Creating WS-Federation connection on the PingFederate server
Set up a WS-Federation connection with PingFederate to establish federation with the SharePoint server.
Before you begin
-
Have a fully created and functional Web Application with federated authentication.
Steps
-
Open the PingFederate Admin console.
-
Go to System → Server → Protocol Settings.
-
On the Roles & Protocols tab, select the Enable Service Provider (SP) Role and Support the Followingcheckbox, and then select the WS-Federation checkbox below. Click Save.
-
Go to Identity Provider → SP Connections. Click Create New.
-
On the Connection Template tab, click Do Not Use a Template for This Connection. Click Next.
-
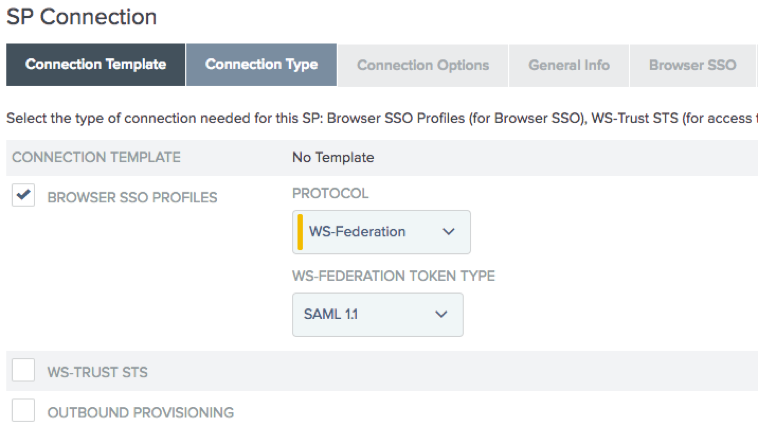
On the Connection Type tab, select the Browser SSO Profiles checkbox.
-
From the Protocol list, select WS-Federation.
-
From the WS-Federation Token Type list, select SAML 1.1. Click Next.
-
-
On the Connection Options tab, keep the default settings. Click Next.
-
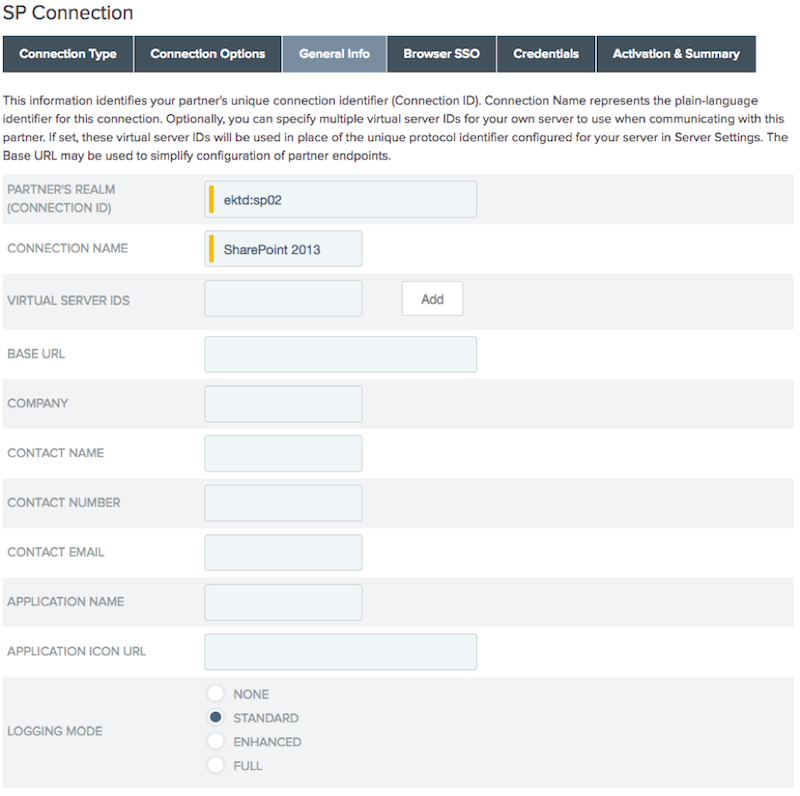
Complete the General Info tab.
-
In the Partner’s Realm (Connection ID) field, enter the partner’s unique connection identifier.
-
In the Connection Name field, enter a name for the connection. Click Next.
The Partner’s Realm can be an arbitrary value.
-
-
On the Browser SSO tab, click Configure Browser SSO.
-
Complete the Assertion Lifetime tab.
-
In the Minutes Before field, enter
15. -
In the Minutes After field, enter
15. Click Next.
-
-
On the Assertion Creation tab, click Configure Assertion Creation.
-
On the Identity Mapping tab, click User Principal Name. Click Next.
