Sideband ASE
When deployed in sideband mode, API Security Enforcer (ASE) receives application programming interface (API) calls from an API gateway which passes API traffic information for AI processing. In such a deployment, ASE works along with the API gateway to protect your API environment.
The following diagram and steps describe a typical ASE sideband deployment traffic pattern.
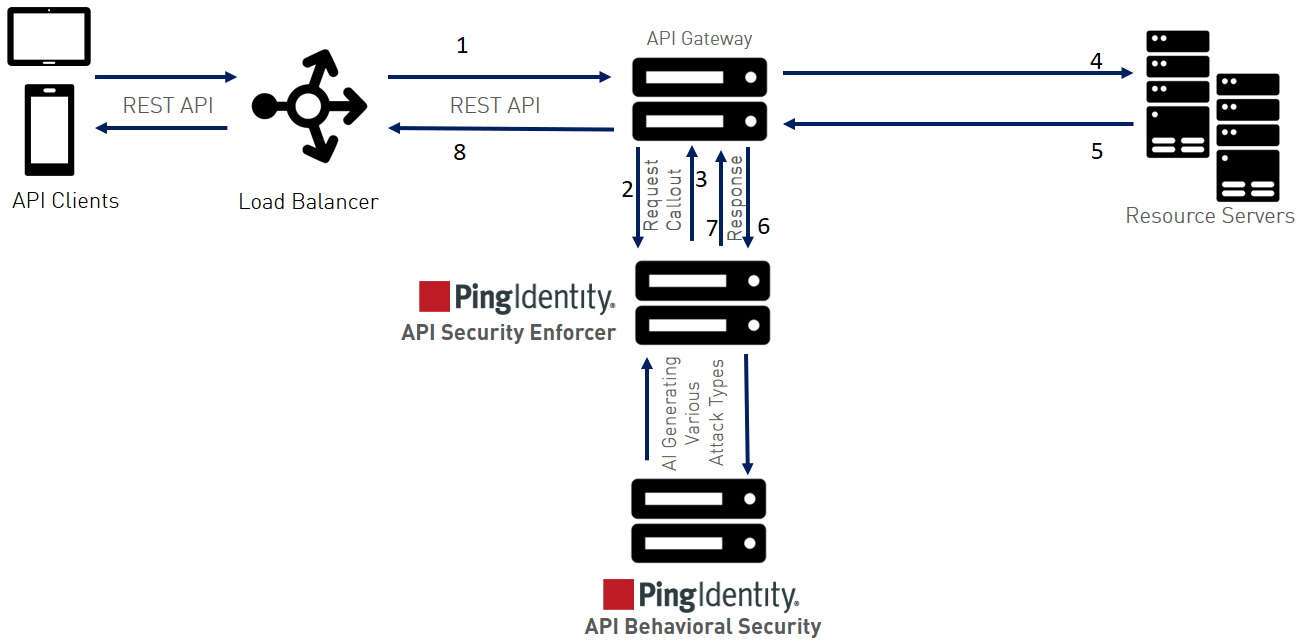
-
An incoming request reaches the API gateway.
-
The API gateway makes an API call to send the request metadata in JSON format to ASE.
-
ASE checks the request against a registered set of APIs and checks the origin Internet Protocol (IP) against the AI-generated deny list. If all checks pass, ASE returns a 200-OK response to the API gateway. Otherwise, a different response code is sent to the gateway. The request is also logged by ASE and sent to the AI Engine for processing.
-
If the API gateway receives a 200-OK response from ASE, then it forwards the request to the backend server. If it receives a 403, the gateway does not forward the request to the backend server and returns a different response code to the client.
-
The response from the backend server is received by the API gateway.
-
The API gateway makes a second API call to pass the metadata information to ASE, which sends the information to the API Behavioral Security (ABS) AI engine for processing.
-
ASE receives the metadata information and sends a 200-OK to the API gateway.
-
The API gateway sends the response received from the backend server to the client.
|
Make sure that XFF is enabled in the API gateway for ASE to detect the client IP addresses correctly. |