Enabling SLO for a PingAccess-protected application using PingFederate
Learn how to require a sign off of a PingAccess-protected application with PingFederate acting as a token provider.
There are multiple scenarios for signing off a user. As an administrator, you might require one or more sign-off flows because requirements for each application can differ.
This guide provides information for the following use cases:
-
Global single logout (SLO)
-
Per application or partial logout
Each PingAccess sign-off flow is user-initiated, not system-initiated. PingAccess checks if a session is revoked and, if the existing session is found to be revoked, redirects to the web. PingAccess doesn’t revoke sessions. It checks the revocation status by sending a GET request to that endpoint.
Learn more in Authorization endpoint (page 1,069) and Session Revocation API endpoint (page 1,156).
PingAccess Logout endpoint
PingAccess responds differently depending on whether the sign off is successful or unsuccessful.
-
For successful sign offs:
-
PingAccess responds to the
/pa/oidc/logout.pngrequest withSet-Cookie: PA.ACE_ws=;. -
The
/pa/oidc/logout.pngendpoint clears the ID token from the browser containing the PingAccess cookie.Unless you select Use single-logout (SLO) for the token provider, the
/pa/oidc/logout.pngendpoint clears the cookie only from the requested host/domain, and the cookie might still exist in requests bound for other hosts/domains.If you select the Use Single-Logout option when configuring the token provider, the
/pa/oidc/logout.pngendpoint also sends a logout request to the token provider, which completes a full SLO flow.
-
-
For unsuccessful sign offs:
-
PingAccess responds to the same
/pa/oidc/logout.pngrequest without clearing thePA.ACE_ws;cookie. -
The user is directed back to the PingAccess-protected application page.
-
If the application reads and finds the
PA.ACE_ws;cookie present, it doesn’t redirect to PingFederate for authentication.
-
PingAccess can only clear the sessions for which the corresponding cookie was sent in the request to the /pa/oidc/logout resource. If PingFederate or the authentication authority can maintain different sessions for each set of apps, you can use SLO to sign off of all sessions in each set. To initiate the end sessions sign off in specific domains, call the /pa/oidc/logout.png endpoint used by SLO.
Learn more in Server-side session management configuration (page 112) in the PingAccess solutions documentation.
Configuring PingAccess partial logout
Learn how to require termination of a user’s session per application or by a partial logout protected in the PingAccess administrative console.
Before you begin
You must:
-
Execute the identity provider (IdP) adapter’s logout endpoint. Learn more in HTML Form Adapter Logout Configuration.
-
Have experience with PingFederate and PingAccess.
Steps
-
In the PingAccess administrative console:
-
Go to Settings > Token Provider > Runtime > Show Advanced Settings.
-
Clear the Use Single-Logout checkbox.
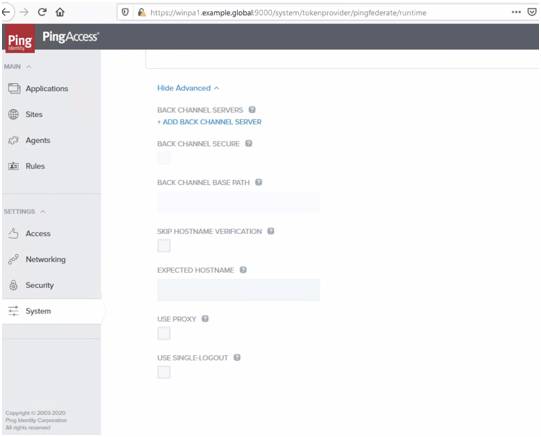
-
Click Save.
-
-
In the PingFederate administrative console:
-
Go to Authentication > Integration > IdP Adapters > Manage Adapter Instances and then select the relevant IdP adapter instance.
Result:
The Create Adapter Instance page opens.
-
To show the logout related fields, go to the IdP Adapter > Show Advanced Fields.
-
In the Logout Path field, enter the path with the PingAccess endpoint.
You can enter any valid path string.
This value must start with a "/" character. For example, if you enter
/mylogoutpath, then the logout path is/ext/mylogoutpath. Don’t use a path already used by another adapter, such as/ext/pickupor/ext/dropoff.Use an alphanumeric string to minimize the risk of using an invalid value in this field.
