ASE deployment modes
API Security Enforcer (ASE) supports REST and WebSocket APIs and can dynamically scale and secure system infrastructure.
ASE can be deployed in inline or sideband mode.
Inline mode
In the inline deployment mode, ASE sits at the edge of your network to receive the API traffic. It can also be deployed behind an existing load balancer, such as AWS ELB. In inline mode, ASE deployed at the edge of the datacenter terminates SSL connections from API clients. ASE then forwards the requests directly to the correct APIs and app servers, such as Node.js, WebLogic, Tomcat, PHP, etc.
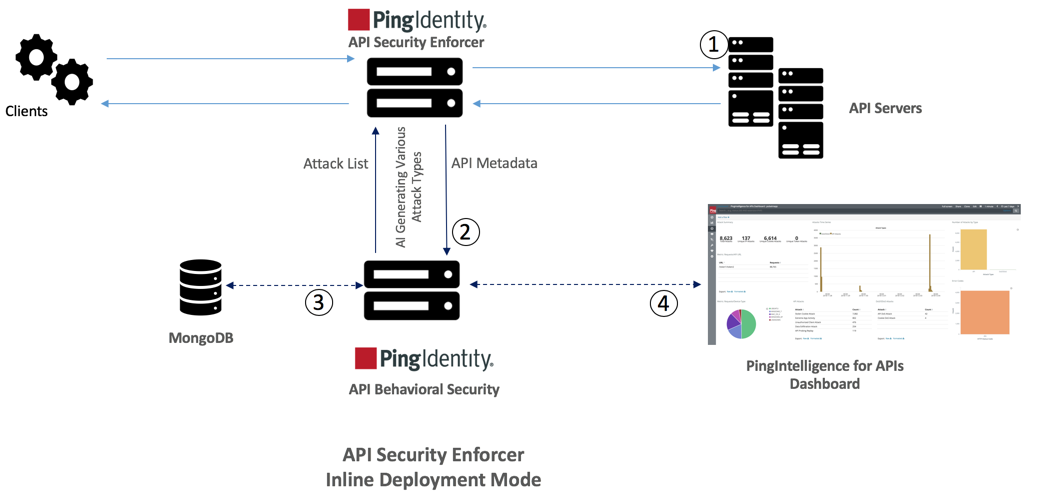
To configure ASE to work in the inline mode, set mode=inline in the /opt/pingidentity/ase/config/ase.conf file.
Some load balancers (for example, AWS ELB) require responses to keep alive messages from all devices receiving traffic. In an inline mode configuration, ASE should be configured to respond to these keep alive messages by updating the enable_ase_health variable in the /opt/pingidentity/ase/config/ase.conf file. When enable_ase_health is true, load balancers can perform an ASE health check using the following URL: http(s)://<ASE Name>/ase where <ASE Name> is the ASE domain name. ASE will respond to these health checks.
Sideband mode
When deployed in sideband mode, ASE works behind an existing API gateway. The API request and response data between the client and the backend resource or API server is sent to ASE. In this case, ASE does not directly terminate the client requests.
To configure ASE to work in inline mode, set mode=sideband in the /opt/pingidentity/ase/config/ase.conf file.
