code examples under |
|
You can’t compile the sample code referenced in this section because it uses classes that aren’t available publicly. The code provides patterns to developers familiar with the problem domain and is intended only to assist developers who want to programmatically consume STS instances. |
Query, validate, and cancel tokens
The Security Token Service (STS) instance supports token persistence, which is the ability to store tokens issued for the STS instance in the Core Token Service (CTS). You enable token persistence for STS instances under Realms > Realm Name > STS > STS Instance Name > General Configuration > Persist Issued Tokens in Core Token Store. Tokens are saved in the CTS for the duration of the token lifetime, which is a configuration property for STS-issued SAML v2.0 and OIDC tokens. Tokens with expired durations are periodically removed from the CTS.
With token persistence enabled for an STS instance, AM provides the ability to query, validate, and cancel tokens issued for the instance:
-
Querying tokens means listing tokens issued for an STS instance or for a user.
-
Validating a token means verifying that the token is still present in the CTS.
-
Cancelling a token means removing the token from the CTS.
Invoke the sts-tokengen endpoint
The sts-tokengen endpoint provides administrators with the ability to query and cancel tokens issued using REST API
calls.
When using the sts-tokengen endpoint, make sure you provide the token ID for an AM administrator,
such as amAdmin, as the value of a header whose name is the name of the SSO token cookie,
by default iPlanetDirectoryPro.
Query tokens
List tokens issued for an STS instance by using the queryFilter action in an HTTP GET call
to the sts-tokengen endpoint with the /sts-id argument.
The following example lists all the tokens issued for the username-transformer STS instance.
The results show that AM has issued two OIDC tokens for bjensen
for the username-transformer STS instance:
$ curl \
--request GET \
--header "iPlanetDirectoryPro: AQIC5…" \
https://am.example.com:8443/am/sts-tokengen?_queryFilter=\/sts_id+eq+\'username-transformer\'
{
"result":[
{
"_id":"B663D248CE4C3B63A7422000B03B8F5E0F8E443B",
"_rev":"",
"token_id":"B663D248CE4C3B63A7422000B03B8F5E0F8E443B",
"sts_id":"username-transformer",
"principal_name":"bjensen",
"token_type":"OPENIDCONNECT",
"expiration_time":1459376096
},
{
"_id":"7CB70009970D1AAFF177AC2A08D58405EDC35DF5",
"_rev":"",
"token_id":"7CB70009970D1AAFF177AC2A08D58405EDC35DF5",
"sts_id":"username-transformer",
"principal_name":"bjensen",
"token_type":"OPENIDCONNECT",
"expiration_time":1459376098
}
],
"resultCount":2,
"pagedResultsCookie":null,
"totalPagedResultsPolicy":"NONE",
"totalPagedResults":-1,
"remainingPagedResults":-1
}List tokens issued for a particular user with the queryFilter action in an HTTP GET call
to the sts-tokengen endpoint with the /token-principal argument.
The following example lists all the tokens issued for bjensen.
The results show that AM has issued two OIDC tokens:
$ curl \
--request GET \
--header "iPlanetDirectoryPro: AQIC5…" \
https://am.example.com:8443/am/sts-tokengen?_queryFilter=\/token_principal+eq+\'bjensen\'
{
"result":[
{
"_id":"B663D248CE4C3B63A7422000B03B8F5E0F8E443B",
"_rev":"",
"token_id":"B663D248CE4C3B63A7422000B03B8F5E0F8E443B",
"sts_id":"username-transformer",
"principal_name":"bjensen",
"token_type":"OPENIDCONNECT",
"expiration_time":1459376096
},
{
"_id":"7CB70009970D1AAFF177AC2A08D58405EDC35DF5",
"_rev":"",
"token_id":"7CB70009970D1AAFF177AC2A08D58405EDC35DF5",
"sts_id":"username-transformer",
"principal_name":"bjensen",
"token_type":"OPENIDCONNECT",
"expiration_time":1459376098
}
],
"resultCount":2,
"pagedResultsCookie":null,
"totalPagedResultsPolicy":"NONE",
"totalPagedResults":-1,
"remainingPagedResults":-1
}Cancel tokens
Cancel tokens by making an HTTP DELETE call to the sts-tokengen/token-id endpoint:
$ curl \
--request DELETE \
--header "iPlanetDirectoryPro: AQIC5…" \
https://am.example.com:8443/am/sts-tokengen/B663D248CE4C3B63A7422000B03B8F5E0F8E443B
{
"_id":"B663D248CE4C3B63A7422000B03B8F5E0F8E443B",
"_rev":"B663D248CE4C3B63A7422000B03B8F5E0F8E443B",
"result":"token with id B663D248CE4C3B63A7422000B03B8F5E0F8E443B successfully removed."
