API Security Enforcer
The API Security Enforcer (ASE) supports multiple deployments modes to provide customers flexibility in deploying PingIntelligence for APIs.
This ASE admin guide covers the following deployment modes:
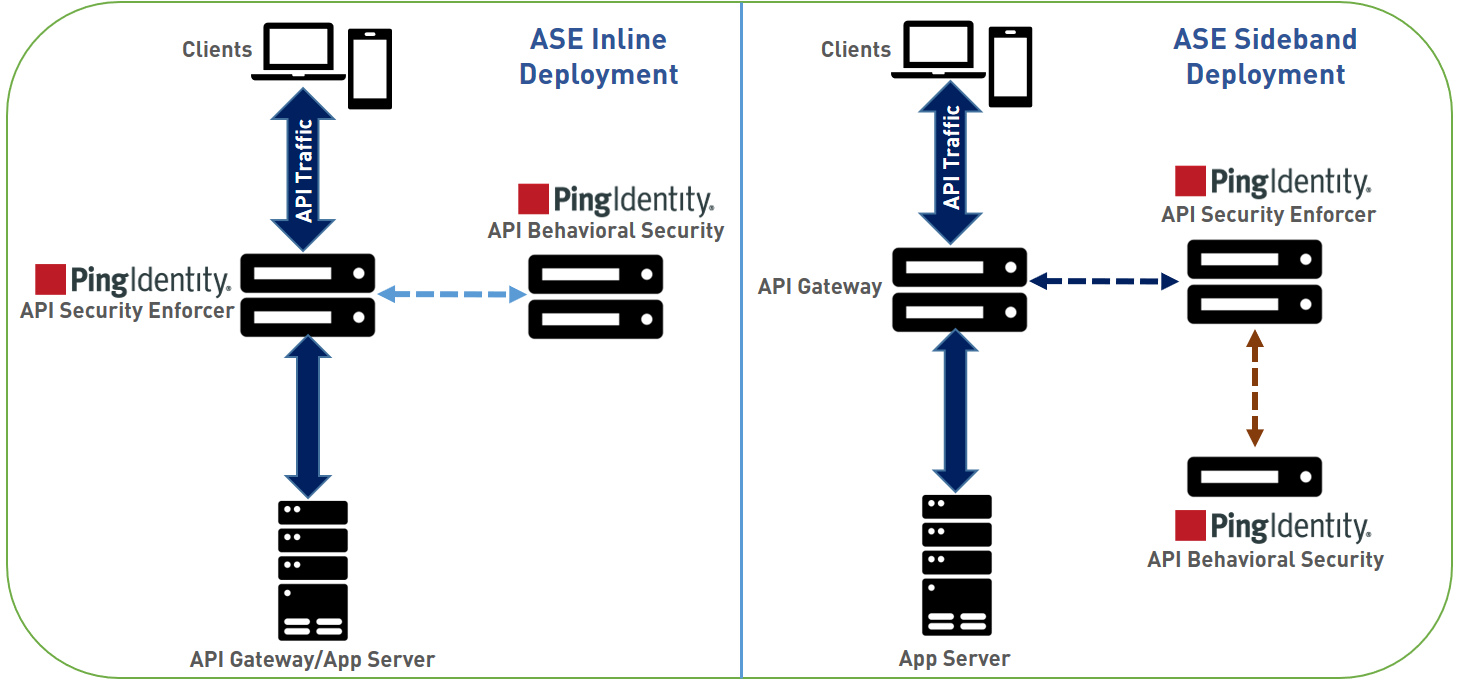
- Inline ASE
-
ASE receives API client traffic and then routes the traffic to a backend API gateway or directly to App Servers. ASE applies real time security and passes API metadata to the API Behavioral Security (ABS) Engine for AI powered advanced attack detection. ABS engine notifies ASE of attacks, and ASE then blocks the rogue clients.
- Sideband ASE
-
An API gateway receives API client traffic and then makes API calls to pass API metadata to ASE for processing. ASE passes the API metadata to the ABS Engine for AI powered advanced attack detection. ABS engine notifies ASE of attacks, and ASE then works with API gateway to block inbound rogue client requests. See ASE sideband chapter for more information.
The following tables show a summary of security and admin features available in each deployment option.
| Security Features | Inline | Sideband |
|---|---|---|
Interface to ABS AI Engine for AI powered attack detection. |
Yes |
Yes |
API deception where decoy APIs look like legitimate APIs to hackers. After accessing a decoy API, a hacker is quarantined, plus activity information is collected. |
Yes |
Yes |
Real-time client blocking based on lists with ASE detected attacks, ABS AI Engine detected attacks, or customer-built lists. Blocking can be based on OAuth tokens, API keys, user names, cookies, and IP addresses. |
Yes |
Yes |
Deny and allow list management of tokens, API keys, cookies, IP addresses. |
Yes |
Yes |
Real-time blocking of API clients with traffic that deviates from API attributes. |
Yes |
No |
Dynamic mapping of public API identity to private internal API identity. |
Yes |
No |
Custom API error messages prevent disclosure of sensitive error information. |
Yes |
No |
Admin Features |
Inline |
Sideband |
Simple deployment with modular JSON configuration files. |
Yes |
Yes |
Live updates to add or remove without loss of traffic or stopping services. |
Yes |
Yes |
Obfuscation of keys and passwords. |
Yes |
Yes |
Active-active clustering that supports scaling and resiliency: all nodes are peers and self-learn the configuration, traffic information, and security updates. |
Yes |
Yes |
Syslog information messages sent to Syslog servers in RFC 5424 format. |
Yes |
Yes |
Automatic API discovery discovers API JSON configuration data. |
Yes |
Yes |
Command-line interface (CLI) and REST API for management and automation tool integration. |
Yes |
Yes |
Linux PAM-based administrator authentication with existing Linux tools. |
Yes |
Yes |
Audit log captures administrative actions for compliance reporting. |
Yes |
Yes |
Distributed inbound flow control limits client traffic and server traffic. |
Yes |
No |
Multiprotocol Layer 7 routing and load balancing of WebSocket, REST API. |
Yes |
No |
Secure connection between ASE and ABS. Secure connection also between ASE and ASE REST APIs. |
Yes |
Yes |