Akana API gateway sideband integration
This integration guide discusses PingIntelligence for APIs deployment in a sideband configuration with the Akana API Gateway.
PingIntelligence for APIs in a sideband deployment mode integrates with the Akana API Gateway to provide in-depth analytics on API traffic. A PingIntelligence policy is installed in the Policy Manager component of the Akana API Gateway to pass API metadata to PingIntelligence for detailed API activity reporting and attack detection. For more information on sideband deployment, see Sideband ASE.
PingIntelligence for APIs provides the JavaScript policy that extracts API metadata from a request and response processed by the Akana API Gateway. The API metadata is passed to API Security Enforcer (ASE). The following are a few highlights of the integration solution:
-
Support for SSL connectivity through a valid certificate authority (CA)-signed certificate.
-
Support for connection keep alive between the Akana Gateway and ASE for faster processing of request and response data.
-
Support for ASE-failover by provisioning a secondary ASE.
-
OAuth attribute extraction and username support for OAuth-enabled APIs.
-
Interception of OAuth tokens sent as part of query parameters.
|
The Akana Gateway does not support self-signed certificates. |
Three PingIntelligence policies are made available to support the integration. The policies are packaged in the pi-api-akana-policy-4.x.x.tar.gz file. The following diagram shows the directory structure for reference.
pi_policy.js: This is the main PingIntelligence policy. It extracts the metadata for each API call, formats it into JSON and makes API calls to pass the metadata to ASE.
retain-header-policy.js: After validating a token with the OAuth server, Akana gateway deletes the incoming Authorization header. As a result, this header does not get forwarded to ASE. The retainHeader.js remedies this by capturing the deleted Authorization header and passes it to pi_policy.js for metadata extraction. The retainHeader.js policy gets executed before pi_policy.js.
config.js: This script takes ASE configuration as input from the user. The script then connects the ASE nodes and the policy.
|
The |
The following diagram shows the logical setup of PingIntelligence for APIs components and the Akana API Gateway:
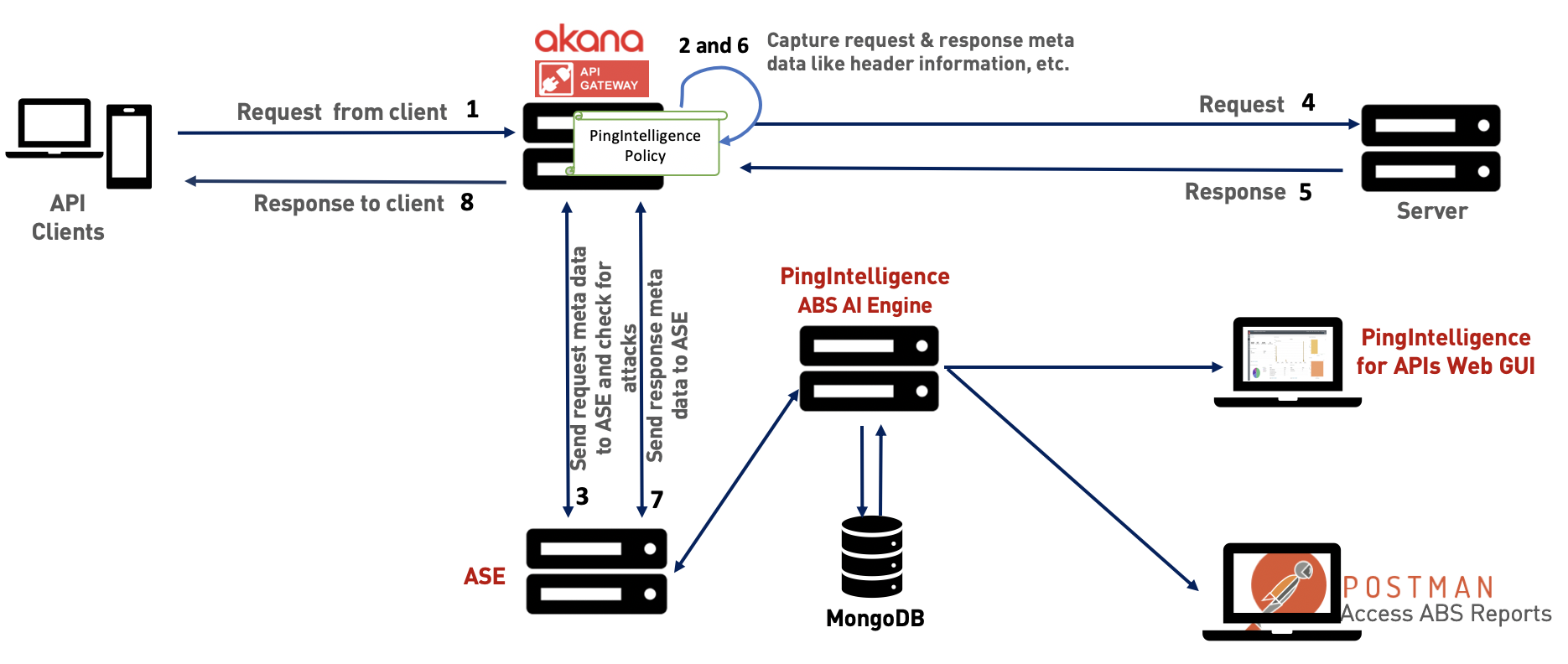
The traffic flow through the Akana API Gateway and PingIntelligence for APIs components is explained below:
-
The client sends an incoming request to Akana API gateway.
-
PingIntelligence policy deployed on the Akana API Gateway is executed on the request to extract the metadata from the incoming request.
-
Akana API gateway makes an API call to send the request metadata to API Security Enforcer (ASE). The ASE checks the client identifiers, such as usernames and tokens, against the deny list. If all checks pass, ASE returns a
200-OKresponse to the Akana API gateway. If not, a different response code is sent to the Akana API Gateway (400 or 403). The request information is also logged by ASE and sent to the PingIntelligence API Behavioral Security (ABS) artificial intelligence (AI) engine for processing. -
The Akana API gateway forwards the API requests to the backend server after the ASE processes it. If the gateway receives a
403-Forbiddenresponse from ASE, it blocks the client. Otherwise, it forwards the request to the backend server. -
The response from the backend server is received by the Akana API Gateway.
-
The PingIntelligence policy is again applied on the response to extract the metadata from the server response.
-
The Akana API gateway makes a second API call to pass the response information to ASE, which sends the information to the AI engine for processing. ASE sends a
200-OKto the API Gateway. -
The Akana API gateway sends the response received from the backend server to the client.