Financial services journey
The Ping Identity Marketplace includes a prebuilt financial services journey. The journey provides secure and adaptive digital banking that protects against fraud and account takeover. It lets end users make safe payments and transfers, as well as managing accounts and privacy settings.
The journey is intended as a template. Review and adapt it to meet your organization’s specific security policies and business requirements before deploying to a production environment.
| Journey name | Version | Download |
|---|---|---|
Financial services |
1.0 |
This guide details the prerequisites and configuration steps to implement this solution in your Advanced Identity Cloud tenant.
About the financial services journey
This solution uses a main journey and inner journeys to evaluate the risk level of a user’s sign-on attempt. Authenticated end users can manage their account settings and make financial transactions.
Example use case
A bank needs to protect against fraud while maintaining a smooth customer experience. To do this, they want a journey that provides adaptive security by evaluating risk signals in real time across various end-user actions, from sign-on to financial transactions and data sharing. Users should be able to set preferences, such as enabling online payments and setting transaction limits. The solution would allow routine, low-value payments to proceed seamlessly, while automatically triggering a multi-factor authentication (MFA) challenge or knowledge-based authentication (KBA) for high-value transfers or suspicious activity to verify the user’s identity.
Journey components
The financial services journey includes one main journey and nine inner journeys.
| Journey | Description | Configuration required? | ||
|---|---|---|---|---|
Financial Services - Main Journey |
Orchestrates the entire user session, coordinating security checks before granting access to account management options. Show detailsThis journey orchestrates the entire user session, acting as the main entry point. It starts by checking for an active session. If none exists, it delegates the sign-on process to the Financial Services - SignOn Inner Journey. After the user is authenticated, the main journey performs the following security checks to secure the session:
After all security checks pass successfully, the user is redirected to the Financial Services - Manage Account Inner Journey, where they can access their account details and perform financial tasks. |
Yes |
||
Financial Services - SignOn Inner Journey |
Manages the initial user sign-on, including credential validation, email verification, and security checks Show detailsThe journey performs the following checks:
On successful completion of all checks, the user is granted access. |
No |
||
Financial Services - Threat Detection Inner Journey |
Performs real-time threat detection using PingOne Protect to assess session risk. Show detailsThe journey gathers behavioral data from the user’s session and determines a risk level. Depending on the assessed risk, the journey takes different paths:
|
Yes |
||
Financial Services - MFA Authentication Inner Journey |
Orchestrates the MFA process, prompting for and verifying a second factor. Show detailsThe journey starts by identifying an existing user and then prompts them to select an authentication method. The journey proceeds with one of the following MFA flows:
For most methods, if the user fails to authenticate, they’re given a limited number of retry attempts before the journey fails. The journey also includes paths for users to authenticate using a recovery code if other methods are unavailable. |
Yes |
||
Financial Services - Enhanced KBA Inner Journey |
Performs an enhanced Knowledge-based authentication (KBA) check. Show detailsThe journey starts by identifying an existing user. It then proceeds as follows:
The specific questions used for the challenge are configured in the PingOne Authorize policy’s statements. Learn more in Create the enhanced KBA policy. |
Yes |
||
Financial Services - Manage Account Inner Journey |
Presents as a post-authentication page that lets users perform account management tasks. Show detailsThe journey starts by checking for an active user session. If a session is found, it displays the Manage Your Account page where the user can choose from several options, such as Make a Payment, Make a Transfer, Account Settings, or Privacy Settings. The journey might require the user to perform MFA to increase their security level:
The journey then checks if a risk evaluation update with PingOne Protect is necessary and performs it. Finally, it directs the user to a separate, inner journey to handle their request. |
No |
||
Financial Services - Make Transfer Inner Journey |
Orchestrates the secure process for making transfers between a checking account and a savings account. It includes risk-based authorization checks. Show detailsThe journey starts by identifying the user. After successful identification, the user can proceed to enter the transfer amount and other details. The journey performs the following checks:
If the transfer is permitted, the user’s savings and checking account balances are updated. The journey includes paths to handle various errors, such as invalid input or insufficient balance, which typically redirect the user back to the Manage Your Account page to make corrections. |
Yes |
||
Financial Services - Make Payment Inner Journey |
Orchestrates the secure process for making transfers between a checking or savings account and a credit card or mortgage account. It includes risk-based authorization checks. Show detailsThe journey starts by identifying the user. After successful identification, the user can proceed to enter the payment amount and other details. The journey performs the following checks:
If the payment is permitted, the user’s mortgage or credit card account is updated. The journey includes paths to handle various errors, such as invalid input or insufficient balance, which typically redirect the user back to the Manage Your Account page to make corrections. |
Yes |
||
Financial Services - Account Settings Inner Journey |
Lets authenticated users view and modify their profile and account details. Show detailsThe journey starts by identifying the user. After successful identification, it displays the Account Settings page allowing the user to select account settings. If the user provides incorrect details, an error message shows, and the user is returned to the Account Settings page to make corrections. |
No |
||
Financial services - Privacy Settings Inner Journey |
Lets authenticated users manage their data sharing and privacy preferences. Show detailsThe journey starts by identifying the user. After successful identification, it displays the Privacy Settings page allowing the user to manage their privacy settings. |
No |
Before you begin
To implement the sample financial services journey, you must have the following prerequisites:
-
Tenant administrator access to your Advanced Identity Cloud development environment.
