Importing and configuring the PingIntelligence policy
To deploy the PingIntelligence policy, first import and configure the policy.
About this task
The PingIntelligence policy is specific to an ASE cluster. If you have more than one ASE cluster, then add the policy to a new workspace and create a new plugin. When you import the PingIntelligence policy, it is imported to an LX workspace and opens in a Node.js editor.
To import the PingIntelligence policy in F5:
Steps
-
Sign on to F5 and navigate to Local Traffic → iRules → LX Workspaces.
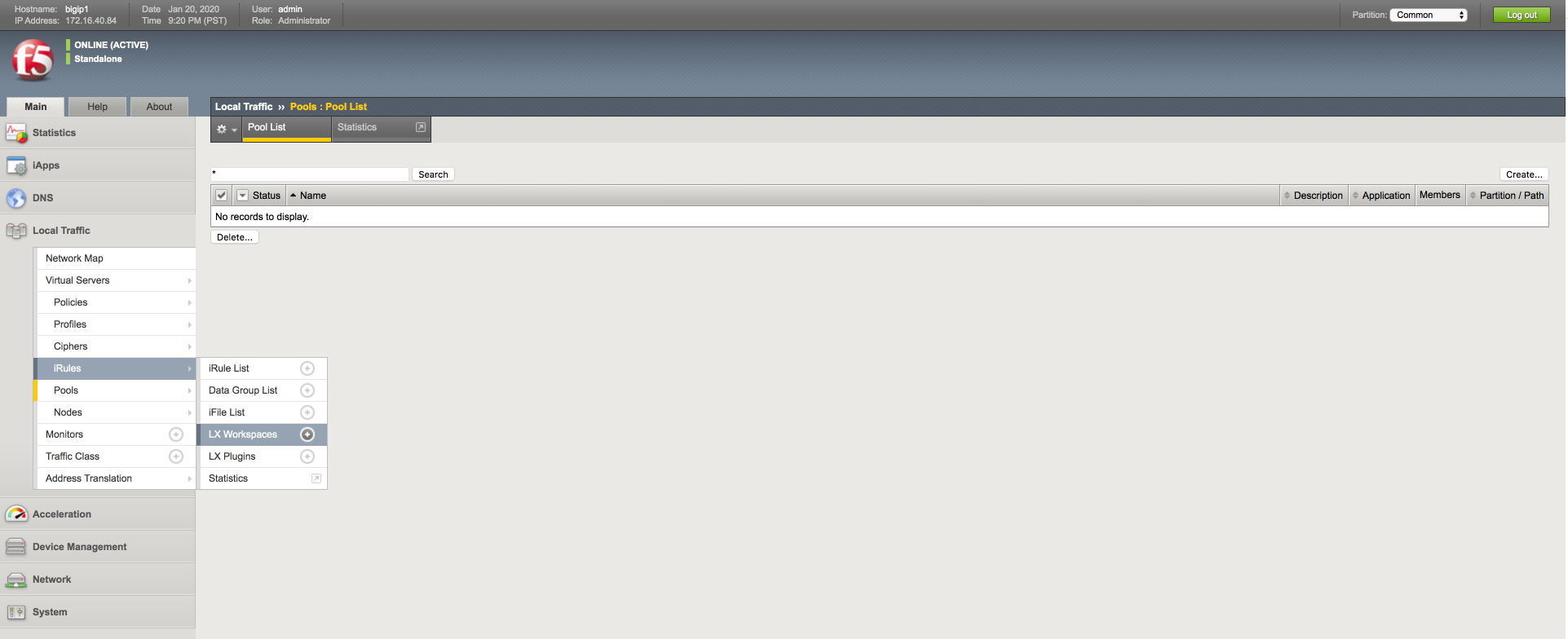
-
In the Workspaces tab, click import.
