Workforce passwordless journey
The journey to passwordless is comprised of many phases and goals.

The following diagrams show each step of the passwordless journey and its goals.
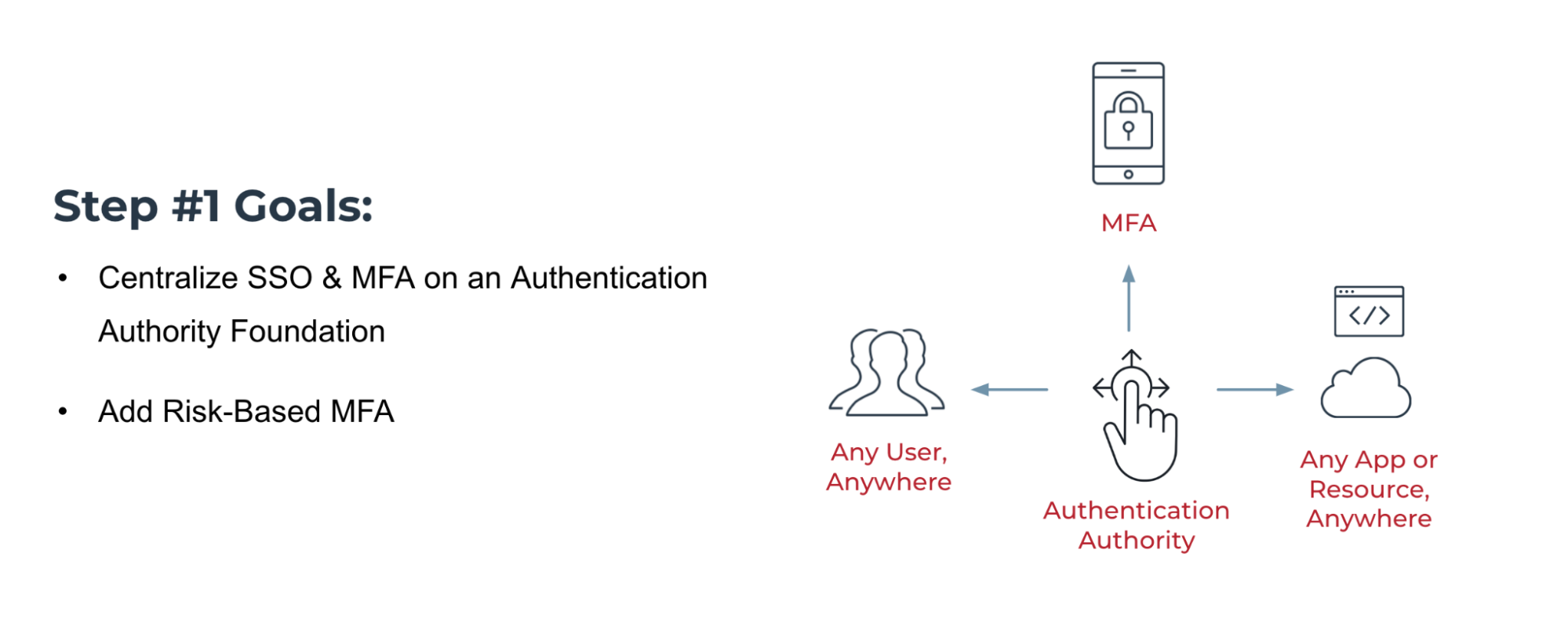
The goals of step 1 are to centralize SSO and MFA on an authentication authority foundation.
