Secure identity data
Some managed objects contain data which you want to secure. Examples of sensitive data include:
-
Passwords
-
Authentication questions
-
Credit card numbers
-
Social security numbers
There are two ways to secure a managed object’s sensitive data properties: reversible encryption and salted hashing. To configure encryption or hashing, update the managed object’s configuration at the openidm/config/managed endpoint.
Reversible encryption
Reversible encryption secures your data by encrypting it with a key. It should be used in cases where you may need to decrypt the sensitive data in order to synchronize it or provide it to another system.
Encrypt and decrypt properties using the IDM admin console
To encrypt or decrypt a property of a managed object using the IDM admin console:
-
On the top navigation bar, select Configure > Managed Objects. A list of the system’s managed objects displays.
-
Select an object type (for example, User). A page displays where you can configure the managed object’s properties, details, and scripts.
-
On the Properties tab, select the property to be encrypted. A page displays where you can can manage the property.
-
On the Privacy & Encryption tab, select the Encrypted toggle. If encryption is enabled, the toggle is green and displays a white checkmark. If encryption is disabled, the toggle is grey and no checkmark displays.
-
In the Encryption Purpose field, type
idm.password.encryption.A blank or invalid purpose may cause errors. Do not leave the field blank or provide an invalid purpose. -
Click Save.
Encrypt and decrypt properties using REST
You can encrypt and decrypt property values over REST by calling the openidm.encrypt or openidm.decrypt scripts on the openidm/script?_action=eval endpoint.
Refer to Functions available in identity-related scripts for more information about the openidm.encrypt and openidm.decrypt functions.
Advanced Identity Cloud tenants only support the AES-128 encryption algorithm and the idm.password.encryption alias.
|
This curl command demonstrates using openidm.encrypt to encrypt a key-value pair ({"myKey": "myPassword"}):
curl \ --header "Authorization: Bearer <access-token>" \ --header "Content-Type: application/json" \ --cacert ca-cert.pem \ --request POST \ --data '{ "type": "text/javascript", "globals": { "val": { "myKey": "myPassword" } }, "source":"openidm.encrypt(val,null,'idm.password.encryption');" }' \ "https://<tenant-env-fqdn>/openidm/script?_action=eval" { "$crypto": { "type": "x-simple-encryption", "value": { "cipher": "AES/CBC/PKCS5Padding", "stableId": "openidm-sym-default", "salt": "qAS/eG7zdnFyK5H8lXvqTA==", "data": "zewf6hR1yjp34EFJqUGpdnzzFCPJs2IaX4V97jdQlSI=", "keySize": 128, "purpose": "idm.password.encryption", "iv": "A4pIiY6kG6t0uLyLmJAoWQ==", "mac": "sFDJqg0Mmp0Ftl+1q1Bjzw==" } } }
This curl command demonstrates decrypting an object using openidm.decrypt:
curl \ --header "Authorization: Bearer <access-token>" \ --header "Content-Type: application/json" \ --cacert ca-cert.pem \ --request POST \ --data '{ "type": "text/javascript", "globals": { "val": { "$crypto": { "type": "x-simple-encryption", "value": { "cipher": "AES/CBC/PKCS5Padding", "stableId": "openidm-sym-default", "salt": "qAS/eG7zdnFyK5H8lXvqTA==", "data": "zewf6hR1yjp34EFJqUGpdnzzFCPJs2IaX4V97jdQlSI=", "keySize": 128, "purpose": "idm.password.encryption", "iv": "A4pIiY6kG6t0uLyLmJAoWQ==", "mac": "sFDJqg0Mmp0Ftl+1q1Bjzw==" } } } }, "source":"openidm.decrypt(val);" }' \ "https://<tenant-env-fqdn>/openidm/script?_action=eval" { "myKey": "myPassword" }
Salted hashing
Hashing is a one-way process of transforming a key or string of characters into a different fixed-length value. Salting is a process of improving the hash’s security by adding random data as additional input. If you do not need to synchronize your secure data or provide it to another system in an unencrypted form, hash and salt it.
| Hashed data cannot be decrypted. Do not secure your data by hashing it if you will need the unencrypted value. |
The following table displays supported hashing algorithms:
| Algorithm | Attributes | ||
|---|---|---|---|
|
|
||
|
|
||
|
|
||
|
|
||
|
|
||
|
|
Configure hashing using the IDM admin console
You can set a property hash algorithm using the IDM admin console. Only some algorithms and none of the enhanced configuration options are supported.