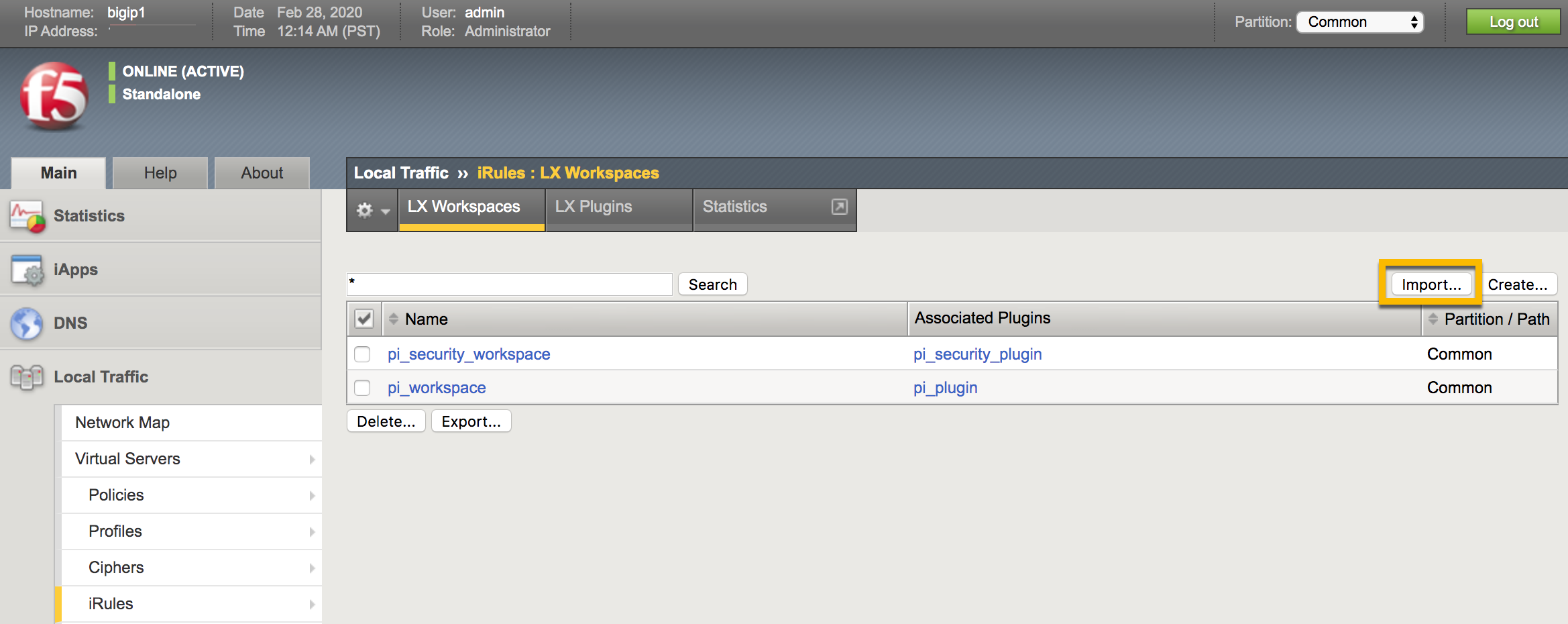
Result:
A Workspace import page is displayed.
-
Enter the Name and choose the PingIntelligence policy that you downloaded in Preparing to deploy the PingIntelligence policy.
-
Click Import.
