Create private network connections with Secure Connect
|
Advanced Identity Cloud add-on capability
Contact your Ping Identity representative if you want to add Secure Connect to your PingOne Advanced Identity Cloud subscription. Learn more in Add-on capabilities. Secure Connect is currently also a limited availability feature. |
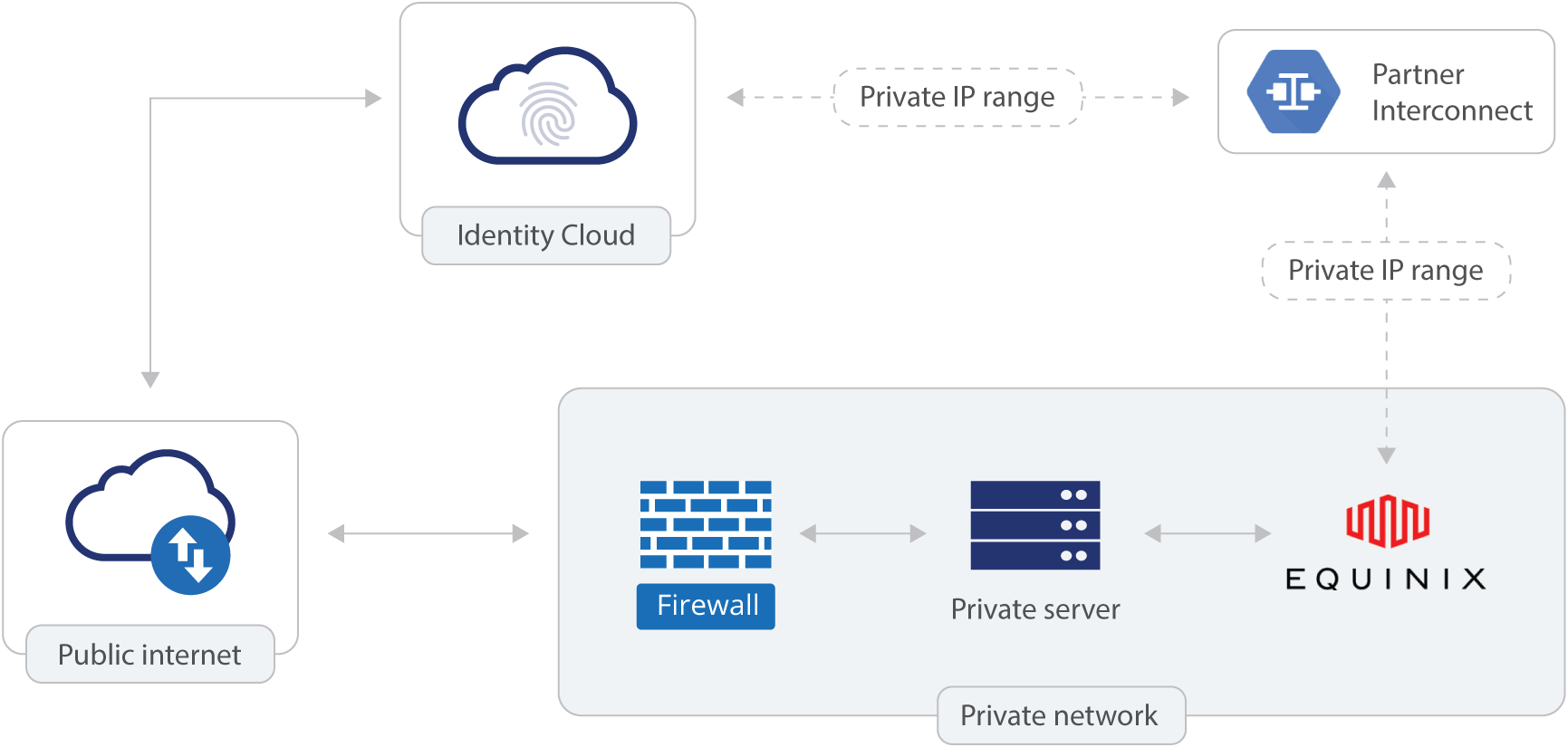
You can use Secure Connect to provide dedicated, direct, and secure communication between your PingOne Advanced Identity Cloud network and your private network, such as an on-premises data center or IaaS provider. Secure Connect bypasses the public internet, improving latency, throughput, and security.
Use cases
The following are examples of how you might use Secure Connect:
-
Call an API endpoint in your private network from a journey script or journey authentication node in Advanced Identity Cloud.
-
Send Advanced Identity Cloud emails from an internal MX/SMTP server not exposed to the public internet.
-
Resolve an internal DNS name using a private DNS server; for example, an internal DNS name using the
.companydomain extension. -
Access PII/classified data which cannot be sent over public internet.
