Device Profile Collector node
The Device Profile Collector node collects metadata about the user’s device, and optionally the device location.
The amount and type of data collected depends on whether you’re using the Ping SDKs or not.
- Without the SDKs (browser-only collection)
-
If you aren’t using the Ping SDKs, the device details are limited to those collected by the web browser.
Examples of collected data include:
-
User-agent string
-
Screen resolution and color depth
-
Browser language and timezone
-
A unique identifier generated from HTML5 canvas fingerprinting
-
- With the SDKs
-
The Ping SDKs have built-in support for device-profiling nodes, which lets you collect richer device information.
When the client application uses the Ping SDKs, the SDK intercepts the
DeviceProfileCallbackand collects additional device information.In addition to the data available from the web browser, the SDKs can collect the following types of information:
-
Hardware: Device manufacturer, model, CPU architecture, and memory.
-
Operating System: OS version, build number, and kernel version.
-
Security: Whether the device is rooted or jailbroken, and the status of disk encryption.
-
Network: IP address and MAC address of network interfaces.
-
|
It’s up to you what information you collect from users and devices. Always use data responsibly and provide your users with appropriate control over data they share with you. You’re responsible for complying with any regulations or data protection laws. |
Use this node with the Device Profile Save node to create a trusted profile from the collected data. You can use the trusted device profile in subsequent authentication attempts. For example, with the Device Match node and Device Location Match node.
Examples
Example 1: Device profiling journey
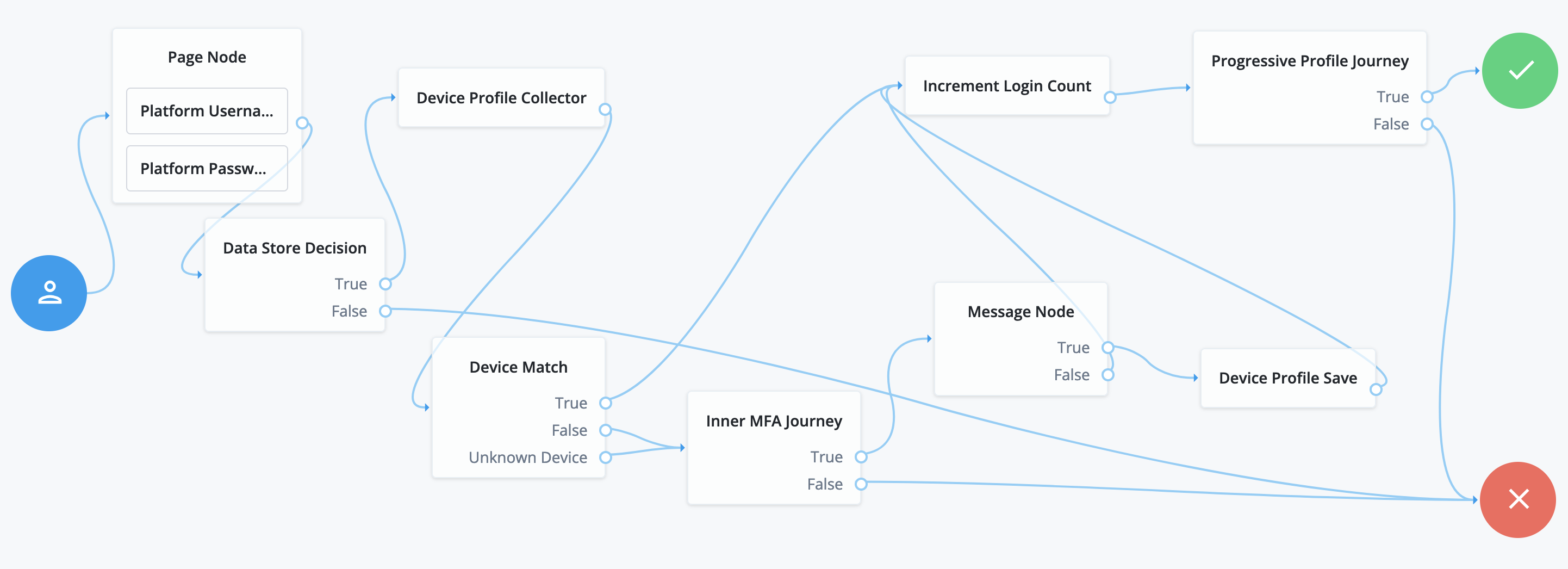
The following journey authenticates the user and checks whether the current device is trusted. If the device isn’t trusted yet, the journey requires an additional authentication factor and lets the user opt to trust the device:
-
The Page node containing the Platform Username node and Platform Password node prompts for credentials.
