Sign on with MFA using push notifications
Description
Estimated time to complete: 30 minutes
In this use case, you authenticate a user with multi-factor authentication (MFA) by setting up the PingID app for push notifications on a smartphone. The push notifications are sent from Advanced Identity Cloud to the PingID app as an additional factor when signing on.
Goals
After completing this use case, you’ll know how to do the following:
-
Configure services for push notifications in the AM native admin console.
-
Capture and validate a username and password.
-
Configure and register an end user’s device with their user profile in Advanced Identity Cloud.
-
Create a journey to enforce MFA at sign on.
-
Provide recovery codes to end users if they lose their device.
Prerequisites
Before you start work on this use case, ensure you have these prerequisites:
-
A basic understanding of these Advanced Identity Cloud concepts:
-
Realms
-
The AM native admin console and hosted pages
-
Journeys
-
Nodes
-
-
Access to your development environment as a tenant administrator
-
An identity in Advanced Identity Cloud to test the journey (you might need to create this)
-
An Android or iOS smartphone with access to the internet
-
A Ping Identity Backstage account
Tasks
Task 1: Sign on and configure the push service
-
Sign on to the Advanced Identity Cloud admin console as a tenant administrator.
-
In the left menu pane, select Native Consoles > Access Management.
The realm overview for the Alpha realm opens.
-
Select Services.
-
Click + Add a Service.
-
Create the push service configuration:
-
Select ForgeRock Authenticator (Push) Service in the service type drop-down list.
-
Click Create.
-
Click Save Changes to accept the default settings.
The default settings don’t encrypt the device metadata stored in user profiles. This use case accepts the default settings for simplicity. Learn more in Configure the ForgeRock Authenticator (Push) service.
-
Task 2: Create Push service credentials in Backstage
Advanced Identity Cloud uses an external AWS service to send push notifications. Its configuration requires access keys and other metadata. As a Ping Identity customer, you have streamlined access to the required metadata:
-
In a new tab, sign on to Backstage.
-
In the top right corner, click your profile icon > Backstage Account.
-
On the left menu pane, select Service Credentials.
-
Under Push Notifications AWS Credentials, click Create.
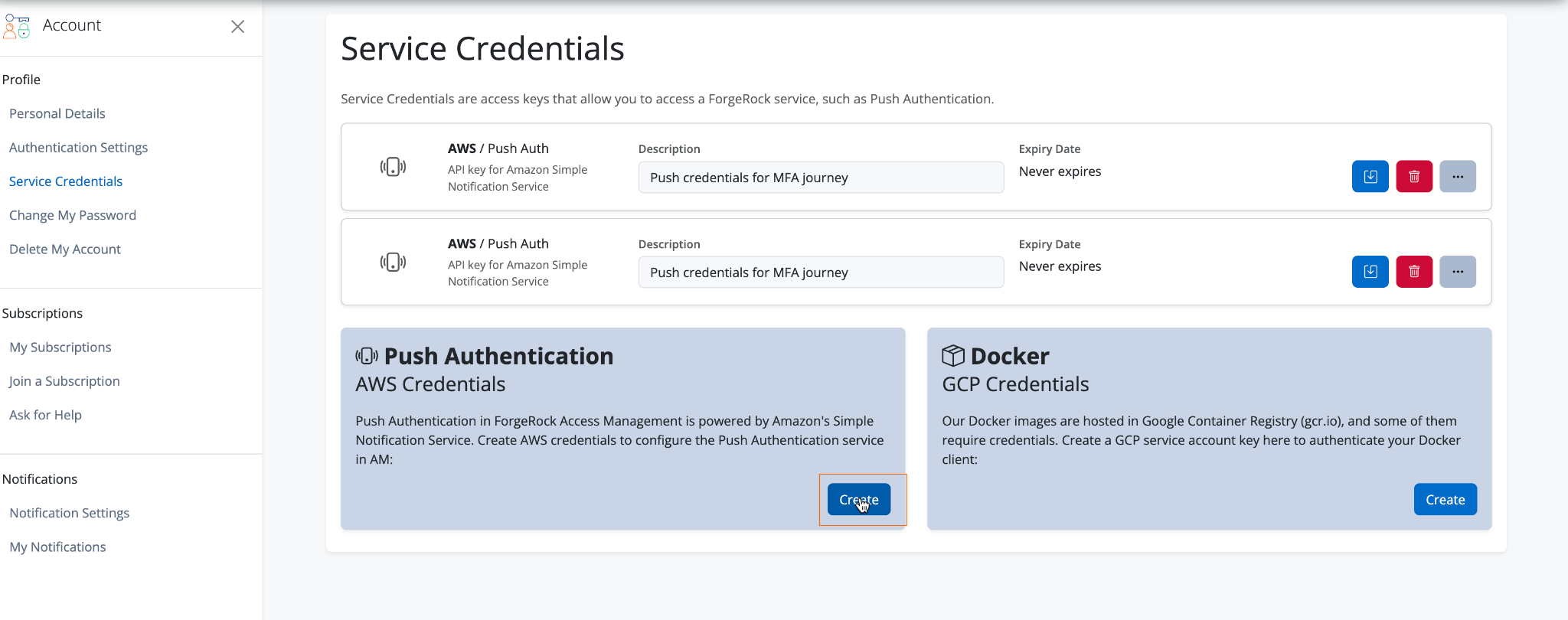
-
In the Mobile Application field, select
PingID. -
In the Description field, enter
Push credentials for MFA journey. -
Click Create.