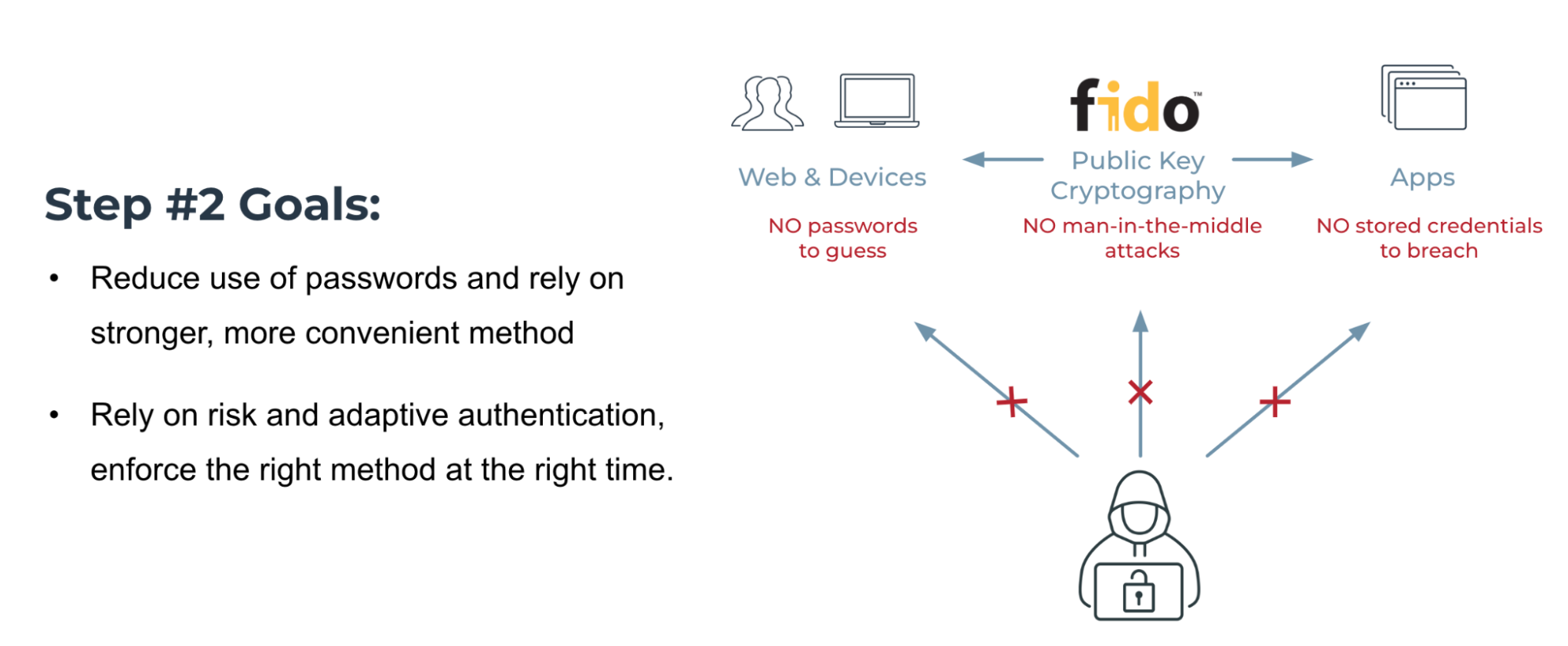
The goals of step 2 are to reduce password use and rely on adaptive authentication to enforce the right methods as needed.