}Validate and cancel tokens by invoking an STS instance
STS users can validate and cancel tokens by making an HTTP POST call to an STS instance’s endpoint.
To validate a token, use the validate action.
The following example validates an OIDC token
previously issued by the username-transformer STS instance:
$ curl \
--request POST \
--header "iPlanetDirectoryPro: AQIC5…" \
--header "Content-Type: application/json" \
--data '{
"validated_token_state": {
"token_type": "OPENIDCONNECT",
"oidc_id_token": "eyAidHlwIjogIkpXVCIsIC…"
}
}' \
https://am.example.com:8443/am/rest-sts/username-transformer?_action=validate
{
"token_valid":true
}To cancel a token, use the cancel action.
The following example cancels an OIDC token previously issued by the username-transformer STS instance:
$ curl \
--request POST \
--header "iPlanetDirectoryPro: AQIC5…" \
--header "Content-Type: application/json" \
--data '{
"cancelled_token_state": {
"token_type": "OPENIDCONNECT",
"oidc_id_token": "eyAidHlwIjogIkpXVCIsIC…"
}
}' \
https://am.example.com:8443/am/rest-sts/username-transformer?_action=cancel
{
"result":"OPENIDCONNECT token cancelled successfully."
}The Publish service
To publish an STS instance, perform an HTTP POST on the /sts-publish/rest endpoint,
specifying the _action=create parameter in the URL.
For example, you could publish an STS instance named username-transformer in the Top Level Realm as follows:
$ curl \
--request POST \
--header "iPlanetDirectoryPro: AQIC5…" \
--header "Content-Type: application/json" \
--data '{
"invocation_context": "invocation_context_client_sdk",
"instance_state":
{
"saml2-config":
{
"issuer-name":"saml2-issuer",
…
},
"deployment-config":
{
"deployment-url-element":"username-transformer",
"deployment-realm":"/",
…
},
"persist-issued-tokens-in-cts":"false",
"supported-token-transforms":[{
"inputTokenType":"USERNAME",
"outputTokenType":"OPENIDCONNECT",
"invalidateInterimOpenAMSession":false
}],
"oidc-id-token-config":{
"oidc-issuer":"test",
…
}
}
}' \
https://am.example.com:8443/am/sts-publish/rest?_action=create
{
"_id":"username-transformer",
"_rev":"21939129",
"result":"success",
"url_element":"username-transformer"}
}The instance_state object in the JSON payload represents the STS instance’s configuration.
Find a complete example of an instance_state object in the sample code for the RestSTSInstancePublisher class in Publish STS instances.
Accessing the sts-publish endpoint requires administrative privileges.
Authenticate as an AM administrative user, such as amAdmin, before attempting to publish an STS instance.
In addition to publishing instances, the sts-publish endpoint can also return the configuration of an STS instance
when you perform an HTTP GET on the endpoint for the instance, such as
/sts-publish/rest/realm/deployment-URL-element.
Where deployment-URL-element is the value of the STS instance’s deployment URL element, which is one of the instance’s configuration properties, and realm is the realm in which the instance has been configured.
For example, you could obtain the configuration of an STS instance configured in the Top Level Realm
with the deployment URL element username-transformer as follows:
$ curl \
--request GET \
--header "iPlanetDirectoryPro: AQIC5…" \
https://am.example.com:8443/am/sts-publish/rest/username-transformer
{
"_id":"username-transformer",
"_rev":"-659999943",
"username-transformer":{
"saml2-config":{
"issuer-name":"saml2-issuer",
…
},
"deployment-config":{
"deployment-url-element":"username-transformer",
…
},
"persist-issued-tokens-in-cts":"false",
"supported-token-transforms":[
{
"inputTokenType":"USERNAME",
"outputTokenType":"OPENIDCONNECT",
"invalidateInterimOpenAMSession":false
}
],
"oidc-id-token-config":{
"oidc-issuer":"test",
…
}
}
}You can delete STS instances by performing an HTTP DELETE on /sts-publish/rest/realm/deployment-URL-element.