-
Click Download as JSON.
-
Click Close.
-
Close the Backstage tab.
Task 3: Configure the Push Notification service in the AM native admin console
-
Click back to the tab that displays the AM native admin console.
-
Select Services.
-
Click + Add a Service.
-
To configure the Push Notification service, select Push Notification Service in the service type drop-down list.
-
Open the JSON file you downloaded in step 8.
-
Enter the fields from the JSON file into the fields that display:
Don’t enter the quotes that surround the JSON value. Field in AM native admin console Field in JSON file Description SNS Access Key ID
accessKeyId
The generated Key ID; the
"accessKeyId"in the JSON.SNS Access Key Secret
accessKeySecret
The generated Secret; the
"accessKeySecret"in the JSON.To make this configuration compatible with the promotion process, create an ESV secret for the AWS Access Key Secret and replace the literal value with an ESV placeholder.
Learn more in this KB article.
SNS Endpoint for APNS
APNS
The generated APNS; the
"APNS"in the JSON. Used to send push notifications to the Apple Push Notification Service (APNS).SNS Endpoint for GCM
GCM
The generated GCM; the
"GCM"in the JSON. Used to send push notifications to Android devices using Google Cloud Messaging (GCM). -
Click Create.
-
Click Save Changes.
-
Close the AM native admin console tab.
-
Click back to the Advanced Identity Cloud admin console tab.
Task 4: Create the MFA using push notifications journey
Configure journey options
-
In the Advanced Identity Cloud admin console, go to Journeys > Journeys.
-
Click + New Journey.
-
Configure options for the new journey:
Field Value Description Name
Enter
Login with Push MFAA name to display in the journeys list.
Identity Object
Select
Alpha Realm - UsersThe type of object that this journey authenticates.
Description
Enter
A login journey with MFA using push notificationsDescription of the journey.
Override theme
