Integrating CyberArk with Ping products for SSO and authentication
This guide provides information for configuring a SAML connection to the CyberArk solution from the PingFederate or PingOne for Enterprise single sign-on (SSO) solutions while leveraging PingID for multi-factor authentication (MFA).
MFA is strongly advised and is the best practice for all authentication to the CyberArk Privileged Vault. For more information, see Product integration and overview.
Integrating CyberArk with PingOne for Enterprise
You can integrate CyberArk with PingOne for Enterprise using a SAML connection for CyberArk PVWA or an authentication policy for PingID MFA using CyberArk PVWA.
Click the tab for the configuration that you want to see.
Integrating CyberArk with PingFederate
You can integrate CyberArk with PingFederate using a SAML connection for CyberArk PVWA or an authentication policy for PingID MFA using CyberArk PVWA.
Click the tab for the configuration that you want to see.
Configuring SAML for CyberArk PVWA
Configure a SAML configuration for PingFederate or PingOne for Enterprise to provide single sign-on (SSO) to CyberArk.
Steps
-
Go to Administration → Options.
-
Expand Authentication Methods, and then select saml.
-
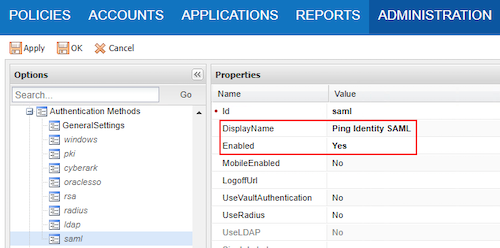
In the Properties pane, enter a name in the DisplayName field to be displayed in the PVWA sign-on page.
-
In the Enabled field, enter Yes.
Choose a name that clearly identifies Ping Identity.
-
Go to Administration → Options
-
In the Options pane, select Access Restriction.
-
Right-click Access Restriction, and in the context menu, select Add Allowed Referrer.
-
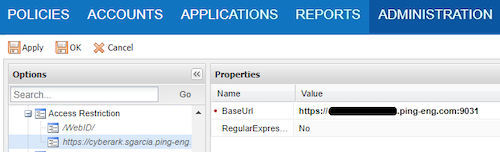
In the Properties pane, in the BaseUrl field, enter the URL of your Ping Identity tenant host.
-
In the Regular Expression field, enter No. Click Apply.
Your changes are saved when the Your changes have been saved successfully modal appears.
-
Open the PVWA
web.configfile and in the<appSettings>section, add the following key and value pairs:-
addkey="IdentityProviderLoginURL" value="your identity provider login URL" -
addkey="IdentityProviderCertificate" value="your certificate"Get an ASCII export of the certificate and remove all CR’s to make the entry a single line.
-
addkey="Issuer" value="PasswordVault"PasswordVaultis the default value.
-
-
Save the file and restart IIS.
Product integration and overview
Product integration description and diagram
-
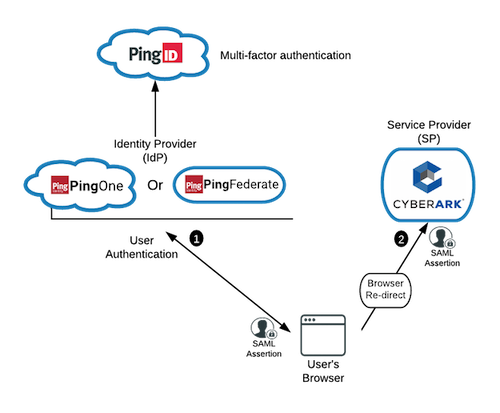
The user initiates an identity provider (IdP) URL to access CyberArk. The IdP solution (PingOne for Enterprise or PingFederate) validates the user through the configured authentication flow.
(Not shown) Alternatively, the user could attempt to access CyberArk directly. CyberArk would redirect the user to step 1 with a SAML request to validate the user.
-
PingFederate or PingOne for Enterprise invokes the PingID MFA process.
-
After the MFA process is completed, the IdP solution redirects the user’s browser to CyberArk with a SAML assertion.
-
(Not shown) CyberArk validates the SAML assertion and grants access.
PingFederate overview
PingFederate enables:
-
Outbound and inbound solutions for SSO
-
Federated identity management
-
Customer identity and access management (CIAM)
-
Mobile identity security
-
API security
-
Social identity integration
Browser-based SSO extends employee, customer, and partner identities across domains without passwords, using only standard identity protocols, such as SAML, WS-Fed, WS-Trust, OAuth and OpenID Connect, and SCIM. For more information, see PingFederate Introduction.
PingOne for Enterprise Overview
PingOne for Enterprise is a cloud-based identity as a service (IDaaS) framework for secure identity access management. Use PingOne for Enterprise to give members of your organization secure SSO to cloud applications. For more information, see PingOne for Enterprise overview.
PingID Overview
PingID is a cloud-based authentication service that binds user identities to devices. During the PingID authentication process, the PingID service sends an authentication request to the user’s device, requiring no password response: the user just swipes to authenticate. For more information, see introduction to PingID.