Publish STS instances
The sample code referenced in this section provides an example of how to programmatically publish STS instance. The code isn’t intended to be a working example. Instead, it is a starting point that you can modify to satisfy your organization’s specific requirements.
Learn about downloading and building PingAM sample source code in the following Knowledge Base article: How do I access and build the sample code provided for PingAM?.
You can find the STS code examples under /path/to/openam-samples-external/sts-example-code.
After publishing an STS instance programmatically, you can view the instance’s configuration in the AM admin UI. The instance is ready for consumption.
Sample code is available for the following classes:
- RestSTSInstancePublisher
-
The
RestSTSInstancePublisherclass exposes an API to publish, delete, and update STS instances by calling methods that perform an HTTP POST operation on thests-publish/restendpoint. - RestSTSInstanceConfigFactory
-
The
RestSTSInstancePublisherclass calls theRestSTSInstanceConfigFactoryclass to create aRestSTSInstanceConfiginstance.RestSTSInstanceConfigobjects encapsulate all the configuration information of an STS instance, and emit JSON values that you can post to thests-publish/restendpoint to publish an STS instance. - STSPublishContext
-
The sample
STSPublishContextclass specifies the configuration necessary to publish STS instances. The class provides a programmatic method for setting configuration properties. The same configuration properties are available through the AM admin UI under Realms > Realm Name > STS. - CustomTokenOperationContext
-
The sample
CustomTokenOperationContextclass specifies custom validators, token types, and transformations that an STS instance can support.
|
The sample code referenced in this section isn’t compilable because it uses classes that aren’t available publicly. The code provides patterns to developers familiar with the problem domain and is intended only to assist developers who want to programmatically publish STS instances. The sample code imports a number of classes, introducing dependencies.
Classes imported from the AM API can remain in your code,
but other imported classes must be removed and replaced with code
that provides similar functionality in your environment.
For example, the The critical part of the sample code is the idioms that programmatically set all the state necessary to publish an STS instance. |
STS configuration properties
- Deployment Url Element
-
A string that identifies this STS instance.
The Deployment Url Element is a component of the STS instance’s endpoint. For example, if you set
mySTSInstanceas the Deployment Url Element, the STS endpoint would berest-sts/myRealm/mySTSInstance.
General configuration properties
The following are general configuration properties for STS instances:
- Persist Issued Tokens in Core Token Store
-
Indicate whether to enable token persistence in the Core Token Service (CTS).
AM saves all STS-issued tokens to CTS when token persistence is enabled. A token’s lifetime in CTS has the same length as the Token Lifetime property specified for issued tokens.
STS token validation and cancellation capabilities require tokens to be present in CTS. Therefore, if your deployment requires token validation and cancellation, you must enable token persistence.
- Supported Token Transforms
-
The token transformations supported by this STS instance. Token transformations are listed in the AM admin UI using the notation
input-token-type → output-token-type.For each supported token transformation, AM provides an option to invalidate the interim AM session. When transforming a token, the STS creates an AM session. If desired, you can invalidate the AM session after token transformation is complete.
- Custom Token Validators
-
A validator class for a custom token type.
Use the format
CUSTOM-TOKEN-TYPE|custom-validator-classto specify each validator class. For example,CUSTOM|org.mycompany.tokens.myCustomTokenValidator.Learn more in Custom token types.
- Custom Token Providers
-
A provider class for a custom token type.
Use the format
CUSTOM-TOKEN-TYPE|custom-provider-classto specify each provider class. For example,CUSTOM|org.mycompany.tokens.myCustomTokenProvider.Learn more in Custom token types.
- Custom Token Transforms
-
The token transformations that take a custom token type as the input or output token. If you specify a custom token validator or provider, you must also specify a custom token transform.
The custom transform uses three values separated by the vertical bar character | as follows:
-
The input token type
-
The output token type
-
Whether to invalidate the AM session created during token transformation. Use
TRUEto invalidate the session orFALSEto let the session remain valid.
For example, a value of
CUSTOM|SAML2|TRUEconfigures a token transformation that transforms aCUSTOMtoken to a SAML v2.0 assertion and then invalidates the created AM session. -
- STS Instance is running as remote instance
-
Indicate whether the STS instance is running on the AM host or as a separate, remote Java process.
