Extract user information from JWT in sideband mode
The API Security Engine (ASE) supports the decoding of transparent JSON Web Token (JWT) received as part of application programming interface (API) requests. ASE extracts the user information from the JWT and logs it in ASE access logs. The API Behavioral Security (ABS) AI Engine analyzes these access logs to generate reports and detect attacks.
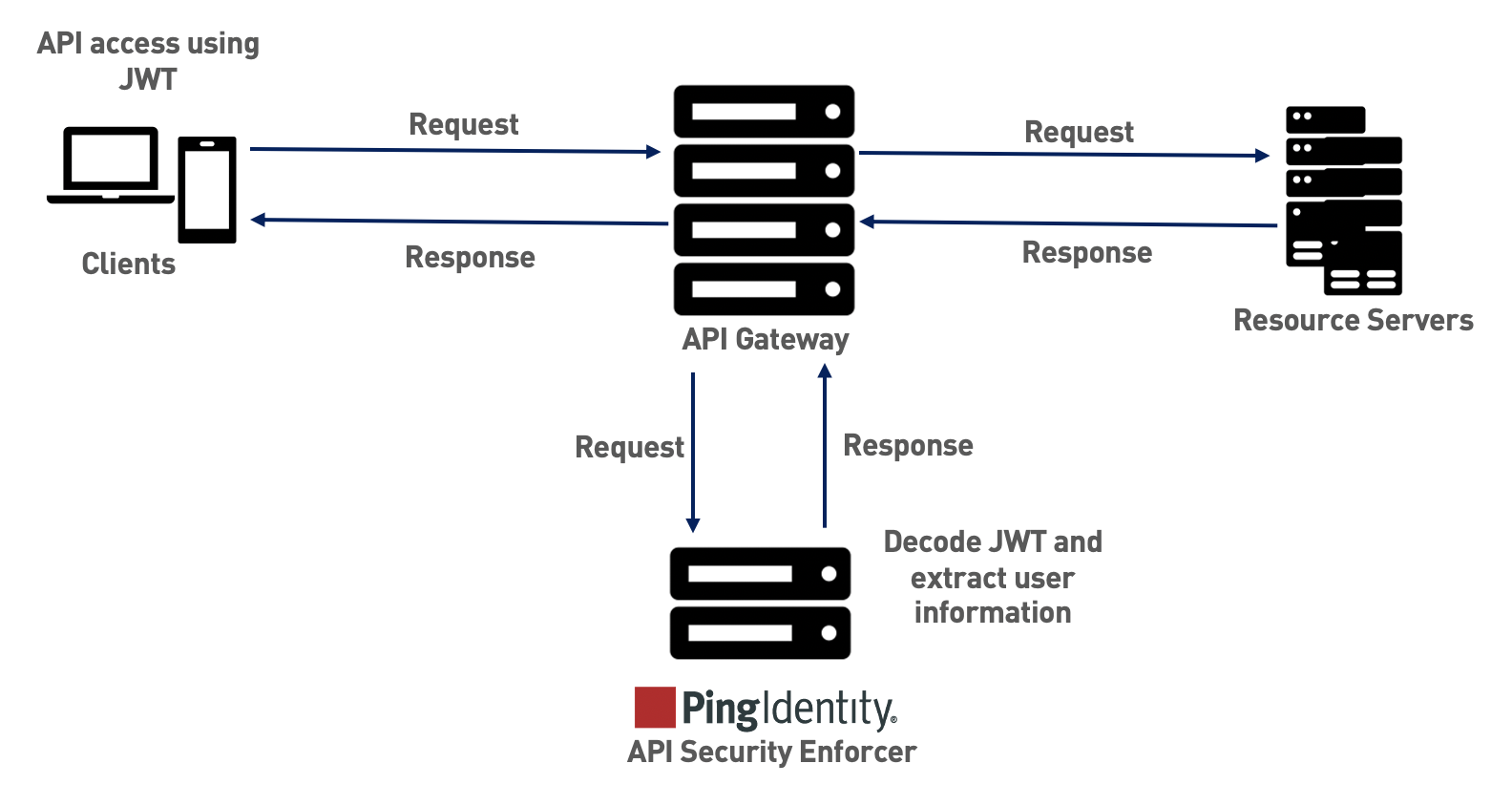
The following diagram shows the traffic flow when ASE is in sideband mode.
A JWT consists of a header, a payload, and a signature. They are concatenated with periods(.). The following is a sample JWT structure.

ASE decodes the payload to extract user information from a JWT. It can decode JWTs received as part of request headers or query strings. In sideband mode, ASE supports only Bearer scheme in the Authorization header.
|
ASE does not validate JWTs. It just decodes the JWTs and extracts the user information. |
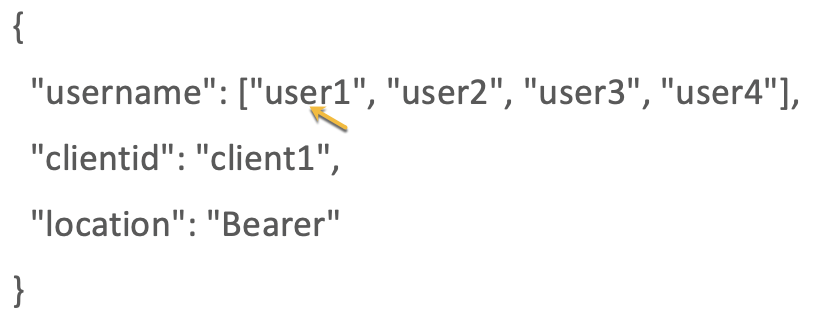
ASE supports a list of usernames in JWT. When the username claim in the payload is an array with multiple elements, ASE extracts the first element of the array. The elements in the array can be strings or numbers and the array should be a valid JavaScript Object Notation (JSON) array.