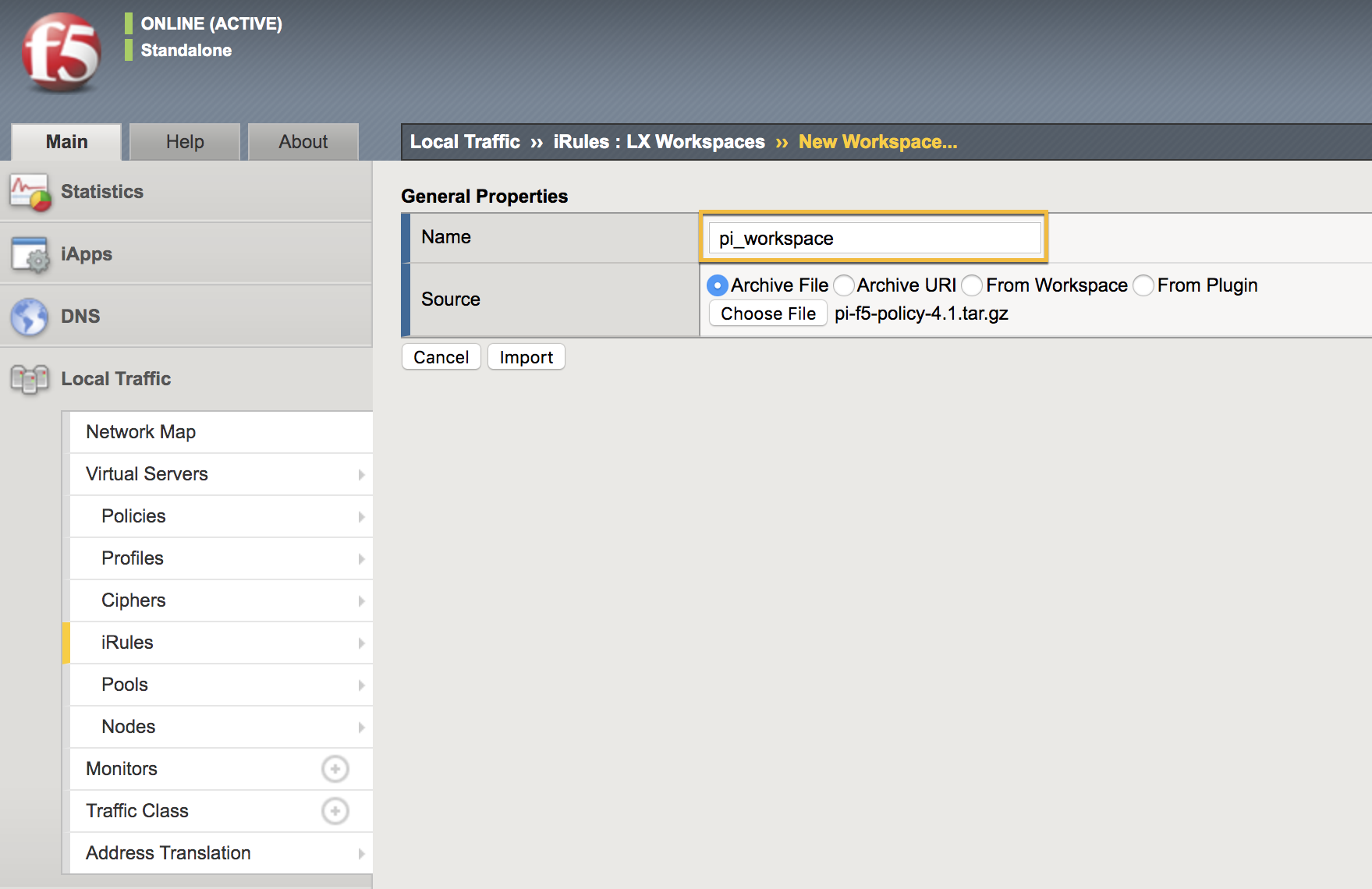
Result:
Clicking on Import creates an LX Workspace.
-
Click the Workspace.
The policy is pre-loaded with the extension
oi_ext. -
Edit the ASE configuration by clicking the ASEConfig.js file.