Do not enable
Lets you provide a unique UI for this journey.
Default journey for end users
Do not enable
Lets you designate this journey as the default journey for your Advanced Identity Cloud environment.
-
Click Save. The journey editor displays.
To save your progress, periodically click Save in the top right of the journey editor. Failure to do this results in losing your work if the page reloads or if you lose your network connection. 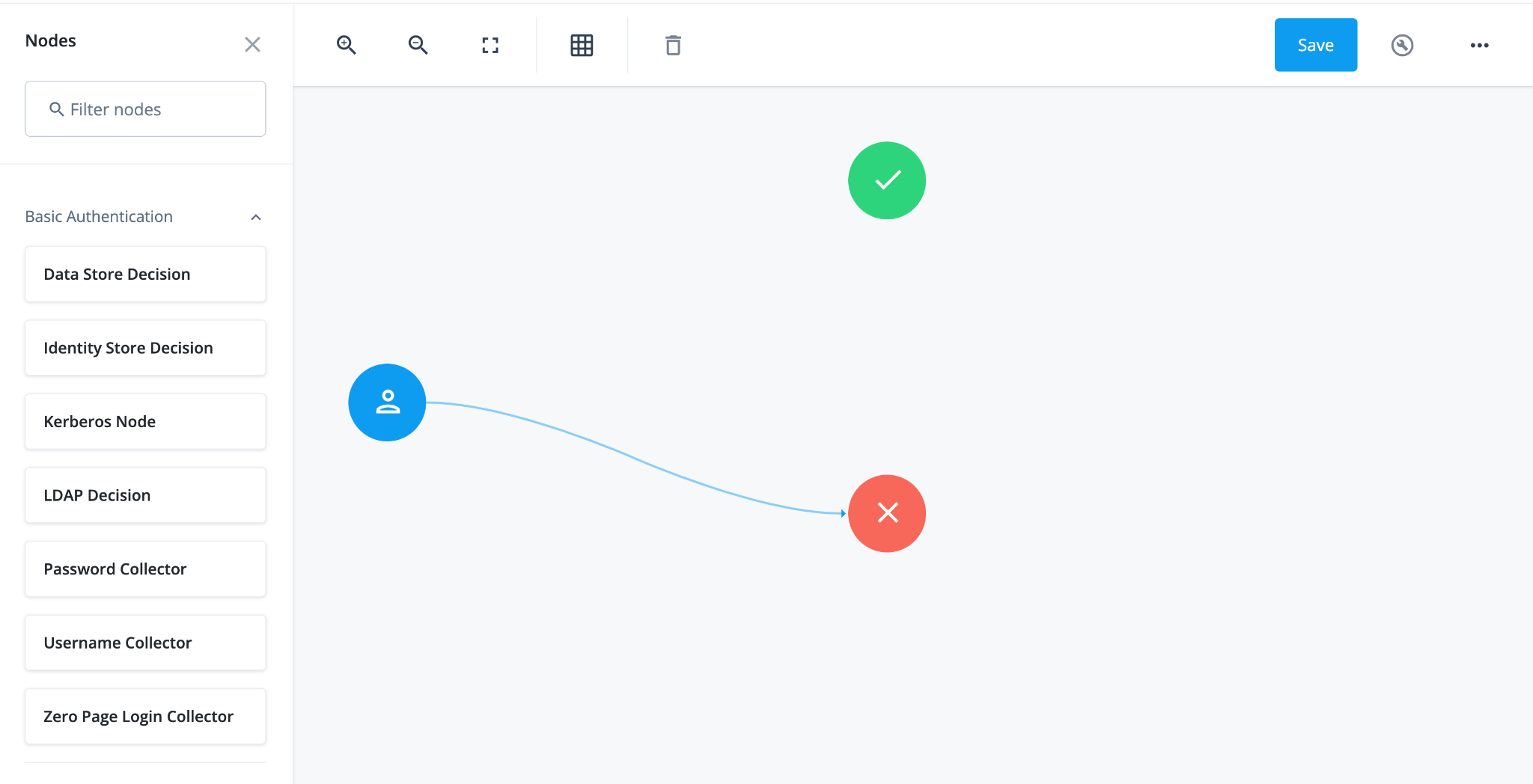
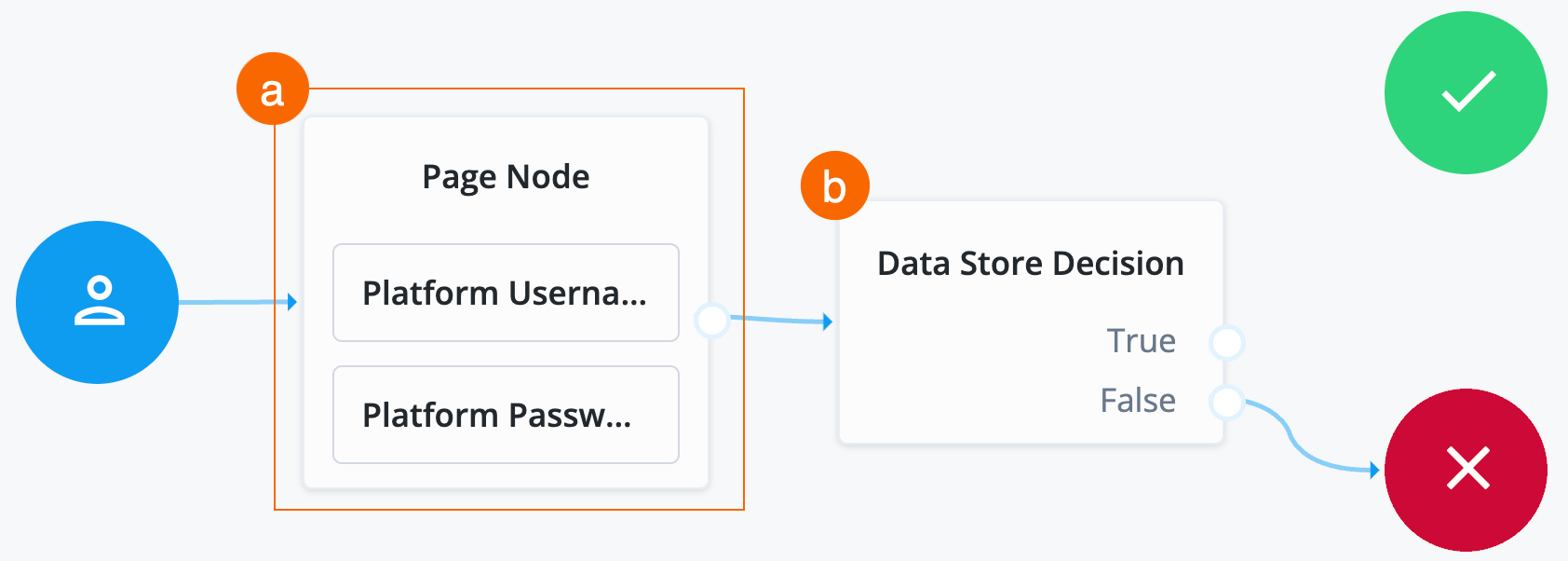
Collect username, password, and validate login on one page
-
In the top left search bar, enter
Page Node.A Page node combines multiple nodes that request input into a single page for display to the user. In this case, it allows the username and password boxes to display to the end user on the same page.
-
Drag the Page Node box from the left side of the journey editor to the right side (the canvas).
-
Connect the start (person) icon to the Page Node by selecting the icon and dragging it into the left side (input) of the Page Node. An arrow shows the flow of the journey from the person icon into the Page Node.
When you connect nodes together, the arrows show the flow of the journey from node to node.
-
Search for the Platform Username node and drag it into the Page Node.
The Platform Username node prompts the end user to enter their username and stores it in a configurable state attribute.
-
Search for the Platform Password node and drag it into the Page Node.
The Platform Password node prompts the end user to enter their password and stores it in a configurable state attribute.
-
Search for the Data Store Decision node and drag it to the right of the Page Node.
The Data Store Decision node verifies that the username and password values match those in the data store configured for the realm.
-
Connect the right side of the Page Node (the outcome) into the left side of the Data Store Decision node (input).
