Deploying PingIntelligence policies
Deploying PingIntelligence policies in the Akana API Gateway is divided into three parts:
About this task
-
Adding an input script (
config.js) -
Adding a PingIntelligence policy and applying the policy to APIs
-
Adding the RetainerHeader policy and applying the policy to APIs
Downloading PingIntelligence policies
About this task
To download and extract the PingIntelligence policy:
Steps
-
Download the PingIntelligence policy.
-
Extract the policies by running the following command:
# tar –zxvf <file name>
Example:
# tar –zxvf pi-api-akana-policy-4.1.1.tar.gz
Adding an input script
About this task
To add an input script to the Akana API gateway:
Steps
-
Sign on to Akana Policy Manager, navigate to Tenant, and click Scripts.
-
Click Add Script.
-
Enter Script Name and Script Description, and clickNext.
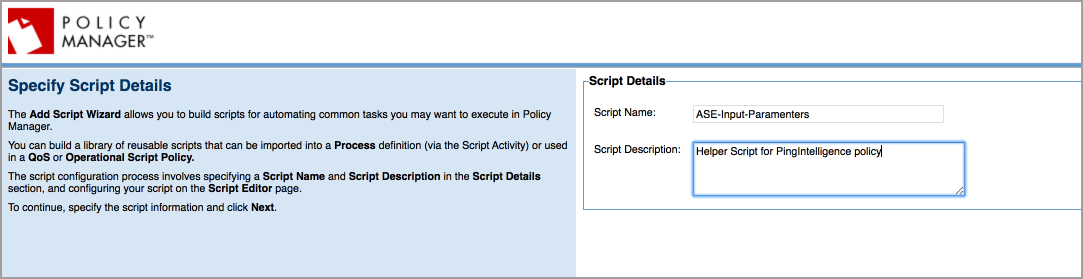
-
Select JavaScript for Language from the list.
-
Copy the contents of the
config.jsscript provided by PingIntelligence and paste them into the Source.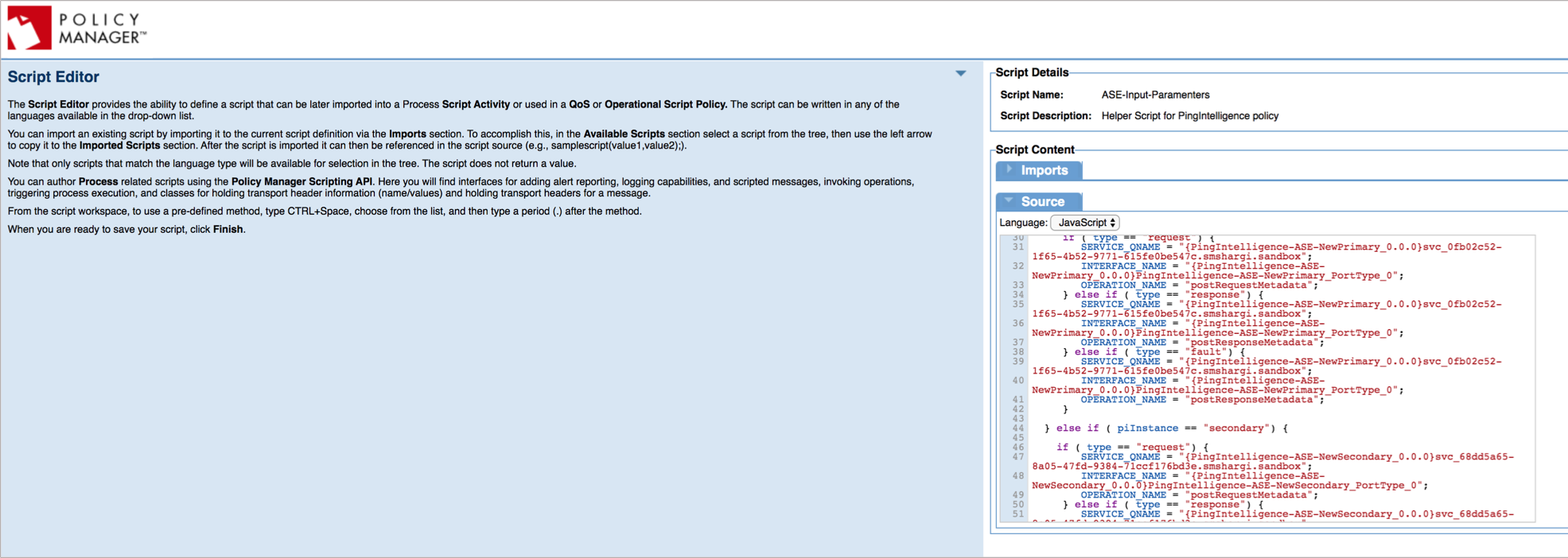
-
Paste the values of Service_QName, Interface_Name, and Operation_Name that were copied in Capturing ASE details.
