Configuring the AWS automated policy tool
Configure the automated Amazon Web Services (AWS) policy tool.
About this task
To configure the automated policy tool:
Steps
-
Configure the
aws.propertiesfile available in the/pingidentity/pi/aws/config/directory.The following table describes the variables in the
aws.propertiesfile.Variable Description modeChoose the authentication mode between
keysandrole.If you are running the PingIntelligence policy tool from your local machine, use the
keysmode. If you are running the tool from an EC2 instance, use therolemode.access_keyAWS access key. This is applicable when the mode is set to
keys.secret_keyAWS secret key. This is applicable when the mode is set to
keys.aws_lambda_memoryAWS Origin Response Lambda memory in MB. Default value is 1024 MB. The memory can be configured in multiple of 64. Minimum and maximum value are 128 and 3008 respectively. For more information, see AWS Lambda Pricing.
cloudfront_distribution_idThe CloudFront distribution ID.
ase_host_primaryThe API Security Enforcer (ASE) primary host Internet Protocol (IP) address and port or hostname and port.
ase_host_secondaryThe ASE secondary host IP address and port or hostname and port. ASE secondary host receives traffic only when the primary ASE host is unreachable.
This field cannot be left blank. In a testing environment, enter the same IP address for primary and secondary ASE host.
If both the ASE hosts are unreachable, the request is directly sent to the backend API server.
ase_sslEnable or disable Secure Sockets Layer (SSL) communication between Lambda functions and ASE. The default value is
true.ase_sideband_tokenEnter the ASE token generated during the Preparing to run the AWS policy tool, step 7.
Example:
The following is a sample
aws.propertiesfile:# Copyright 2019 Ping Identity Corporation. All Rights Reserved. # Ping Identity reserves all rights in The program as delivered. Unauthorized use, copying, # modification, reverse engineering, disassembling, attempt to discover any source code or # underlying ideas or algorithms, creating other works from it, and distribution of this # program is strictly prohibited. The program or any portion thereof may not be used or # reproduced in any form whatsoever except as provided by a license without the written # consent of Ping Identity. A license under Ping Identity's rights in the Program may be # available directly from Ping Identity. #Authentication mode access-key & secret-key / role based access. Values can be keys or role. mode=keys #AWS access key access_key=AKIAID7MDWSCUUVHMTNA #AWS secret key secret_key=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 #AWS Lambda memory in MB. It should be a multiple of 64. Minimum and maximum value are 128 and 3008 respectively. aws_lambda_memory=1024 #Cloudfront distribution ID cloudfront_distribution_id=EGQ9OEG3ZDABP #ASE Primary Host <IP/Host>:<port> ase_host_primary=test.elasticbeam.com #ASE Secondary Host <IP/Host>:<port> ase_host_secondary=test.elasticbeam.com #ASE SSL status ase_ssl=true #ASE sideband authentication token ase_sideband_token=283ded57cd5f48e6bcd8fa3ba9d2888d
-
If you have set the authentication
modeasrolein theaws.propertiesfile, create a role for the EC2 instance.This role is required for the PingIntelligence policy deployment tool.
-
Select EC2 as service and click on Next: Permissions button.