-
The Data Store Decision node validates the username-password credentials.
-
The Device Profile Save node collects metadata about the current device.
-
The Device Profile Collector node compares saved device profiles with the current device.
-
The Inner MFA Journey, an Inner Tree Evaluator node, requires an additional authentication factor.
-
The Message node prompts the user with an option to trust the current device.
-
The Device Profile Save node saves the current device profile.
-
The Increment Login Count node updates the number of successful authentications.
-
The Progressive Profile Journey, an Inner Tree Evaluator node, invokes a journey to collect additional profile data.
Example 2: Device profiling journey with location matching
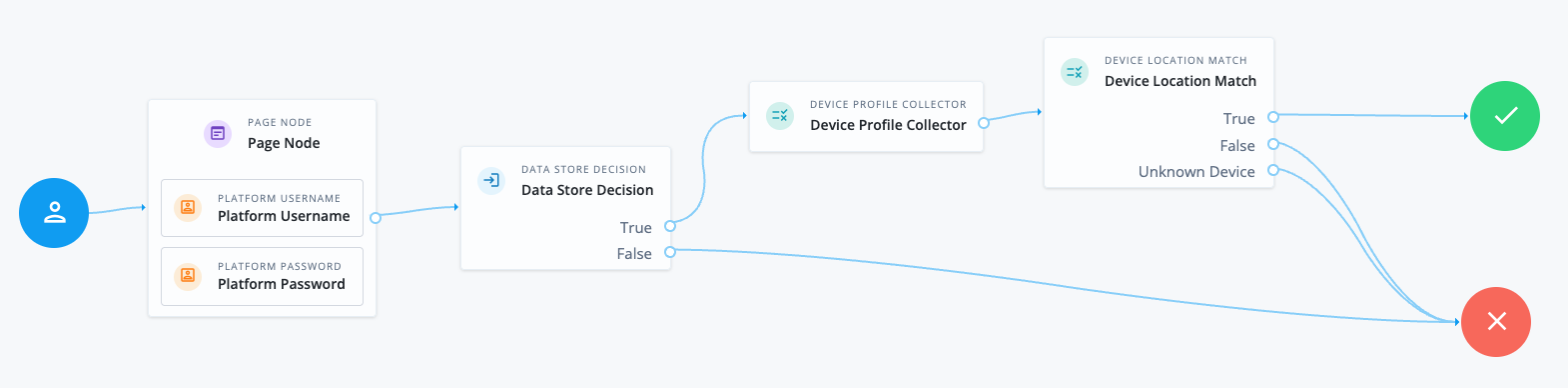
The following journey authenticates the user and checks whether the current device is located within ten kilometers of a previously saved device location.
If the user doesn’t have a saved device that matches the current device identifier or the device location is outside of this range, authentication fails:
-
The Page node containing the Platform Username node and Platform Password node prompts for credentials.
-
The Data Store Decision node validates the username-password credentials.
-
The Device Profile Collector node collects metadata about the current device, including the device’s location.
-
The Device Location Match node compares saved device location details with the current device’s location.