This property determines how calls are made to the STS instance during session token validation.
Default:
trueIf
true, the STS does an outbound HTTP call to itself during session validation. If you set this property tofalse(for example, for an AM instance running in a clustered Docker pod), the STS validates sessions and generates tokens locally, with no HTTP call to thesessionsorsts-genendpoints.
Deployment configuration properties
The following are deployment configuration properties for STS instances:
- Authentication Target Mappings
-
The mappings that define how the STS instance authenticates input tokens.
Each mapping is a set of arguments separated by the vertical bar character | as follows:
-
(Required) The input token type:
USERNAME,OPENAM,X509,OPENIDCONNECT, or a custom token type. -
(Required) The value
service. -
(Required) The name of an authentication tree, which authenticates the input token.
-
(Optional) The name of the header in which you place the token when authenticating to AM. Set this parameter for input
X509andOPENIDCONNECTtokens as follows:-
For
X509input tokens, the format isx509_token_auth_target_header_key=Header Name. -
For
OPENIDCONNECTinput tokens, the format isoidc_id_token_auth_target_header_key=Header Name.
Make sure you specify the header names configured in the Certificate Collector node or OIDC ID Token Validator node properties as the Header Name argument.
This argument can also be used with custom token types to specify the name of a header or cookie from which to obtain a token. When using this argument with a custom token type, its format is determined by the custom validator class that validates the custom token type.
-
The following are example mappings:
-
USERNAME|service|ldapServiceconfigures STS to authenticate inputUSERNAMEtokens to theldapServiceauthentication tree. -
X509|service|certificateAuth|x509_token_auth_target_header_key=ClientCertconfigures STS to obtain an X.509 certificate from theClientCertheader, use it as the input token, and authenticate it using a tree namedcertificateAuththat includes the certificate authentication nodes.
-
- Client Certificate Header Key
-
The name of the header a TLS offloader should use to transmit client certificates.
Token transformations that take an X.509 certificate as the input token require the certificate to be presented using mTLS, so the TLS handshake can validate client certificate ownership.
A common way to obtain the client certificate with mTLS is to use the
jakarta.servlet.request.X509Certificateattribute in the servlet request.However, in deployments with TLS offloading, the offloader must use an HTTP header to transmit the certificate to its destination. This configuration property is the name of the HTTP header whose value contains the certificate.
- Trusted Remote Hosts
-
The IP addresses of hosts trusted to transmit client X.509 certificates in deployments with TLS offloading.
To allow any host to transmit a certificate, specify
anyas the value of this property.As with the Client Certificate Header Key property, configure this property for deployments with TLS offloading.
SAML2 token configuration properties
The following are SAML v2.0 token configuration properties for STS instances:
The properties fall into two categories:
-
Properties that determine content in STS-issued SAML v2.0 assertions. Learn more about SAML v2.0 assertions in Assertions and Protocols for the OASIS Security Assertion Markup Language (SAML) V2.0.
-
Properties that determine how the issued SAML v2.0 assertion is signed or encrypted.
- The SAML2 Issuer Id
-
The IdP entity ID. Populates the
Issuerelement of the SAML v2.0 assertion. - Service Provider Entity Id
-
An audience attribute value. Populates the
AudienceRestrictionsub-element of theConditionselement of the SAML v2.0 assertion.This value is required when issuing Bearer assertions.
- Service Provider Assertion Consumer Service Url
-
A recipient attribute value. Populates the
Recipientsub-element of theSubjectConfirmationelement of the SAML v2.0 assertion.The scheme, FQDN, and port configured must exactly match those of the service provider as they appear in its metadata.
This value is required when issuing Bearer assertions.
- NameIdFormat
-
The name identifier format for the SAML v2.0 assertion.
- Token Lifetime(Seconds)
-
The lifetime, in seconds, for the assertion. The default is 600 seconds.