This needs to be done for both primary and secondary ASE nodes. The following table lists the variables in
config.jsthat need to be populated.Variable Description ase_token
Variable for the ASE sideband authentication token.
primary_ase_service
Service QName for primary ASE.
primary_ase_interface
Interface Name for primary ASE.
primary_ase_request_operation
Operation Name for posting Request Metadata in primary ASE.
primary_ase_response_operation
Operation Name for posting Response Metadata in primary ASE.
secondry_ase_service
Service QName for secondary ASE.
secondary_ase_interface
Interface Name for secondary ASE.
secondary_ase_request_operation
Operation Name for posting Request Metadata in secondary ASE.
secondary_ase_response_operation
Operation Name for posting Response Metadata in secondary ASE.
Example:
Below is a sample substitution snippet:
var ase_token = "ASE-Token-123"; /Primary ASE Configuration/ var primary_ase_service = "{pi-as-ase-primary_0.0.0}svc_314492f1-ecdc-4184-93a0-57ee2258154b.smshargi.sandbox"; var primary_ase_interface = "{pi-as-ase-primary_0.0.0}pi-as-ase-primary_PortType_0"; var primary_ase_request_operation = "postRequestMetadata"; var primary_ase_response_operation = "postResponseMetadata"; /**/ /Secondary ASE Configuration/ var secondry_ase_service = "{pi-as-ase-primary_0.0.0}svc_314492f1-ecdc-4184-93a0-57ee2258154b.smshargi.sandbox"; var secondary_ase_interface = "{pi-as-ase-primary_0.0.0}pi-as-ase-primary_PortType_0"; var secondary_ase_request_operation = "postRequestMetadata"; var secondary_ase_response_operation = "postResponseMetadata"; -
Click Finish, and then click Close.
Adding a PingIntelligence policy
About this task
To add a PingIntelligence policy to the Akana API Gateway:
Steps
-
Sign on to Akana Policy Manager, navigate to the Tenant, and click Operational Policies under Policies.
-
Select Add Policy.
-
For Type, select Private Operational Script Policy from the drop-down list, and click Next.
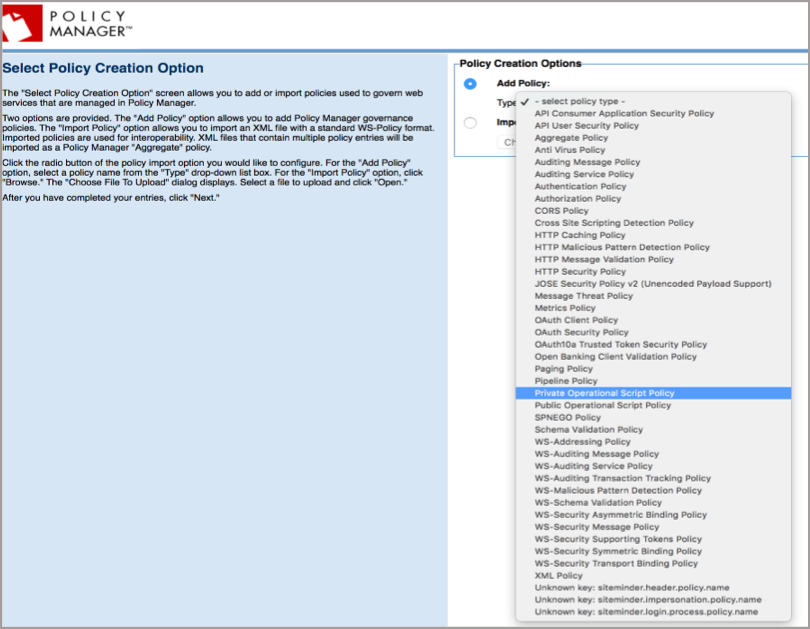
-
Enter Policy Name and Description, click Finish, and then click Close.
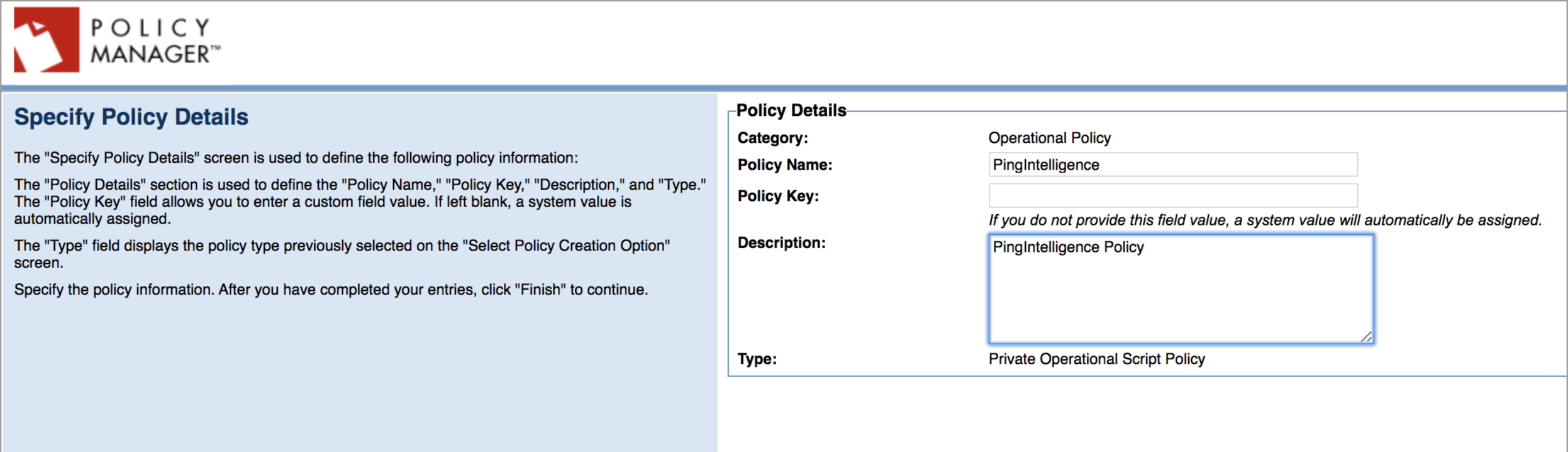
-
Navigate to Workbench.