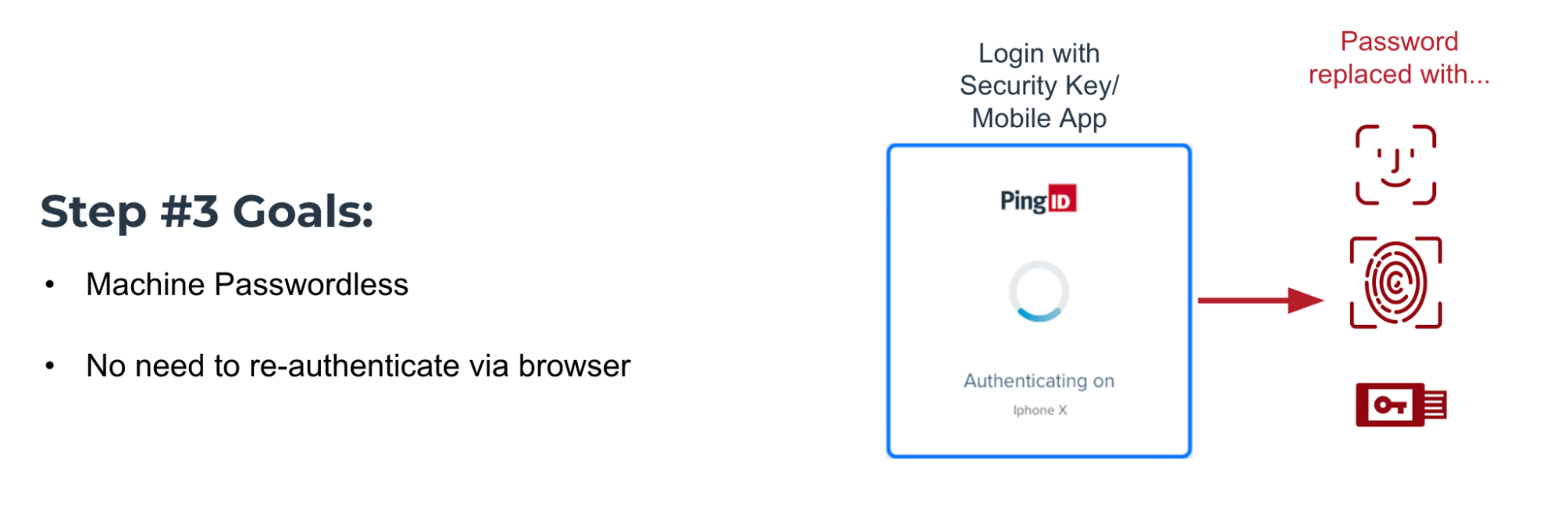
The goals of step 3 are to implement machine passwordless control and remove the need for re-authentication with a browser.
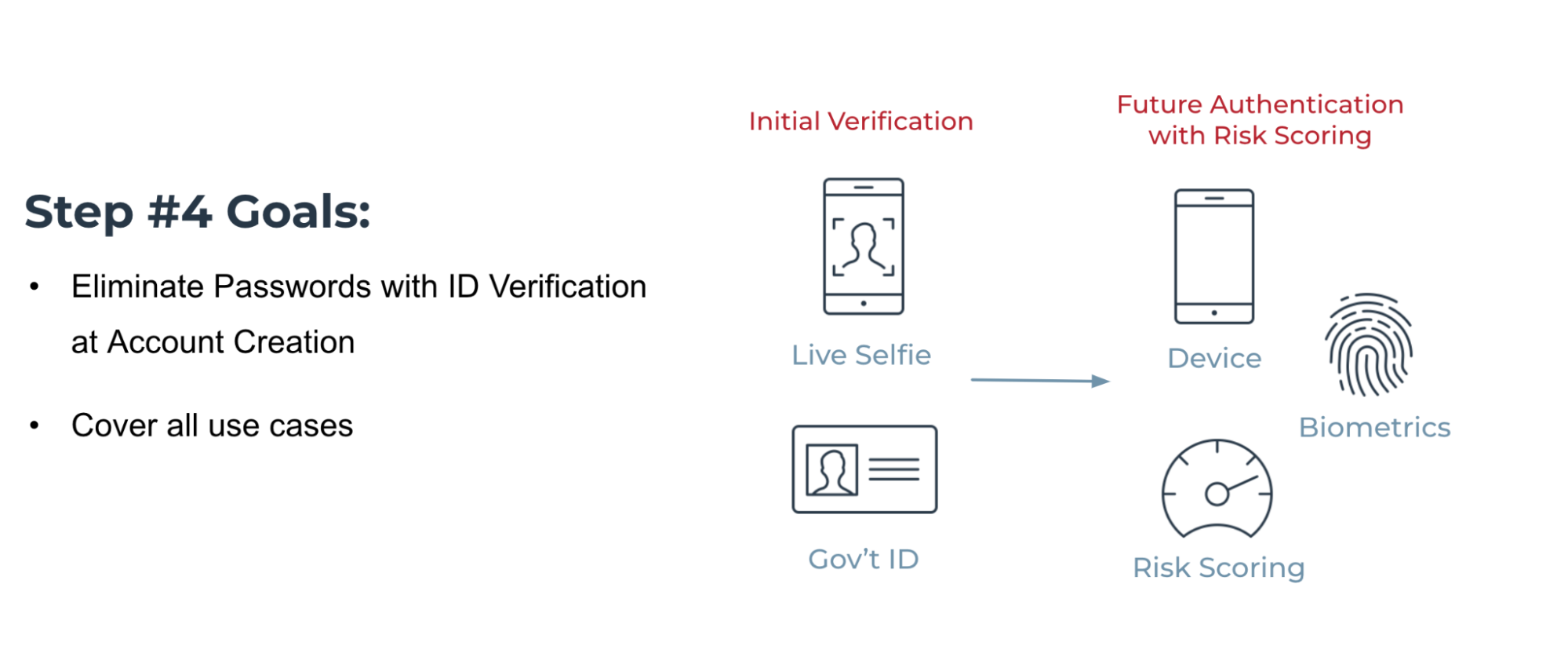
The goals of step 4 are to eliminate passwords with ID verification at account creation and to cover all use cases.
Planning the workforce passwordless journey
Passwordless authentication provides technologies, such as FIDO security keys, FIDO biometrics, and Ping Risk, that eliminate the use of passwords.
Because lost and stolen passwords create security risks, passwordless authentication helps mitigate security risks associated with passwords and removes friction from the authentication process.
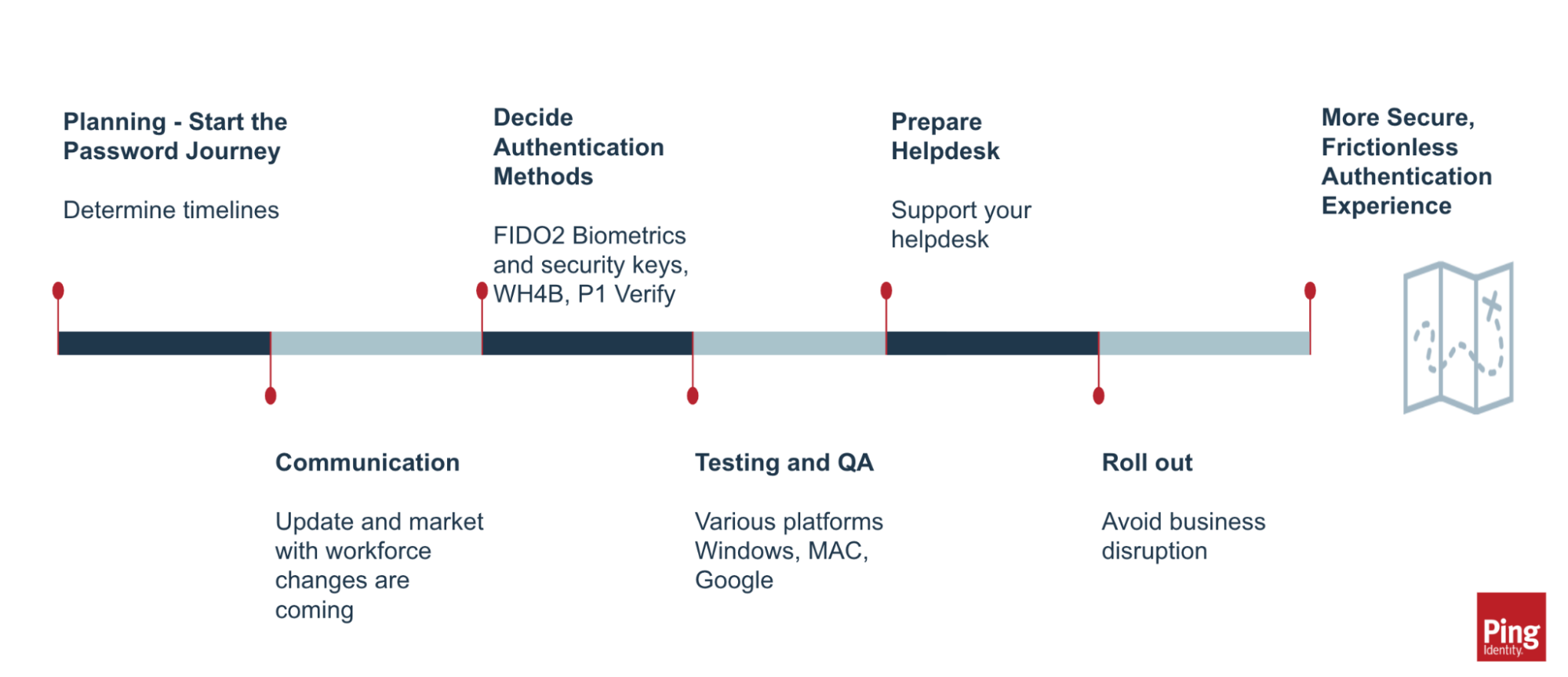
The following planning diagram breaks the implementation process apart into separate phases:
-
Planning the journey
-
Communicating the upcoming changes
-
Deciding on authentication methods
-
Testing the implementation
-
Preparing your help desk for passwordless
-
Rolling out the passwordless experience
Change management
The most important step to begin discussing and planning with your organization. This helps to define the change that is coming, prepare for communication, and begin working with the internal channels that the enterprise is shifting to passwordless.