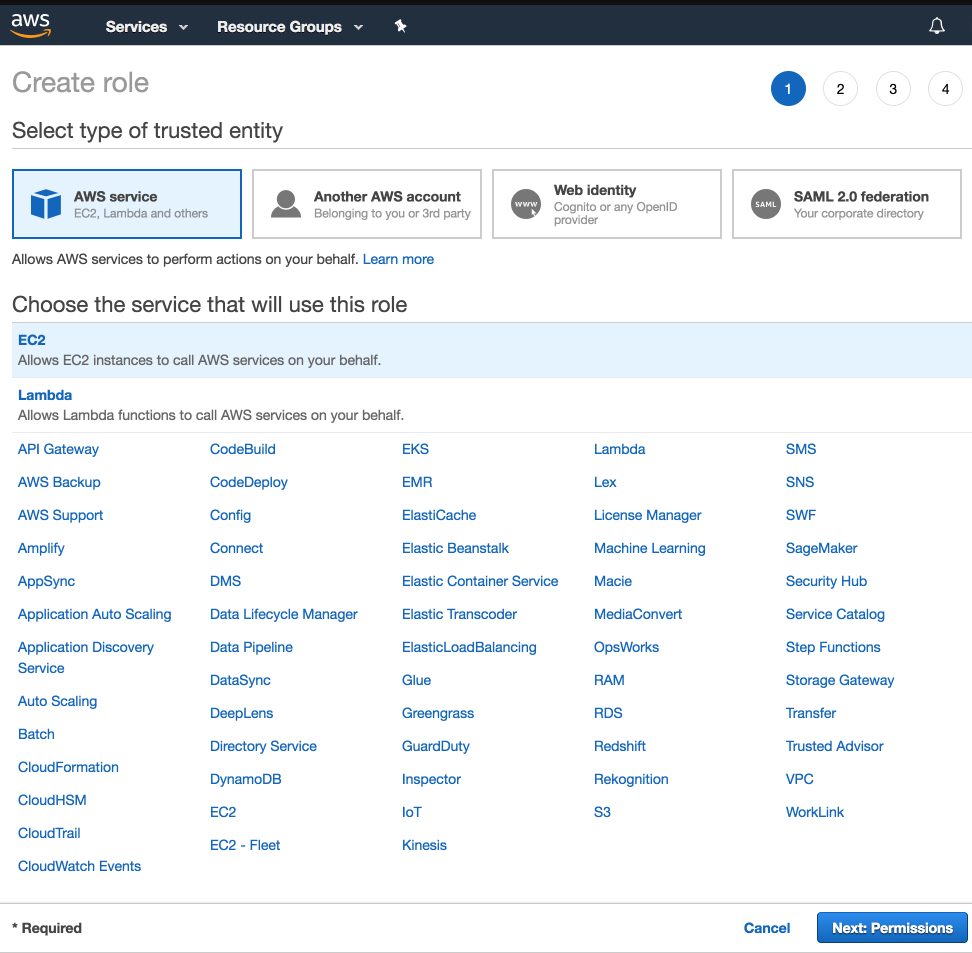
-
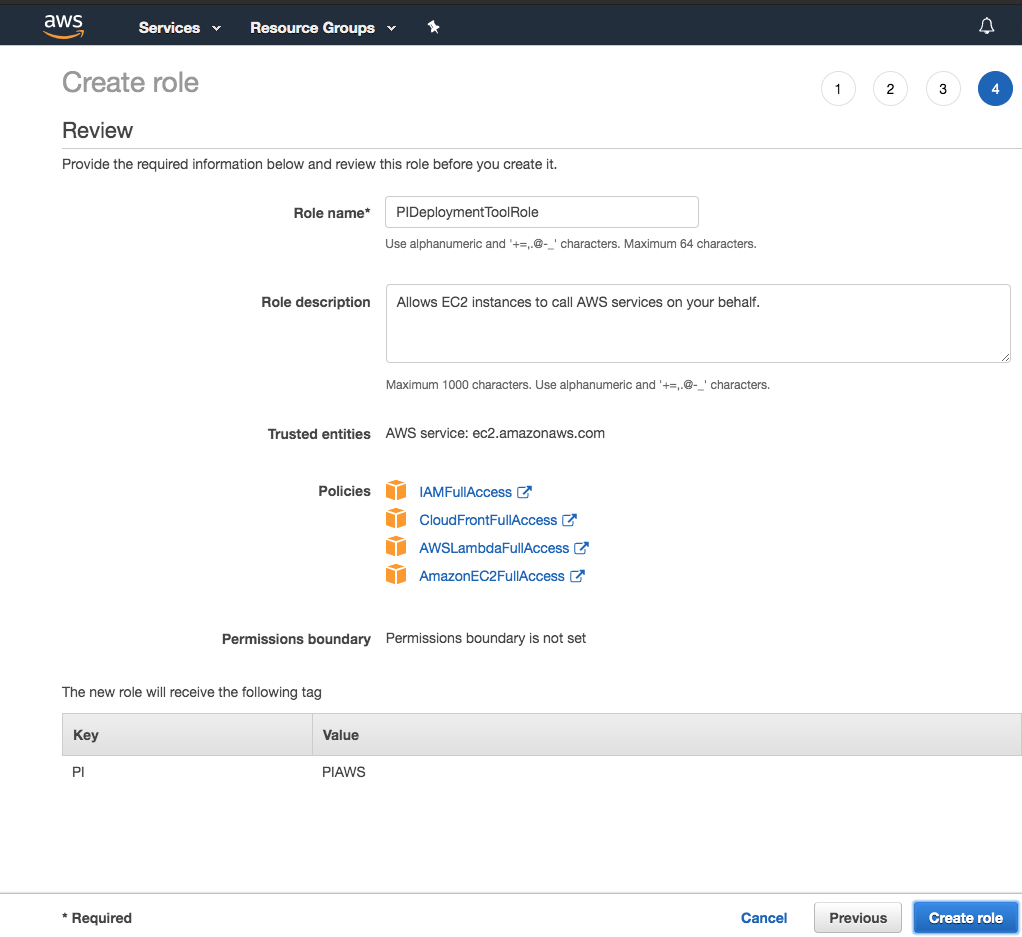
Choose the following four policies and provide a name for each role (for example, PIDeploymentToolRole):
-
IAMFullAccess -
AWSLambdaFullAccess -
CloudFrontFullAccess -
AmazonEC2FullAccess
-
-
After providing the name, click on Create role.