-
In the Private Operational Script Policy section, select the policy name and click Modify.
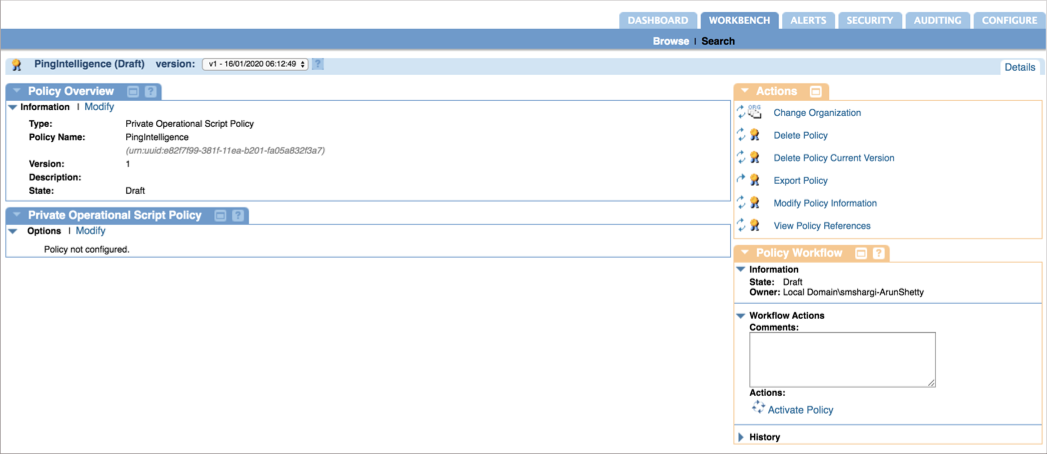
-
Click on Imports. Select the script added in Adding an input script and import it by clicking <<.
-
Select JavaScript for Language from the list.
-
Copy the contents of the
pi_policy.jsscript and paste them into Expression under Source.
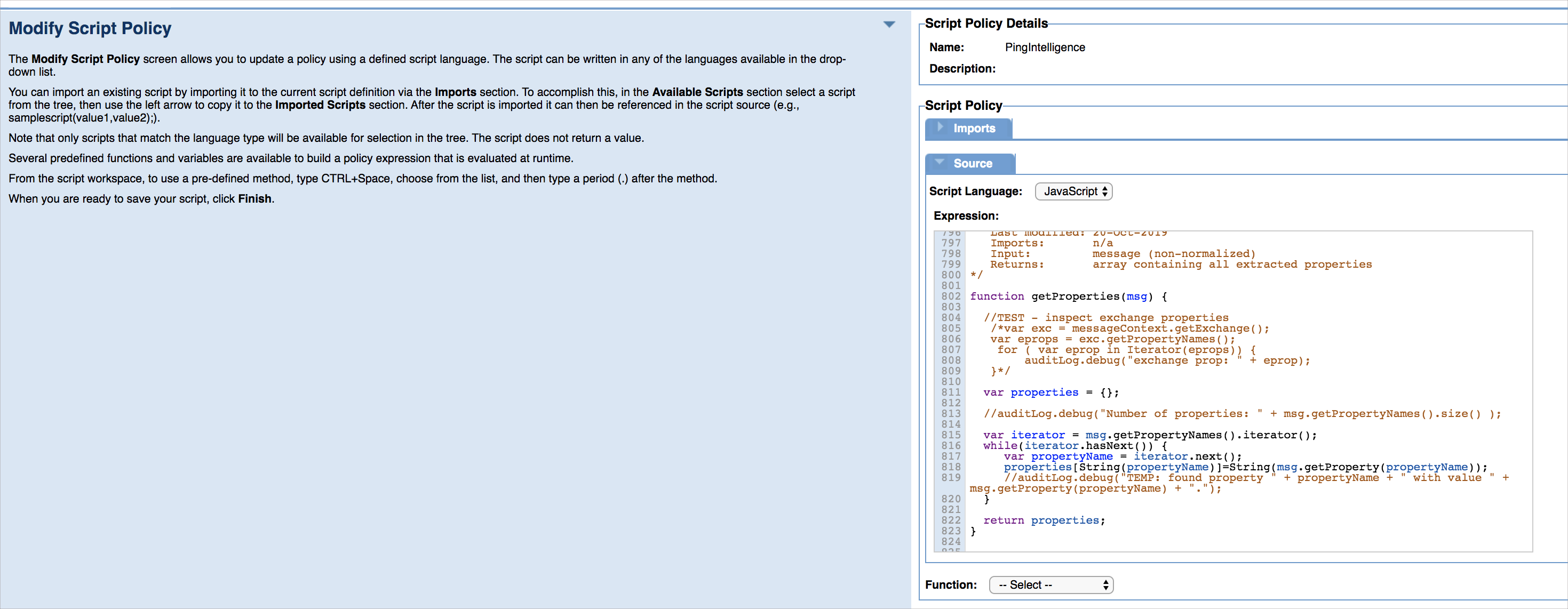
-
Click Finish and then click Close.
