Configuring OIDC authentication for AWS EKS clusters
Open ID Connect (OIDC) supports authentication for Amazon Web Services (AWS) Elastic Kubernetes Service (EKS) clusters. You can configure PingOne as an identity provider (IdP) to provide strong user authentication to your EKS clusters.
Integrating OpenID Connect (OIDC) within AWS EKS involves creating a PingOne OIDC application and configuring the kubectl CLI for OIDC.
You can use the PingOne IdP as an alternative, or in addition, to AWS Identity and Access Management (IAM). With this feature, you can manage user access to your cluster by leveraging an existing identity management life cycle through your OIDC identity provider.
The features and benefits of this configuration are:
- Centralized Authentication Policy
-
User authentication to the EKS can leverage the centralized PingOne Identity Provider policy.
- Extended Multi-Factor Authentication
-
By using PingOne, strong multi-factor authentication can be extended to your EKS user authentication.
- Strengthened security using PingOne Protect
-
By analyzing multiple risk signals, PingOne Protect can identify anomalous activity to block attacks or require strong authentication methods, providing a greater level of assurance of your users’ identities.
Components
-
PingOne for Enterprise
-
AWS EKS cluster 1.6+
-
Kubelogin plugin for kubectl (https://github.com/int128/kubelogin)
Before you begin
Make sure you have the following:
-
A basic understanding of OIDC and OAuth 2.0 protocols
-
An understanding of JSON Web Tokens
-
A local installation of AWD CLI for configuring the OIDC integration within Amazon EKS
-
AWS CLI installed and configured to the existing AWS EKS Cluster
-
A PingOne for Enterprise account (https://www.pingidentity.com/en/trials/p14e-trial.html)
For more information, see Integrating an OIDC application.
Creating a PingOne OIDC application
About this task
To configure your AWS EKS cluster for OIDC authentication, you must first create a PingOne OIDC application to acquire the required OIDC Issuer URL and OIDC Client ID.
To create a PingOne OIDC application:
Steps
-
Sign on to your PingOne for Enterprise tenant.
-
Go to Applications → My Applications → OIDC.
-
Select Advanced Configuration, and click Next.
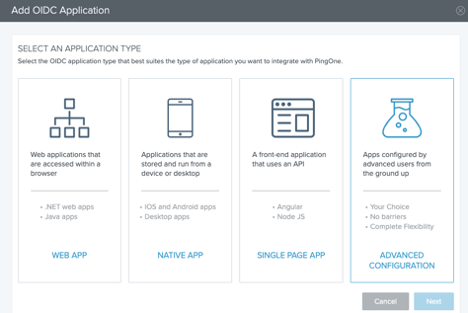
-
Type the Application Name and Description, and click Next.
-
In the Authorization Settings section, check Authorization Code for the Allowed Grant Types.
-
To include a client secret, click Add Secret. Record the Client ID and Client Secret for later use. Click Next.
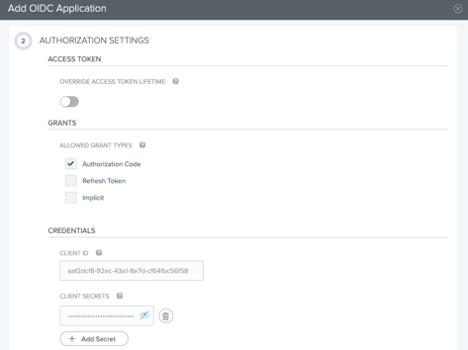
-
In the SSO Flow and Authentication Settings section, enter the following:
-
In the Start SSO URL field, enter
https://localhost. -
In the Redirect URIs field, enter
http://locallhost:8000andhttp://localhost:18000. -
Click Next.
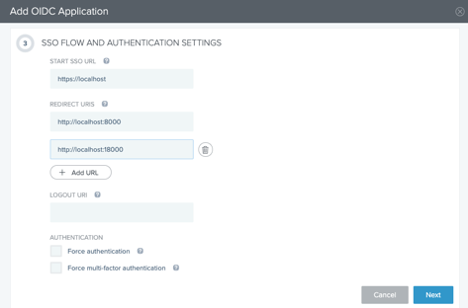
-
-
Leave the default configuration for Default User Profile Attribute Contract and Connect Scopes.
-
Configure the required Attribute Mapping for the
subjectattribute. Click Next.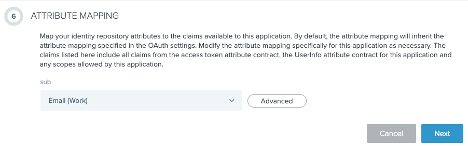
-
Assign any required PingOne Groups for access, and then click Done.