- Custom Conditions Provider Class Name
-
(Optional) The name of a custom class that generates a
Conditionselement in the SAML v2.0 assertion. Use a custom class when theConditionselement created by the default provider doesn’t meet your needs.The class must implement the
org.forgerock.openam.sts.tokengeneration.saml2.statements.ConditionsProviderinterface, and must be bundled in the AM.warfile. - Customs Subject Provider Class Name
-
(Optional) The name of a custom class that generates a
Subjectelement in the SAML v2.0 assertion. Use a custom class when theSubjectelement created by the default provider doesn’t meet your needs.The class must implement the
org.forgerock.openam.sts.tokengeneration.saml2.statements.SubjectProviderinterface and must be bundled in the AM.warfile. - Custom AuthenticationStatements Class Name
-
(Optional) The name of a custom class that generates an
AuthnStatementelement in the SAML v2.0 assertion. Use a custom class when theAuthnStatementelement created by the default provider doesn’t meet your needs.The class must implement the
org.forgerock.openam.sts.tokengeneration.saml2.statements.AuthenticationStatementsProviderinterface and must be bundled in the AM.warfile. - Custom AttributeStatements Class Name
-
(Optional) The name of a custom class that generates an
AttributeStatementelement in the SAML v2.0 assertion. Use a custom class when theAttributeStatementelement created by the default provider doesn’t meet your needs.The class must implement the
org.forgerock.openam.sts.tokengeneration.saml2.statements.AttributeStatementsProviderinterface and must be bundled in the AM.warfile. - Custom Authorization Decision Statements Class Name
-
(Optional) The name of a custom class that generates an
AuthzDecisionStatementelement in the SAML v2.0 assertion. Use a custom class when theAuthzDecisionStatementelement created by the default provider doesn’t meet your needs.The class must implement the
org.forgerock.openam.sts.tokengeneration.saml2.statements.AuthzDecisionStatementsProviderinterface and must be bundled in the AM.warfile. - Custom Attribute Mapper Class Name
-
The name of a custom attribute mapper class. An attribute mapper generates
attributeelements to be included in the SAML v2.0 assertion.The class must implement the
org.forgerock.openam.sts.tokengeneration.saml2.statements.AttributeMapperinterface and must be bundled in the AM.warfile. - Custom Authentication Context Class Name
-
(Optional) The name of a custom class that generates an
AuthnContextelement in the SAML v2.0 assertion. Use a custom class when theAuthnContextelement created by the default provider doesn’t meet your needs.The class must implement the
org.forgerock.openam.sts.tokengeneration.saml2.statements.AuthnContextMapperinterface and must be bundled in the AM.warfile.By default, AM generates the
AuthnContextelement based on the input token type as follows:-
For input AM tokens:
urn:oasis:names:tc:SAML:2.0:ac:classes:PreviousSession -
For input username tokens and OIDC ID tokens:
urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport -
For input X.509 tokens:
urn:oasis:names:tc:SAML:2.0:ac:classes:X509
-
- Attribute Mappings
-
Configures mappings between SAML v2.0 attribute names (map keys) and AM user profile attributes or session properties to generate
Attributeelements in the SAML v2.0 assertion.AM’s default attribute mapper generates
Attributeelements as follows:-
The map key populates the
Attributeelement’sNameproperty. -
The user profile or session property value populates the
Attributeelement’sAttributeValueproperty.
When specifying map keys in the
Attribute Mappingsproperty, use the following format:[NameFormatURI]|SAML_ATTRIBUTE_NAME.Map values enclosed in quotes are included in the attribute without mapping. Add
;binaryto the end of a map value for attributes with binary values.The following are examples of attribute mappings:
-
EmailAddress=mail -
Address=postaladdress -
urn:oasis:names:tc:SAML:2.0:attrname-format:uri|urn:mace:dir:attribute-def:cn=cn -
partnerID="staticPartnerIDValue" -
urn:oasis:names:tc:SAML:2.0:attrname-format:uri|nameID="staticNameIDValue" -
photo=photo;binary -
urn:oasis:names:tc:SAML:2.0:attrname-format:uri|photo=photo;binary
-
- Sign Assertion
-
Indicate whether to sign the SAML v2.0 assertion.
When enabling assertion signing, you must also specify the KeystorePath, Keystore Password, Signature Key Alias, and Signature Key Password properties.
- Encrypt Assertion
-
Indicate whether to encrypt the entire SAML v2.0 assertion. When enabling assertion encryption:
-
You must also specify the KeystorePath, Keystore Password, and Encryption Key Alias properties.
-
You mustn’t specify the Encrypt Attributes or Encrypt NameID options.