As an administrator, understand you are eliminating friction in the authentication process and improving security posture by eliminating passwords. Achieving frictionless authentication requires introducing friction at the start of the process, such as when you’re planning change management, training, and implementing a deployment. The end result is a frictionless authentication experience.
When working with many internal teams through your change management processes there will be friction introduced in the beginning until this is complete. This is the part where you introduce more friction before going frictionless.
-
Understand that you are aiming to mitigate password risks currently present and introducing a frictionless experience, improved end user experience.
-
Take advantage of biometrics and FIDO2 compliant devices.
-
Deploy adaptive authentication with passwordless using intelligent behavior analysis of user activity to determine authentication requirements:
-
Low-risk authentication requests
-
High-risk authentication requests that require re-authentication or block
-
When dealing with change management, understand what devices and technologies are available for the organization. Work with the departments that handle inventory and the preferred choice of software used on workstations, and list what is available today for testing. Ensure internal teams are aligned as you prepare for implementation.
The different changes you have planned not only determine your timelines and goals, but affect the tools and strategies that you will need going forward. Team alignment helps leaders identify whether they must provide any additional resources before rolling out passwordless authentication.
What is being used with MFA today?
|
What is your current inventory?
|
Default timelines
|
Test with user groups
|
Communication
When planning this step, understand and determine who are the internal stakeholders including who will own what from the help desk, other departments, vendors, and application teams:
-
Communicate timelines.
-
Design marketing material and knowledge management articles.
-
Establish the guidelines for these changes.
-
Documentation and KMs.
-
Prepare and train the help desk.
-
Create a communication plan to update Workforce changes that are coming in the future.
Decide passwordless methods
As you decide on passwordless methods, keep the following in mind:
-
Does your organization use Windows, Apple, Linux, or a combination of those?
-
Are you using MFA?
-
Ensure backup authentication methods are in place, such as:
-
TouchID, FaceID, FIDO2 compliant Security Key
-
Phone, tablet, laptop, and similar hardware.
Always register more than one device or technology. Biometric authentication is slightly more secure than a PIN, but if biometric authentication fails, it can be set up to fail back to PIN.
-
-
What adaptive authentication capabilities does your organization use, such as PingOne Protect?
Rethink policies and processes
When you rethink your authentication policies, consolidate them to simplify.