-
In the WorkFlow Actions, click Activate Policy to activate the PingIntelligence policy.
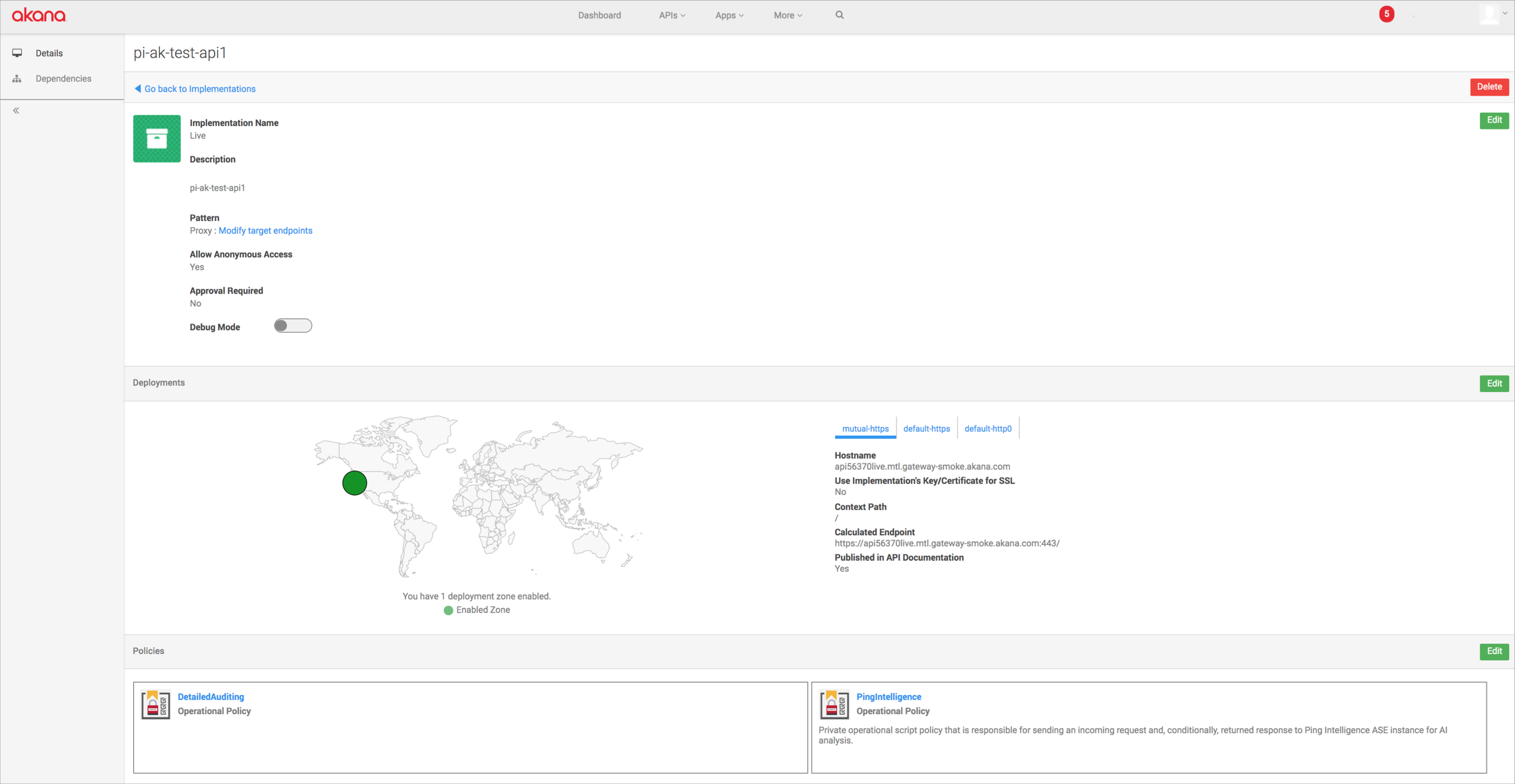
Applying the PingIntelligence policy to APIs
About this task
The PingIntelligence policy can be applied at tenant level, org level and at individual API level.
To add a policy at the API level:
Steps
-
Sign on to Akana Portal.
-
Click the API name.
-
In the left navigation, click Implementations.