-
Connect the
Falseoutcome of the Data Store Decision node into the Failure node (red X circle). -
In the top right of the journey editor, click Save.
|
When connecting the outcome of a node to another node, make sure there is a hand icon present on the node you’re connecting to. Click to display an example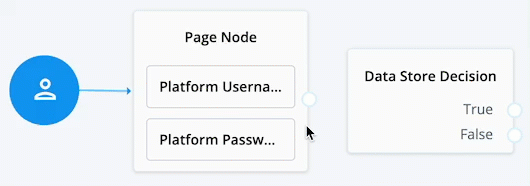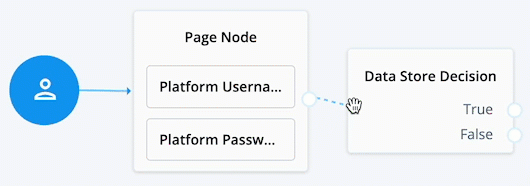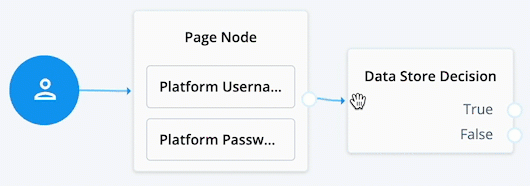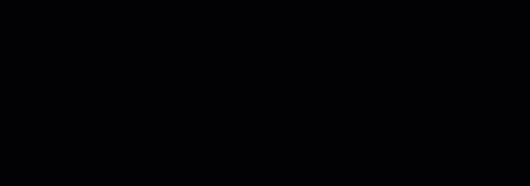
|
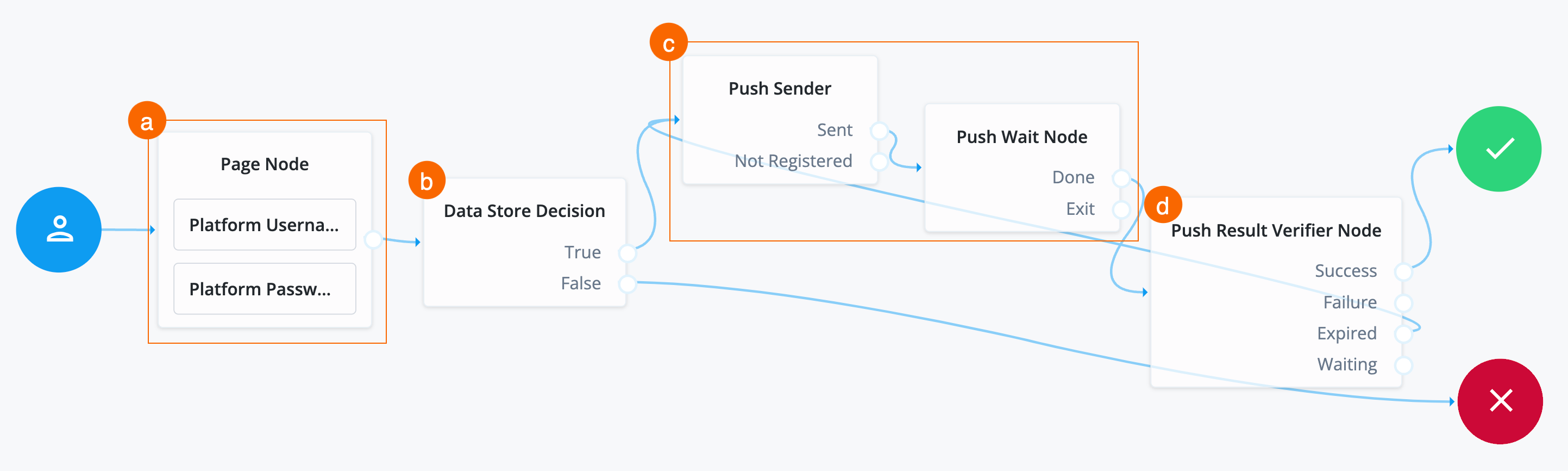
Send and verify push notifications
The journey goes down this path when the end user has a device registered with their Advanced Identity Cloud profile.
-
Search for the Push Sender node and drag it to the right of the Data Store Decision node on the canvas.
-
Connect the
Trueoutcome of the Data Store Decision node to the input of the Push Sender node. -
Click the Push Sender node and configure its options:
Field Value Description Message Timeout
Do not modify
Specifies the number of milliseconds the push notification message remains valid.
User Message
Do not modify
Specifies an optional message to send to the end user on their device.
Remove ‘skip’ option
Enable this property
Enable this option in the node to make the push authentication mandatory.
When disabled, the user can skip the push authentication requested by the node and evaluation continues along the
Skippedoutcome path.Share Context Info
Enable this property
Enable this option to include context data, such as remoteIp, userAgent, and location, in the notification payload.
Custom Payload Attributes
Do not modify
Include shared state objects in the message payload sent to the client. The size of the payload must not exceed 3 Kb or a
NodeProcessExceptionis thrown.Push Type
Select Display Challenge Code.
The type of push authentication the user must perform on their device to continue the journey. Select one of the following types:
-
Tap to accept: Requires the user to tap to accept.
-
Display Challenge Code: Requires the user to select one of three numbers displayed on their device. This selected number must match the code displayed in the browser for the request to be verified.
-
Use Biometrics to Accept: Requires the user’s biometric authentication to process the notification.