When you rethink procedures, consider:
-
Help desk policies
-
Lost device policies
-
How to test for your use cases
Testing and QA
Before you plan for rollout, make sure you perform sufficient testing on different browsers and operating systems to prevent delays in implementation.
To test:
-
Take into account third-party implementers for the standard.
Chrome, Safari, Edge, and Firefox might have different requirements and behaviors that you must take into account.
-
Involve diverse departments to help choose authentication factors and to test.
-
Register a device on different operating systems.
Some devices require updating the operating system. Updating the operating system for security requirements could create a delay with your planned timeline.
-
Continue to test whenever browser and operating system updates occur.
Planning rollout
As you plan for rollout, consider the following priorities:
-
Prevent disrupting business.
-
What groups or apps are already using MFA?
Start here.
-
Rollout to end users.
What departments and groups are best-equipped for the first wave?
-
Deploy in a small volume, then ramp it up:
-
10 users with 5 or 10 applications
-
Increase to 100 users for 10 apps and so on
-
Increase to 500 users with 10 apps and so on
-
Onboarding
As you prepare to onboard individuals with your passwordless authentication experience, consider the following:
-
Self-service is the goal.
-
Who is your user population?
-
What groups are best-equipped to be first adopters?
-
What considerations do you need to take into account for global users?
-
Not all can use MFA today.
-
Might not own smartphones.
-
-
What considerations do you need to take into account for seasonal employees?
-
You might not want to give them a security key.
-
You might need a policy for these groups.
-
-
-
Are you using MFA?
-
What are those devices?
-
Is more than one registered?
-
How many of those would fall into biometric, security keys, Windows Hello, or others?