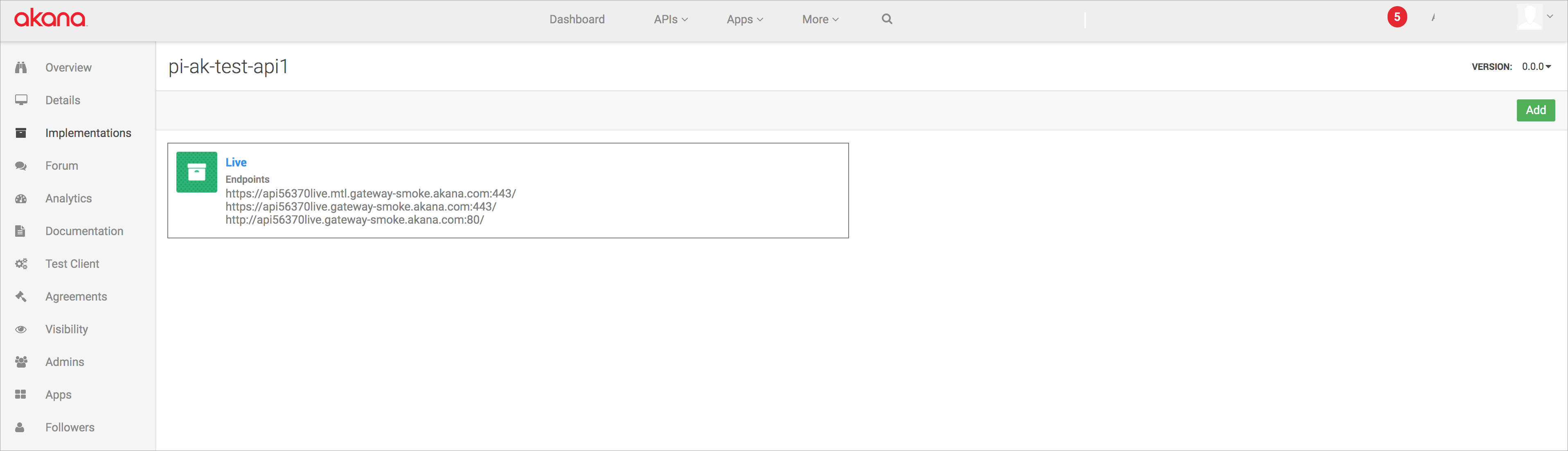
-
Click the API Implementation Name icon.
Possible values for API Implementation are
Live,Sandbox, orDevelopment. -
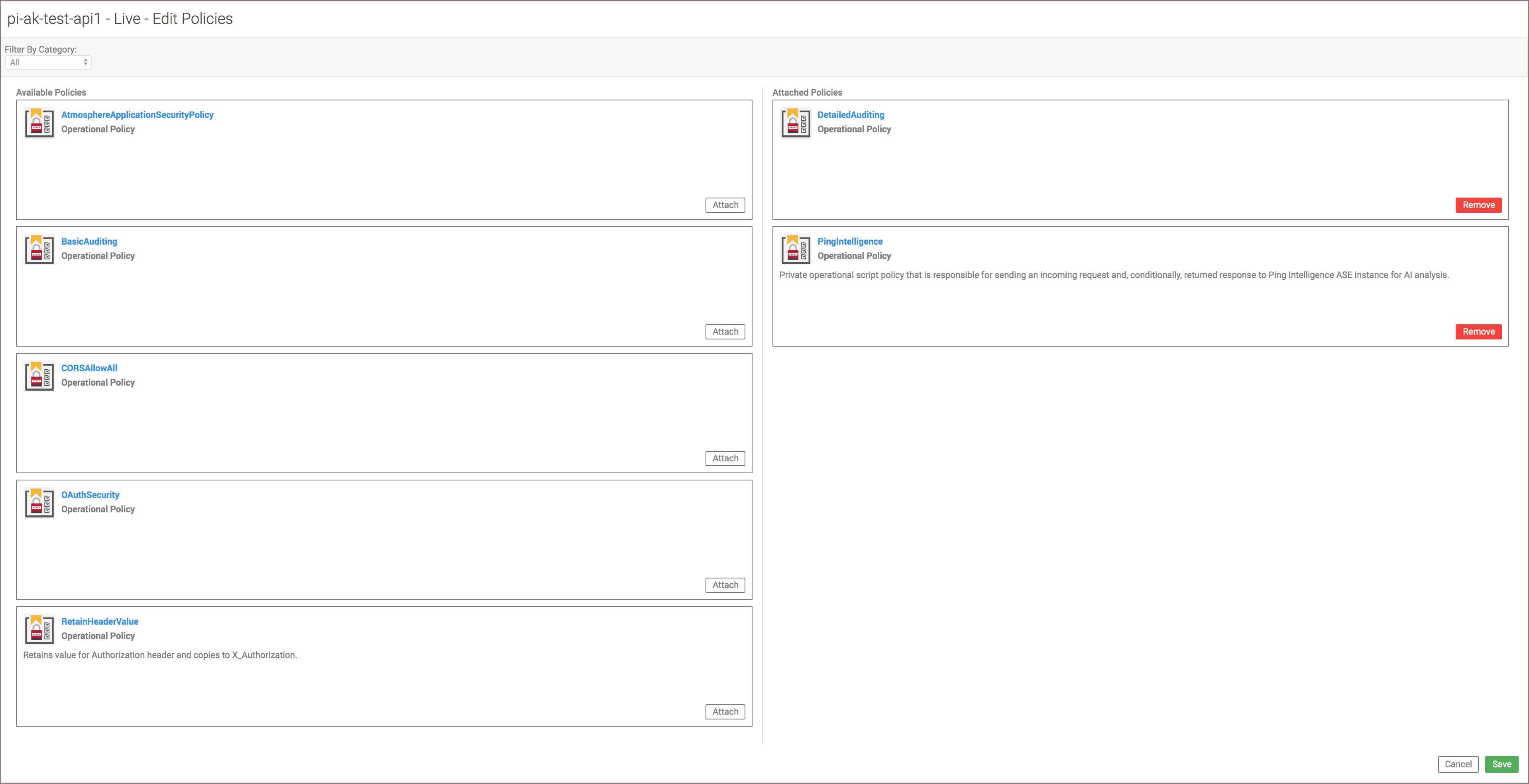
In the Policies section, click Edit.