-
For PingOne Protect:
-
PingOne Protect enabled in your PingOne environment. Learn more in Getting started with PingOne Protect.
-
PingOne Protect integrated with Advanced Identity Cloud. Learn more in Use PingOne Protect for risk-based authentication and fraud detection.
-
-
For PingOne Authorize:
-
PingOne Authorize enabled in your PingOne environment. Learn more in Getting started with PingOne Authorize.
-
Your PingOne Authorize decision endpoint.
-
-
Your PingOne Worker service ID. Learn more in Set up PingOne workers and configure them as Advanced Identity Cloud services
The worker application associated with the PingOne Worker Service must be granted the necessary permissions to interact with both the PingOne Protect and PingOne Authorize services. -
For MFA:
-
If you’re using Twilio for phone-based MFA, a Twilio account with access to Twilio Verify.
-
-
A test user in your
Alpharealm with a registered email address. It’s also useful to have other MFA methods configured for testing. -
A basic understanding of journeys and the Scripted Decision node.
Task 1: Prepare your tenant environment
To get the journey working you must first perform some setup tasks in your Advanced Identity Cloud tenant environment.
Add custom attributes to the alpha_user managed object
Add the following custom attributes to the Advanced Identity Cloud alpha_user managed object.
Learn more in Customize user identities using custom attributes.
|
When adding new attributes, use advanced options to specify view and edit permissions:
|
User profile and security attributes
| Name | Label | Type | Description |
|---|---|---|---|
|
|
String |
Confirms the user has verified their email address. |
|
|
Array |
Stores the user’s registered MFA devices. |
|
|
String |
The user’s most recently used registered MFA device. |
Transaction and payment control attributes
| Name | Label | Type | Description | ||
|---|---|---|---|---|---|
|
|
String |
The user’s preferred currency. Select User Editable to allow end users to change this value. |
||
|
|
Number |
The user’s maximum payment limit. Ping Identity recommends that you enter a default value. For example, |
||
|
|
Number |
The user’s minimum payment limit. Ping Identity recommends that you enter a default value. For example, |
||
|
|
Boolean |
Indicates whether transactions are enabled or disabled for the user. Select User Editable to allow end users to change this setting. |
||
|
|
Number |
The maximum transaction value allowed for a single transaction. Ping Identity recommends that you enter a default value. For example, Select User Editable to allow end users to change this value in their account settings.
|
||
|
|
Number |
The transaction value above which push authentication is required. Ping Identity recommends that you enter a default value. For example, Select User Editable to allow end users to change this value in their account settings.
|
Account and balance attributes
| Name | Label | Type | Description |
|---|---|---|---|
|
|
Number |
The user’s current balance in their checking account. |
|
|
Number |
The user’s current balance in their savings account. |
|
|
Object |
Stores the user’s mortgage account details.
Add the following properties in the
|
|
|
Object |
Stores the user’s credit card details. Add the following properties in the
|
Advanced and calculated attributes
| Name | Label | Type | Description |
|---|---|---|---|
|
|
Object |
Stores user preferences for account visibility to third-party vendors Add the following properties in the
|
|
|
Array |
An array of objects, where each object stores details of a past transaction. This is used to calculate the KBA threshold. A maximum of 50 days of transactions are stored. Add the following properties in the
|
|
|
Number |
The threshold limit for triggering a KBA prompt, calculated based on the |
(Optional) Set an ESV variable for PingOne Protect analysis
The Prerequisites & Init Variables node in the main journey contains a script that uses the protectAnalysisRequired variable to determine if PingOne Protect analysis is enabled. By default, this variable is set to true in the script.