-
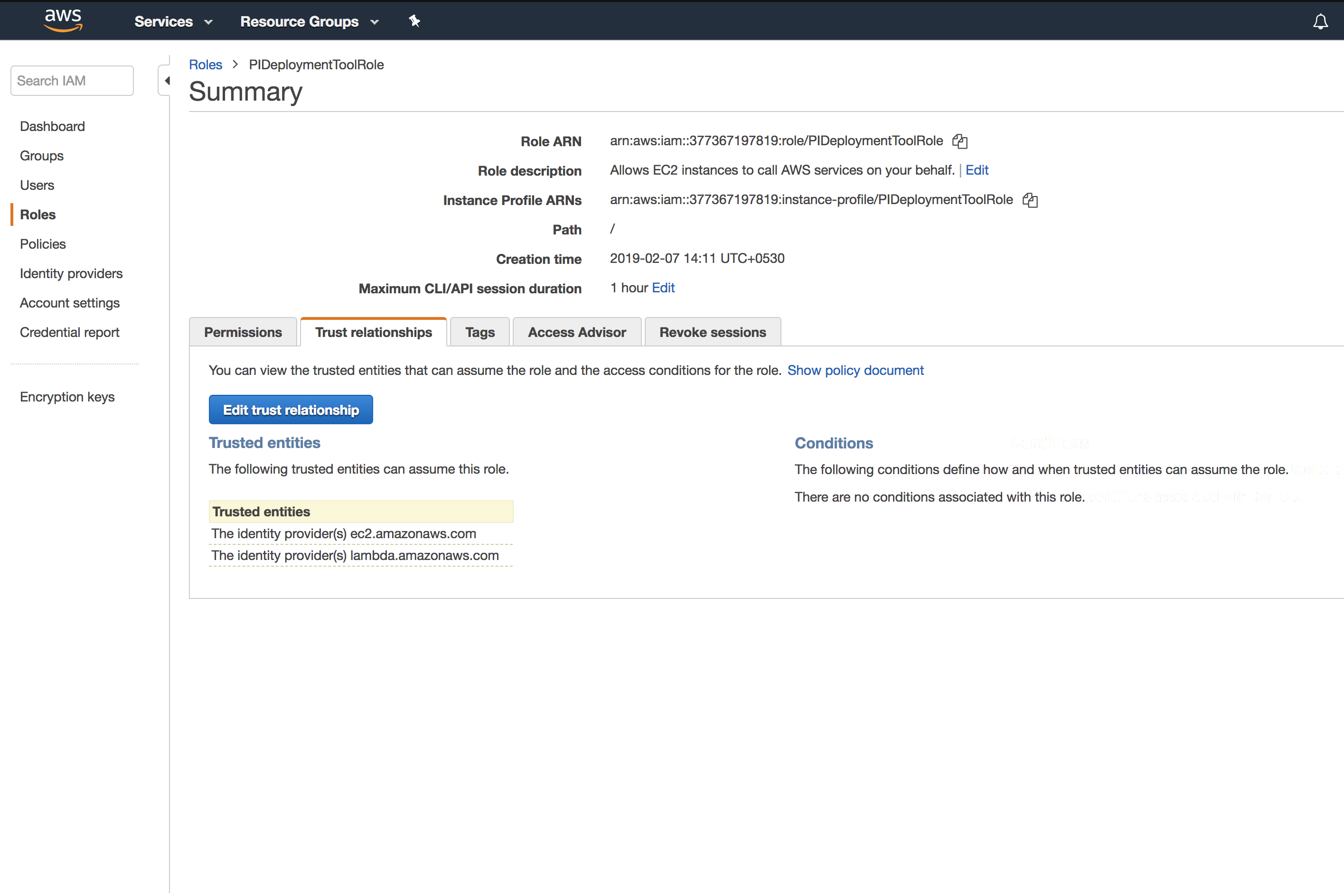
In the Summary page of the role that you created in step 2c, click the Trust relationships tab and then click the Edit trust relationship button.
