Azure APIM sideband integration
This guide describes the deployment of PingIntelligence for APIs in a sideband configuration with Azure API Manager (APIM).
A PingIntelligence policy is installed in APIM and passes API metadata to PingIntelligence for detailed API activity reporting and attack detection with optional client blocking. The PingIntelligence policy for Azure also supports detecting attacks based on the username.
The APIM PingIntelligence policy works in the following two configurable modes:
-
Asynchronous mode: When the PingIntelligence policy is configured in the Asynchronous mode, APIM does not wait for a response from PingIntelligence API Security Enforcer (ASE) before sending the API client request to the backend API server. In this mode, PingIntelligence deployment passively logs the API request and response. It performs detailed API activity reporting and attack detection without blocking of attacks.
-
Synchronous mode: When the PingIntelligence policy is configured in the Synchronous mode, Azure API gateway waits for a response from PingIntelligence ASE before sending the request to the backend API server or blocking it. In this mode, PingIntelligence actively logs and responds to the API requests and response. It performs detailed API activity reporting with attack detection and blocking of attacks.
The following diagram shows the logical setup of PingIntelligence ASE and Azure:
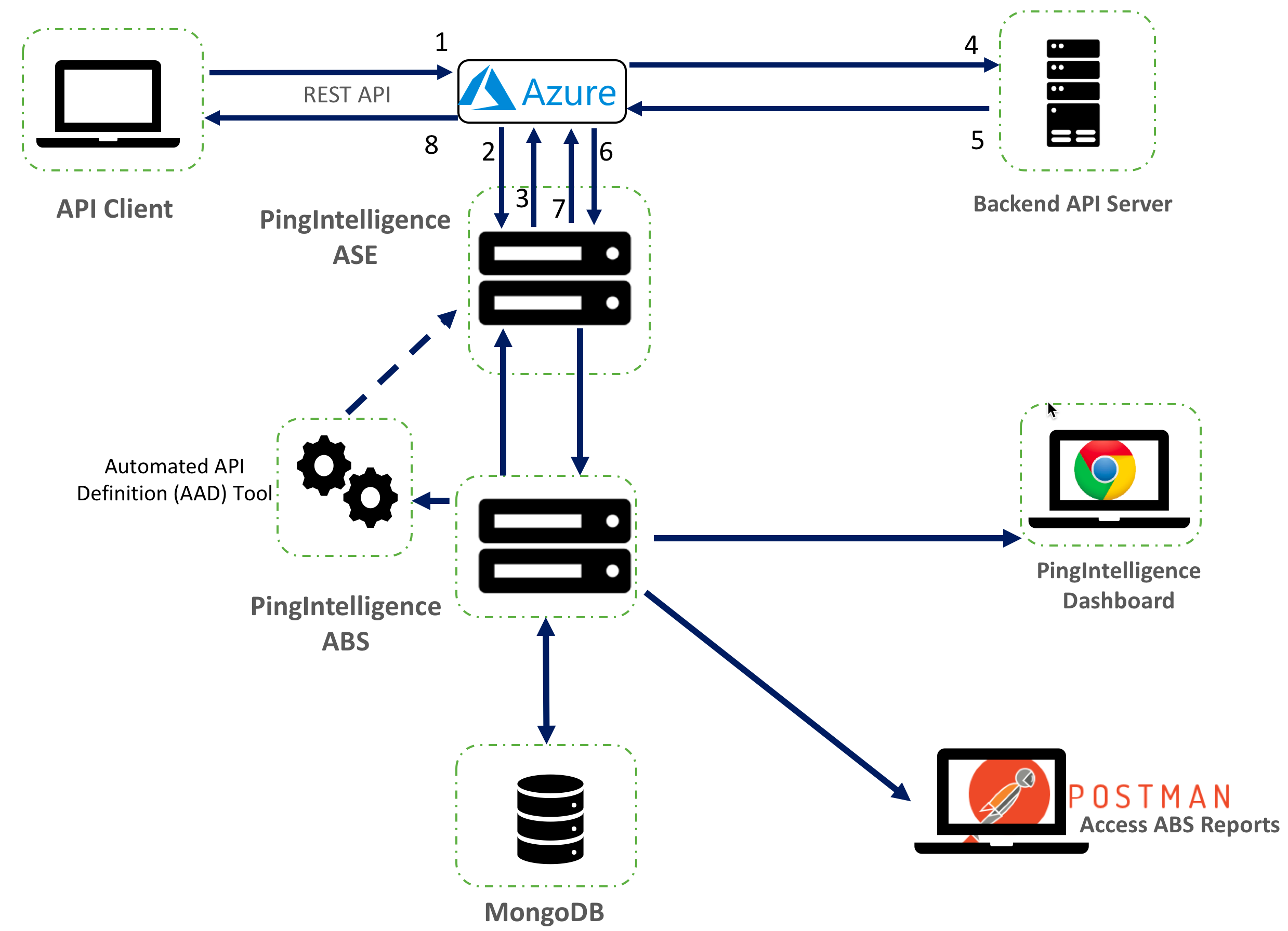
Below is the traffic flow through the Azure and PingIntelligence for APIs components.
-
Client sends an incoming request to APIM.
-
APIM makes an API call to send the request metadata to ASE.
-
ASE checks the request against a registered set of APIs and looks up the origin Internet Protocol (IP), cookie, OAuth2 token, or API key on the PingIntelligence AI engine-generated deny list. If all checks pass, ASE returns a
200-OKresponse to APIM. If not, a different response code is sent to APIM. The request information is also logged by ASE and sent to the AI engine for processing. -
If APIM receives a
200-OKresponse from ASE, then it forwards the request to the backend server. Otherwise, if it receives a403-forbiddenresponse, the APIM blocks the client when blocking is enabled for the API. -
The response from the backend server is received by APIM.
-
APIM makes a second API call to pass the response information to ASE which sends the information to the AI engine for processing.
-
ASE receives the response information and sends a
200-OKto Azure. -
APIM sends the response received from the backend server to the client.