To override this variable and control how PingOne Protect analysis is performed in different environments, you can set an Environment Secret & Variable (ESV) variable.
-
In the Advanced Identity Cloud admin console, go to Tenant Settings > Global Settings > Environment Secrets & Variables.
-
On the Variables tab, click + Add Variable.
-
In the Add a Variable modal, enter the following information:
Name
p1-protect-analysis-requiredType
stringDescription (optional)
PingOne Protect analysis requiredValue
true -
Click Save to create the variable.
-
Restart Advanced Identity Cloud services by applying updates in the Advanced Identity Cloud admin console.
Task 2: Create PingOne Authorize policies
To perform risk-based authorization for payments and transfers, you must create two authorization policies in PingOne Authorize. These policies use custom attributes to evaluate the context of a transaction.
Define the attributes
First, define the attributes that the policies will use to make decisions.
-
In the PingOne admin console, go to Authorization > Trust Framework.
-
Click the Attributes tab.
-
For each attribute in the following table, click + Add new Attribute and configure it with the specified values. For these attributes, you’ll need to add a second resolver to set a default constant value.
Attribute name Value type Default resolver type Default value ActionString
Constant (String)
DefaultamountNumber
Constant (Number)
-1custom_approvalLimitNumber
Constant (Number)
-1custom_transactionLimitNumber
Constant (Number)
-1Show attributes
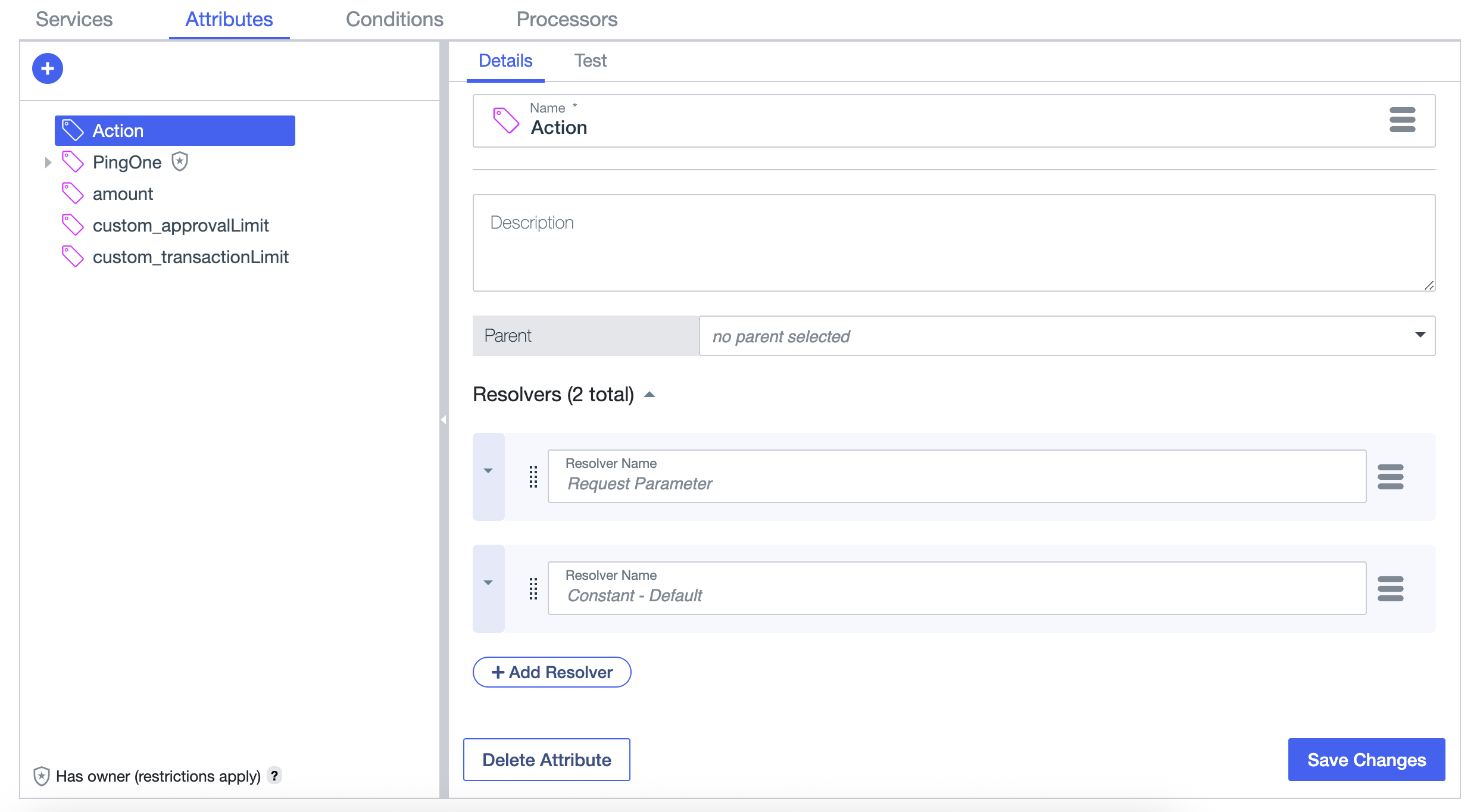
Create the payment check policy
This policy evaluates a payment’s amount against the user’s transaction limits.
