Securing an ASE cluster
You can secure an API Security Enforcer (ASE) cluster using a new SSL certificate.
To achieve this, you can either use a self-signed certificate or a certificate authority (CA)-signed SSL certificate:
-
Self-signed certificate
-
CA-signed certificate
Creating a self-signed certificate
About this task
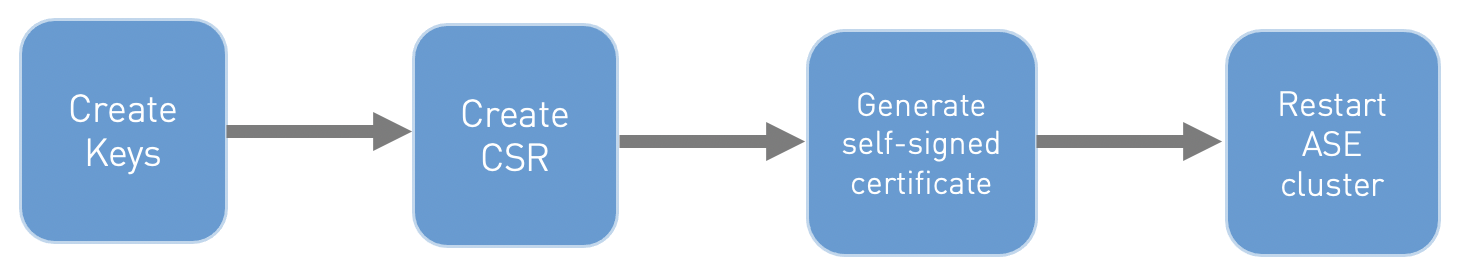
To create a self-signed certificate:
Steps
-
Create a cluster key pair by running the following command-line interface (CLI) command:
create_cluster_key_pair [--yes | -y] create private key for cluster server --yes | -y : create private key without confirmation prompt
The Private key in the pair is automatically created and updated in the keystore in
<pi_install_path>/pingidentity/ase/config/certs/directory.Example:
The following command creates
dh1024.pemin the/opt/pingidentity/ase/config/certs/cluster/directory:$ pingidentity/ase/bin/cli.sh -u admin -p admin create_cluster_key_pair Warning: create_cluster_key_pair will delete any existing cluster key_pair, CSR and self-signed certificate Do you want to proceed [y/n]:y Ok, creating new cluster key pair. Creating DH parameter may take around 20 minutes. Please wait Cluster key created at keystore Cluster dh param file created at /opt/pingidentity/ase/config/certs/cluster/dh1024.pemshell -
Generate a certificate signing request (CSR) from the private key running the following CLI command:
create_cluster_csr [--yes | -y] create certificate signing request for cluster server --yes | -y : create certificate signing request without confirmation prompt
Example:
The following command creates a
.csrfile in the/opt/pingidentity/ase/config/certs/cluster/directory:$ pingidentity/ase/bin/cli.sh -u admin -p admin create_cluster_csr Warning: create_cluster_csr will delete any existing cluster CSR and self signed certificate Do you want to proceed [y/n]:y please provide following info Country Code >OP State >GP Location >IP Organization >KP Organization Unit >Kpase Common Name >www.123.com Generating CSR. Please wait... OK, cluster csr created at /opt/pingidentity/ase/config/certs/cluster/cluster.csrshellResult:
This
.csrfile is saved in the<pi_install_path>/pingidentity/ase/config/certs/cluster/directory. -
Generate a self-signed certificate by running the following command:
create_cluster_self_sign_cert [--yes | -y] --yes | -y : create self signed certificate without confirmation prompt
Example:
The following command creates a self-signed certificate in the key store:
$ pingidentity/ase/bin/cli.sh -u admin -p admin create_cluster_self_sign_cert Warning: create_cluster_self_sign_cert will delete any existing cluster self signed certificate Do you want to proceed [y/n]:y Creating new cluster self signed certificate OK, self sign certificate created in key storeshellThe certificate is automatically created in the key store in the
<pi_install_path>/pingidentity/ase/config/certs/directory. -
Restart the ASE cluster for synchronizing the key and certificate.
For more information, follow the instructions in Restarting an ASE cluster.