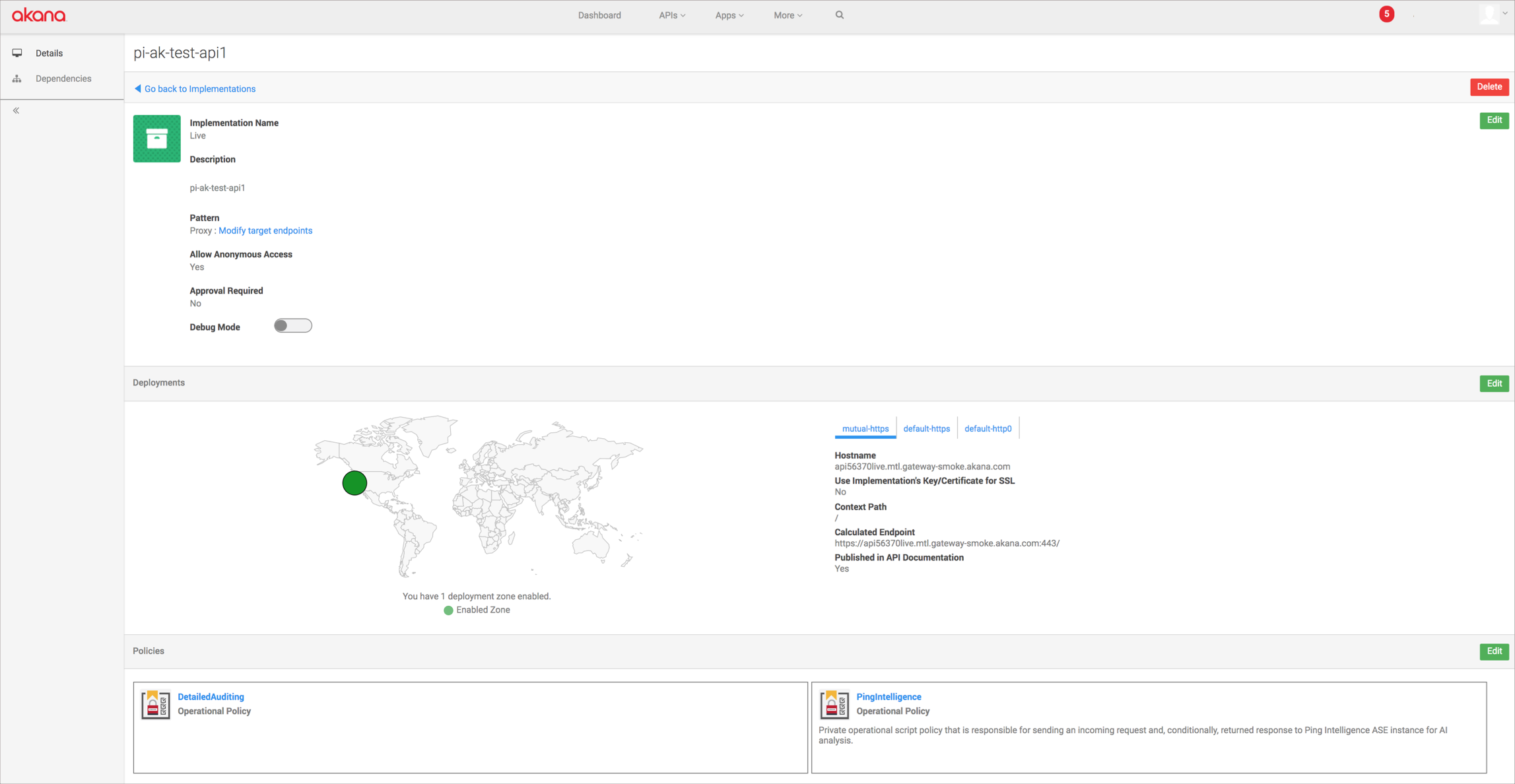
-
Find the PingIntelligence policy in the Available Policies pane, and click Attach under the PingIntelligence policy.
-
Click Save.
Adding the RetainHeader policy
About this task
To add the RetainHeader policy to the Akana API Gateway:
Steps
-
Sign on to Akana Policy Manager and click Tenant in the left navigation.