-
In the PingOne admin console, go to Authorization > Policies.
-
Click the Plus icon () and select Add Policy.
-
Configure the main policy settings:
-
Name:
AIC payment checks -
Applies When: The policy applies when all of the following comparisons are true:
-
amountDoes Not Equal-1 -
custom_transactionLimitDoes Not Equal-1 -
custom_approvalLimitDoes Not Equal-1
-
-
-
Add the following rules to the policy in order.
Rule 1: Deny payments over the maximum limit-
Name:
Deny payments over maximum transaction limit -
Applies When:
amountGreater Thancustom_transactionLimit -
Effect:
Deny
Rule 2: Permit payments under the approval threshold-
Name:
Permit payments less than threshold limit -
Applies When:
amountLess Than or Equalcustom_approvalLimit -
Effect:
Permit
Rule 3: Require approval for payments over the threshold-
Name:
Require approval for payments over threshold limit -
Applies When:
amountGreater Thancustom_approvalLimit -
Effect:
Permit -
Statements: Add a statement with the following values:
-
Name:
Push required -
Code:
PUSH_REQ
-
-
-
Click Save Changes.
Create the enhanced KBA policy
This policy determines if a KBA challenge is required based on the Action attribute.
-
In the PingOne admin console, go to Authorization > Policies.
-
Click and select Add Policy.
-
Configure the main policy settings:
-
Name:
Enhanced KBA Policy -
Applies When:
ActionDoes Not EqualDefault
-
-
Add the following rules to the policy in order.
Rule 1: Deny rule-
Name:
Deny if Action is Deny -
Applies When:
ActionEqualsdeny -
Effect:
Deny
Rule 2: Permit rule-
Name:
Permit if Action is Permit -
Applies When:
ActionEqualspermit -
Effect:
Permit
Rule 3: KBA challenge rule-
Name:
Challenge if Action is Challenge -
Effect:
Permit if condition holds, otherwise deny -
When:
ActionEqualschallenge -
Statements: Add a statement with the following values:
-
Name:
KBA_REQUIRED -
Code:
KBA_REQUIRED -
Create:
On Permit -
Payload:
Show payload
{ "kbaQuestionSets": [ { "question": { "key": "Q1", "text": "Wait - could this be a scam? Tell us your reason so we can protect you." }, "answers": { "1": { "key": "Q1.A1", "text": "Making an investment", "action": "challenge" }, "2": { "key": "Q1.A2", "text": "Account Transfer", "action": "permit" }, "3": { "key": "Q1.A3", "text": "Investing in Crypto", "action": "deny" } } }, { "question": { "key": "Q2", "text": "This seems to be an unusual payment. To help us protect your account, what is the primary reason for this transfer?" }, "answers": { "1": { "key": "Q2.A1", "text": "Paying a family member or a friend.", "action": "permit" }, "2": { "key": "Q2.A2", "text": "Purchasing a high-value item (e.g., car, jewelry).", "action": "challenge" }, "3": { "key": "Q2.A3", "text": "Investing in cryptocurrency.", "action": "deny" }, "4": { "key": "Q2.A4", "text": "To secure my funds after an unexpected call from my bank/police.", "action": "deny" }, "5": { "key": "Q2.A5", "text": "An online investment with guaranteed high returns.", "action": "deny" } } }, { "question": { "key": "Q3", "text": "We see this is a new recipient. How did you receive their account details?" }, "answers": { "1": { "key": "Q3.A1", "text": "From an official company invoice or website.", "action": "permit" }, "2": { "key": "Q3.A2", "text": "From an email or text message.", "action": "challenge" }, "3": { "key": "Q3.A3", "text": "Over the phone from someone who called me unexpectedly.", "action": "deny" }, "4": { "key": "Q3.A4", "text": "From a person I have only met on a social media or dating app.", "action": "deny" } } }, { "question": { "key": "Q4", "text": "Are you being pressured to make this payment right now to avoid a fine, unlock an account, or secure a