The Encryption Key Alias corresponds to the public key of the service provider that is the intended audience of the assertion. SAML v2.0 assertion encryption works as follows:
-
AM generates a symmetric key.
-
AM encrypts the symmetric key with the recipient’s public key.
-
AM includes the encrypted key in the part of the assertion that isn’t symmetric key-encrypted.
-
The service provider (owner of the corresponding private key) uses the private key to decrypt the symmetric key included in the assertion.
-
The service provider can then use the decrypted symmetric key to decrypt the assertion.
-
- Encrypt Attributes
-
Indicate whether to encrypt the assertion’s attributes only. When specifying this option, don’t specify the Encrypt Assertion option.
When encrypting attributes, you must also specify the KeystorePath, Keystore Password, and Encryption Key Alias properties.
- Encrypt NameID
-
Indicate whether to encrypt the assertion’s NameID only. When specifying this option, don’t specify the Encrypt Assertion option.
When encrypting the NameID, you must also specify the KeystorePath, Keystore Password, and Encryption Key Alias properties.
- Encryption Algorithm
-
The encryption algorithm to use when encrypting the entire assertion, the assertion’s attributes, or the NameID.
- Encryption Algorithm Strength
-
The encryption algorithm strength to use.
- Key Transport Algorithm
-
The algorithm used to encrypt the symmetric encryption key when SAML v2.0 token encryption is enabled. Possible values are:
-
http://www.w3.org/2001/04/xmlenc#rsa-oaep-mgf1p. -
http://www.w3.org/2009/xmlenc11#rsa-oaep.When this algorithm is configured, AM will use the Mask Generation Function Algorithm property (Configure > Global Services > Common Federation Configuration) to encrypt the transport key.
Find a list of supported mask generation function algorithms in Algorithms.
-
http://www.w3.org/2001/04/xmlenc#rsa-1_5.
-
- KeystorePath
-
The path to the JKS keystore containing the key aliases for encrypting and signing SAML assertions. Use an absolute path or a location in the AM classpath.
AM provides a JKS keystore with demo keys,
/path/to/am/security/keystores/keystore.jks. Learn more in Secrets, certificates, and keys. - Keystore Password
-
The password used to decrypt the keystore.
- Encryption Key Alias
-
The key alias in the keystore that holds the service provider’s X.509 certificate for this STS instance. This key alias is used to encrypt assertions.
- Signature Key Alias
-
The private key alias in the keystore used to sign assertions.
- Signature Key Password
-
The password of the private key used to sign the assertion.
OpenID Connect token configuration properties
The following are OIDC token configuration properties for STS instances:
The properties fall into two categories:
-
Properties that determine content in the issued OIDC ID token. Learn more about OIDC ID tokens in the OpenID Connect Core 1.0 specification.
-
Properties that determine how the issued token is signed.
An STS instance configured to issue OIDC tokens
models the relationship between an OIDC token provider and relying party.
In other words, an STS instance issues tokens for a particular OAuth 2.0 client.
The tokens contain aud and azp claims for the OAuth 2.0 client,
and signing key state corresponding to a token provider.
In this model, when users call an STS instance to generate an OIDC ID token, the process is analogous to the exchange between an OAuth 2.0 authorization server and resource owner following the initial redirection from an OAuth 2.0 client initiating the implicit flow. The STS instance returns the OIDC ID token that corresponds to the authorization server’s authentication of the resource owner.
AM authenticates the token specified as the input_token_state for the token transformation
Implicit in this model is the notion that an OIDC ID token has value outside of an OAuth 2.0 flow, and that an OAuth 2.0 client, as a relying party, could be generalized as a SAML v2.0 service provider. The ID token isn’t simply an an entity-provided verifiable authorized access to a specific resource, but rather a generic service provider that consumes an OIDC ID token to authenticate and authorize the subject asserted by the token.
Therefore, the configuration of an STS instance that issues OIDC ID tokens contains information that defines the token provider and relying party.
The nonce claim in the ID token isn’t a configuration property of an STS instance.
STS consumers requesting an output OIDC token
provide a nonce value when making token transformation requests.
|
- OpenID Connect Token Provider ID
-
The OIDC token provider issuer ID. Populates the
issclaim of the ID token. - Token Lifetime(Seconds)
-
The ID token’s expiration in seconds. Populates the
expclaim of the ID token. - Token Signature Algorithm
-
An HMAC or RSA algorithm used to sign ID tokens.