-
Under Policies, click Operational Policies.
-
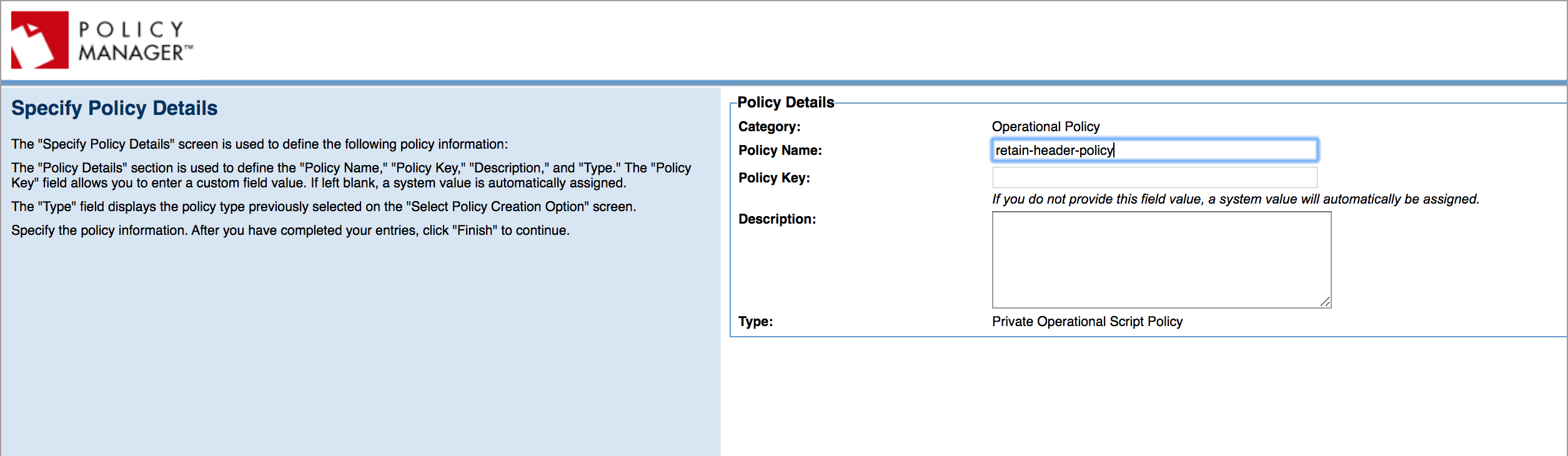
Select Add Policy and choose Private Operational Script Policy from the Type drop-down list.

-
Click Next.
-
Enter Policy Name and Description, click Finish, and then click Close.
-
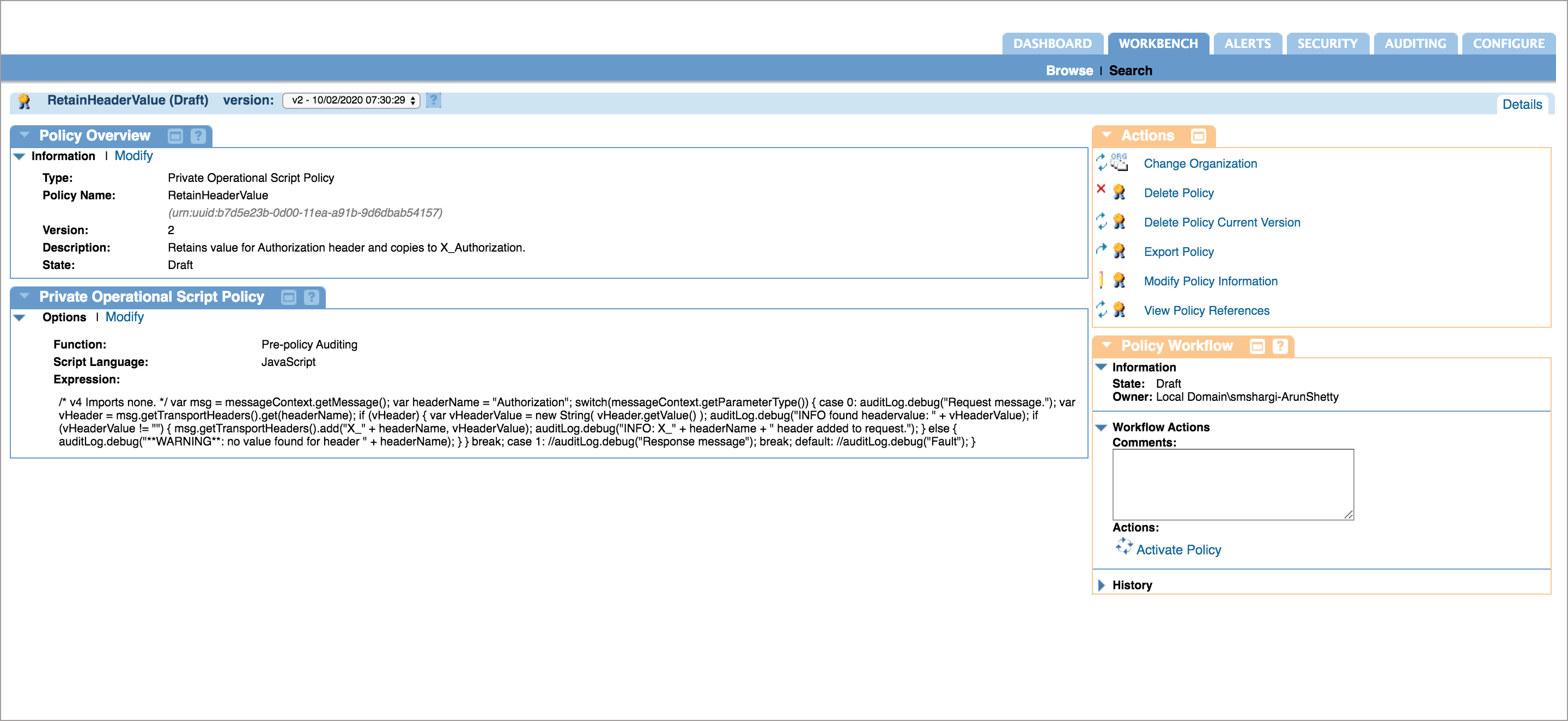
Navigate to the Workbench tab.
