Configuring an OIDC application in PingOne for PingIntelligence Dashboard
Complete the following steps in PingOne to create and configure an OpenID Connect (OIDC) application for setting up single sign-on (SSO) to PingIntelligence for APIs Dashboard.
Steps
-
From the PingOne dashboard, create a new connection.
-
Provide the information for following fields:
-
Application Name
-
Description (Optional)
-
Icon (Optional)
-
-
For Application Type, choose OIDC Web App, and click Save.
-
On the Configuration tab, click the Pencil icon.
-
Enter the following URL in the Redirect URLs field and click Save.
The path in the URI is as follows:
https://<pi_install_host>:8030/login/oauth2/code/PingIntelligence. Do not change the path in the URI, just substitute the hostname. For example,https://127.161.140.180:8030/login/oauth2/code/PingIntelligence. -
Click the Resources tab and then click the Pencil icon. Click the icon next to the profile scope to add to the list of Allowed Scopes. Click Save.
-
Click the Attribute Mappings tab and click the Pencil icon. Add the following attributes and map them to the PingIntelligence Dashboard
SSO.properties. Click Add to add additional attributes. Make sure to select the Required check box for each attribute. When you are finished, click Save.OIDC Attributes Value User ID
PingOne User Attribute
The value defaults to
sub.Family Name
PingOne User Attribute
The value of this property should be a claim name that holds the last name of the signed-on user in
<pi_installation_path>/pingidentity/webgui/sso.propertiesfile. The default value for the claim isfamily_name. For more information, see Configuring Dashboardsso.propertiesfor PingOne.Given Name
PingOne User Attribute
The value of this property should be a claim name that holds the first name of the signed-on user in
<pi_installation_path>/pingidentity/webgui/sso.propertiesfile. The default value for the claim isgiven_name. For more information, see Configuring Dashboardsso.propertiesfor PingOne.Role
Static Key
The value of this property should be a claim name that holds the value of the role of the signed-on user in
<pi_installation_path>/pingidentity/webgui/sso.propertiesfile. For more information, see Configuring Dashboardsso.propertiesfor PingOne.[pingintelligence_configure_oidc_app_p1.dita]The default value in Dashboard is
role. Supported values for the Role claim areADMINandREGULAR. -
Click the Configuration tab and record the values for the following application properties to use in later steps in Configuring Dashboard
sso.propertiesfor PingOne:-
Issuer
-
Client ID
-
Client Secret
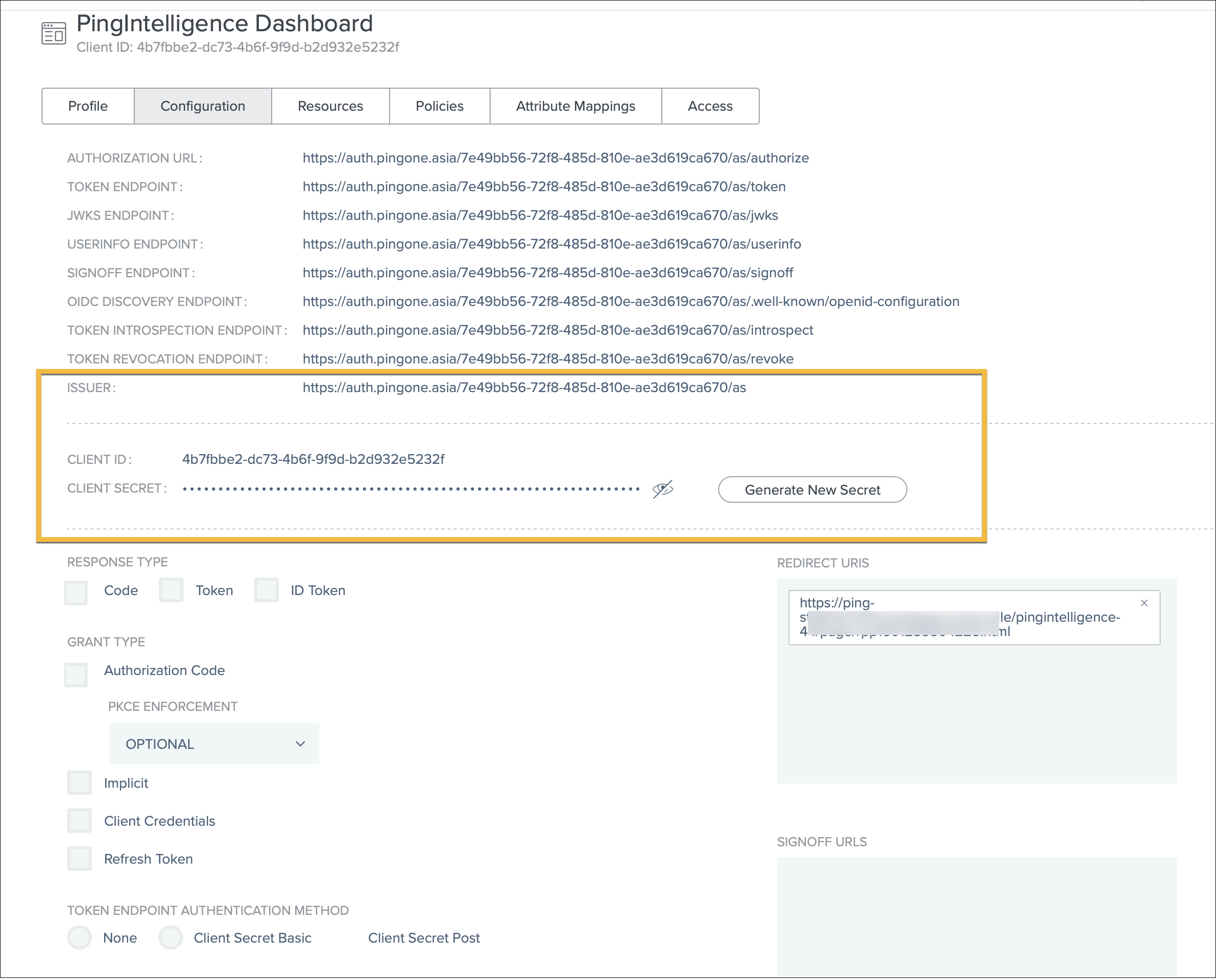
-
-
Click the Pencil icon on the top right, set the following properties, and click Save.
Property Value Response Type
Select Code.
Grant Type
Select Authorization Code. Keep the PKCE Enforcement as OPTIONAL.
Token Endpoint Authentication Method
Select None, Client Secret Basic, or Client Secret Post.
-
To enable the application, click the toggle switch to the on (blue) position.
Next steps
Complete the SSO configuration in PingIntelligence for APIs Dashboard. For more information see, Configuring Dashboard sso.properties for PingOne.