-
On the Edit Trust Relationship page, enter the following lines and click Update Trust Policy:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "Service": "ec2.amazonaws.com" }, "Action": "sts:AssumeRole" }, { "Effect": "Allow", "Principal": { "Service": "lambda.amazonaws.com" }, "Action": "sts:AssumeRole" } ] }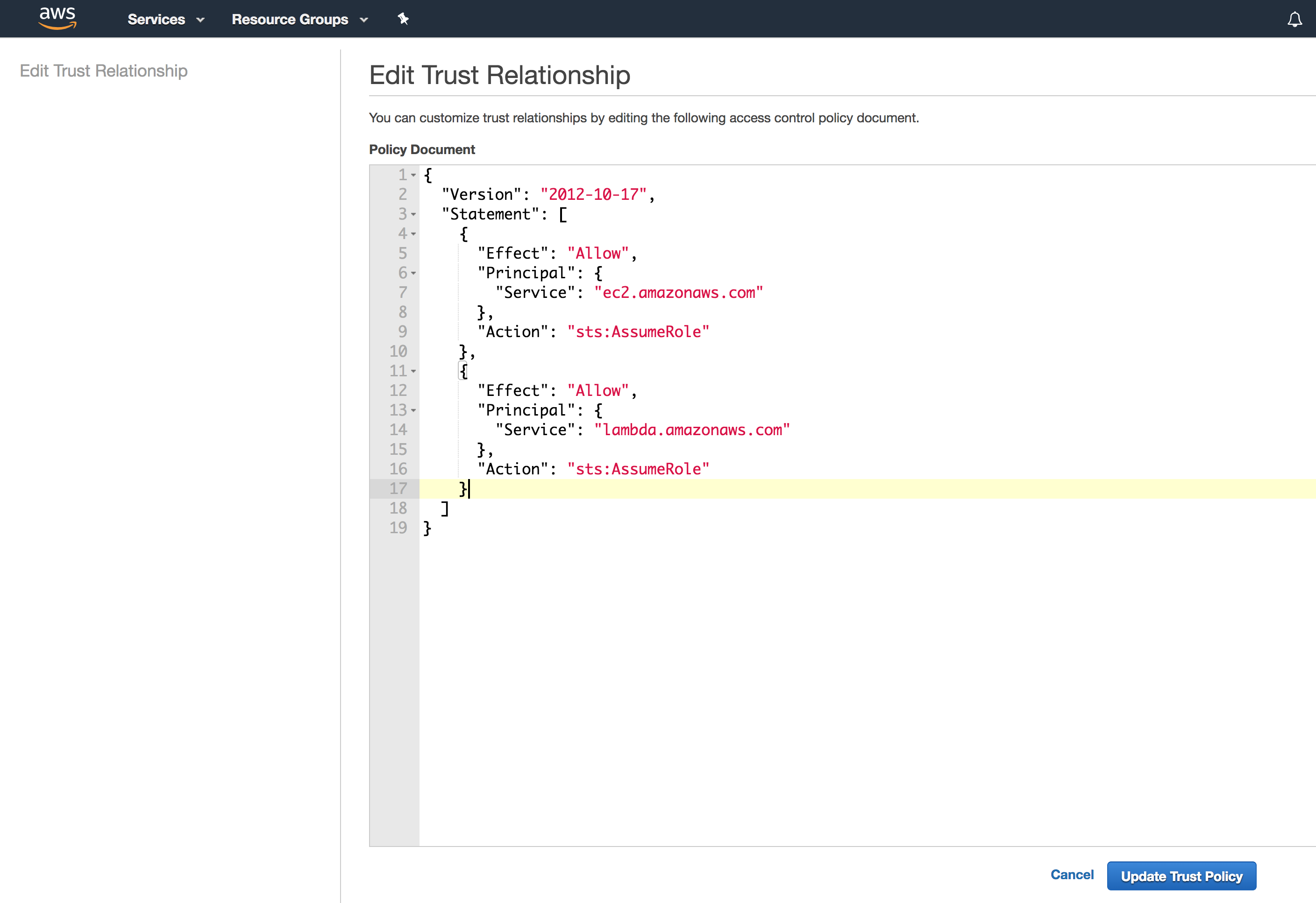
-
Configure the IAM role as the role that you created in step 2c (for example, PIDeploytmentToolRole).