-
In the Private Operational Script Policy section, select the policy name and click Modify.
-
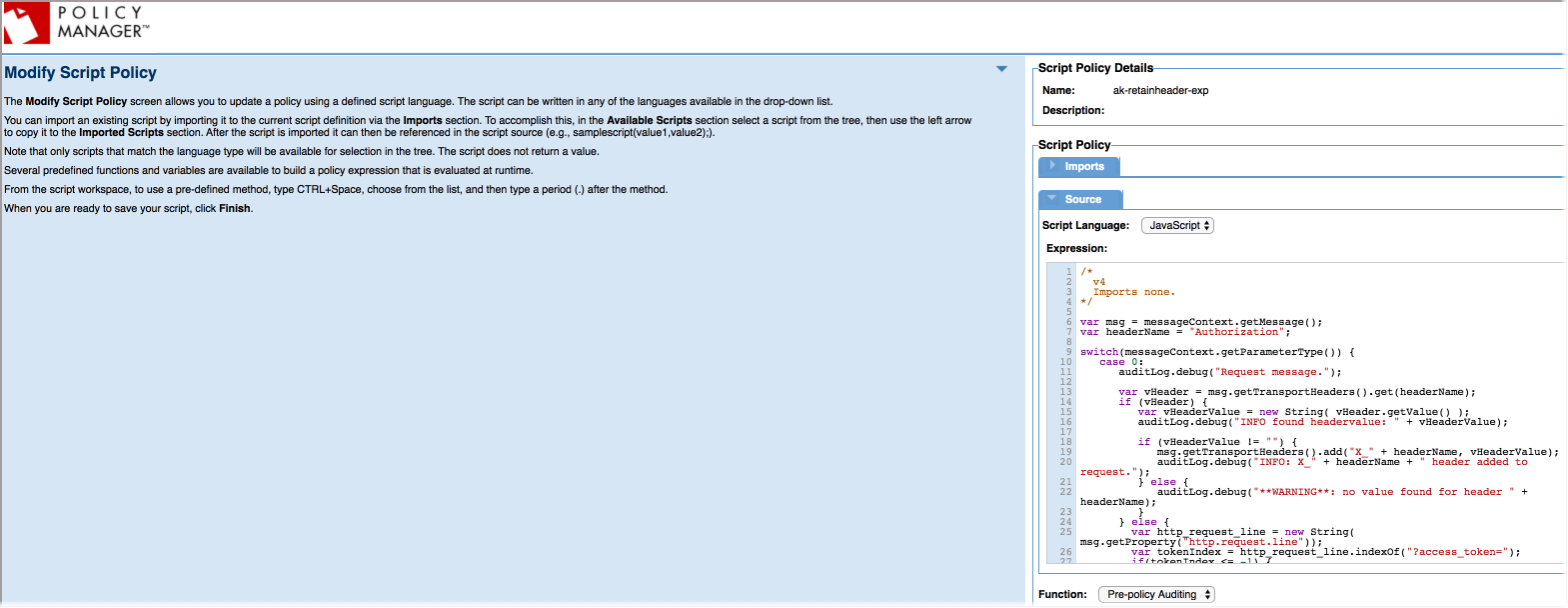
For Script Language, select JavaScript from the drop-down list.
-
Copy the contents of the
retain-header-policy.jsscript and paste them into Expression. -
For Function, select Pre-policy Auditing from the drop-down list.
-
Click Finish and then click Close.
-
Under the WorkFlow Actions, click Activate Policy to activate the RetainHeader policy.
Applying the RetainHeader policy to APIs
About this task
The RetainHeader policy can be applied at the tenant, org, and at individual API level.
To add a policy at the API level:
Steps
-
Sign on to the Akana Portal.
-
Click the API name.
-
In the left navigation, click Implementations.

-
Click the API Implementation Name icon.
Possible values for API Implementation are
Live,Sandbox, orDevelopment. -
In the Policies section, click Edit.
-
Under Available Policies, find the RetainHeader policy, and click Attach under the RetainHeader policy.
-
Click Save.
