API name mapping – hide internal URLs
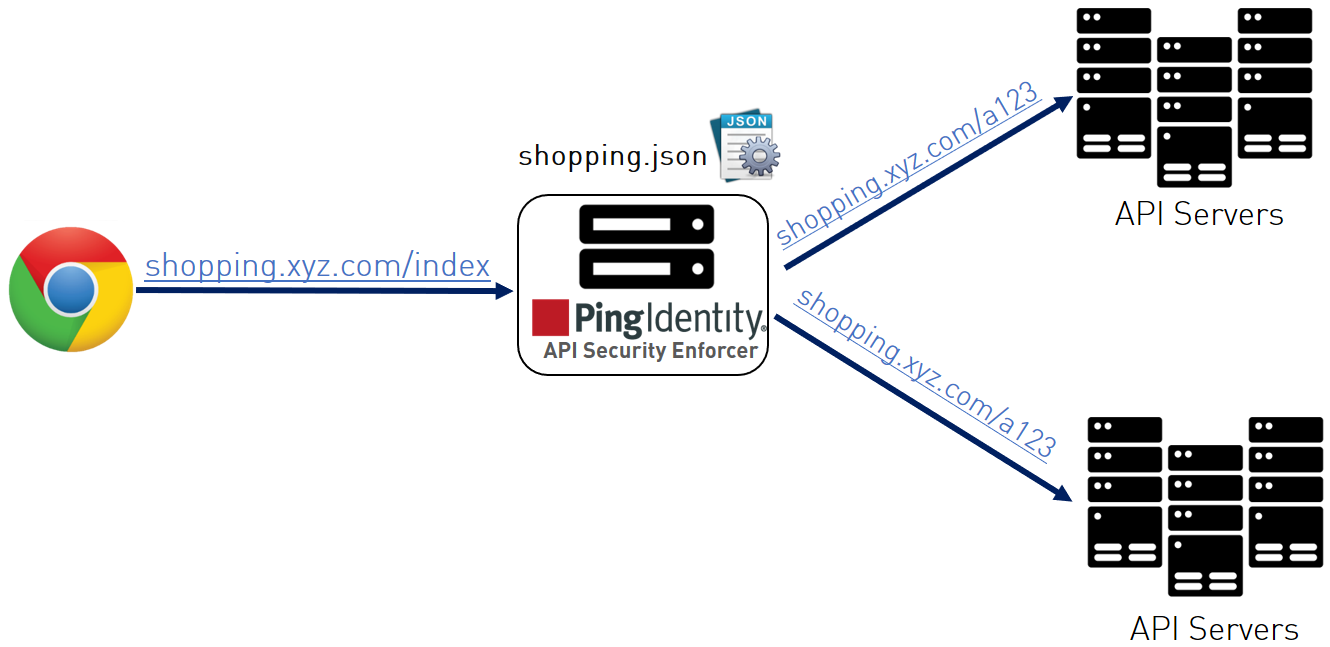
After enabling application programming interface (API) cybersecurity, API name mapping can be configured to protect API servers by hiding internal Uniform Resource Locator (URL)s from the outside world. Internal URLs may also be modified without updating entries in the public DNS server.
For example, the following JavaScript Object Notation (JSON) snippet from an API JSON file maps an external URL (“/index”) for shopping.xyz.com to an internal URL (“/a123”).
"api_metadata": {
"protocol": "http",
"url": "/index",
"hostname": "127.0.0.1",
"cookie": "JSESSIONID",
"cookie_idle_timeout": "200m",
"logout_api_enabled": true,
"cookie_persistence_enabled": false,
"oauth2_access_token": false,
"apikey_qs": "",
"apikey_header": "",
"cookie_persistence_enabled": true,
"login_url": "",
"enable_blocking": true,
"api_mapping": {
"internal_url": ""
},
"login_url": "/index/login",
"api_mapping": {
"internal_url": "/a123"
},
The following diagram illustrates the data flow from the client to the backend server through the API Security Enforcer (ASE):