Configuring SSL for management APIs
API Security Enforcer (ASE) supports both TLS 1.2 and Secure Sockets Layer (SSL)3 for management application programming interface (API)s.
OpenSSL is bundled with ASE. The following are the version details:
-
RHEL 7 : OpenSSL 1.0.2k-fips 26 Jan 2017
-
Ubuntu 16LTS: OpenSSL 1.0.2g 1 Mar 2016
You can configure SSL in ASE for management APIs using one of the following methods:
-
Using a Certificate Authority (CA)-signed certificate
-
Using a self-signed certificate
-
Using an existing certificate
The steps provided in this section are for certificate and key generated are for connections between a management API client and ASE:

In a cluster setup:
-
Stop all the ASE cluster nodes.
-
Configure the certificate on the management node.
-
Start the cluster nodes one by one for the certificates to synchronize across the nodes.
Using a CA-signed certificate
To use Certificate Authority (CA) signed SSL certificates, follow the process to create a private key, generate a Certificate Signing Request (CSR), and request a certificate as shown below:
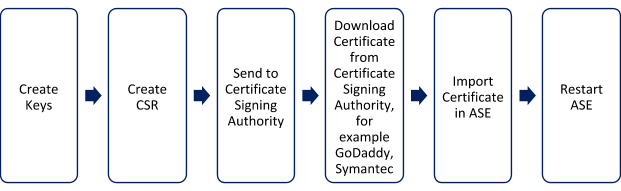
|
ASE internally validates the authenticity of the imported certificate. |
To use a CA-signed certificate:
-
Create a private key. ASE command-line interface (CLI) is used to create a 2048-bit private key and to store it in the
/opt/pingidentity/ase/config/certs/managementdirectory./opt/pingidentity/ase/bin/cli.sh create_management_key_pair -u admin -p Warning: create_management_key_pair will delete any existing management key_pair, CSR and self-signed certificate Do you want to proceed [y/n]:y Ok, creating new management key pair. Creating DH parameter may take around 20 minutes. Please wait Management key created at keystore Management dh param file created at /opt/pingidentity/ase/config/certs/management/dh1024.pem
-
Create a CSR. ASE takes you through a CLI-based interactive session to create a CSR.
/opt/pingidentity/ase/bin/cli.sh create_management_csr -u admin -p Warning: create_management_csr will delete any existing management CSR and self-signed certificate Do you want to proceed [y/n]:y please provide following info Country Code >US State >Colorado Location >Denver Organization >Pingidentity Organization Unit >Pingintelligence Common Name >management.ase Generating CSR. Please wait... OK, management csr created at /opt/pingidentity/ase/config/certs/management/management.csr
-
Upload the CSR created in step 2 to the CA signing authority’s website to get a CA signed certificate.
-
Download the CA-signed certificate from the CA signing authority’s website.
-
Use the CLI to import the signed CA certificate into ASE. The certificate is imported into the
/pingidentity/config/certs/management/management.csrfile/opt/pingidentity/ase/bin/cli.sh import_management_cert <CA signed certificate path> -u admin -p Warning: import_management_cert will overwrite any existing management signed certificate Do you want to proceed [y/n]:y Exporting management certificate to API Security Enforcer... OK, signed certificate added to keystore
-
Restart ASE by first stopping and then starting ASE.
Using a self-signed certificate
A self-signed certificate is also supported for customer testing.
To create a self-signed certificate
-
Create a private key. ASE CLI is used to generate a 2048-bit private key which is in the
/ase/config/certs/directory./opt/pingidentity/ase/bin/cli.sh create_management_key_pair -u admin -p Warning: create_management_key_pair will delete any existing management key_pair, CSR and self-signed certificate Do you want to proceed [y/n]:y Ok, creating new management key pair. Creating DH parameter may take around 20 minutes. Please wait Management key created at keystore Management dh param file created at /opt/pingidentity/ase/config/certs/management/dh1024.pem
-
Create a CSR. Enter the following command.
/opt/pingidentity/ase/bin/cli.sh create_management_csr -u admin -p password > Warning: create_csr will delete any existing CSR and self signed certificate Do you want to proceed [y/n]:y please provide following info Country Code >US State >colorado Location >Denver Organization >PingIdentity Organization Unit >PI Common Name >yoursiteabc.com Generating CSR. Please wait... OK, csr created at /opt/pingidentity/ase/config/certs/management/ase.csr
-
Create a self-signed certificate. Use the CLI to produce a self-signed certificate using the certificate request located in
/pingidentity/ase/config/certs/management/ase.csr/opt/pingidentity/ase/bin/cli.sh create_management_self_sign_cert -u admin -p Warning: create_management_self_sign_cert will delete any existing management self-signed certificate Do you want to proceed [y/n]:y Creating new management self-signed certificate OK, self-sign certificate created in key store
-
Restart ASE by stopping and starting.
Importing an existing certificate and key pair
To install an existing certificate, complete the following steps and import it into ASE. If you have intermediate certificate from CA, then append the content to your server .crt file.
-
Convert the key from the existing
.pemfile:openssl rsa -in private.pem -out private.key
-
Convert the existing
.pemfile to a.crtfile:openssl x509 -in server-cert.pem -out server-cert.crt
-
Import key pair from step 2:
/opt/pingidentity/ase/bin/cli.sh import_management_key_pair private.key -u admin -p Warning: import_key_pair will overwrite any existing certificates Do you want to proceed [y/n]:y Exporting management key to API Security Enforcer... OK, key pair added to keystore
-
Import the
.crtfile in ASE using theimport_management_certCLI command:/opt/pingidentity/ase/bin/cli.sh import_management_cert server-crt.crt -u admin -p Warning: import_management_cert will overwrite any existing management signed certificate Do you want to proceed [y/n]:y Exporting management certificate to API Security Enforcer... OK, signed certificate added to keystore
-
Restart ASE by stopping and starting.