Configuring SAML SSO with Slack and PingFederate
Enable Slack sign-on from a PingFederate URL (IdP-initiated sign-on) and direct Slack sign-on using PingFederate (SP-initiated sign-on) with JIT provisioning.
Before you begin
-
Configure PingFederate to authenticate against an IdP or datastore containing the users that require application access.
-
You must have administrative access to PingFederate and Slack.
Create a PingFederate SP connection for Slack
-
Sign on to the PingFederate administration console.
-
Create a service provider (SP) connection for Slack in PingFederate:
-
Configure using Browser SSO profile SAML 2.0.
-
Set Partner’s Entity ID to
https://slack.com. -
Enable the following SAML Profiles:
-
IdP-Initiated SSO
-
SP-Initiated SSO
-
-
In Assertion Creation > Attribute Contract, extend the contract with the following attributes:
-
SAML_NAME_FORMAT -
User.Email -
User.Username -
first_name -
last_name
Use the following attribute name format:
urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified -
-
In Assertion Creation → Authentication Source Mapping → Attribute Contract Fulfillment:
-
Map SAML_SUBJECT, User.Email, User.Username, first_name, and last_name.
-
Map SAML_NAME_FORMAT to a text value of
urn:oasis:names:tc:SAML:2.0:nameid-format:persistent.
-
-
In Protocol Settings → Assertion Consumer Service URL, set the following properties:
-
Set Binding to POST.
-
Set Endpoint URL to
https://your-slack-domain.slack.com/sso/saml.
-
-
In Protocol Settings → Allowable SAML Bindings, enable POST and REDIRECT.
-
In Protocol Settings → Signature Policy, select Always Sign Assertion.
-
In Credentials → Digital Signature Settings, select the PingFederate Signing Certificate.
-
-
Save the configuration.
-
Export the signing certificate.
-
Export the metadata file, open it in a text editor, and copy:
-
The entityID
-
The Location entry,
https://your-value/idp/SSO.saml2
-
Add the PingFederate connection to Slack
Choose from:
- For Slack Standard or Plus, do the following
-
-
Sign on to your Slack Workspace as an administrator.
-
Go to Settings & Administration → Workspace Settings.
-
Click the Authentication tab.
-
In the Configure an authentication method section, on the SAML authentication line, click Configure.
-
If prompted, enter your password to continue.
-
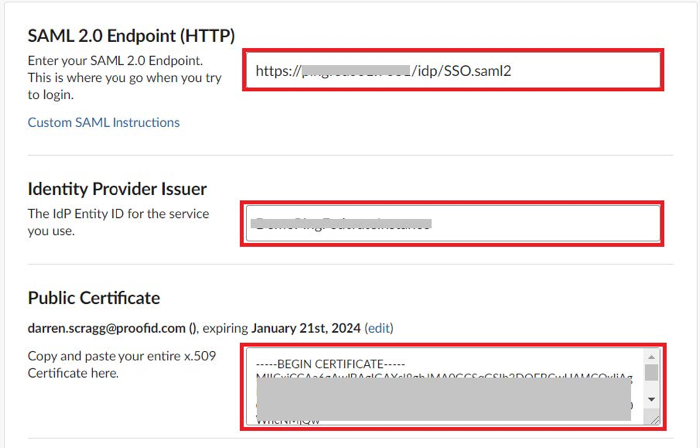
In the SAML 2.0 Endpoint (HTTP) field, enter the PingFederate Location value.
-
In the Identity Provider Issuer field, enter the PingFederate entityID value.
-
In the Public Certificate field, paste in the contents of the PingFederate signing certificate.