-
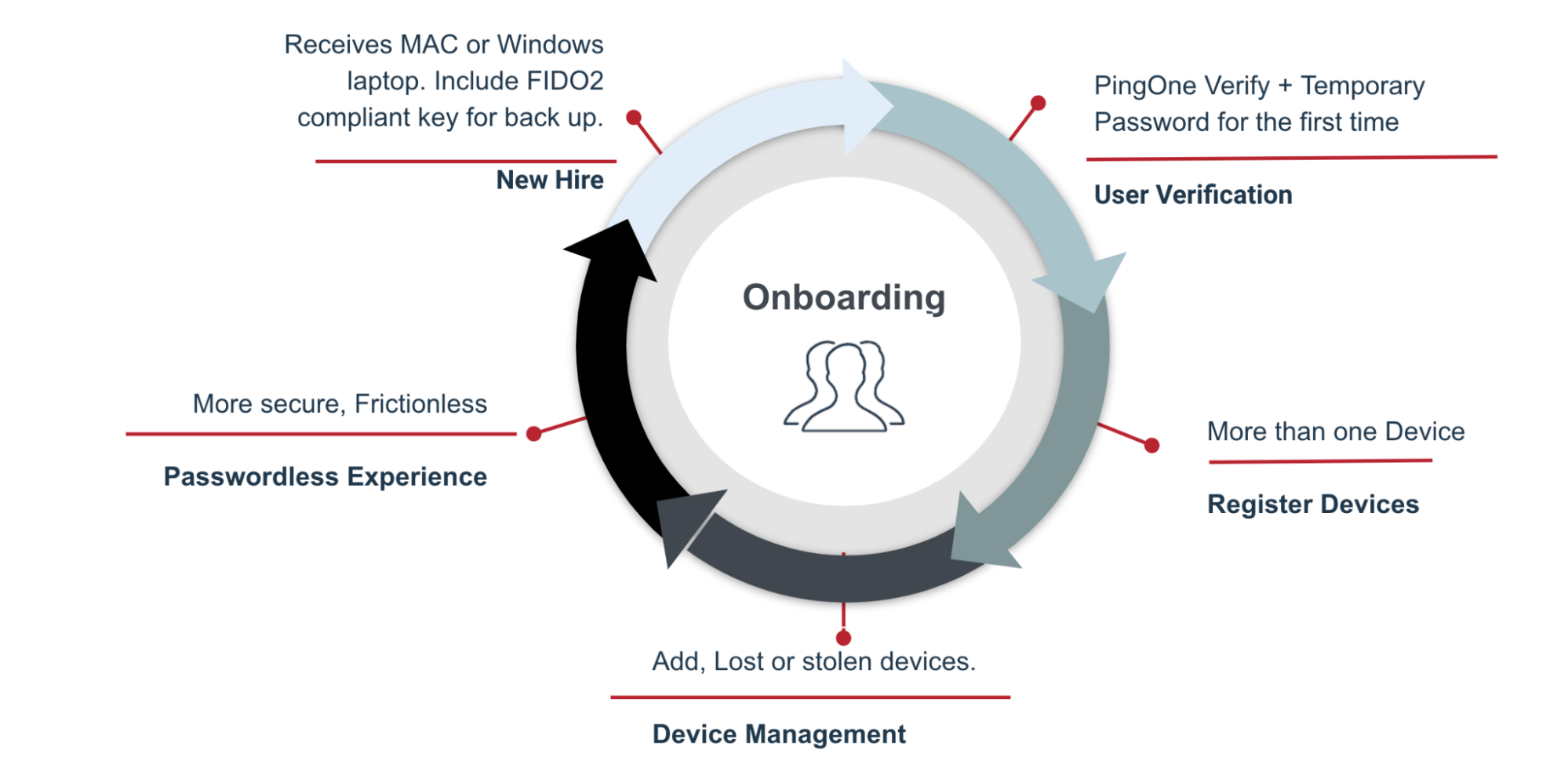
The following diagram shows the onboarding cycle.
-
A new hire receives their Mac or Windows laptop. Include a FIDO2 compliant key for back up.
-
The user undergoes verification for the first time through PingOne Verify and a temporary password.
-
The user registers their devices, adding more than one device.
-
The user manages their devices, including adding device and reporting lost or stolen devices.
-
The user moves into a more secure, frictionless experience through passwordless authentication.
Lost devices
How are you handling lost or stolen devices? The following can all help you plan for what to do about these devices.
|
Remember to have more than one device registered. For example, have an iPhone, iPad, and a laptop registered. |
-
User verification.
-
PingID mobile application.
-
What’s easier to get back on network?
FIDO keys should be the second-to-last resort.
-
HelpDesk can come into play through using a temporary method.
The PingID desktop application with a lost or stolen Yubikey or phone should be your last resort.
Lessons learned from the workforce passwordless journey
-
Passwordless takes time:
-
Having an MFA deployment prior to adoption into passwordless will ease the process.
-
Setting up and testing takes time. There is a high upfront cost with time, planning, and testing. You need to understand the different behavior when interacting with different software and then test and determine what’s best for your users before rolling out passwordless. Stay with the guidelines you’ve set to simplify the onboarding and support process moving forward.
-
-
You are now in the hands of the implementers for the standard:
-
Chrome, Safari, Edge, and Firefox might have different behaviors that you must take into account.
-
Client browser or OS updates could change the experience.
-
Using different browsers requires multiple registrations.