Research shows users might accept a push authentication without fully checking if it’s legitimate. To reduce the chances of a user accepting a malicious push authentication attempt, select Display Challenge CodeorUse Biometrics to Accept.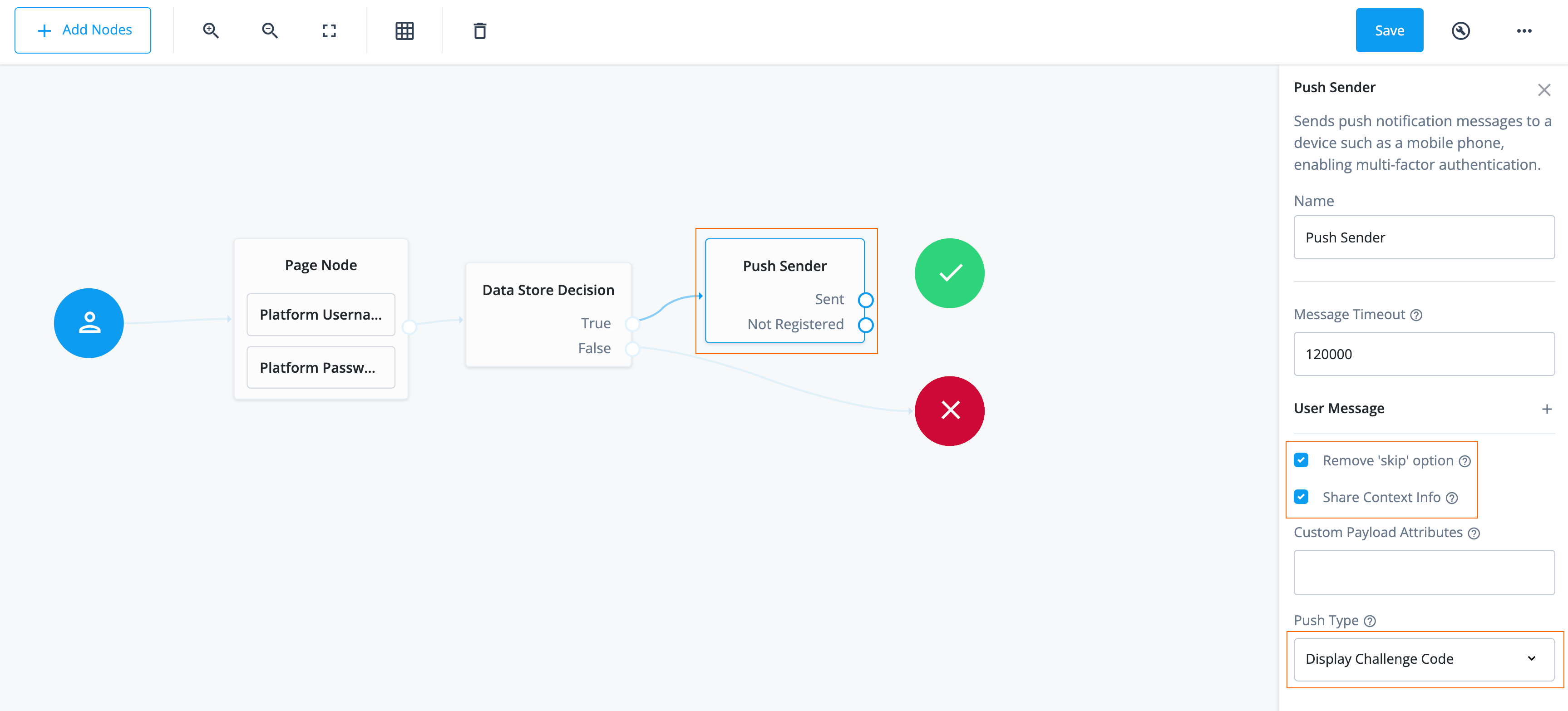
-
-
Search for the Push Wait Node and drag it to the right of the Push Sender node in the canvas.
To let the end user respond to the push notification, the Push Wait node pauses authentication for the specified number of seconds while processing a push authentication request.
-
Connect the
Sentoutcome of the Push Sender node to the input of the Push Wait Node. -
Search for the Push Result Verifier Node and drag it to the right of the Push Wait Node.
The Push Result Verifier node works with the Push Sender node to validate the user’s response to a previously sent push notification message.
-
Connect the
Doneoutcome of the Push Wait Node to the input of the Push Result Verifier Node. -
Connect the outcomes of the Push Result Verifier Node to various nodes:
Outcome path Target node SuccessSuccess node (green check mark)
FailureFailure node (red X)
ExpiredPush sender node
WaitingPush Wait Node
-
Click Save.