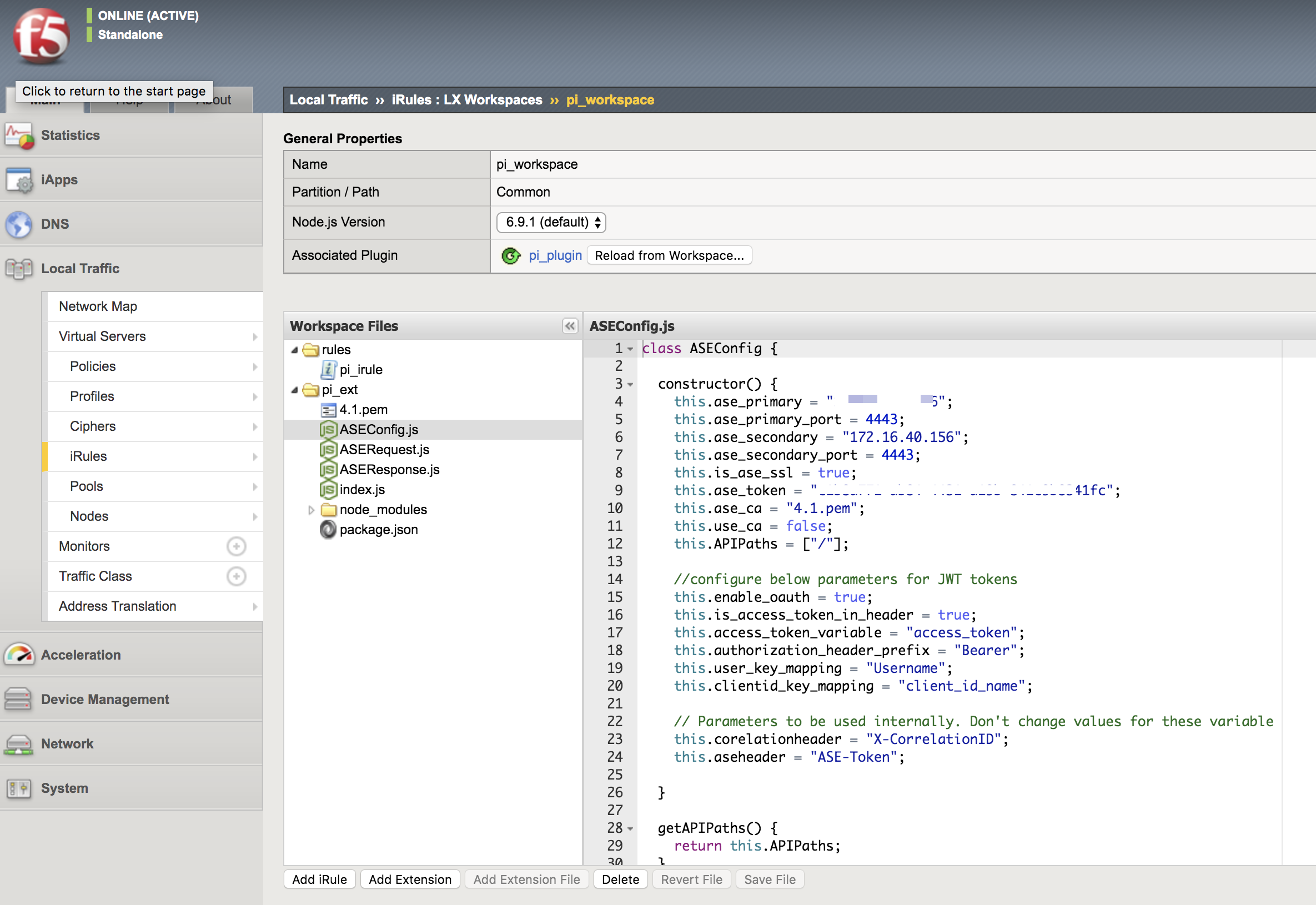
The following table describes the ASE variables:
+
| Variable | Description |
|---|---|
|
IP address of primary ASE node |
|
Port number of primary ASE node |
|
IP address of secondary ASE node |
|
Port number of secondary ASE node |
|
Set to |
|
The ASE sideband authentication token that was generated as part of prerequisites |
|
Set to |
|
Provide the list of paths that the policy should process. If |
|
Set to |
|
Set to |
|
If the access token is present in |
|
If the access token is present in |
|
The location of |
|
The location of client ID in JSON payload of JWT access token |
+
Result:
+ The PingIntelligence policy opens in the editor.