Supported services
Ping Identity supports the following services using Secure Connect:
-
DNS for internal domain names (53/udp)
-
HTTP outbound (Advanced Identity Cloud → private network service) (80/tcp & 8080/tcp)
-
HTTPS outbound (Advanced Identity Cloud → private network service) (443/tcp)
-
HTTPS inbound (private network service → Advanced Identity Cloud) (443/tcp)
-
SMTP outbound (Advanced Identity Cloud → private network service) (25/tcp)
-
SMTPS outbound (Advanced Identity Cloud → private network service) (587/tcp)
This list represents the use cases Ping Identity explicitly tests against; however, you may test and use additional services to support your own private network use cases.
Configure DNS
To support Secure Connect, configure your company’s DNS to avoid collisions. Collisions can occur when the same IP address is allocated to resources inside different private networks and one or both private networks advertise the address publicly. This can cause traffic destined for one network to be incorrectly routed to the other network.
To avoid collisions, separate your company’s DNS configuration into public and private zones. The private zone can advertise resources reachable using public and private addresses, but the public zone should only advertise resources reachable using public addresses and should not advertise private addresses.
Learn more in RFC 1918.
FAQs
Can I still access Advanced Identity Cloud API endpoints over the public internet?
Yes, Advanced Identity Cloud API endpoints are still available over the public internet; however, Secure Connect also exposes the same API endpoints privately to let you communicate between your private network and Advanced Identity Cloud:
-
Communicate inbound by calling API endpoints in your Advanced Identity Cloud tenant environments from your private network.
-
Communicate outbound by calling API endpoints in your private network from your Advanced Identity Cloud tenant environments.
Can I still access the Advanced Identity Cloud admin console over the public internet?
Yes, the Advanced Identity Cloud admin console is still available over the public internet and cannot be made private.
How do I communicate securely with my tenant environments?
When you provision Secure Connect, you provide Ping Identity with CIDR ranges for each tenant environment. Ping Identity uses your CIDR ranges to create an internal endpoint for each Advanced Identity Cloud tenant environment. You then create private DNS records for these Advanced Identity Cloud endpoints and then create a self-managed certificate.
How do I communicate securely to my private network?
For services like SMTP, Ping Identity can add your CA certificate into the trust store of your tenant environments. For assistance with this, learn more in Send Ping Identity a CA or TLS certificate.
Can I connect Google Cloud to another cloud provider? For example, AWS?
Yes, you can connect Google Cloud to another cloud provider. In the example of AWS, you separately implement AWS Direct Connect, then set up virtual routing in your private network between Google Cloud and AWS. Learn more in Partner Interconnect with multi-cloud enabled partners.
How do I choose CIDR blocks for my tenant environments?
Choose CIDR blocks for your tenant environments that allow sufficient IP addresses for the number of users and services you expect to connect to each environment from your private network.
The following table provides guidance on the number of IP addresses available for different CIDR blocks. The lower the numeric value of the CIDR block, the more IP addresses are available.
| CIDR block | Number of IP addresses | Guidance |
|---|---|---|
|
32 |
Suitable for up to 30 users and services. This CIDR block represents the minimum number of IP addresses you can choose when configuring Secure Connect. |
|
64 |
Suitable for up to 62 users and services. |
|
128 |
Suitable for up to 126 users and services. |
|
256 |
Suitable for up to 254 users and services. |
|
512 |
Suitable for up to 510 users and services. |
|
1,024 |
Suitable for up to 1,022 users and services. |
|
2,048 |
Suitable for up to 2,046 users and services. |
|
4,096 |
Suitable for up to 4,094 users and services. |
Google Cloud Interconnect
Secure Connect uses Google Cloud Interconnect to implement private network connections between your Advanced Identity Cloud tenant environments and your private network:
-
The Partner Interconnect option is supported for one service provider (Equinix Fabric).
-
The Dedicated Interconnect option is not supported.
To implement this, Ping Identity creates VLAN attachments that are associated with a cloud router in your Advanced Identity Cloud network. The cloud router creates a BGP session for the VLAN attachments and your corresponding private network router. The cloud router receives the routes your private network router advertises. These routes are added as custom dynamic routes in your Advanced Identity Cloud network. The cloud router also advertises routes for your tenant environments, using CIDR blocks you specify during provisioning.
Availability
You can configure Google Cloud Interconnect to support three-nines availability or four-nines availability. The following table summarizes the different approaches:
| Availability | Guidance | Requirements |
|---|---|---|
Three-nines (99.9%) |
Recommended only for non-critical applications where downtime can be tolerated. |
At least two Interconnect connections. The connections must be located in the same metropolitan area, but in different edge availability domains (metropolitan availability zones). |
Four-nines (99.99%) |
Recommended for most production applications. |
At least four Interconnect connections, two connections in one metropolitan area and two connections in another. Interconnect connections that are in the same metropolitan area must be placed in different edge availability domains (metropolitan availability zones). |
Partner Interconnect service providers
Equinix Fabric
Secure Connect uses the Partner Interconnect service for Equinix Fabric to provide private network connections between your Advanced Identity Cloud tenant environments and an Equinix private network.
To set up Partner Interconnect and Equinix in Advanced Identity Cloud, learn more in Configure Secure Connect with Equinix.