Creating a CA-signed certificate
About this task
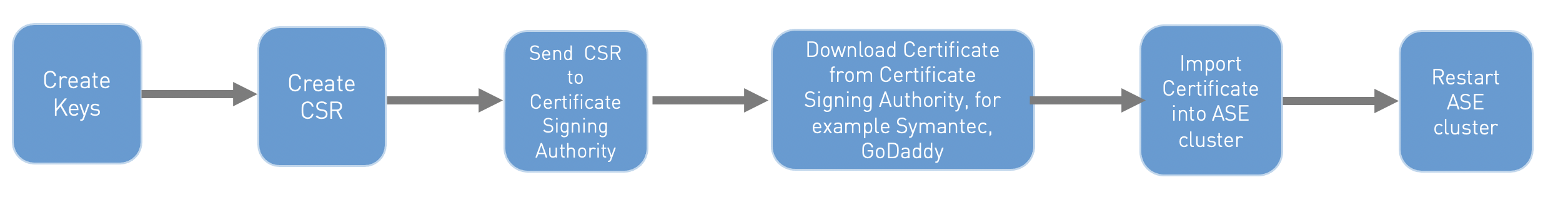
To create a CA-signed SSL certificate:
Steps
-
Create a cluster key pair by running the following CLI command:
create_cluster_key_pair [--yes | -y] create private key for cluster server --yes | -y : create private key without confirmation prompt
Example:
The following command creates a key in the
/opt/pingidentity/ase/config/certs/cluster/directory:$ pingidentity/ase/bin/cli.sh -u admin -p admin create_cluster_key_pair Warning: create_cluster_key_pair will delete any existing cluster key_pair, CSR and self-signed certificate Do you want to proceed [y/n]:y Ok, creating new cluster key pair. Creating DH parameter may take around 20 minutes. Please wait Cluster key created at keystore Cluster dh param file created at /opt/pingidentity/ase/config/certs/cluster/dh1024.pemshellThe private key in the pair is automatically created and updated in the key store in the
<pi_install_path>/pingidentity/ase/config/certs/directory. -
Generate a certificate signing request (CSR) from the private key using the following CLI command:
create_cluster_csr [--yes | -y] create certificate signing request for cluster server --yes | -y : create certificate signing request without confirmation prompt
This
.csrfile gets saved in the<pi_install_path>/pingidentity/ase/config/certs/cluster/directory.Example:
The following command creates a
.csrfile in the/opt/pingidentity/ase/config/certs/cluster/directory:$ pingidentity/ase/bin/cli.sh -u admin -p admin create_cluster_csr Warning: create_cluster_csr will delete any existing cluster CSR and self signed certificate Do you want to proceed [y/n]:y please provide following info Country Code >OP State >GP Location >IP Organization >KP Organization Unit >Kpase Common Name >www.123.com Generating CSR. Please wait... OK, cluster csr created at /opt/pingidentity/ase/config/certs/cluster/cluster.csrshell -
Upload the CSR created in step 2 to the CA-signing authority’s website to get a CA-signed certificate.
-
Download the CA-signed certificate from the CA-signing authority’s website.
-
Import the signed CA-certificate into ASE cluster by running the following CLI command:
import_cluster_cert {cert_path} [--yes | -y] import CA signed certificate for cluster server --yes | -y : import CA signed certificate without confirmation promptThe certificate is imported into the key store in the
<pi_install_path>/pingidentity/ase/config/certs/directory.Example:
./cli.sh -uadmin -padmin import_cluster_key_pair /home/ec2-user/cert_folder/signed_cert/test.elasticbeam.com.key Warning: import_cluster_key_pair will overwrite any existing cluster certificates Do you want to proceed [y/n]:y Exporting cluster key to API Security Enforcer... OK, key pair added to keystore 2:43 [ec2-user@rhel76-cluster-nodes-6-12 bin]$ ./cli.sh -uadmin -padmin import_cluster_cert /home/ec2-user/cert_folder/signed_cert/test.elastic.crt Warning: import_cluster_cert will overwrite any existing cluster signed certificate Do you want to proceed [y/n]:y Exporting cluster certificate to API Security Enforcer... OK, signed certificate added to keystore
-
Synchronizing the key and certificate by restarting the ASE cluster.
For more information, follow the instructions in Restarting an ASE cluster.