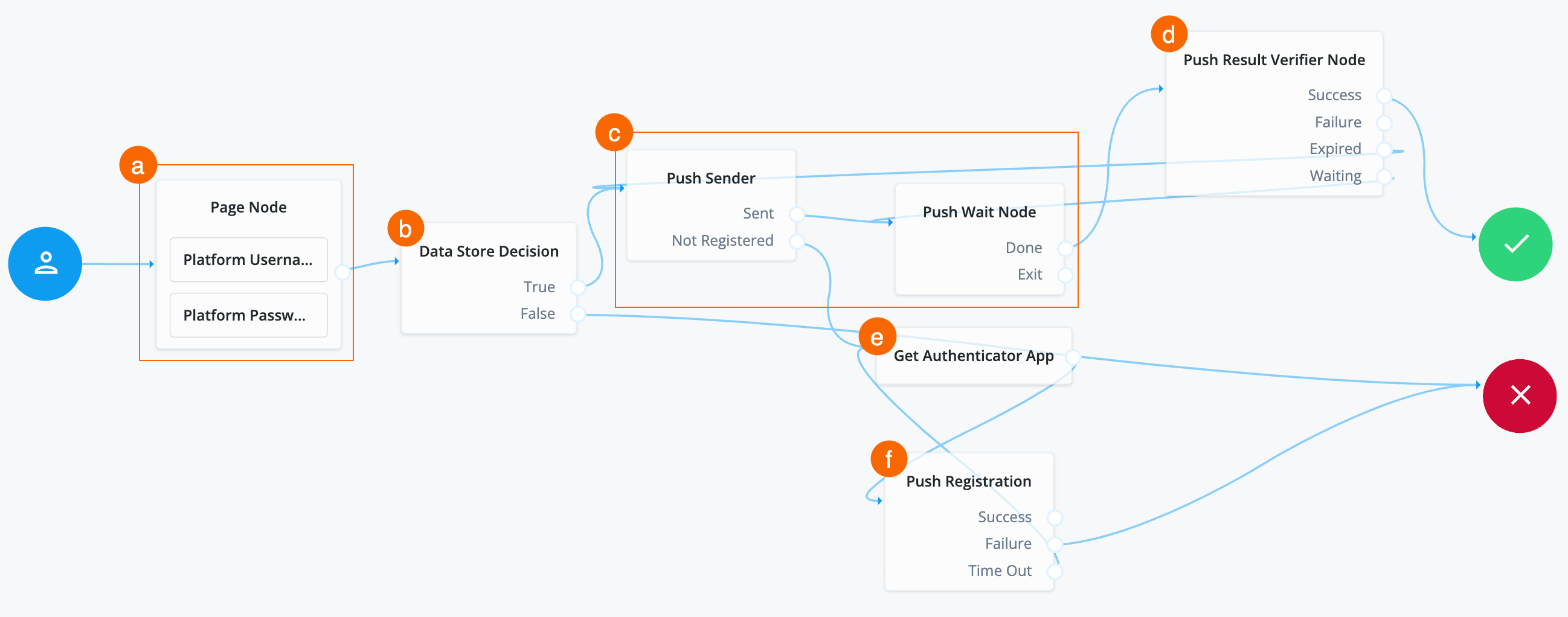
Register device (smartphone) with Advanced Identity Cloud profile
The journey goes down this path when the Push Sender node goes to the Not Registered outcome, signaling that the end user doesn’t have a device registered with their Advanced Identity Cloud profile.
-
Search for the Get Authenticator App node and drag it under the Push Sender node.
The Get Authenticator App node displays information to obtain the PingID app from the Apple App Store or the Google Play Store.
Make sure the URLs in the Get Authenticator App node configuration correctly link to the PingID app on the Apple App Store and Google Play. -
Connect the
Not Registeredoutcome of the Push Sender node to the input of the Get Authenticator App node. -
Search for the Push Registration node and drag it to the right of the Get Authenticator App node.
Make sure the value in the Issuer field in the Push Registration node configuration is Ping. -
Connect the outcome of the Get Authenticator App node to the input of the Push Registration node.
-
Connect the
Failureoutcome of the Push Registration node to the Failure node. -
Connect the
Time Outoutcome of the Push Registration node to the Get Authenticator App node. -
Click Save.
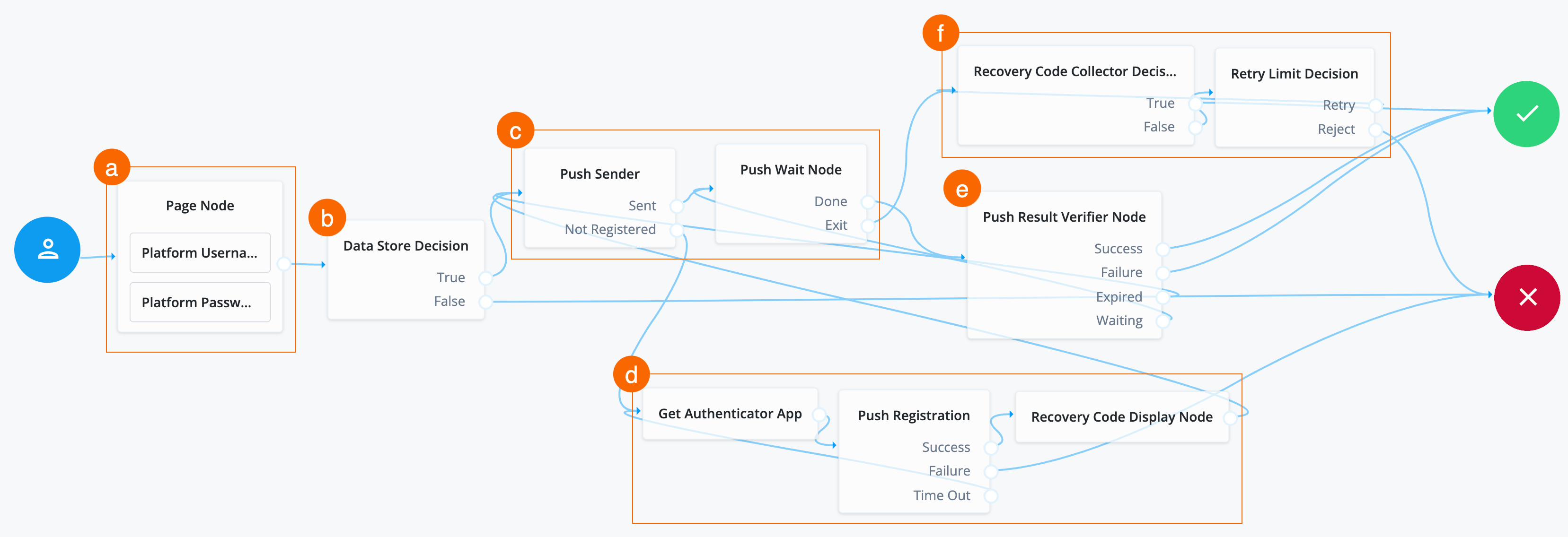
Add recovery codes and send push notification to the new device
-
Search for the Recovery Code Display Node and drag it to the right of the Push Registration node.
