Setting up an authentication flow that includes MFA (PingFederate and PingID)
This configuration creates a service provider (SP) connection with a multi-factor authentication (MFA) flow using PingFederate and PingID.
Creating a password credential validator in PingFederate
Steps
-
In the PingFederate administrative console, go to System > Data & Credential Stores > Password Credential Validators, and click Create New Instance.
-
On the Type tab, in the Type list, select Simple Username Password Credential Validator. Complete the remaining required fields, and then click Next.
-
On the Instance Configuration tab, click Add a New Row to 'Users'. Complete the Username, Password, and Confirm Password fields, and then click Update.
-
Click Next, and then on the Summary tab, click Done.
-
In the Password Credential Validators window, click Save.
Creating an HTML adapter that uses the PCV
Steps
-
Go to Authentication > Integration > IdP Adapters and click Create New Instance.
-
On the Type tab, in the Type list, select HTML Form IdP Adapter. Complete the remaining required fields, and then click Next.
-
On the IdP Adapter tab, in the Password Credential Validator list, select the PCV you previously created. Click Update.
-
Click Next until you reach the Adapter Attributes tab.
-
On the Adapter Attributes tab, select the Pseudonym checkbox for the
usernameentry. Click Next until you reach the Summary tab. -
On the Summary tab, click Done.
-
In the Manage IdP Adapter Instances window, click Save.
Downloading the pingid.properties file in PingOne for Enterprise
Steps
-
In the PingOne for Enterprise admin portal, go to Setup > PingID > Client Integration.
-
In the Integrate with PingFederate and Other Clients section, click Download.
Creating a PingID adapter in PingFederate
Steps
-
In the PingFederate administrative console, go to Authentication > Integration > IdP Adapters and click Create New Instance.
-
On the Type tab, in the Type list, select PingID Adapter 2.6. Complete the remaining required fields, and then click Next.
-
On the IdP Adapter tab, click Choose File. Select the
pingid.propertiesfile, and then click Next. -
Click Next until you reach the Adapter Attributes tab.
-
On the Adapter Attributes tab, select the Pseudonym checkbox for the
subjectentry. Click Next. -
Click Next until you reach the Summary tab, and then click Done.
-
In the Manage IdP Adapter Instances window, click Save.
Creating an authentication policy contract
Steps
-
Go to Authentication > Policies > Policy Contracts and click Create New Contract.
-
On the Contract Info tab, in the Contract Name field, enter a name.
-
Click Next until you reach the Summary tab, and then click Done.
-
In the Authentication Policy Contracts window, click Save.
Creating an SP connection
Steps
-
Go to Applications > Integration > SP Connections and click Create Connection.
-
Click Next until you reach the Connection Type tab.
-
On the Connection Type tab, select the Browser SSO Profiles checkbox. Click Next until you reach the General Info tab.
-
On the General Info tab, in the Partner’s Entity ID field, enter a dummy entity ID. In the Connection Name field, enter a name, and then click Next.
-
On the Browser SSO tab, click Configure Browser SSO.
-
On the SAML Profiles tab, select the IdP-Initiated SSO checkbox only. Click Next until you reach the Assertion Creation tab.
-
On the Assertion Creation tab, click Configure Assertion Creation. Click Next until you reach the Authentication Source Mapping tab.
-
On the Authentication Source Mapping tab, click Map New Authentication Policy.
-
On the Authentication Policy Contract tab, in the Authentication Policy Contract list, select your policy contract. Click Next until you reach the Attribute Contract Fulfillment tab.
-
On the Attribute Contract Fulfillment tab, in the Source list for the
SAML_SUBJECTentry, select Authentication Policy Contract. From the Value list, select subject. -
Click Next and Done until you reach the Protocol Settings tab. Click Configure Protocol Settings.
-
On the Assertion Consumer Service URL tab, enter a number in the Index field. From the Binding list, select POST. In the Endpoint URL field, enter a dummy URL, then click Add.
-
Click Next and Done until you reach the Credentials tab. Click Configure Credentials.
-
On the Digital Signature Settings tab, from the Signing Certificate list, select a signing certificate.
-
Click Next and Done until you reach the Activation & Summary tab. Click Save.
-
In the SP Connections window, click Save.
Creating an authentication selector
Steps
-
Go to Authentication > Policies > Selectors and click Create New Instance.
-
On the Type tab, in the Type list, select Connection Set Authentication Selector. Complete the remaining required fields, and then click Next.
-
On the Authentication Selector tab, click Add a New Row to 'Connections'. From the Connection list, select your SP connection. Click Update and then Next.
-
On the Summary tab, click Done. In the Manage Authentication Selector Instances window, click Save.
Creating an authentication policy
Steps
-
Go to Authentication > Policies > Policies and click Add Policy.
-
In the Name field, enter a name for the policy.
-
In the Policy list, from the list, select Selectors.
-
In the ID column, select the selector from step 7.
-
Beneath the No list, click Continue.
-
In the Yes list, select the HTML adapter from step 2.
-
Beneath the Fail list, click Done.
-
From the Success list, select the PingID Adapter from step 4.
-
Beneath your PingID Adapter instance, click Options.
-
In the Incoming User ID window, from the Source list, select the HTML adapter from step 2. From the Attribute list, select username.
-
Beneath the Fail list, click Done.
-
From the Success list, select the policy contract from step 5.
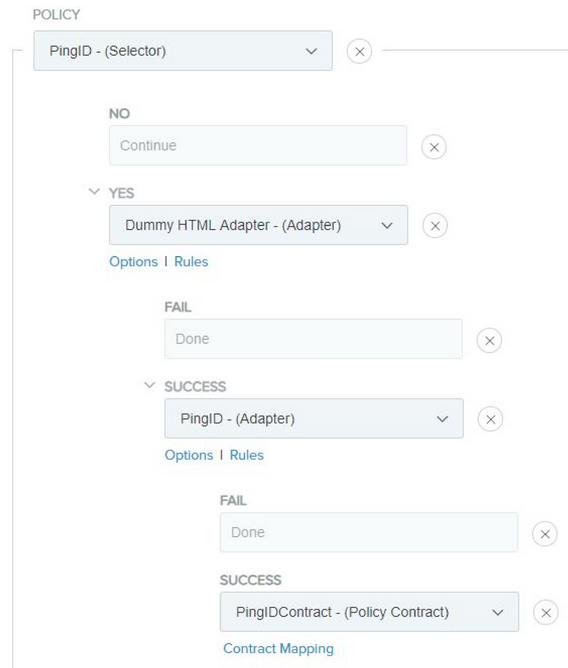
-
Click Contract Mapping.
-
On the Contract Fulfillment tab, from the Source list, select your HTML adapter. From the Value list, select username.
-
Click Next until you reach the Summary tab, and then click Done.
-
Click Done and then in the Authentication Policies window, click Save.
Testing your connection
Steps
-
In PingFederate, go to Applications > Integration > SP Connections, and click your SP connection.
-
On the Activation & Summary tab, verify that the green toggle switch is selected. Click the SSO Application Endpoint link.
-
Sign on as a user with the credentials created in step 1c.
Result:
When a user signs on for the first time, they are prompted to install PingID and register their device. If the user is registered, they are prompted to authenticate using PingID.