Example 3: Device profiling with trusted locations
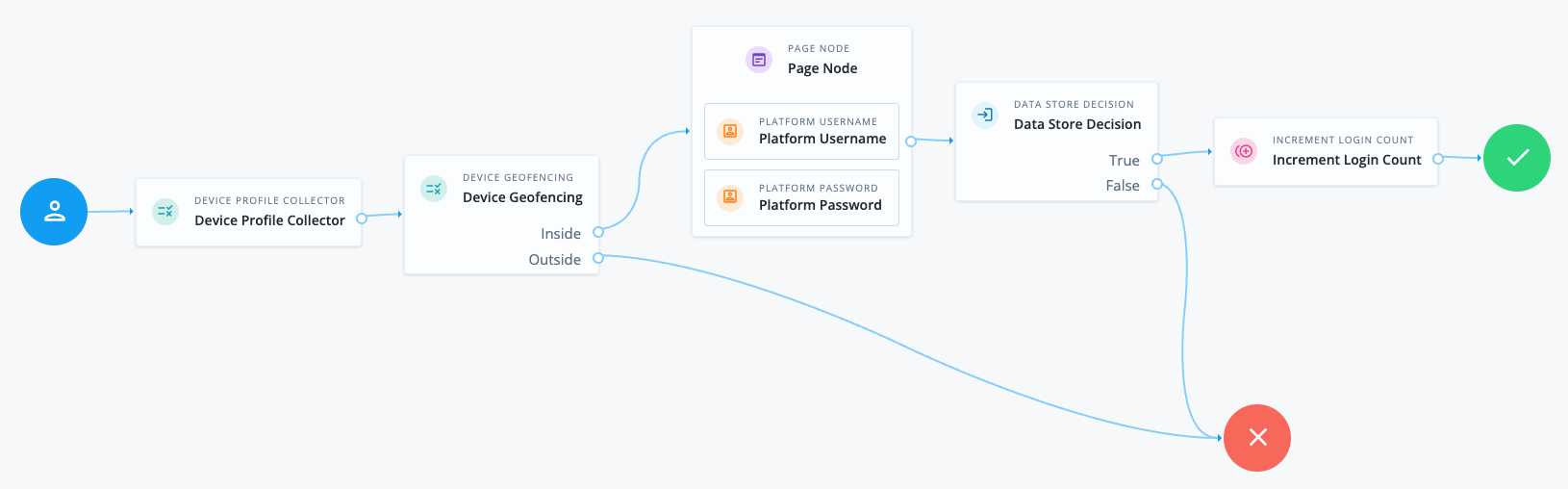
The following journey checks whether the user’s device is located within ten kilometers of their company’s office locations. If the device’s location is within this range from one of the offices, the journey proceeds and prompts the user to authenticate. If the device’s location is outside this range from all of the offices, authentication fails:
-
The Device Profile Collector node collects metadata about the current device, including the device’s location.
-
The Device Geofencing node compares the current device’s location with the specified trusted locations. In this example, the trusted locations are the company’s offices.
-
The Page node containing the Platform Username node and Platform Password node prompts for credentials.
-
The Data Store Decision node validates the username-password credentials.
-
The Increment Login Count node updates the login count on successful authentication.