- Public Key Reference Type
-
Indicate how public keys should be referenced in issued ID tokens signed with RSA. OIDC ID tokens are issued as JSON web tokens (JWTs). Tokens can reference RSA public keys as JSON web keys (JWKs), or not at all.
Used with RSA signing.
- KeyStore Location
-
The path to the JKS keystore containing the key alias for signing the ID token. Use an absolute path or a location in the AM classpath.
Used with RSA signing.
AM provides a JKS keystore with demo keys,
/path/to/am/security/keystores/keystore.jks. Learn more about keystores in Secrets, certificates, and keys. - KeyStore Password
-
The password used to decrypt the keystore.
Used with RSA signing.
- KeyStore Signing Key Alias
-
The private key alias in the keystore used to sign the ID token.
Used with RSA signing.
- Signature Key Password
-
The password of the private key alias used to sign the ID token.
Used with RSA signing.
- Client secret
-
The secret shared between the client and the ID token generator used to sign the ID token.
Used with HMAC signing.
- Issued Tokens Audience
-
The intended audience for the ID token. Populates the
audclaim of the ID token. - Authorized Party
-
The party to which the ID token is being issued. Populates the
azpclaim of the ID token. - Claim Map
-
The additional claim entries to be inserted into the ID token.
The entries use the format
claim-name=user-profile-attribute. When issuing the ID token, AM populates the claim value with the value of the attribute in the authenticated user’s profile.For example, suppose the
Claim mapproperty had an entry with the valueemail=mail. A generated OIDC ID token for user Sam Carter would contain the claim"email":"scarter@example.com"if themailattribute in Sam Carter’s user profile had the valuescarter@example.com. - Custom Claim Mapper Class
-
The name of a custom claim mapper class. A claim mapper generates additional claims to be included in the OIDC ID token.
The class must implement the
org.forgerock.openam.sts.tokengeneration.oidc.OpenIdConntectTokenClaimMapperinterface and must be bundled in the AM.warfile. - Custom Authn Context Mapper Class
-
The name of a custom class that generates an
acrclaim in the OIDC ID token. Anacrclaim indicates which authentication context class was satisfied by the authentication of the principal asserted in the OIDC ID token. Theacrclaim is optional and isn’t included in the generated ID token by default.The class must implement the
org.forgerock.openam.sts.rest.token.provider.oidc.OpenIdConnectTokenAuthnContextMapperinterface and must be bundled in the AM.warfile. - Custom Authn Methods References Mapper Class
-
The name of a custom class that generates an
amrclaim in the OIDC ID token. Anamrclaim indicates which authentication methods were used to authenticate the principal asserted in the OIDC ID token. Theamrclaim is optional and isn’t included in the generated ID token by default.The class must implement the
org.forgerock.openam.sts.rest.token.provider.oidc.OpenIdConnectTokenAuthMethodReferencesMapperinterface and must be bundled in the AM.warfile.
Custom token types
AM supports token transformations to and from a variety of token types, including username, SAML v2.0, OIDC, and X.509. In addition to these core token types, STS instances can use custom token types as the input or output token, or both, in a token transformation. When you configure an STS instance to support a token transformation that takes a custom token type, you can also configure a custom validator and provider class for the custom token type. AM uses custom validator classes to validate custom tokens and custom provider classes to produce custom tokens.
|
Learn about downloading and building PingAM sample source code in the following Knowledge Base article: How do I access and build the sample code provided for PingAM?. You can find the STS code examples under |
Specify custom token validator and provider classes in the AM admin UI by configuring the Custom Token Validators and Custom Token Providers properties under Realms > Realm Name > STS > STS Instance Name.
A custom validator class can be used in transformations that produce standard STS output tokens, such as SAML v2.0 tokens or OIDC tokens, and in transformations that produce custom output token types.
A custom provider class can be used in token transformations that take standard STS input tokens, such as username tokens or AM SSO tokens, and in transformations that take custom input token types.
Before an STS instance can use a custom token type validator or provider class,
you must bundle the class into the AM .war file and restart AM.
AM invokes a single instance of a validator or provider class to run all concurrently dispatched token transformations that use the custom token type. Because there is only a single instance of the class, you must code custom validator and provider classes to be thread-safe.