If the user’s device is lost, the Recovery Code Display node retrieves generated recovery codes from the transient state and presents them to the user for safekeeping. The codes can be used to authenticate if a registered device is lost or stolen.
-
Connect the
Successoutcome of the Push Registration node as input to the Recovery Code Display Node. -
Connect the outcome of the Recovery Code Display Node as input to the Push Sender node.
-
Search for the Recovery Code Collector Decision node and drag it to the right of the Push Wait Node.
In the event the end user doesn’t have access to or has lost their device, the Recovery Code Collector Decision node lets the end user authenticate with the recovery code provided in the Recovery Code Display node.
-
Connect the
Exitoutcome of the Push Wait Node as input to the Recovery Code Collector Decision node. -
Connect the
Trueoutcome of the Recovery Code Collector Decision node to the Success node. -
Search for the Retry Limit Decision node and drag it to the right of the Recovery Code Collector Decision node.
The Retry Limit Decision node permits the specified number of passes through to the Retry outcome path before continuing evaluation along the Reject outcome path. In this case, it lets the end user reenter their recovery codes up to three times before the journey goes to the Failure node.
-
Connect the
Falseoutcome of the Recovery Code Collector Decision node as input to the Retry Limit Decision node. -
Connect the
Retryoutcome of the Retry Limit Decision node as input to the Recovery Code Collector Decision node. -
Connect the
Rejectoutcome of the Retry Limit Decision node to the Failure node. -
Click Save. You’ve now configured the journey successfully.
Task 5: Check journey path connections
The MFA using push notifications journey uses many nodes. Use the following
table to compare the outcomes of each node and to validate that you wired the
journey correctly.
Many nodes can have more than one outcome. "→" denotes that a node only has one outcome path.
| Source node | Outcome path | Target node |
|---|---|---|
Start (person icon) |
→ |
Page Node |
Page Node containing:
|
→ |
Data Store Decision |
Data Store Decision |
True |
Push Sender |
False |
Failure |
|
Push Sender |
Sent |
Push Wait Node |
Not Registered |
Get Authenticator App |
|
Push Wait Node |
Done |
Push Result Verifier Node |
Exit |
Recovery Code Collector Decision |
|
Push Result Verifier Node |
Success |
Success |
Failure |
Failure |
|
Expired |
Push Sender |
|
Waiting |
Push Wait Node |
|
Recovery Code Collector Decision |
True |
Success |
False |
Retry Limit Decision |
|
Retry Limit Decision |
Retry |
Recovery Code Collector Decision |
Reject |
Failure |
|
Get Authenticator App |
→ |
Push Registration |
Push Registration |
Success |
Recovery Code Display Node |
Failure |
Failure |
|
Timeout |
Get Authenticator App |
|
Recovery Code Display Node |
→ |
Push Sender |
Validation
Now that you’ve configured the ForgeRock Authenticator push service, the push notifications for Advanced Identity Cloud, and created your journey, you’re ready to validate your journey.
Before validating, make sure you’ve created a test user and have access to an Android or iOS smartphone.
Steps
In the journey you created, there are various paths the end user can go down, depending on their actions and the information in their user profile. For example, if the end user has a device (smartphone) registered with their profile, the journey doesn’t display the page to download the PingID app or to register a device. On the other hand, if the end user doesn’t approve the push notification in the specified time (defined in the Push Wait node in the journey), the journey prompts the user to enter a recovery code.
To demonstrate the device registration process and push notification approval, this validation explores the path of an end user who doesn’t have the PingID app on their smartphone and doesn’t have a smartphone registered with their user profile in Advanced Identity Cloud.
-
Get a URL you can use to test the journey:
-
Sign on to the Advanced Identity Cloud admin console as an administrator.
-
Go to Journeys > Journeys.