Example 4: Device profiling with tampered device verification
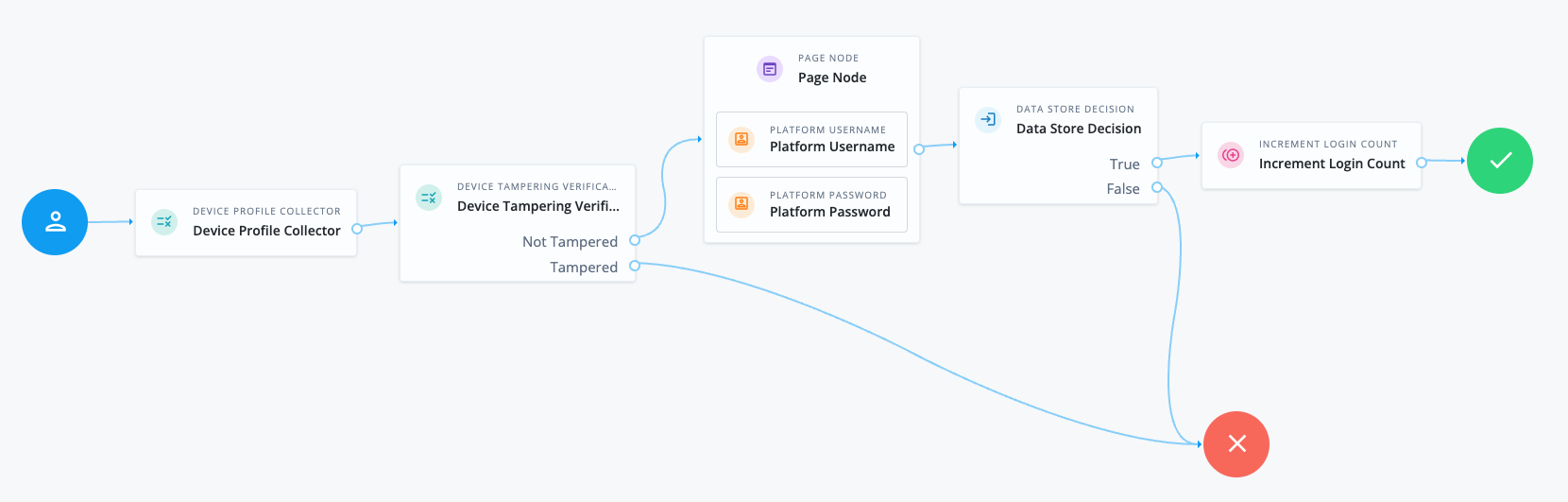
The following journey determines the likelihood that the user’s device has been tampered with or poses a security risk. If the device scores below or equal to the set threshold, the journey proceeds and prompts the user to authenticate. If the device scores more than the set threshold, authentication fails:
-
The Device Profile Collector node collects metadata about the current device.
-
The Device Tampering Verification node determines the likelihood that the user’s device has been tampered with or poses a security risk.
-
The Page node containing the Platform Username node and Platform Password node prompts for credentials.
-
The Data Store Decision node validates the username-password credentials.
-
The Increment Login Count node updates the login count on successful authentication.
Availability
| Product | Available? |
|---|---|
PingOne Advanced Identity Cloud |
Yes |
PingAM (self-managed) |
Yes |
Ping Identity Platform (self-managed) |
Yes |
Configuration
| Property | Usage |
|---|---|
Maximum Profile Size (KB) |
The maximum accepted size, in kilobytes, of a device profile. If the collected profile data exceeds this size, authentication fails. Default: |
Collect Device Metadata |
Select this option to request device metadata. |
Collect Device Location |
Select this option to request device location. When selected, the browser prompts the user to consent to their location being shared. The browser connection must be secure. |
Message |
(Optional) Add custom, localized text to display to the user while the node collects the requested data. Add instructions
Leave blank to use the default message. |
(1) Specify a
locale that Java supports, such as en-gb. Otherwise, the node throws a configuration exception with an Invalid locale provided message.
Outputs
The node writes the device metadata to the forgeRock.device.profile shared state object if the Collect Device Metadata option is selected.
The device metadata includes the device name.
This is either obtained from the shared state if available or is derived from the platform being used.
For example Mac (Browser) is the device name given when the device is a web browser on the Mac operating system.
If the Collect Device Location option is also selected and the user consents,
the device location details are included in this object under the location attribute.
In addition to the collected metadata, the shared state includes an identifier,
which uniquely identifies the device through the journey.
Callbacks
The node sends a DeviceProfileCallback to the client application to collect metadata about the user’s device.
Learn more in DeviceProfileCallback.