-
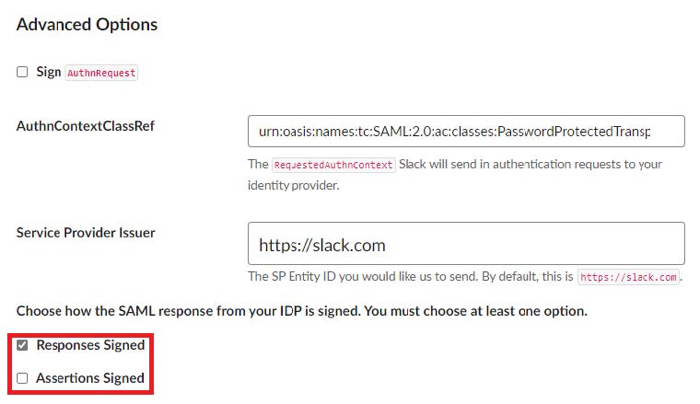
Expand the Advanced Options section, and clear the Assertions Signed check box.
-
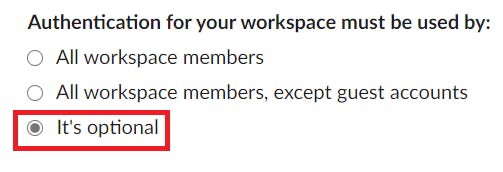
In the Settings section, select the It’s optional radio button for the authentication setting.
You can change the authentication setting to your desired value after you have completed testing.
-
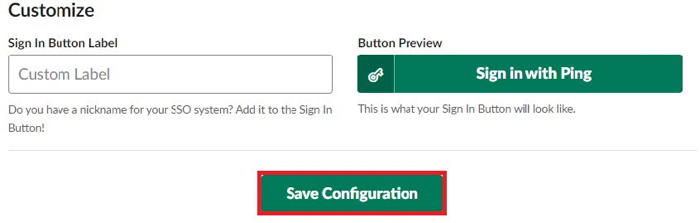
Click Save Configuration.
-
When you’re redirected to PingFederate, authenticate with PingFederate.
Your selection is confirmed against PingFederate and saved if successful.
-
- For Slack Enterprise Grid, do the following
-
-
Sign on to your Slack Organization (not Workspace) as an administrator.
-
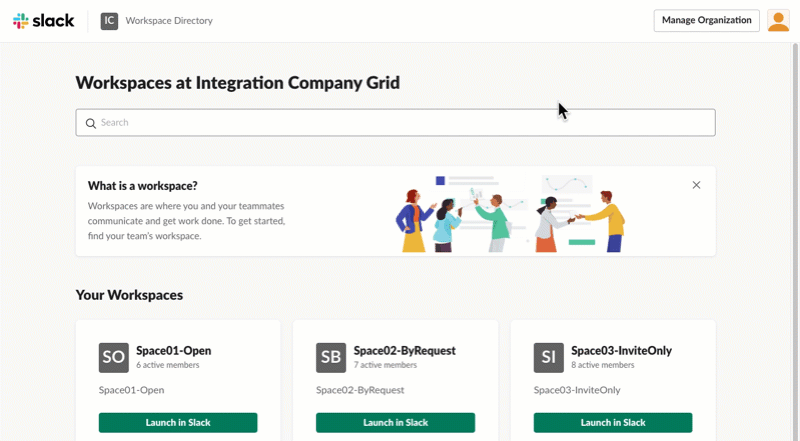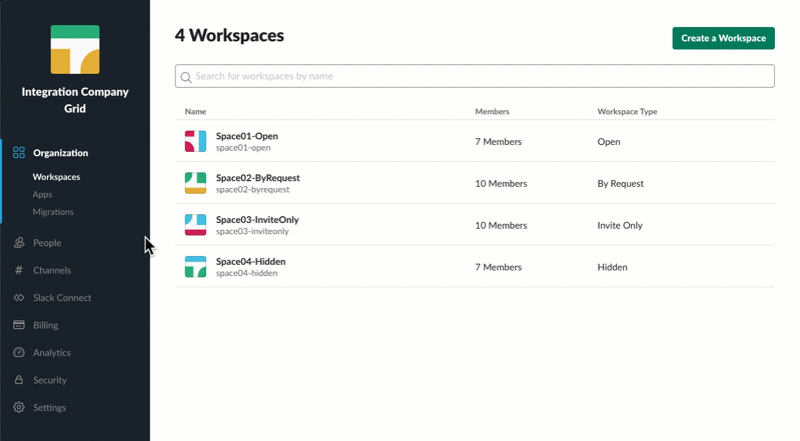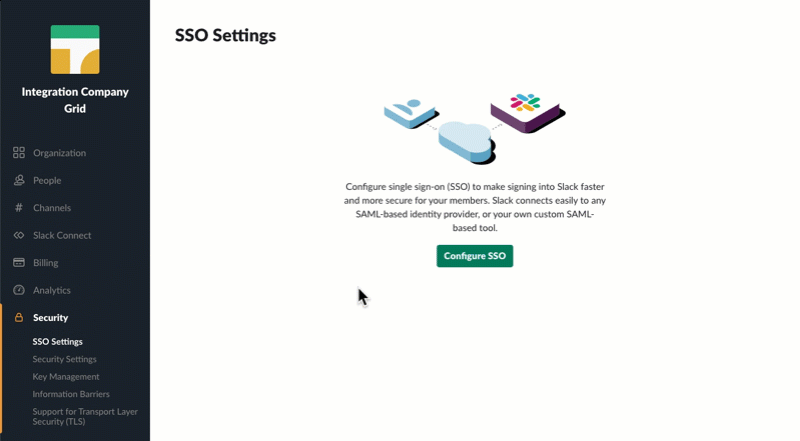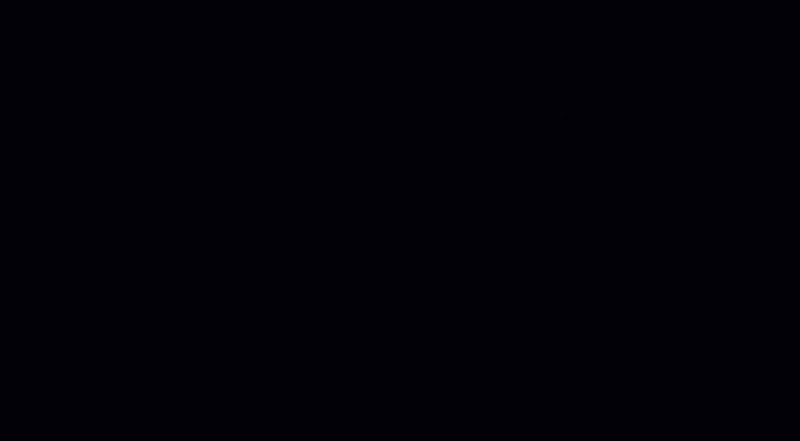
Go to Manage Organization → Security → SSO Settings → Configure SSO.
-
In the SAML 2.0 Endpoint (HTTP) field, enter the PingFederate Location value from the metadata file.
-
In the Service Provider Issuer URL, use the default value of https://slack.com.
-