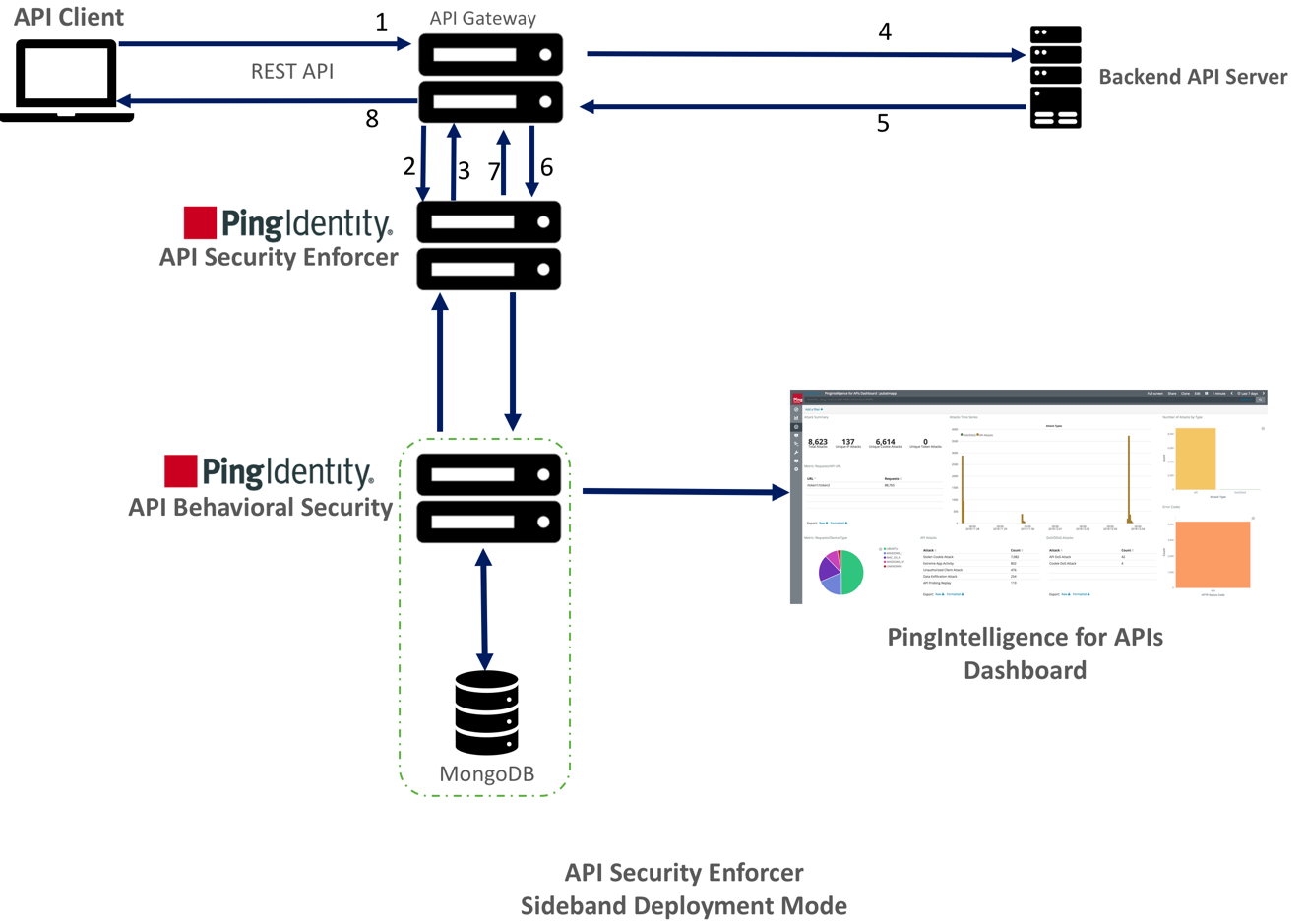
The following is a description of the traffic flow through the API gateway and Ping Identity ASE.
-
The API client sends a request to the API gateway.
-
The API gateway makes an API call to send the request detail in JSON format to ASE
-
ASE checks the request against a registered set of APIs and checks the origin IP against the AI-generated deny list. If all checks pass, ASE returns a
200-OKresponse to the API gateway. Otherwise, a different response code is sent to the gateway. The request is also logged by ASE and sent to the AI engine for processing. -
If the API gateway receives a
200-OKresponse from ASE, then it forwards the request to the backend server. Otherwise, the gateway returns a different response code to the client. -
The response from the backend server is received by the API gateway.
-
The API gateway makes a second API call to pass the response information to ASE, which sends the information to the AI engine for processing.
-
ASE receives the response information and sends a
200-OKto the API gateway. -
API gateway sends the response received from the backend server to the client.
|
To complete the ASE sideband mode deployment, see the Integrate API gateways for sideband deployment. |