-
In the Logout Redirect field, enter the URL that PingFederate uses to redirect the user after sign off.
The default Logout Redirect value is
https://<pingaccessServer>:3000/pa/oidc/logout. -
For PingFederate to display a page using a template, in the Logout Template field, enter the name of the template file.
-
In the Logout Path field, enter a path with the PingAccess endpoint.
The default Logout Path value is
<pf_install>/server/default/conf/template/idp.logout.success.page.template.html.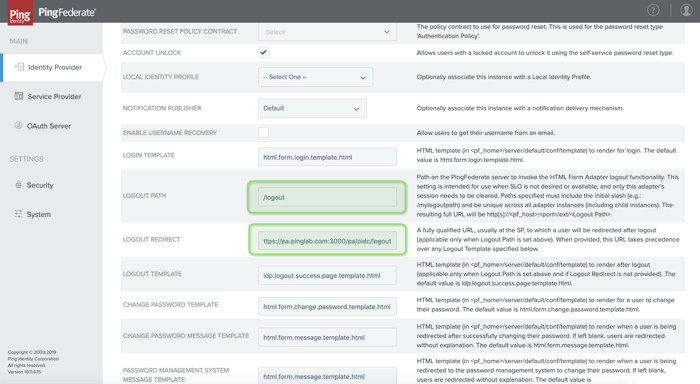
-
Click Done.
-
Configuring global single logout
Learn how to revoke global sessions with single logout (SLO) in the PingFederate administrative console.
Before you begin
Make sure the identity provider (IdP) adapters have their Session State set to Globally in PingFederate.
About this task
To revoke global sessions with SLO:
Steps
-
In the PingFederate administrative console, go to Applications > Integrations > Default URLs > SP Default URLs.
-
To allow
TargetResourceas a redirect URI in PingFederate, enter and edit the URL in the Provide The Default URL You Would Like to Send The User to When Single Logout (SLO) Has Succeeded field.The
TargetResourceis the landing page PingFederate directs the user to after logout, for example,http://pf01.pinglab.com:9331/idp/startSLO.ping?TargetResource=://pa01.pinglab.com:3000/PingAccessQuickstart/.The
TargetResourcemust be an allowed redirect URI in PingFederate. -
Click Save.
Result
PingFederate automatically redirects to the PingAccess logout endpoint pa/oidc/logout.
Configuring PingFederate for PingAccess single logout
Learn how to configure PingFederate for user-initiated PingAccess single logout (SLO) so that PingFederate knows to add the Subresource Integrities (SRIs) to the revocation list if SLO is initiated.
About this task
There are two ways to implement Server-Side Session Management:
-
PingAccess can reject a PingAccess cookie associated with a PingFederate session that has been invalidated as a result of an end-user-driven logout.
-
The end-user can initiate a logout from all PingAccess issued web sessions using a centralized sign off.
PingAccess can only clear the sessions for which the corresponding cookie is sent in the request to the /pa/oidc/logout resource. If PingFederate, as the authentication authority, can maintain different sessions for each set of apps, you can use SLO to sign off of all sessions in each set. Call the /pa/oidc/logout.png endpoint used by SLO to initiate the end sessions sign off in specific domains.
SLO is done by redirecting to the standard SLO location, which is configured in the run.props file. PingAccess does not revoke the user’s session. The user is directed to the pa.oidc.logout.redirectURI URI when they sign off using OpenID Connect and the PingFederate SLO endpoint.
Learn more in Configuration file reference (page 171) and OpenID Connect endpoints (page 158).
Steps
-
In the PingFederate administrative console, go to Applications > OAuth > Clients > Client Management, and select the relevant client.
Result:
The Client page opens.
-
To enable PingFederate to add the SRIs to the revocation list if SLO is initiated, in the OpenID Connect section, select the PingAccess Logout Capable checkbox.
-
Click Save.
Result
PingFederate uses the logout.png endpoint /pa/oidc/logout.png to initiate a sign off from PingAccess in conjunction with the SLO functionality. This endpoint terminates the PingAccess tokens across domains.
Learn more in Configuring PingFederate for user-initiated single logout (page 113).