|
ASE supports arrays only for username claims in the payload. It does not support arrays in clientid or location claims. |
When deployed in sideband mode, ASE receives the API request information from the gateway policy and extracts the metadata. The user_info object contains the user information along with other metadata. The following is an example snippet of information received by ASE from API gateway:
{
“source_ip”: “127.0.0.1 ",
“source_port”: 12345,
“method”: “GET”,
“url”: “/api3?query=eyJ0eXAiOiJKV1QiLCJhbGciHuDXOyfQqAnoXC4bA&abc=xyz”,
“http_version”: “1.1”,
“user_info”:[{“username”:“abc”,“client_id”:“cabfsghhbsag”}],
“headers”: [ { “host”: “shop.com” },
{ “content-type”: “application/xml” },
{ “content-length”: “100” },
{ “x-forwarded-for”: “dev.pxy.com” },
{ “user-agent”: “Mozilla/5.0 (X11; Linux x86_64)
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/57.0.2987.110 Safari/537.36” }
]
}ASE extracts the user information from the user_info object, JWT or both. The following scenarios explain the different ways in which ASE extracts user information:
-
If the gateway policy sends the user_info object with
usernameandclientid, ASE does not decode the JWT. It extracts the user information from the user_info object. -
If the gateway policy sends the user_info object without
usernameandclientid, ASE decodes the JWT to extract the information. -
If the gateway policy sends the user_info object without a
username, but withclientid, ASE decodes the JWT and extractsusernamefrom the JWT and client identifier from the user_info object. -
If the gateway policy sends the user_info object with a
username, but without aclientid, ASE decodes the JWT to extractclientidand captures theusernamefrom the user_info object. -
If the gateway policy does not send user_info object or sends an invalid user_info object, ASE decodes the JWT to extract the
usernameandclientidinformation if available.
|
If the JWT decoding fails, the API request is not blocked. ASE logs the information got from the gateway policy in the access logs. |
The API JSON file
The behavior and properties of your API are defined in an API JSON file in ASE. To enable username capture, set the values for the parameters defined in the JWT object of the API JSON file as per your API setup. For more information, see Defining an API using API JSON configuration file in sideband mode.
The following is an example snippet of an API JSON file:
{
"api_metadata": {
"protocol": "http",
"url": "/rest",
"hostname": "*",
"cookie": "",
"cookie_idle_timeout": "200m",
"logout_api_enabled": false,
"cookie_persistence_enabled": false,
"oauth2_access_token": true,
"apikey_qs": "",
"apikey_header": "",
"login_url": "",
"enable_blocking": true,
"api_mapping": {
"internal_url": ""
},
"username_header": "",
"jwt": {
"location": "h:authorization:bearer",
"username": "username",
"clientid": "client_id"
}
}
}|
The values assigned to |
The following table explains the parameters in the JWT object of API JSON file.
| Parameter | Description |
|---|---|
|
The supported values for
https://server.example.com/resource?access_token=mF_9.B5f-4.1JqM&p=q
X-jwt-header: eyJhbGcUzI1NiI.eyJzDkwIG4gRG9xpZWQiOjwMjJ9.DWw5PDZEl-g
Authorization: Bearer eyJhbGIUzIiI.eyJzdiIxG4gRG9lIiwiZiOjJ9.DWPwNDZEl-g
Cookie: access_token=eyJhbGiIsI.eyJpc3MiOiJodHRwczotcGxlL.mFrs3ZodqKP4F1cB |
|
The JWT claim to extract the username. |
|
The JWT claim to extract the client identifier. |
When enable_blocking is set to true, ASE checks the username against the list of usernames in the allow list and deny list. If the username is in the deny list, the client using the username is blocked.
|
ASE also supports extracting a username from a custom HTTP header. However, you can configure username capture from either custom header or JWT, but not both. For more information, see Extract username from custom header in sideband mode. |
The API discovery process
The ABS AI Engine processes the ASE access logs and discovers new and unknown APIs in your environment. A root API JSON is defined in ASE to enable API discovery by ABS. If the root API JSON has a JWT object configured with values set for all the keys, then the APIs discovered by the ABS will have the JWT object. For more information on API discovery, see API discovery and configuration.
The following table explains the behavior of ASE when the root API JSON has an incomplete JWT object. It also describes its impact on the APIs discovered by ABS in your environment.
| Scenarios | Behavior of ASE | API discovery |
|---|---|---|
When a JWT object is not configured in |
ASE processes the |
A JWT object gets added to the discovered APIs with all the keys but empty values. For example: "jwt": {
"username": "",
"clientid": "",
"location": ""
}
|
When a JWT object is configured in the “jwt”:{}
|
ASE does not process the |
The API is not discovered. |
When a JWT object is configured with all the keys present but no values set. For example: "jwt": {
"username": "",
"clientid": "",
"location": ""
}
|
ASE processes the |
A JWT object gets added to the discovered APIs with all the keys but empty values. For example: "jwt": {
"username": "",
"clientid": "",
"location": ""
}
|
When a JWT object is configured but not all keys are set. For example: "jwt": {
"username": "",
"location": ""
}
|
ASE does not process the |
The API is not discovered. |
|
The API JSON file shipped with ASE is compatible with earlier versions of API JSON files. ASE automatically adds an empty JWT object to the API JSON file to maintain compatibility. |