Configuring SAML SSO with BambooHR and PingFederate
About this task
The following table details the required and optional attributes to be configured in the assertion attribute contract.
| Attribute Name | Description | Required / Optional |
|---|---|---|
|
Email address for user |
Required |
The following table details the references that are used within this guide which are environment specific. Replace these with the suitable value for your environment.
| Reference | Description |
|---|---|
tenant |
BambooHR Tenant name |
Steps
-
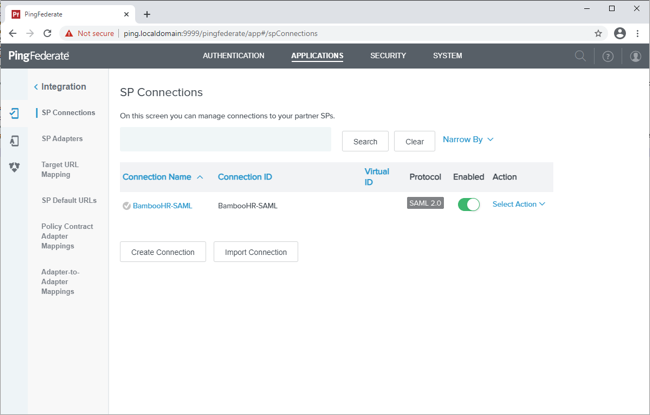
Create the PingFederate service provider (SP) connection for BambooHR.
-
Sign on to the PingFederate administrative console.
-
Using the metadata from
https://tenant.bamboohr.com/saml/sp_metadata.php, create an SP connection in PingFederate:-
Configure using Browser SSO profile SAML 2.0
-
Enable the IdP-Initiated SSO SAML profile.
-
Enable the SP initiated SSO SAML profile.
-
In Assertion Creation → Attribute Contract, set the Subject Name Format to urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress.
-
In Assertion Creation → Attribute Contract Fulfillment, map the attribute SAML_SUBJECT to the attribute mail.
-
In Protocol Settings → Allowable SAML Bindings, enable Redirect.
-
-
Export the metadata for the newly-created SP connection.
-
Export the signing certificate public key.
-
-
Configure the PingFederate identity provider (IdP) connection for BambooHR.
-
Sign on to BambooHR as a Full Admin administrator user.
-
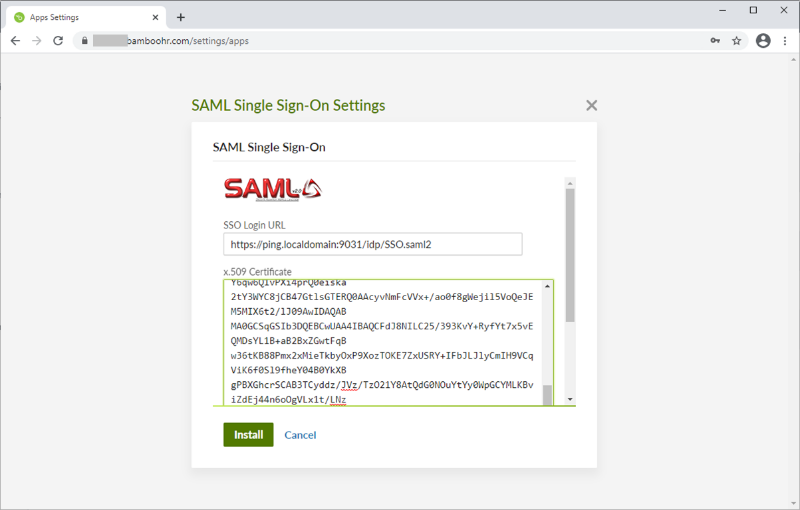
On the Settings page, click Apps.
-
On the SAML Single Sign-On application published by BambooHR line, click Install.

-
In the SSO Login URL field, enter the URL Location for SingleSignOnService Location retrieved from the PingFederate SP metadata that you downloaded from the BambooHR configuration.
Example:
https://PingFederateHostname:PingFederatePort/idp/SSO.saml2 -
In a text editor, open the signing certificate that you downloaded in from PingFederate and paste the contents into the x.509 Certificate field.
-
Click Install.
Result:
Your configuration is complete.
From this point BambooHR will redirect to the configured IdP for authentication for all new sessions. You should complete testing in a private or incognito browser session while keeping the original admin session active. This allows you to change settings or remove the configuration if the integration testing fails.

-
-
Test the integration.
Choose from:
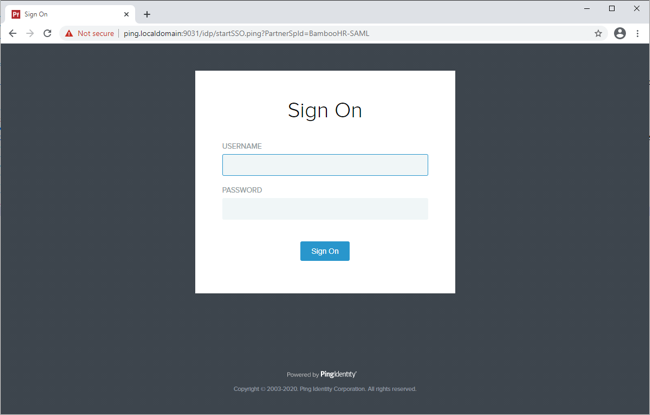
- PingFederate IdP-initiated SSO
-
-
Go to the SSO Application in the PingFederate Application configuration to perform IdP-initiated SSO, such as https://PingFederateHostname:PingFederatePort/idp/startSSO.ping?PartnerSpId=BambooHR-SAML.
-
Go to the SSO Application Endpoint in the BambooHR configuration
-
- PingFederate SP-initiated SSO
-
Go to the URL for your BambooHR tenant: https://tenant.bamboohr.com