Device Tampering Verification node
The Device Tampering Verification node specifies a threshold for deciding if the device has been tampered with. For example, if it has been rooted or jailbroken.
The device scores between zero and one,
based on the likelihood that it’s been tampered with or may pose a security risk.
For example, an emulator scores the maximum of 1.
Use this node with the Device Profile Collector node to retrieve the tampering score from the device.
Example
The following journey determines the likelihood that the user’s device has been tampered with or poses a security risk. If the device scores below or equal to the set threshold, the journey proceeds and prompts the user to authenticate. If the device scores more than the set threshold, authentication fails:
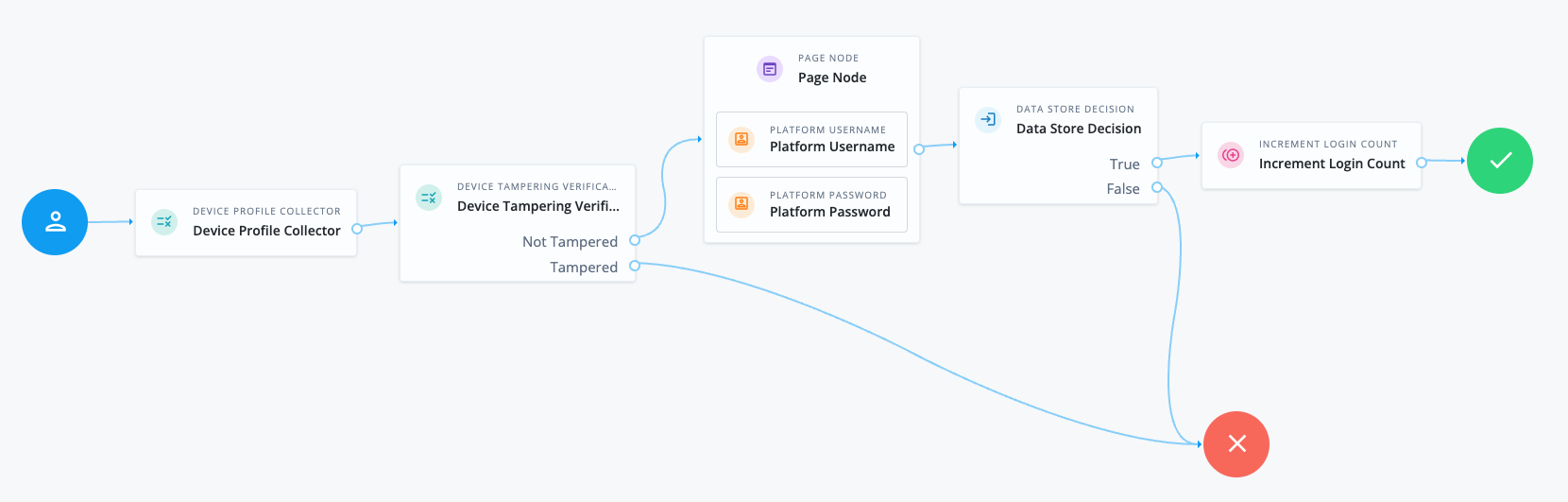
-
The Device Profile Collector node collects metadata about the current device.
-
The Device Tampering Verification node determines the likelihood that the user’s device has been tampered with or poses a security risk.
-
The Page node containing the Platform Username node and Platform Password node prompts for credentials.
-
The Data Store Decision node validates the username-password credentials.
-
The Increment Login Count node updates the login count on successful authentication.
Availability
| Product | Available? |
|---|---|
PingOne Advanced Identity Cloud |
Yes |
PingAM (self-managed) |
Yes |
Ping Identity Platform (self-managed) |
Yes |
Inputs
This node reads the collected device metadata from the shared state.
Implement a Device Profile Collector node earlier in the journey to collect metadata for the current device.
Configuration
| Property | Usage |
|---|---|
Score Threshold |
The score threshold for determining if a device has been tampered with.
Enter a decimal fraction, between The higher the score returned from the device, the more likely the device is jailbroken, rooted, or is a potential security risk. Emulators score the maximum, |