-
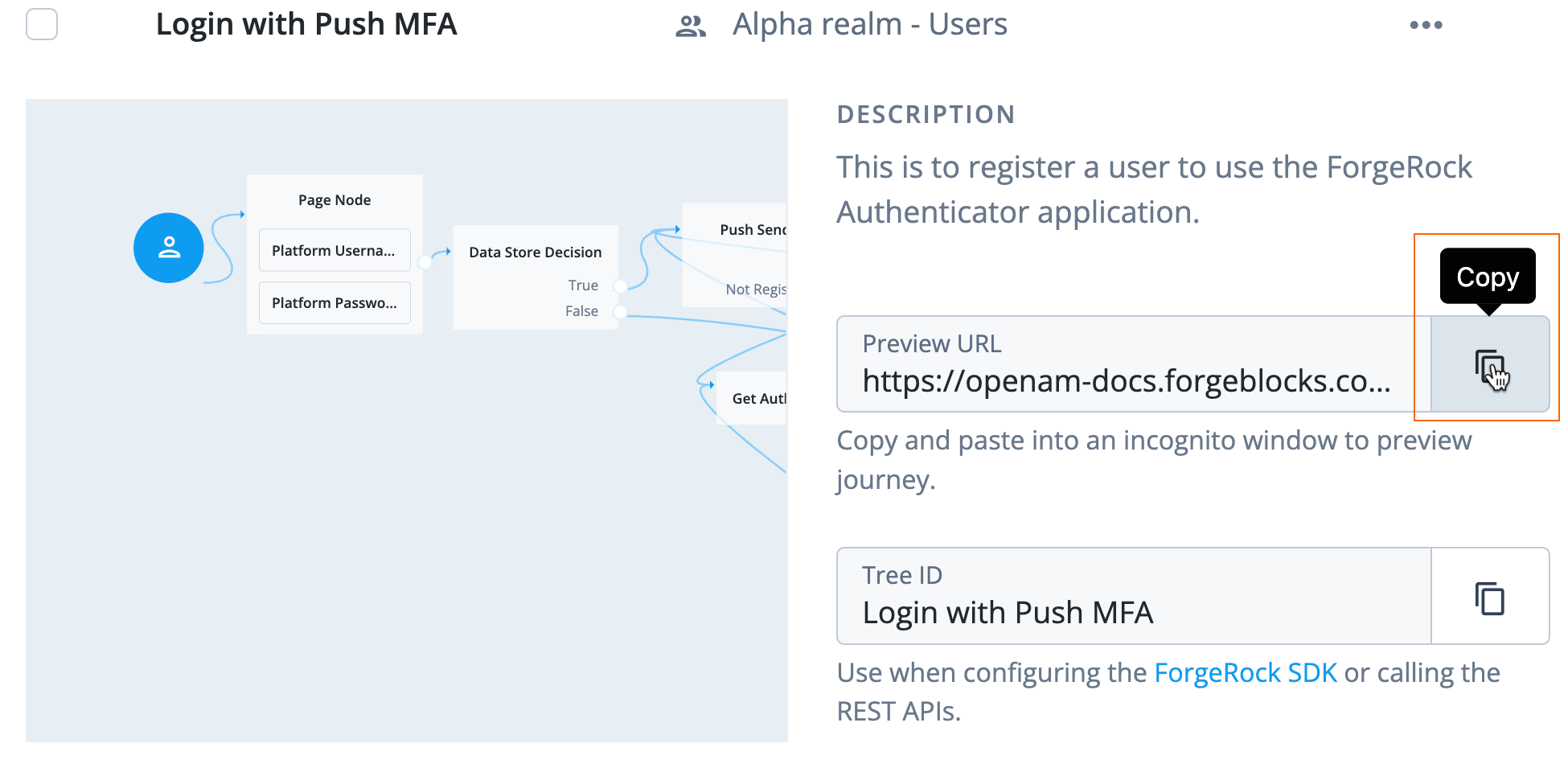
Select the journey you created, Login with Push MFA. A journey preview page opens.
-
Click the copy icon next to the Preview URL, a URL you can use to test a journey as an end user:
-
-
Sign on to the hosted account pages:
-
Paste the URL into an incognito window.
Use incognito mode for testing to avoid caching issues, and so that any current sessions you have don’t interfere with your test.
-
Enter the test user’s username and password.
-
Click Next.
A page opens prompting you to download the PingID app.
-
-
Download the PingID app:
-
Click the Apple App Store or Google Play Store link, depending on which smartphone you have.
-
Download the PingID app.
-
After you’ve downloaded the app, click Continue. A page opens prompting you to scan a QR code.
-
-
Register your user profile with your smartphone and copy recovery codes:
-
Open the PingID app on your smartphone.
-
Tap the blue Scan icon at the bottom of the screen.
-
Scan the QR code that displays in your browser window with your smartphone’s camera.
A new profile for the test user appears in the PingID app.
-
The browser displays a list of recovery codes. Copy these codes and save them in a secure location. You can use them to sign on if you lose access to your device.
-
Click Done.
A push notification is sent to your smartphone.
-
-
Approve the push notification:
-
On your device, tap the number that matches the code displayed in the browser.
-
Tap Done.
You should now be signed on to the hosted account pages.
-
-
Sign out of the hosted account pages:
-
Click the test user’s name in the top right corner of the hosted account pages.
-
Select Sign Out.
You’re redirected to a sign-in page. This page differs from the journey you created, Login with MFA Push. The page you’re directed to when you sign out is the default journey in the realm. Learn how to set the default journey in "Default end-user journey" in Journeys.
-
Explore further
Reference material
| Reference | Description |
|---|---|
Realms are administrative units that group configurations and identities together. Realms let you manage different sets of identities and applications within the same Advanced Identity Cloud tenant. Each realm is fully self-contained and operates independently of other realms within a tenant. |
|
Get to know the admin interfaces; Advanced Identity Cloud admin console, AM native admin console, and IDM admin console. |
|
Conceptual information on journeys and their purpose in Advanced Identity Cloud. |
|
Learn about the configurable nodes Advanced Identity Cloud offers for use in journeys. |
|
Integrate third-party services into your applications or journeys with marketplace nodes. |
|
Manage, group, and assign privileges to identities. |
|
Customize the look and feel of the hosted pages. This is used when you’re using the Advanced Identity Cloud hosted pages as your UX option. |
|
A more in-depth reference on the configuration properties and the steps to create a journey with push notifications. |