Configuring alert notifications on Slack and email
You can configure Splunk to send alert notifications to a Slack channel or through email.
Before you begin
Make sure to install the Slack app in your Splunk setup. Also be sure to connect Slack and Splunk using webhooks. For more information on Slack webhooks, see Incoming Webhooks.
About this task
Complete the following steps to create an alert for Slack:
Steps
-
Navigate to Settings ̶> Searches, reports and alerts.
Alerts should be created for App: Search & Reporting(search).
-
Create new alerts. Enter the values as described in the table below:
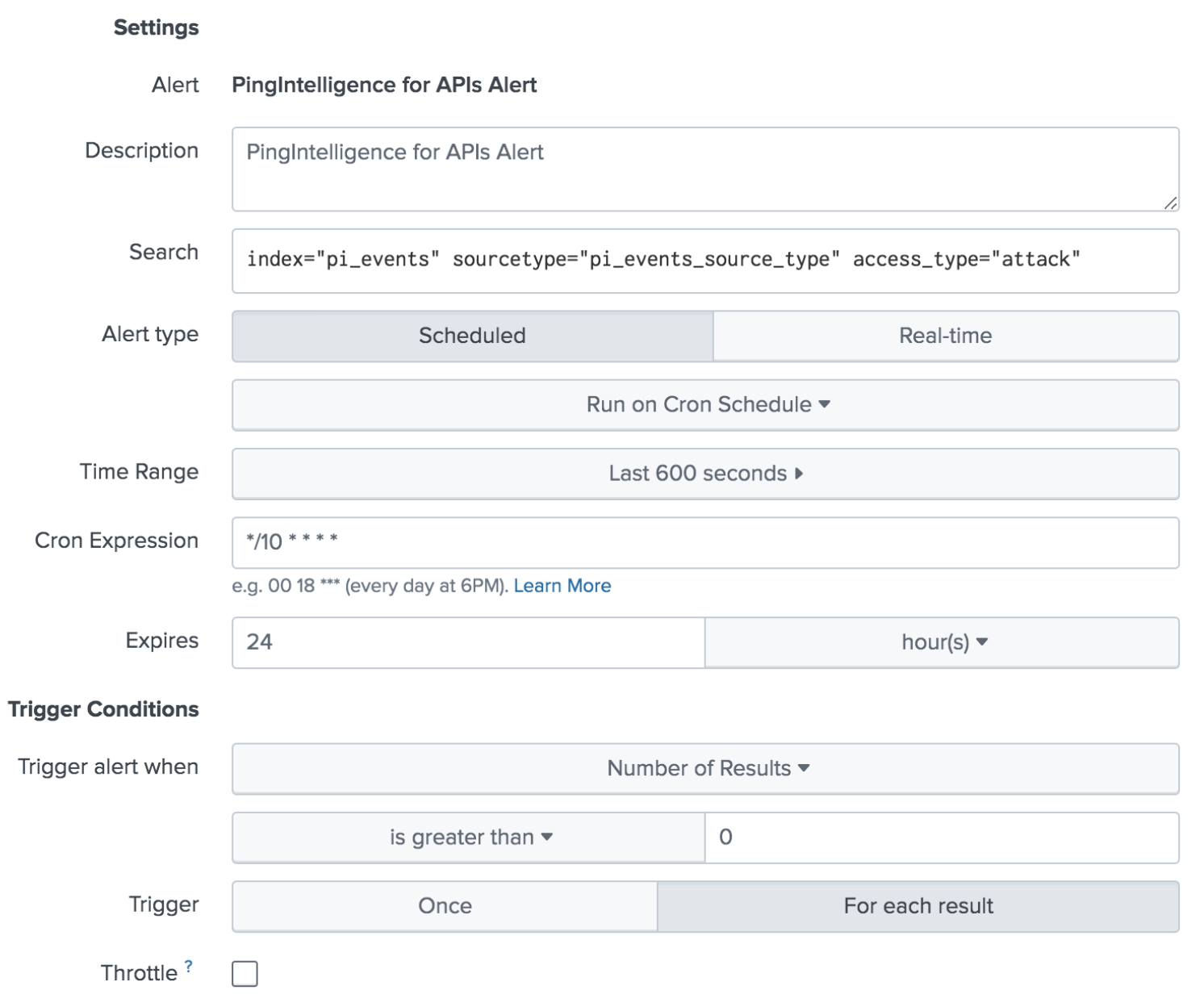
Value Description Description
PingIntelligence for APIs AlertSearch
Search: index="pi_events"sourcetype="pi_events_source_type"access_type="attack"Alert Type
Scheduled → Run on Cron Schedule
Time Range
Last 600 seconds
Cron Expression
*/10 * * * *Expires
24HoursTrigger alert when
The alert should be triggered for results when greater than 0.