In the Public (X.509) Certificate field, enter the contents of your PingFederate signing certificate.
-
Enable authentication request signing.
-
Select the Sign the AuthnRequest check box.
-
Copy the certificate text.
-
Create a new
.crtfile on your computer and paste the certificate text. -
In PingFederate, import the
.crtfile as a trusted certificate authority. For help, see Manage Trusted Certificate Authorities in the PingFederate documentation.
-
-
Clear the Sign the Assertion check box.
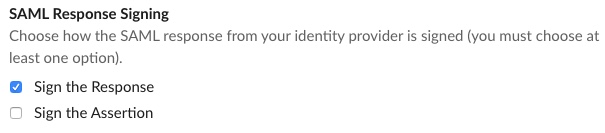
-
Click Test Configuration.
-
Sign out of Slack and then sign back on using SSO.
-
Test the PingFederate IdP-initiated SSO integration
-
Go to the PingFederate SSO application endpoint for the Slack SP connection.
-
Complete the PingFederate authentication.

You’re redirected to your Slack domain.
Test the PingFederate SP-initiated SSO integration
-
Go to your Slack domain,
https://your-domain.slack.com. -
Click Sign in with Ping.

-
After you’re redirected, enter your PingFederate username and password.
After successful authentication, you’re redirected back to Slack.
If the user doesn’t exist in Slack, you are prompted to accept the Slack terms.
