Splunk for PingIntelligence
Splunk for PingIntelligence provides a pictorial view of various attacks in an API environment with granular event details.
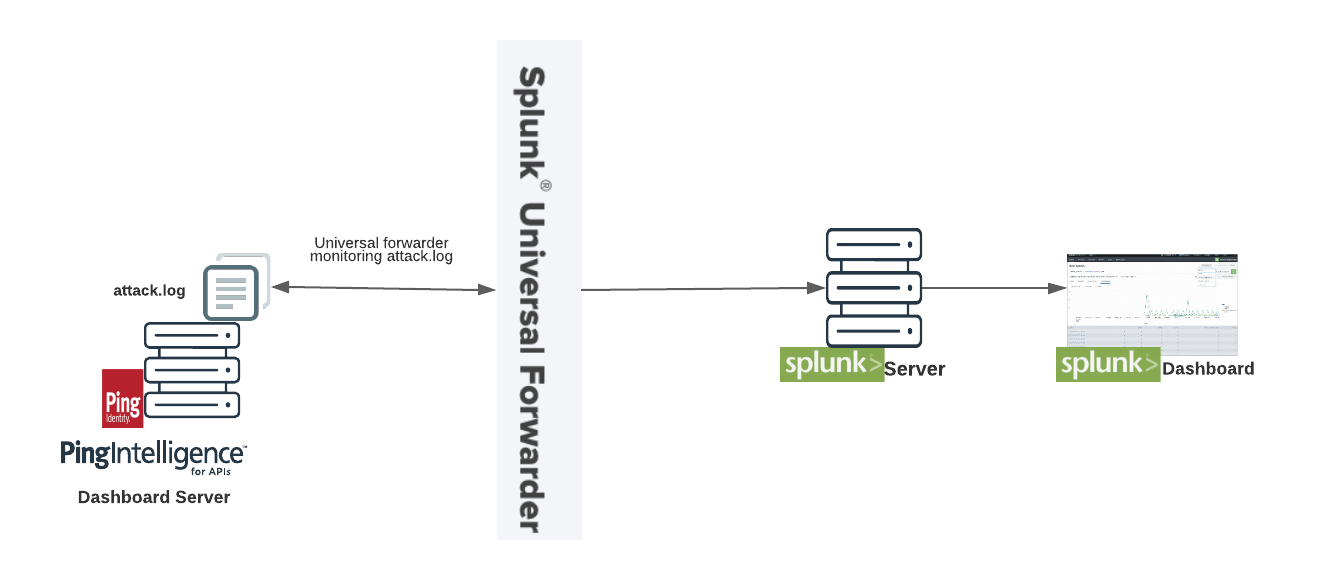
The Splunk Dashboard monitors the attack.log file in PingIntelligence for APIs Dashboard. The Dashboard server through attack.log returns a JSON report that contains attack details. The following is a snippet of attack.log with attack details:
{
"timestamp": "1575965866132",
"protocol": "HTTP",
"attack_id": "11",
"description": "Extreme App Activity",
"attack_bucket": "API",
"attack_scope": "SINGLE_API",
"attacked_api": "shop-electronics",
"attack_identifier_type": "TOKEN",
"attack_key": "",
"attack_value": "343077883101e1c8f2b3ec0fbf6a32ab2327e4c2e7ebe525a27a125225fa136d"
}The following illustration summarizes the data flow between the PingIntelligence Dashboard and Splunk.
|
PingIntelligence for APIs is qualified for Splunk 8.0.0. |