Trigger
For each result. This would trigger a new alert for each event.
Throttle
Do not throttle the events.
-
Configure alert action as follows.
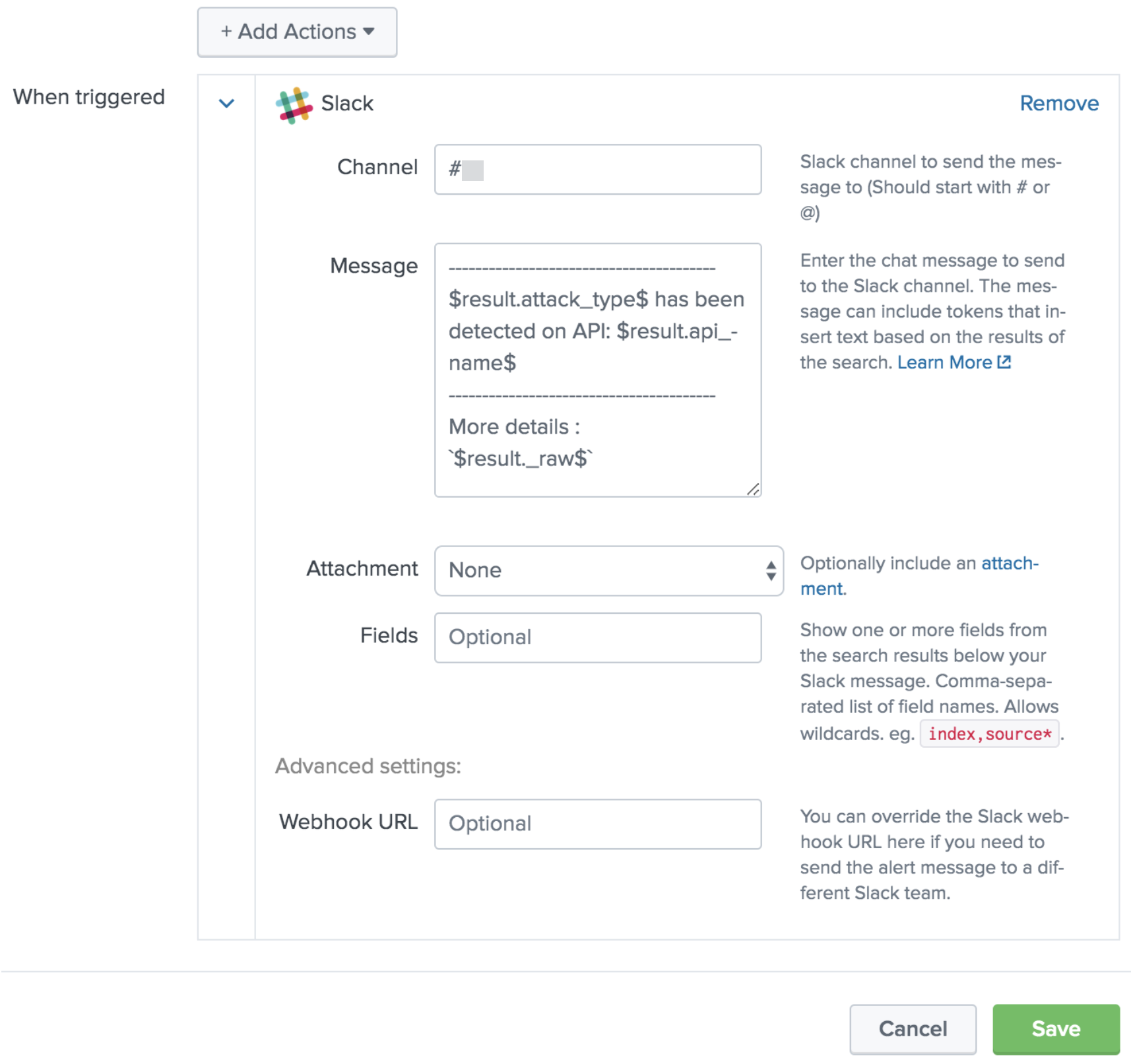
Value Description Add Actions
Choose the Slack app to add actions.
Channel
Use the channel that has been configured with a Webhook URL starting with either # or @.
In this example, we are using Channel name as:
# PingIntelligence_alertsMessage
This is the message that will be posted along with the alert in Slack. We recommend using the following message:
------------------------------------------------------- $result.attack_type$ has been detected on API: $result.api_name$ ----------------------------------------------------------------- More details :
$result._raw$Attachments
N/A
Fields
N/A
Webhook URL
N/A
-
Post a message in Splunk to verify that it is notified in Slack.