Show Me
-
Select Configure > Managed Objects, and select an object type (for example, User).
-
On the Properties tab, select a property to hash.
-
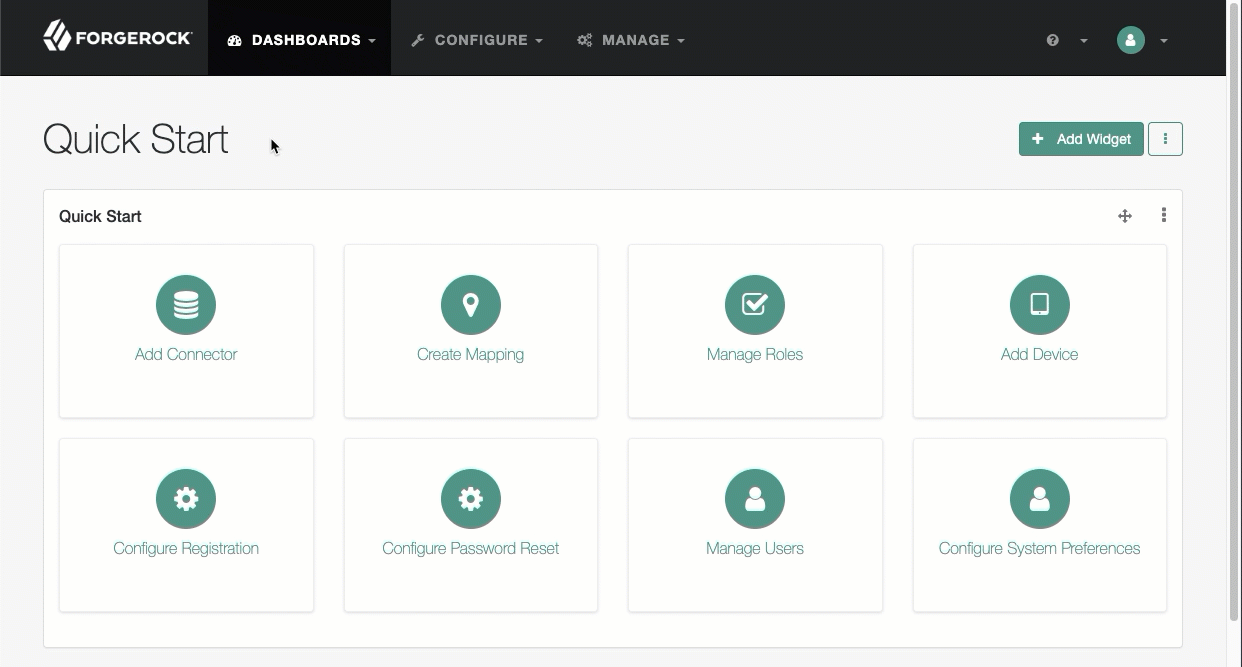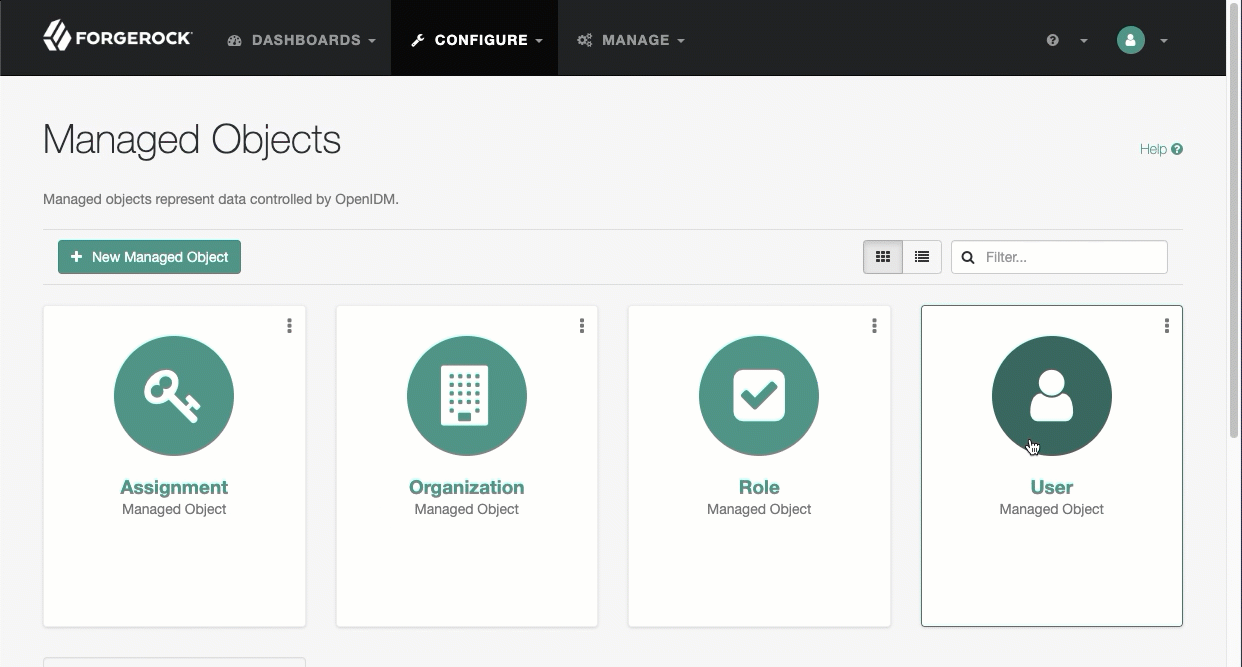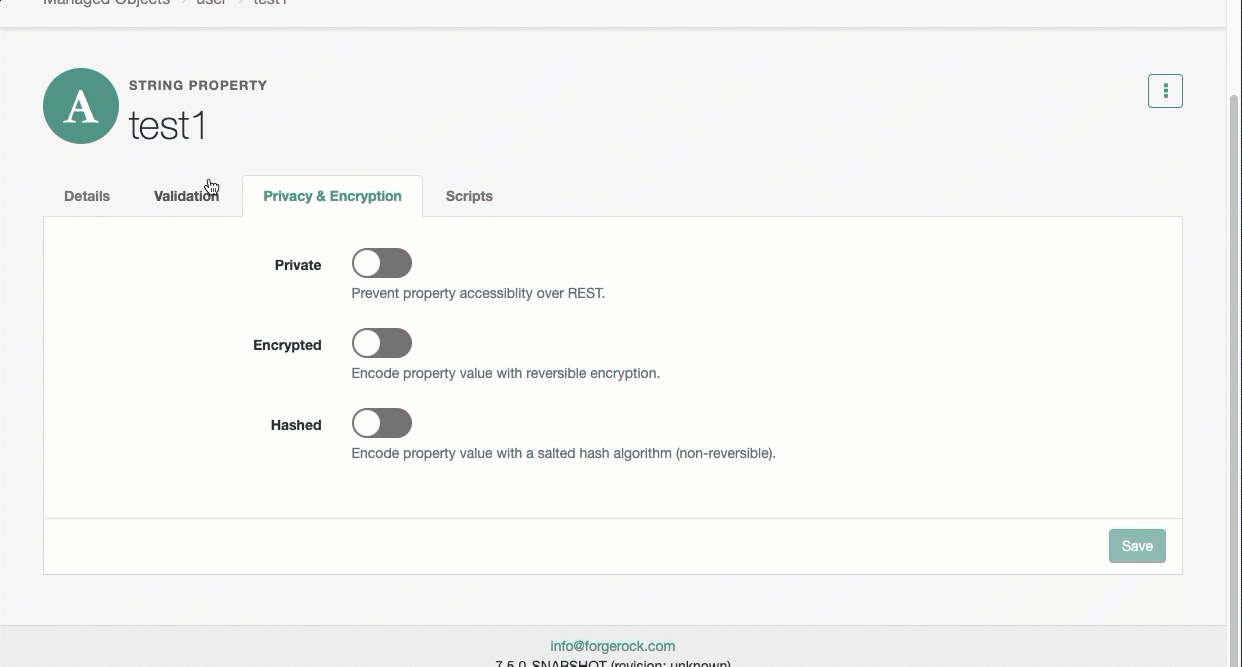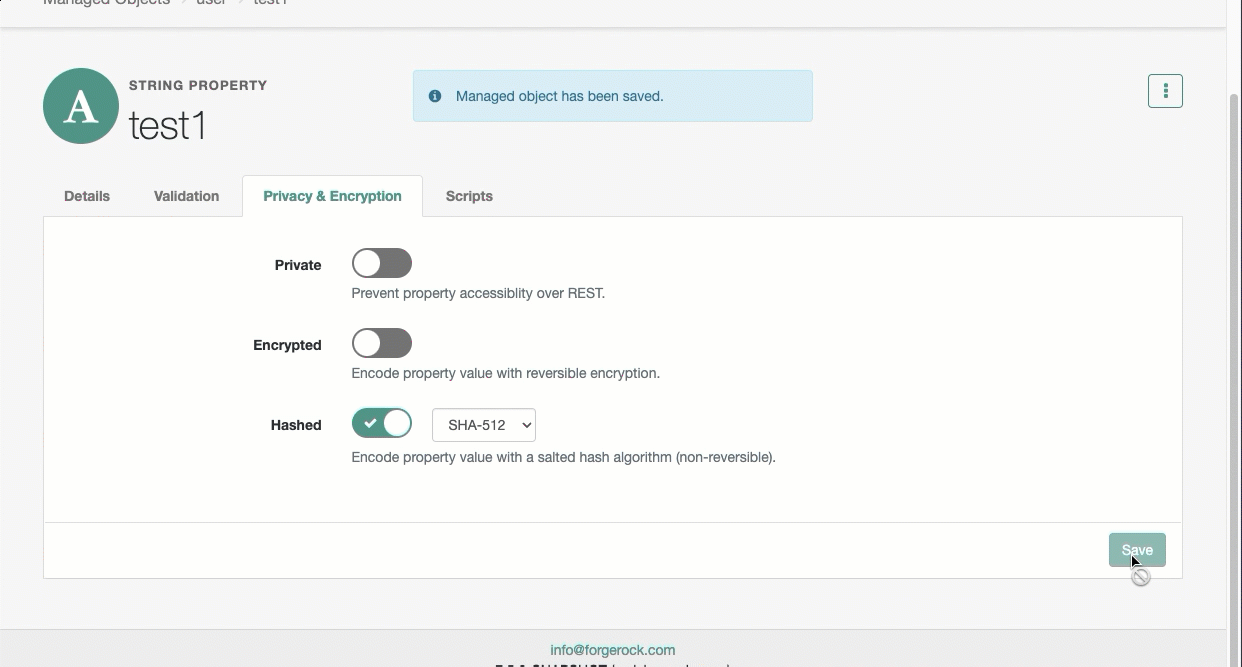
On the Property page, click the Privacy & Encryption tab, and select Hashed.
-
From the adjacent drop-down menu, select an algorithm.
-
Click Save.