Configure the identity claim type on the SharePoint server for different attributes like email address, UPN or common name.
-
Complete the Attribute Contract tab.
-
In the Extend the Contract field, enter
upn. -
From the Attribute Name Format list, select http://schemas.xmlsoap.org/ws/2005/05/identity/claims.
-
Click Add, and then click Next.
The attribute names are case-sensitive. They should match the claim type names configured for the Trusted Identity Provider on the SharePoint server.
-
-
On the Authentication Source Mapping tab, add a mapping of your choice. Choose one of the following options.
Choose from:
-
Map New Adapter Instance
-
Map New Authentication Policy
-
-
Depending on your choice, from the Authentication Policy Contract list select an authentication policy contract, or from the Adapter Instance list select the adapter instance. Click Next.
If you do not have an Authentication Policy Contract or an Adapter Instance created, click Manage Authentication Policy Contracts or Manage Adapter Instance and configure the authentication source mapping as needed.
For more information, see Policy contracts and Manage IdP Adapters in the PingFederate documentation.
-
On the Mapping Method tab, select Retrieve Additional Attributes From Multiple Data Stores Using One Mapping.
Result:
This selection retrieves the UPN value from an LDAP Data Store.
-
On the Attribute Sources & User Lookup tab, click Add Attribute Store and select an existing data store under Active Data Store or create a new one.
For more information, see Data Stores in the PingFederate documentation.
-
On the LDAP Directory Search tab, enter the base DN details in the Base DN field.
-
In the attribute list, add userPrincipalName to the list of attributes returned from search. Click Next.
-
In the Filterfield, enter a name for the filter. Click Next.
-
Click Done.
-
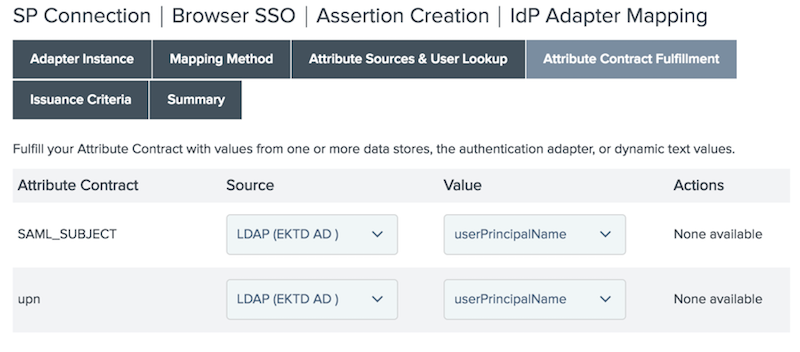
On the Attribute Contract Fulfillment tab, select the attribute contract source from the Source list, and the value from the Value list for each attribute contract. Click Next.
-
If necessary, complete the Issuance Criteria tab. Click Next.
The Issuance Criteria tab is not required to continue.
-
On the Summary tab, review the information and click Done.
-
On the Authentication Source Mapping tab, click Next.
-
On the Summary tab, click Done.
-
On the Assertion Creation tab, click Next.
-
On the Protocol Settings tab, click Configure Protocol Settings.
-
On the Service URL tab, in the Endpoint URL field enter the Endpoint URL. Click Next.
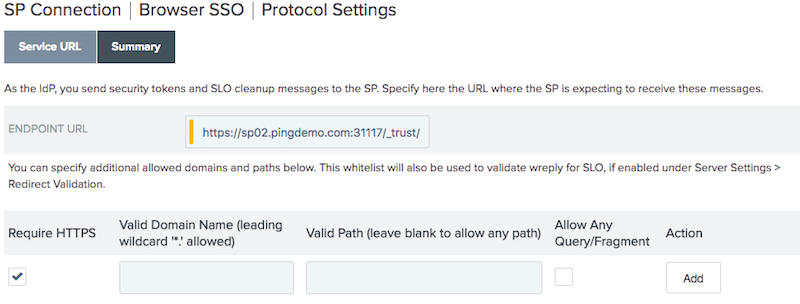
Construct the Endpoint URL by adding
/_trust/at the end of the SharePoint Web Application URL. In order to support multiple web applications on the same connection, see Additional configuration options. -
On the Summary tab, click Done.
-
On the Protocol Settings tab, click Next.
-
On the Summary tab, click Done.
-
On the Browser SSO tab, click Next.
-
On the Credentials tab, click Configure Credentials.
-
On the Digital Signature Settings tab, from the Signing Certificatelist, select your signing certificate.
-
From the Signing Algorithm list, select the Signing Algorithm. Click Next.
-
On the Summary tab, click Done.
-
On the Credentials tab, click Next.
-
On the Activation & Summary tab, review the connection settings and set the Connection Status to Active. Click Save.