Obfuscating keys and passwords
Using the API Security Enforcer (ASE) command-line interface (CLI), you can obfuscate keys and passwords configured in the ase.conf, cluster.conf, and abs.conf files.
Before you begin
When obfuscating a password, you must stop ASE.
About this task
Here is the obfuscated data in each file:
-
ase.conf– Email and keystore (PKCS#12) password -
cluster.conf– Cluster authentication key -
abs.conf– ABS access and secret key
ASE ships with a default master key (ase_master.key), which is used to obfuscate other keys and passwords. You should generate your own ase_master.key.
The following diagram summarizes the obfuscation process.
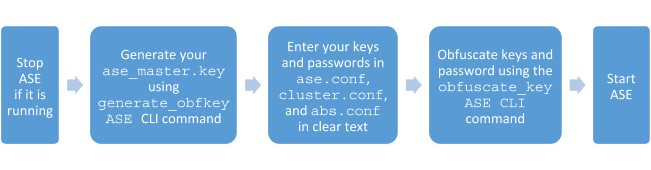
Steps
-
Generate your
ase_master.keyby running thegenerate_obfkeyASE CLI command.The new
ase_master.keyis used to obfuscate the keys and passwords in the configuration files.Example:
/opt/pingidentity/ase/bin/cli.sh generate_obfkey -u admin -p Please take a backup of config/ase_master.key, config/ase.conf, config/abs.conf, config/cluster.conf before proceeding Warning: Once you create a new obfuscation master key, you should obfuscate all config keys also using cli.sh obfuscate_keys Warning: Obfuscation master key file /opt/pingidentity/ase/config/ase_master.key already exists. This command will delete it and create a new key in the same file. Do you want to proceed [y/n]:y creating new obfuscation master key Success: created new obfuscation master key at /opt/pingidentity/ase/config/ase_master.key
In an ASE cluster, the
ase_master.keymust be manually copied to each cluster node. -
Obfuscate keys and passwords:
-
Enter the keys and passwords in clear text in the
ase.conf,cluster.conf, andabs.conffiles. -
Run the
obfuscate_keyscommand to obfuscate keys and passwords.Example:
/opt/pingidentity/ase/bin/cli.sh obfuscate_keys -u admin -p Please take a backup of config/ase_master.key, config/ase.conf, config/abs.conf, and config/cluster.conf before proceeding If config keys and passwords are already obfuscated using the current master key, they are not obfuscated again Following keys will be obfuscated: config/ase.conf: sender_password, keystore_password config/abs.conf: access_key, secret_key config/cluster.conf: cluster_secret_key Do you want to proceed [y/n]:y obfuscating config/ase.conf, success obfuscating config/abs.conf, success obfuscating config/cluster.conf, success
-
Start ASE after keys and passwords are obfuscated.
After the keys and passwords are obfuscated, the
ase_master.keymust be moved to a secure location from ASE for security reasons. If you want to restart ASE, thease_master.keymust be present in the/opt/pingidentity/ase/config/directory.
-