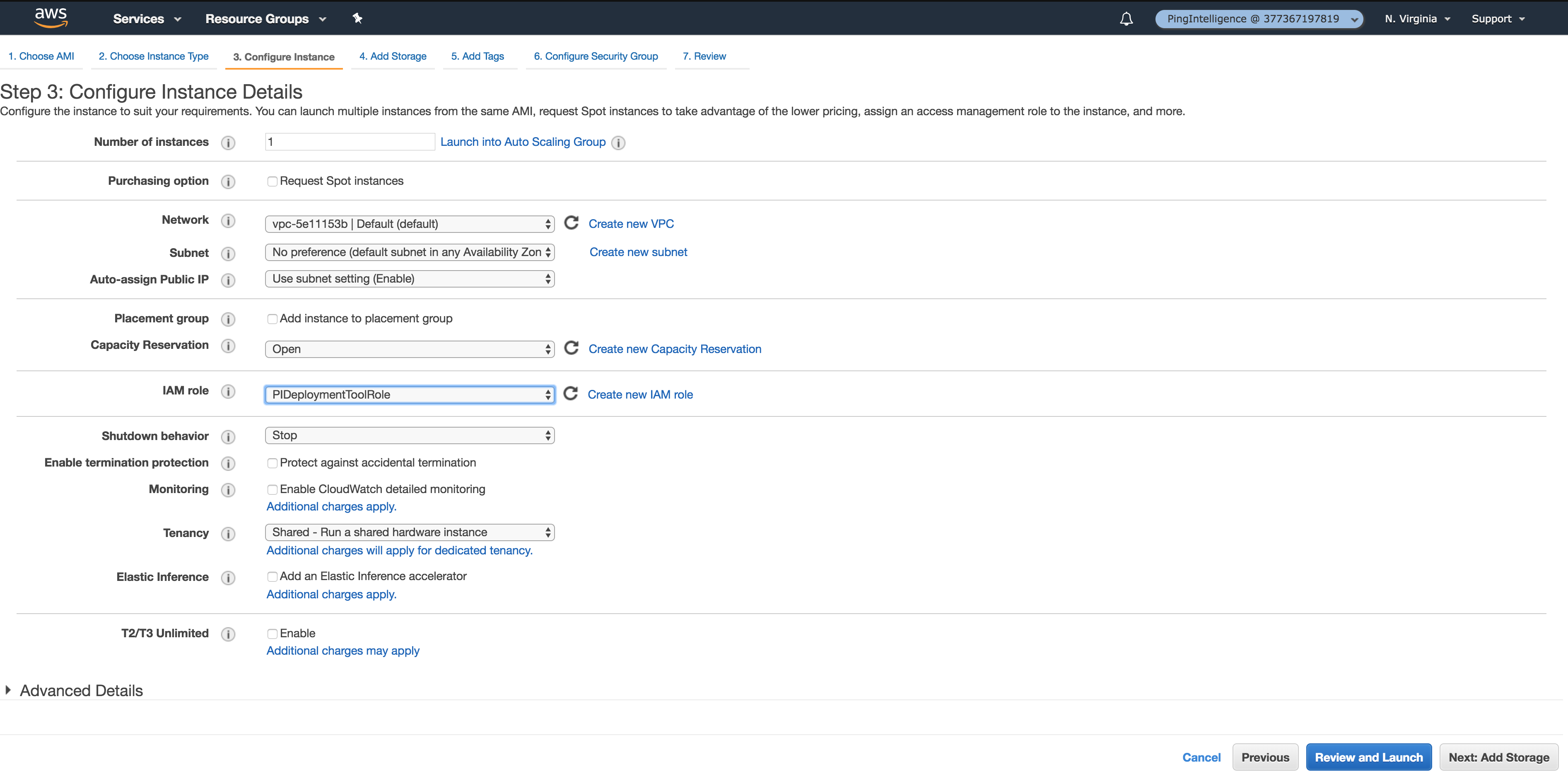
-