prize?" }, "answers": { "1": { "key": "Q4.A1", "text": "No, I am making this payment on my own time without any pressure.", "action": "permit" }, "2": { "key": "Q4.A2", "text": "Yes, I was told it must be done immediately.", "action": "deny" }, "3": { "key": "Q4.A3", "text": "I am not sure if I am being pressured.", "action": "challenge" } } }, { "question": { "key": "Q5", "text": "Is anyone you do not personally know guiding you through this payment on your computer or phone right now?" }, "answers": { "1": { "key": "Q5.A1", "text": "No, I am in full control and completing this myself.", "action": "permit" }, "2": { "key": "Q5.A2", "text": "Yes, a support agent or bank employee is helping me remotely.", "action": "deny" }, "3": { "key": "Q5.A3", "text": "A friend or family member is helping me.", "action": "challenge" } } }, { "question": { "key": "Q6", "text": "Have you ever met the person you are sending this money to in real life?" }, "answers": { "1": { "key": "Q6.A1", "text": "Yes, they are a friend, family member, or business contact I know personally.", "action": "permit" }, "2": { "key": "Q6.A2", "text": "No, I have only ever interacted with them online or over the phone.", "action": "deny" }, "3": { "key": "Q6.A3", "text": "This is for an online purchase from a company.", "action": "challenge" } } }, { "question": { "key": "Q7", "text": "What is the expected outcome of this payment?" }, "answers": { "1": { "key": "Q7.A1", "text": "To pay for goods or services from a known vendor.", "action": "permit" }, "2": { "key": "Q7.A2", "text": "To pay a tax bill or government fine I was notified of by phone or email.", "action": "deny" }, "3": { "key": "Q7.A3", "text": "To claim lottery winnings, an inheritance, or a prize.", "action": "deny" }, "4": { "key": "Q7.A4", "text": "To pay a contractor for home repairs.", "action": "challenge" } } } ] }
-
-
-
Click Save Changes.
Task 3: Download and import the journey
Download the journey
-
Go to Financial Services journey on the Ping Identity Marketplace.
-
Click Download Integration to download the
Financial Services - Main Journey.jsonfile. This JSON file contains the main journey and inner journeys, scripts, and email templates required for the authentication flow.
Import the journey
-
In the Advanced Identity Cloud admin console, go to Journeys, and click Import.
-
Click either Download Backup or Skip Backup. Learn more in Import journeys.
-
On the Import Journeys page, browse to and select
Financial Services - Main Journey.json. -
Select
Alpha realm usersbecause the journey is configured for the Alpha realm. -
In the Conflict Resolution section, choose how the system resolves import conflicts:
-
Overwrite all conflicts (default)
-
Manually pick conflict resolution
-
-
Click Next.
-
Click Start Import.
-
On the Import Complete page, click Done.
-
On the left panel of the Journeys page, click Financial Services (10) view the financial services main journey and inner journeys.
Task 4: Configure the journey components
Configure the financial services main journey
-
On the Journeys page, click Financial Services - Main Journey and click Edit.
-
In the journey editor, configure the journey as follows:
-
Click Save.
| To save your progress, periodically click Save in the top right of the journey editor. If you don’t save, you’ll lose your work if the page reloads or if you lose your network connection. |
Review and set the initialize variables
The Financial Services - Main Journey includes a Scripted Decision node containing the initialize variables used later in the authentication flow. This script lets you:
-
Set the allowed MFA types:
FIDO2,OATH,PUSH,EMAIL,SMS,VOICE. -
Enable or disable PingOne Protect analysis.
-
Enable or disable magic link.