Configuring kubectl for OIDC
About this task
Configure the kubectl command line tool to work with OIDC.
Steps
-
Update your context to the cluster.
aws eks update-kubeconfig --name tech-partners --region us-west-2
-
Configure the kubectl OIDC login by using the Issuer URL, Client ID, and Client Secret created in the PingOne EKS application.
ubectl oidc-login setup --oidc-issuer-url=https://sso.connect.pingidentity.com/ 7e29215f-b6c3-42f5-9153-85147e3de93a --oidc-client-id=7e29215f-b6c3-42f5-9153-85147e3de93a --oidc-client-secret=nJ1GHnQzlmyhtOLMNNOOGokiYqPc7YaZ3p7clTbF3m9KuYkdHTxfPJV53P7KovVnO
-
Bind a Cluster Role to a PingOne account.
kubectl create clusterrolebinding oidc-cluster-admin --clusterrole=cluster-admin --user='https://sso.connect.pingidentity.com/7e29215f-b6c3-42f5-9153-85147e3de93a #emma.sharp@pingidentity.com'
-
Set up the kubeconfig with the OIDC PingOne configuration.
kubectl config set-credentials oidc \ --exec-api-version=client.authentication.k8s.io/v1beta1 \ --exec-command=kubectl \ --exec-arg=oidc-login \ --exec-arg=get-token \ --exec-arg=--oidc-issuer-url=https://sso.connect.pingidentity.com/ 7e29215f-b6c3-42f5-9153-85147e3de93a \ --exec-arg=--oidc-client-id=7e29215f-b6c3-42f5-9153-85147e3de93a \ --exec-arg=--oidc-client- secret=nJ1GHnQzlmyhtOLMNNOOGokiYqPc7YaZ3p7clTbF3m9KuYkdHTxfPJV53P7KovVnO --exec-arg -v1
The
--exec-arg -v1sets kubectl to verbose logging, which is useful for troubleshooting.
Result
OIDC for EKS is configured, and PingOne users can authenticate to EKS by executing any kubectl command.
Authenticating to EKS
After you have configured OIDC for EKS, PingOne users can execute the kubectl command to authenticate to EKS.
Executing kubectl get svc opens a new window in the user’s default browser and redirects them to authenticate with PingOne.
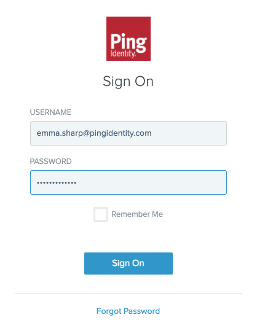
Upon successful authentication, PingOne redirects the user to the Kubelogin successful login page, indicating that they are now authenticated to the cluster.
With verbose kubectl logging enabled, the output of the kubectl get svc command is shown here.
I0408 16:45:16.147985 34902 get_token.go:53] WARNING: log may contain your secrets such as token or password
I0408 16:45:16.148119 34902 get_token.go:60] acquiring a lock get-token-8000-18000
I0408 16:45:16.148190 34902 get_token.go:72] finding a token from cache directory /Users/peterholko/.kube/cache/oidc-login
I0408 16:45:16.148501 34902 authentication.go:76] checking expiration of the existing token
I0408 16:45:16.148566 34902 authentication.go:85] you already have a valid token until 2021-04-08 16:46:39 -0700 PDT
I0408 16:45:16.148607 34902 get_token.go:104] you got a token: {
"sub": "emma.sharp@pingidentity.com",
"aud": "7e29215f-b6c3-42f5-9153-85147e3de93a",
"acr": "urn:oasis:names:tc:SAML:2.0:ac:classes:Password",
"idpid": "db6dccae-f491-426d-a16e-052eb4214011",
"auth_time": 1617925299,
"iss": "https://sso.connect.pingidentity.com/7e29215f-b6c3-42f5-9153-85147e3de93a",
"exp": 1617925599,
"iat": 1617925299,
"nonce": "rsWXrEH2MT5JPaBBPMU6PJ_s3kepPbkBtgcG_X7Orfo"
}
I0408 16:45:16.148620 34902 get_token.go:107] you already have a valid token until 2021-04-08 16:46:39 -0700 PDT
I0408 16:45:16.148630 34902 get_token.go:114] writing the token to client-go
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes ClusterIP 10.100.0.1 <none> 443/TCP 8d