WebSocket API protection from DoS and DDoS
Flow control protects WebSocket (ws) servers using five control variables which are independently configured. By default, no flow control is enabled.
| Variable | Description |
|---|---|
Configured once in every application programming interface (API) JavaScript Object Notation (JSON) file |
|
|
Maximum number of HTTP requests per time-period from a single Internet Protocol (IP) to a specific WebSocket API. Time can be in seconds, minutes or hours. |
|
Maximum number of bytes per time-period from a single IP to an API Security Enforcer (ASE) node. Time can be in seconds, minutes or hours. |
|
Maximum number of bytes per time-period sent from an ASE node to a single IP. Time can be in seconds, minutes or hours. |
|
When The default value is |
Configured for each server in every API JSON file |
|
|
Maximum number of concurrent connections to a specific WebSocket API on a server. Prevents aggregate connections from one or a cluster of ASE nodes from overloading a WebSocket API on a specific server. |
The following diagram shows the effect of the parameters on traffic flow through ASE. In the diagram, client-side flow control is managed by the client_spike_threshold, bytes_in_threshold, and bytes_out_threshold parameters. The bytes_out threshold protects against data exfiltration. Server flow control is regulated by theserver_connection_quota parameter.
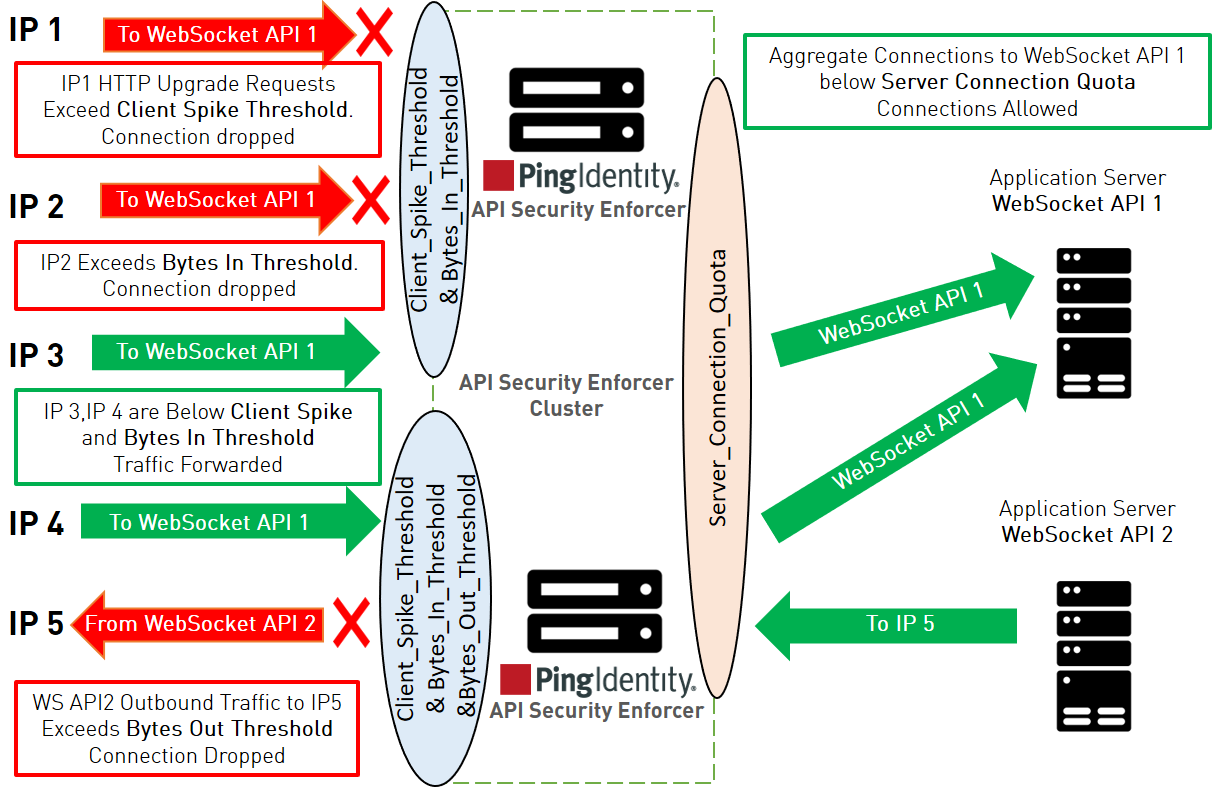
Client flow control monitors incoming traffic from each client connection and drops sessions when HTTP request or bytes in threshold limits are exceeded. In addition, outbound traffic from each ASE Node is monitored to protect against exfiltration. The diagram shows client scenarios including:
-
IP1 sending HTTP request volumes which exceed the
client_spike_thresholdvalue. ASE 1 sends an error message and terminates the session to stop the attack. -
IP2 sending WebSocket streaming traffic volumes which exceed the
bytes_in_thresholdlimits. ASE 1 sends an error message and terminates the session to stop the traffic. -
IP3 and IP4 within client spike threshold and bytes in threshold criteria and requests are forwarded to the backend server.
-
Traffic from ASE 2 to IP5 exceeds the bytes out threshold value. ASE blocks the traffic and drops the client session.
The server-side flow control provides the ability to control session count to an API on an application server. server_connection_quota sets the maximum number of concurrent connections that can be established to an API on a server. The concurrent connections are the aggregate connections from all ASE nodes forwarding traffic to the specified API on a given server.
The following table is an example with a hypothetical deployment for the Application Server in the previous diagram.
| Variable | Configured value |
|---|---|
|
50,000 requests per second per IP |
|
2000 bytes per second per IP |
|
1000 bytes per second per server |
|
20,000 concurrent connections per server |
|
|
Client flow control permits a maximum of 50,000 HTTP requests/second from an individual IP. If IP 1, 2, or 3 exceeds the 50,000/second limit, ASE drops the client session. Otherwise, all requests are passed to the backend servers.
Client flow control allows a maximum of 2,000 bytes/second from each WebSocket client connection to an ASE node. If IP 1, 2, or 3 exceeds the 2,000 bytes/second limit, ASE drops the client session. Otherwise, all requests are passed to the backend servers.
Server flow control allows 20,000 concurrent connections to WebSocket API 1 on the application server. If the sum of connections from the ASE cluster nodes (i.e. ASE 1 + ASE 2 connection count) to WebSocket API1 exceeds 20,000, then ASE will queue the request for a time-period since server_connection_queuing is enabled. If queuing is not enabled, then the request is dropped.
Client Flow Control allows a maximum of 1,000 bytes/second from a WebSocket API to any WebSocket client connection. If outbound traffic exceeds the 1,000 bytes/second limit, ASE blocks the traffic and drops the client session. Otherwise, all requests are passed to the backend servers.
The following is a summary table for WebSocket flow control:
| Parameter | Notes |
|---|---|
|
Maximum HTTP request rate from a client to an API |
|
Maximum number of bytes per time-period from a client to a specific ASE node |
|
Maximum number of bytes per time-period from an ASE node |
|
Maximum number of concurrent sessions from ASE cluster nodes to an API on a specific server |