To review and set the initial variables:
-
Click the Prerequisites & Init Variables node.
-
In the Script field, click the Pencil icon () to open the
Financial Services - Initialize Variablesscript. -
Review the script and make changes if needed.
-
Click Save and Close.
| You don’t need to update the values in the Script Outputs field of the Prerequisites & Init Variables node. |
Configure the success URL
-
Click the Success URL node.
-
Enter the preview URL of the Financial Services - Manage Account Inner Journey. For example:
https://<tenant-env-fqdn>/am/XUI/?realm=alpha&authIndexType=service&authIndexValue=Financial%20Services%20-%20Manage%20Account%20Inner%20Journey. -
Click Save.
Configure the Threat Detection Inner Journey
-
On the Journeys page, click Financial Services - Threat Detection Inner Journey and click Edit.
-
In the journey editor, configure the journey as follows:
-
Click the PingOne Protect Initialize node and enter the following:
-
PingOne Worker Service ID: Select the ID of the PingOne Worker Service for connecting to PingOne. Learn more in PingOne Protect Initialize node.
-
-
Click the Auth: PingOne Protect Authentication node and enter the following:
-
PingOne Worker Service ID: Select the ID of the PingOne worker service for connecting to PingOne.
-
(Optional) Risk Policy Set ID: Enter the ID of the risk policy in PingOne. Learn more in PingOne Protect Evaluation node.
-
-
Click the PingOne Protect Authorization node and enter the following:
-
PingOne Worker Service ID: Enter the ID of the PingOne worker service for connecting to PingOne.
-
(Optional) Risk Policy Set ID: Enter the ID of the risk policy in PingOne. Learn more in PingOne Protect Evaluation node.
-
-
-
Click Save.
Configure the MFA Authentication Inner Journey
This configuration is required if SMS, or VOICE are opted in the allowedMFATypes array in the Financial Services - Initialize Variables script in the Prerequisites & Init Variables node in the main journey.
-
On the Journeys page, click
MFA Authentication Inner Journeyand click Edit. -
In the journey editor, update the required fields in the following nodes:
-
Click Save.
Configure the Enhanced KBA Inner Journey
-
On the Journeys page, click Financial Services - Enhanced KBA Inner Journey and click Edit.
-
In the journey editor, click the PingOne Authorize node and enter the following:
-
PingOne Worker Service ID: Select the ID of the PingOne worker service for connecting to PingOne.
-
In the Decision Endpoint ID: Enter the decision endpoint ID from the service in PingOne Authorize
Learn more about the PingOne Authorize node
-
-
Click Save.
Configure the Make Payment Inner Journey
-
On the Journeys page, click Financial Services - Make Payment Inner Journey and click Edit.
-
In the journey editor, click the PingOne Authorize node and enter the following:
-
PingOne Worker Service ID: Select the ID of the PingOne worker service for connecting to PingOne.
-
In the Decision Endpoint ID: Enter the decision endpoint ID from the service in PingOne Authorize.
Learn more about the PingOne Authorize node
-
-
Click Save.
Configure the Make Transfer Inner Journey
-
On the Journeys page, click Financial Services - Make Transfer Inner Journey and click Edit.
-
In the journey editor, click the PingOne Authorize node and enter the following:
-
PingOne Worker Service ID: Select the ID of the PingOne worker service for connecting to PingOne.
-
In the Decision Endpoint ID: Enter the decision endpoint ID from the service in PingOne Authorize.
Learn more about the PingOne Authorize node
-
-
Click Save.
Task 5: Validate the journey
After configuring the journey, test the different paths to ensure the risk-based security policies work as expected. The following steps demonstrate low-risk and high-risk sign-on attempts, and low-risk and high-risk transactions.
|
To trigger different risk evaluations, you may need to adjust your risk policies in PingOne Protect or sign on using different conditions (for example, using a VPN or a new device to simulate higher risk). |
Before you begin
Add values for the following attributes for your test user: In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
Click Alpha realm - Users and
-
On the Manage Identities page, click Alpha realm - Users and find and select your test user.
-
Enter values in the following fields:
-
Minimum payment limit
-
Maximum payment limit
-
Latest savings balance
-
Latest checking balance
-
Account visibility
-
Mortgage account
-
Credit card account
-
Custom currency
-
-
Click Save.
Test a low-risk sign-on
-
In the Advanced Identity Cloud admin console, go to Journeys.
