Nodes and journeys
Journeys provide fine-grained authentication by allowing multiple paths and decision points throughout the authentication flow. Use them to build complex authorization scenarios, while offering a streamlined login experience to users.
Journeys are made up of nodes, which define actions taken during authentication. Each node performs a single task during authentication; for example, collecting a username or making a simple decision based on a cookie.
Nodes can have multiple outcomes rather than just success or failure. These outcomes let you create complex yet user-friendly authentication experiences by linking nodes together, creating loops and sections for different authentication scenarios, and nesting nodes within a journey.
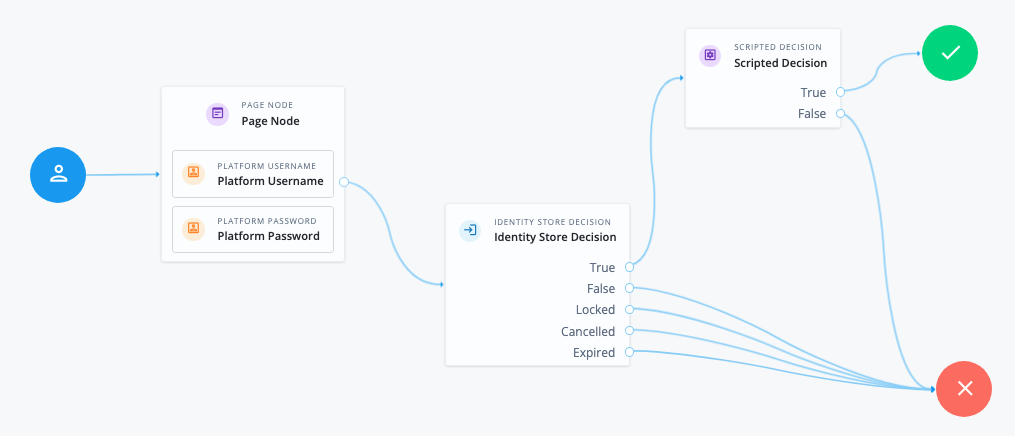
For greater control of the authentication process, you can assign authentication levels to sections of a journey, with higher levels typically allowing access to more restricted resources.
Learn more about creating an authentication journey using the Advanced Identity Cloud admin console in Journeys.
The following table summarizes the high-level tasks required to create and configure authentication journeys:
| Task | Resources |
|---|---|
Design your user authentication journey Authentication journeys are flexible. For example, the same journey can branch for different use cases, or users can be forced to loop though branches until they’re able to present the required credentials. It’s easy to create a massive journey that’s difficult to understand, read, and maintain in the UI. To avoid this, Advanced Identity Cloud lets you nest journeys within journeys. The best way to tackle the design decision is to write down a list of required steps users would need to take to log in to your environment, and then check the list of nodes available in Advanced Identity Cloud. |
|
Create your authentication journeys Use the journey editor to put together your journeys quickly. |
|
Configure your authentication journeys Learn how to enable and disable journeys, specify resource types, set the session time for a journey, and so on. |
|
Configure webhooks, if required Use webhooks to send contextual information about authenticated sessions on predefined events, for example, logging out. |
Authentication levels
When a user authenticates successfully, Advanced Identity Cloud creates a session which allows Advanced Identity Cloud to manage the user’s access to resources. The session is assigned an authentication level. The authentication level is often used as a measure of the strength of the authentication performed. For example, a simple username and password might be assigned a low authentication level, while multi-factor authentication with push and WebAuthn might be assigned a high level.
Authorization policies might require a particular authentication level to access protected resources. When an authenticated user tries to access a protected resource without satisfying the authentication level requirement, Advanced Identity Cloud denies access to the resource and returns an advice indicating that the user must reauthenticate at the required level to access the resource.
The policy enforcement point, such as an agent, sends the user back to Advanced Identity Cloud for a session upgrade.
Advanced Identity Cloud provides the following nodes to manage authentication levels:
-
The Auth Level Decision node checks that the current authentication level is equal to or greater than the level specified in the node.
-
The Modify Auth Level node can raise or lower the authentication level.
Position these nodes to alter the authentication level, depending on the route taken through the authentication flow.
Account lockout
Use account lockout to limit the number of times an end-user can attempt to authenticate with invalid credentials before rendering their account inactive. Limiting the number of attempts helps to prevent password-guessing and brute-force attacks.
Authentication journeys have built-in support for account lockout. They also provide nodes for checking and changing the status of a user.
Learn more in Account lockout.