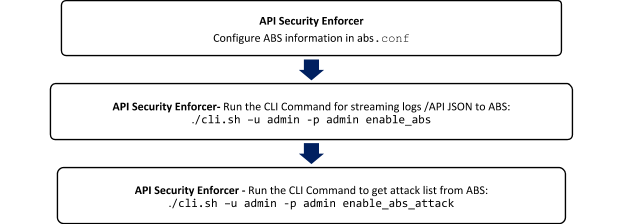
Connect ABS to ASE
Before connecting API Behavioral Security (ABS), API Security Enforcer (ASE) must be installed.
For more information on installing and configuring ASE, see the ASE Admin guide.
The following diagram summarizes the process of connecting ABS to ASE:
The following is a sample abs.conf file which is part of the ASE:
; API Security Enforcer ABS configuration. ; This file is in the standard .ini format. The comments start with a semicolon (;). ; Following configurations are applicable only if ABS is enabled with true. ; a comma-separated list of abs nodes having hostname:port or ipv4:port as an address. abs_endpoint=127.0.0.1:8080 ; access key for abs node access_key=OBF:AES://ENOzsqOEhDBWLDY+pIoQ:jN6wfLiHTTd3oVNzvtXuAaOG34c4JBD4XZHgFCaHry0 ; secret key for abs node secret_key=OBF:AES:Y2DadCU4JFZp3bx8EhnOiw:zzi77GIFF5xkQJccjIrIVWU+RY5CxUhp3NLcNBel+3Q ; Setting this value to true will enable encrypted communication with ABS. enable_ssl=true ; Configure the location of ABS's trusted CA certificates. If empty, ABS's certificate ; will not be verified abs_ca_cert_path=
The access_key and secret_key are the keys that were defined in the abs_init.js file when configuring MongoDB.
|
To connect an ASE to ABS, configure the |
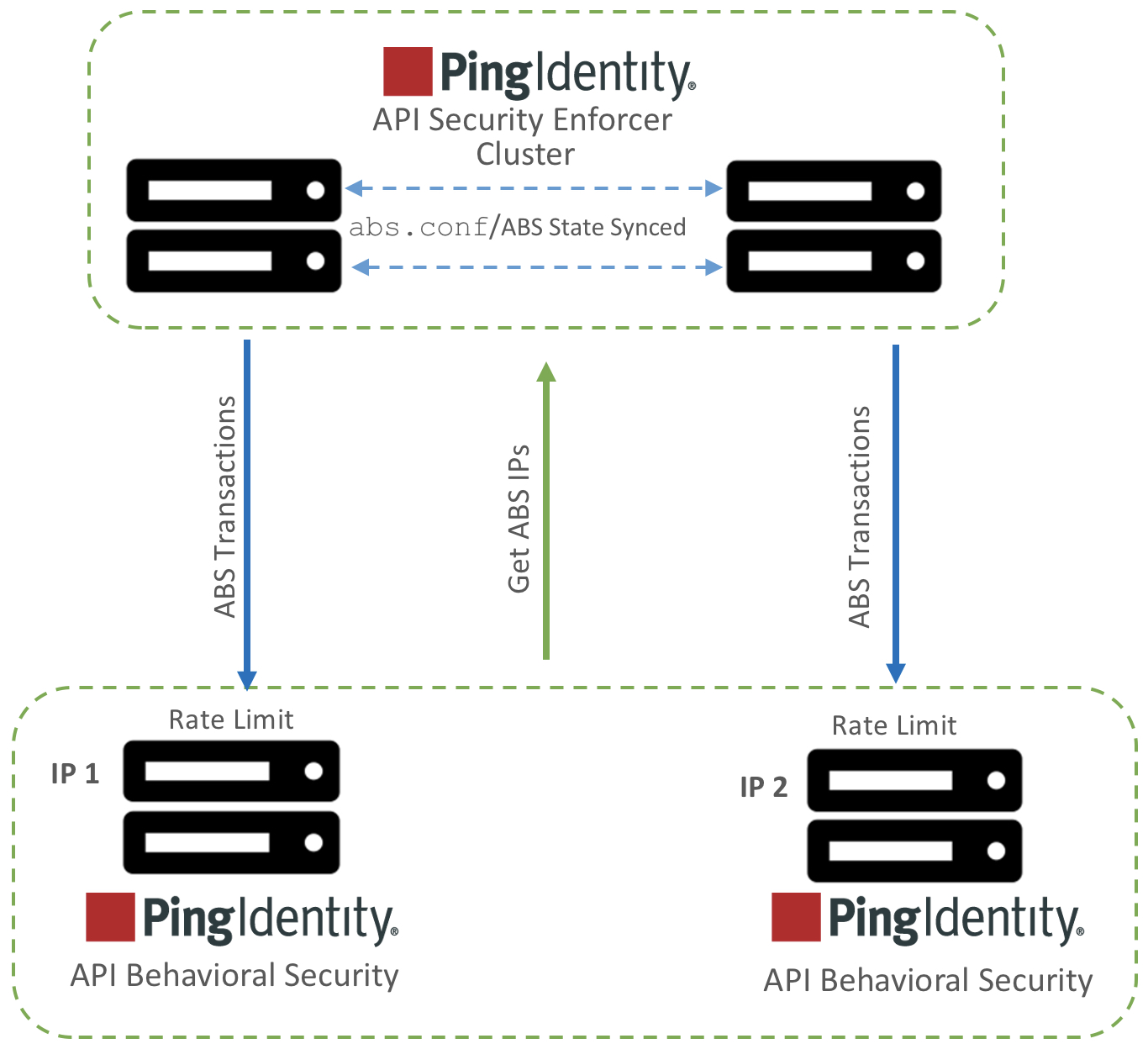
If ABS is running in cluster mode, choose the Internet Protocol (IP) address and port from any ABS node to add to the abs.conf file in ASE.
Dataflow
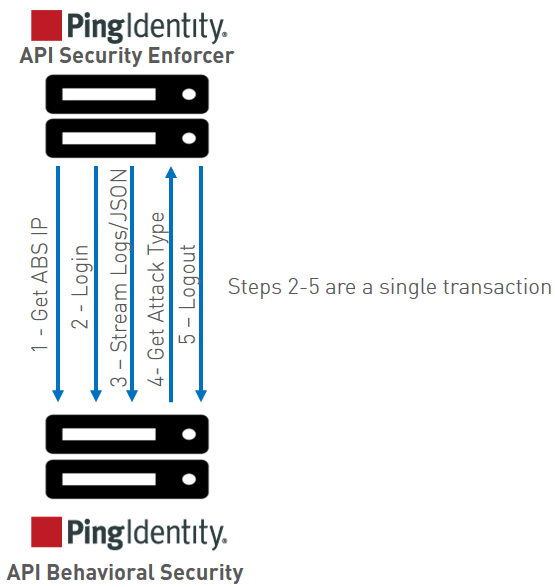
ASE to the ABS node defined in abs.conf to obtain available ABS IP addresses (step 1). In stand-alone mode, ABS sends the only IP address. In cluster mode, ABS sends the IP addresses of all available ABS nodes to ASE.
After ASE receives the IP address, it establishes a session with ABS by sending the secret and access keys (step 2). After successful authentication, ASE streams the access log files and API JSON files to the ABS node (step 3). After sending the files, it receives the attack lists (only available if blocking is activated for ASE) from ABS (step 4). When the transaction is complete, ASE logs out from ABS (step 5).
ABS uses machine learning algorithms to discover attacks, anomalies, and other traffic information. It stores incoming ASE logs and then passes these logs to the machine learning engine for analysis. In high load environments, a single ABS node may not be able to process all log files, and multiple ABS nodes should be deployed for log processing.
The following diagrams show the ASE – ABS Dataflow.
Stand-alone mode
In stand-alone mode, a single MongoDB node is used for both read and write operations. A stand-alone mode of deployment is only recommended for testing purposes.
Cluster mode
In cluster mode, ASE nodes synchronize the abs.conf file as well as the state of each ABS node. The ABS cluster nodes do not communicate among themselves. Each node records its status in MongoDB and reads about the state of other nodes from the database.