-
Click Financial Services - Main Journey.
-
In the Preview URL field, click and paste the URL into an incognito window.
The browser displays the Sign In hosted journey page.
-
Enter your test user’s username and password and click Next.
The browser displays the Manage Your Account hosted account page.
Because the sign-on is evaluated as low risk, you’re authenticated without an MFA challenge. This confirms the frictionless path is working correctly. 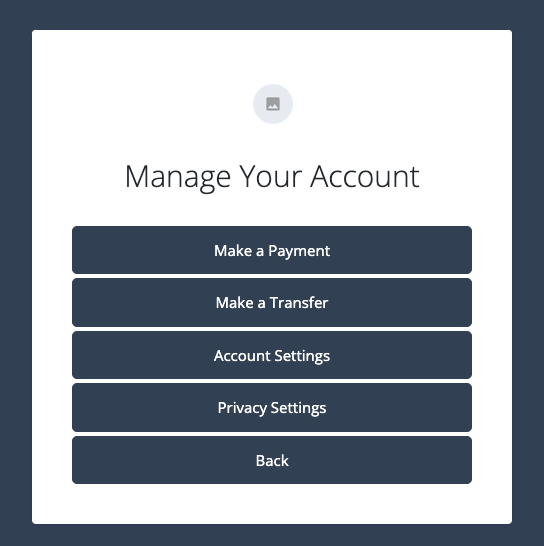
-
Click Account Settings and complete the following:
-
The maximum allowed transaction limit during any transaction:
1000 -
The threshold limit above which push approval step is required before successful transaction:
500 -
Online Transactions:
Enabled
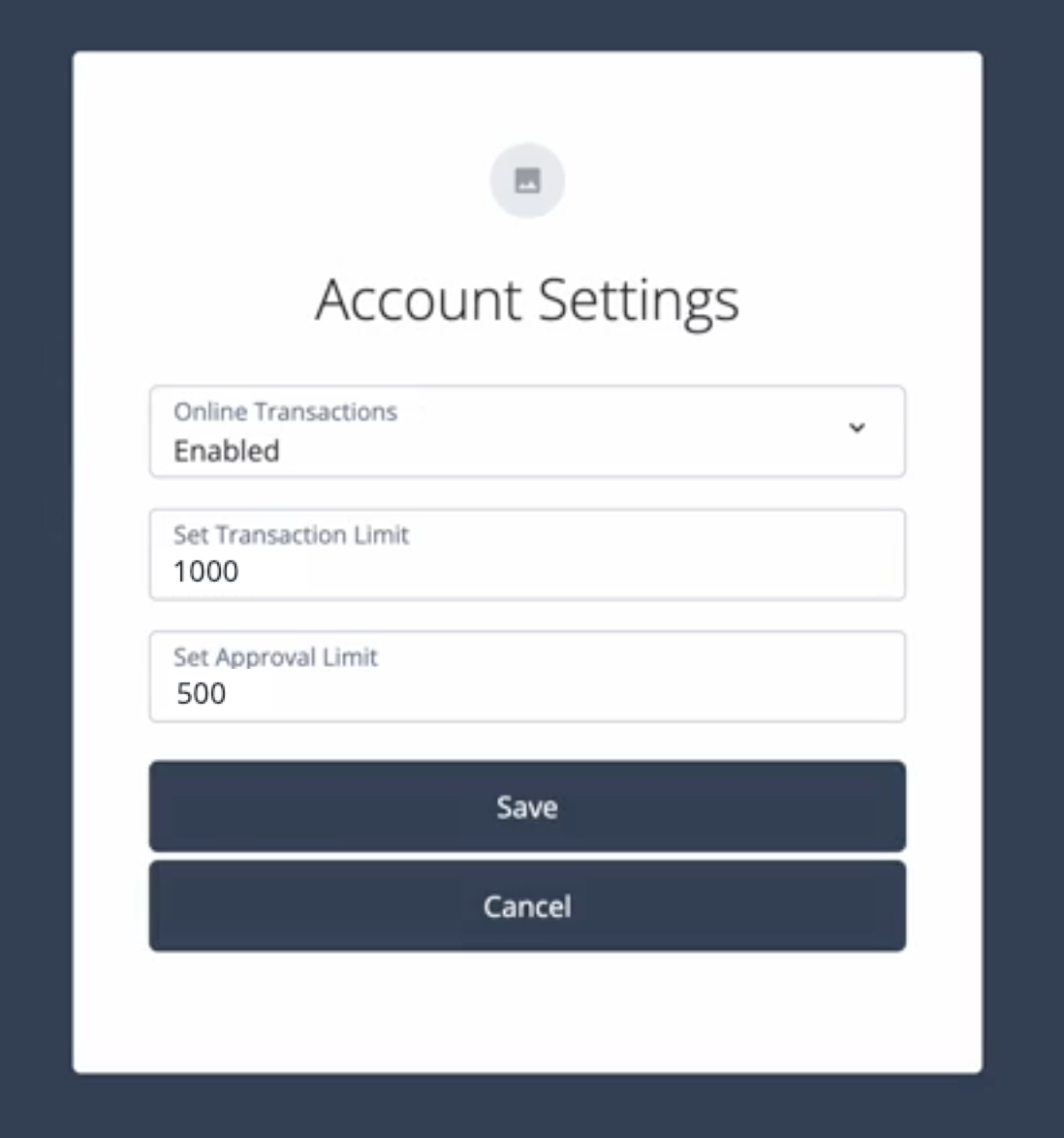
-
-
Click Save.