-
-
User experience:
-
Format for selecting registered devices
-
-
User verification and adaptive authentication:
-
Risk-based authentication
-
Web browsers
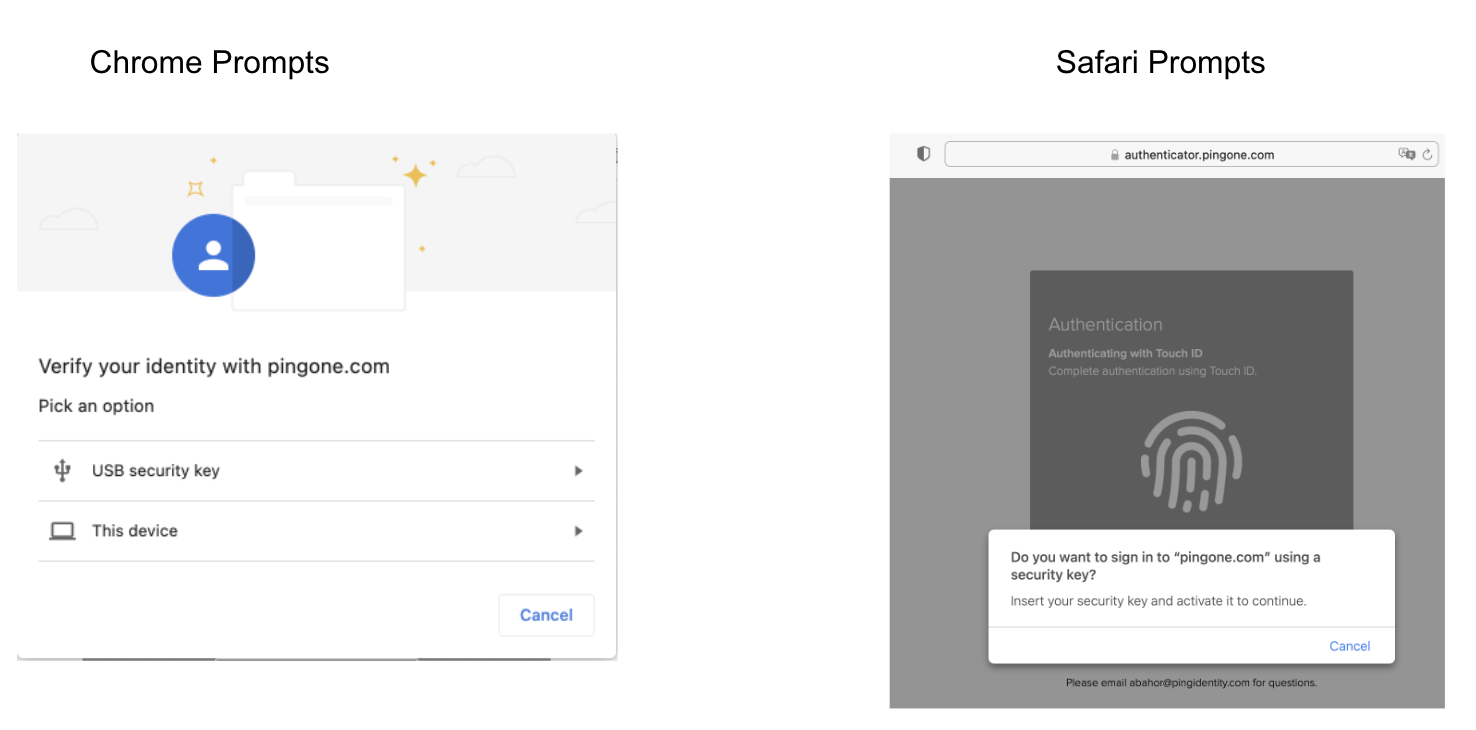
Different clients will provide a slightly different passwordless experience, as shown in the following example of the differences between a prompt in Chrome and a prompt in Safari.
|
FIDO must be registered twice if you are using two clients. Your organization should support at least two clients in case one encounters an issue from an update or similar. |
Deploying products
Before you begin
You must have:
-
FIDO2 capable Security Key
The example below leverages Yubikey 5.
-
PingID Adapter 2.8.
-
A browser that supports WebAuthn.
-
PingFederate 10.2 or later, which provides native support for adding a passwordless authentication flow icon for the HTML Form Adapter along with only showing the Security Key button on the HTML Form when the browser in use supports WebAuthn.
About this task
This document makes the following assumptions:
-
The organization has a functioning HTML Form IdP Adapter that passwordless authentication processes can be added to.
-
A new PingFederate authentication policy is being built as opposed to adding to an existing authentication policy, which should also be possible.
-
The authentication policy built within the example is at a global level as opposed to an application-specific one. An admin determines the authentication flow that will be best suited for passwordless experience.
|
As of this writing, Firefox for Mac does not support PIN code user verification, resulting in the registered security key that has an associated PIN not being recognized. |