Develop custom token type validator classes
To create a custom token type validator class,
implement the org.forgerock.openam.sts.rest.token.validator.RestTokenTransformValidator class.
Custom token type validator classes implement the validateToken method.
This method takes a RestTokenValidatorParameters object as input.
Note that the generic type of RestTokenValidatorParameters is org.forgerock.json.fluent.JsonValue.
As a result of using this type, custom validator classes can access the JSON representation of the input token
passed to the STS instance in the input_token_state JSON key.
The validateToken method returns
an org.forgerock.openam.sts.rest.token.validator.RestTokenTransformValidatorResult object.
At a minimum, this object contains the AM SSO token corresponding to the validated principal.
It can also contain additional information specified as a JSON value,
allowing a custom validator to pass extra state to a custom provider in a token transformation.
Develop custom token type provider classes
To create a custom token type provider class,
implement the org.forgerock.openam.sts.rest.token.provider.RestTokenProvider class.
Custom token type provider classes implement the createToken method.
This method takes an org.forgerock.openam.sts.rest.token.provider.CustomRestTokenProviderParameters object as input.
This object gives the custom provider access to the following information:
-
The principal returned by the
RestTokenTransformValidator -
The AM SSO token corresponding to the validated principal
-
Any additional state returned in the
RestTokenValidatorResultobject -
The type of input token validated by the
RestTokenTransformValidatorin the token transformation -
The
JsonValuecorresponding to this validated token, as specified by theinput_token_stateobject in the transformation request -
The
JsonValuecorresponding to thetoken_output_stateobject specified in the token transformation request (which can provide additional information pertinent to the creation of the output token)
The createToken method returns a string representation of the custom token
in a format that can be transmitted across HTTP in JSON.
It should be base64-encoded if binary.
Use custom token type validators and providers
This section provides an example of how to use custom token type validators and providers.
The example assumes that you already configured a token transformation by completing the following tasks:
-
Implementing the
RestTokenTransformValidatorinterface to create a custom token type validator -
Implementing the
RestTokenProviderinterface to create a custom token type provider -
Bundling the two classes into the AM
.warfile -
Restarting AM
-
Publishing an STS instance with a custom token type named
CUSTOM, specifying the custom validator and provider classes in the instance’s configuration
To transform a CUSTOM token to an OIDC token, you might specify a JSON payload similar to the following:
{
"input_token_state":
{
"token_type": "CUSTOM",
"extra_stuff": "very_useful_state"
},
"output_token_state":
{
"token_type": "OPENIDCONNECT",
"nonce": "1234",
"allow_access": true
}
}With the preceding JSON payload,
AM passes a JsonValue instance to the validateToken method of the custom token type validator class:
{
"token_type": "CUSTOM",
"extra_stuff": "very_useful_state"
}To transform a username token to a CUSTOM token, you might specify a JSON payload similar to the following:
{
"input_token_state":
{
"token_type": "USERNAME",
"username": "unt_user17458687",
"password": "password"
},
"output_token_state":
{
"token_type": "CUSTOM",
"extra_stuff_for_custom": "some_useful_information"
}
}With the preceding JSON payload, AM passes the following information
to the createToken method of the custom token type provider:
-
The principal returned by the
USERNAMEtoken validator:unt_user17458687. -
The AM SSO token corresponding to this authenticated principal.
-
Additional state returned by the token validator, if any. Because the
USERNAMEtoken validator doesn’t return any additional state, the additional state for this example would be null. -
The input token type:
CUSTOM -
A
JsonValuerepresentation of the following:{ "token_type": "USERNAME", "username": "unt_user17458687", "password": "password" }json -
A
JsonValuerepresentation of the following:{ "token_type": "CUSTOM", "extra_stuff_for_custom": "some_useful_information" }json
To transform a CUSTOM token to a CUSTOM token, you might specify a JSON payload similar to the following:
{
"input_token_state":
{
"token_type": "CUSTOM",
"extra_stuff": "very_useful_state"
},
"output_token_state":
{
"token_type": "CUSTOM",
"extra_stuff_for_custom": "some_useful_information"
}
}The input to the custom validator and provider would be similar to the preceding examples,
with the possible addition of any additional state that the custom validator returned from the validateToken method.