Test a high-risk sign-on
This test validates that the journey blocks a sign-on attempt that PingOne Protect evaluates as high risk (for example, an attempt from an anonymous proxy).
-
Using a new incognito window or a browser configured to use a VPN, go to the preview URL for the Financial Services - Main Journey.
-
On the Sign In screen, enter your test user’s username and password and click Next.
Expected result: The journey identifies the high-risk attempt and blocks the sign-on. An error message displays, and the user’s account might be disabled. You should also receive an email notification confirming that the high-risk security response was triggered.
Test a low-risk payment
-
If you’re not already signed on, follow the steps in Test a low-risk sign-on to sign on as your test user.
-
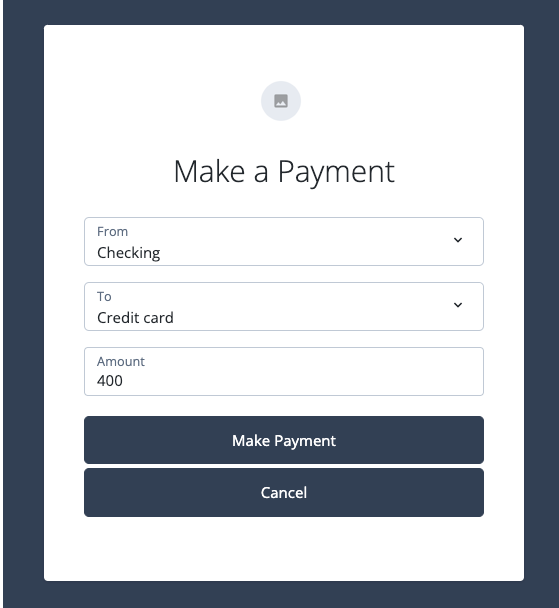
Click Make a Payment.
-
Enter a payment amount below the transaction threshold (for example,
400).
-
Click Make Payment.
Expected result: The payment is successful. The page confirms the transaction was completed, and the user’s account balance is updated.
Test a high-risk payment
This test validates that a payment exceeding the maximum transaction limit is blocked.
-
If you’re not already signed on, follow the steps in Test a low-risk sign-on to sign on as your test user and arrive at the Manage Your Account page.
-
Click Make a Payment.
-
Enter a payment amount greater than the payment limit (for example,
6000) and complete the payment details. -
Click Submit.
Expected result: The payment is denied. An error message displays, indicating that the transaction exceeds the maximum limit. This confirms the high-risk payment path is correctly blocking the transaction.
Best practices
This sample journey provides a strong foundation for a financial services journey. When preparing to use it in a production environment, consider the following best practices:
-
Treat as a template: Remember that this is a sample journey. Always adapt and harden it to meet your specific security policies and business requirements before deploying to production.
-
Use ESVs: Avoid hardcoding sensitive information like API keys and IDs directly in your journey scripts. Use ESVs to manage these values securely.
-
Test extensively: Validate all possible user paths, including low, medium, and high-risk scenarios, as different MFA registration and authentication flows. Ensure the user experience is smooth and the security responses are correct for each case.
-
Review PingOne Protect policies: Fine-tune your risk policies in PingOne Protect to align with your organization’s risk tolerance.