Configuring SAML SSO with Amazon Managed Grafana and PingOne
Learn how to configure SAML SSO for Amazon Managed Grafana and PingOne.
About this task
|
Amazon Managed Grafana only supports SP-initiated SSO that is initiated from the Grafana Workspace URL. |
Configuring an Amazon Managed Grafana connection
Steps
-
Set up the Amazon Managed Grafana application in PingOne:
-
Go to Applications → Application Catalog.
-
In the Application Catalog, search for
Grafana. -
Expand the Amazon Managed Grafana entry and click Setup.
-
Review the instructions to configure SAML with the Amazon Managed Grafana console.
-
Click Continue to Next Step.
-
-
In the ACS URLfield, replace the
${namespace}and${region}variables with your Grafana namespace and your AWS region. -
In the Entity ID field, replace the
${namespace}and${region}variables with your Grafana namespace and your AWS region. -
Click Continue to Next Step.
Mapping Amazon Managed Grafana attributes
About this task
PingOne will automatically populate required SAML attributes.
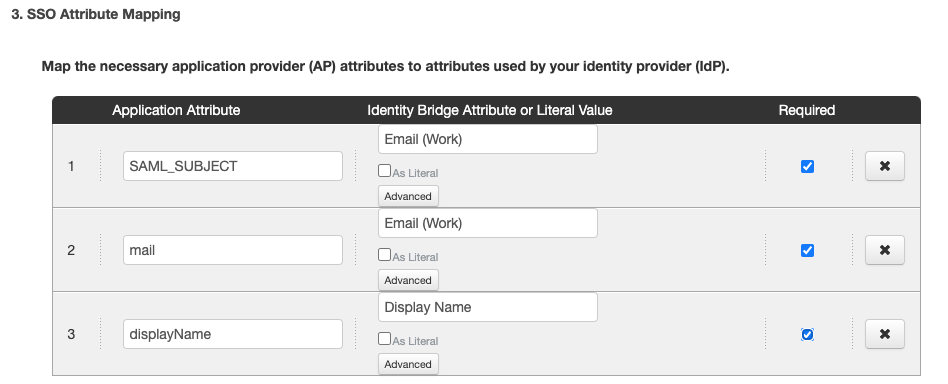
For Amazon Managed Grafana, the required attributes are:
-
SAML_SUBJECT -
mail -
givenName
|
You must set |
Steps
-
In the Application Attribute field, enter the attribute name as it appears in the application.
-
In the Identity Bridge Attribute or Literal Value field, choose one of the following.
Choose from:
-
Enter or select a directory attribute to map to the application attribute.
-
Select As Literal, then enter a literal value to assign to the application attribute.
-
-
Optional: To create advanced attribute mappings, click Advanced.
-
Click Continue to Next Step.
Customizing Amazon Managed Grafana boxes
Steps
-
To change the application icon, click Select Image and upload a local image file.
The image file must be:
-
PNG, GIF, or JPG format
-
312 x 52 pixels maximum
-
2 MB maximum file size
Images are scaled to 64 X 64 pixels for display.
-
-
To change the name of the application displayed on the dock, in the Name field, enter a new name.
-
To change the description of the application, in the Description field, enter the new description.
-
To change the category the application is assigned on the dock, in the Category list, select a category.
-
Click Continue to Next Step.
Assigning Amazon Managed Grafana group access
About this task
The Group Access tab shows every user group that you’ve created.
Steps
-
To add a group’s access to Amazon Managed Grafana, on the row for that group, click Add.
-
To remove a group’s access, on the row for that group, click Remove.
-
After you finish assigning groups, click Continue to Next Step.
Configuring Amazon Managed Grafana SAML
Steps
-
In PingOne, on the Review Setup tab, either:
Choose from:
-
Click Download to download the SAML metadata file
-
Copy the PingOne SAML Metadata URL.
-
-
Click Finish to add Amazon Managed Grafana to your PingOne dock.
-
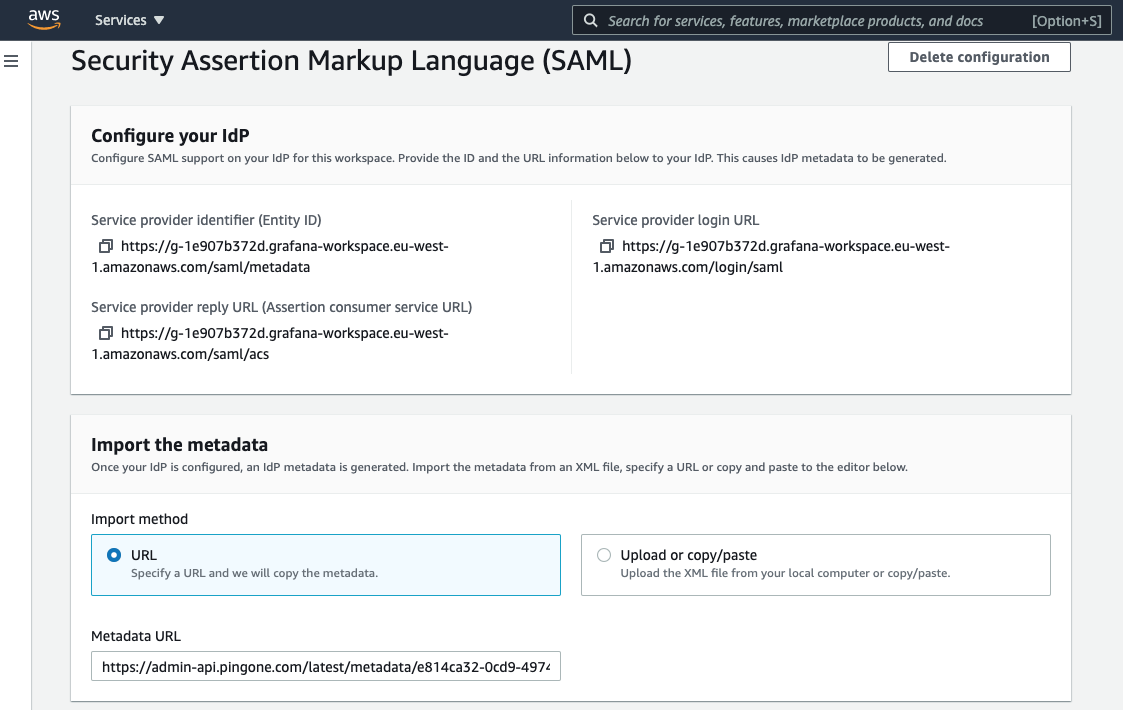
In the AWS Console, go to the Amazon Managed Grafana console.
-
To import the SAML metadata into Amazon Managed Grafana, either:
Choose from:
-
Use the PingOne SAML Metadata URL on the Amazon Managed Grafana connection summary page in PingOne.
-
Upload the SAML metadata file.
-
Assigning Amazon Managed Grafana administrators
About this task
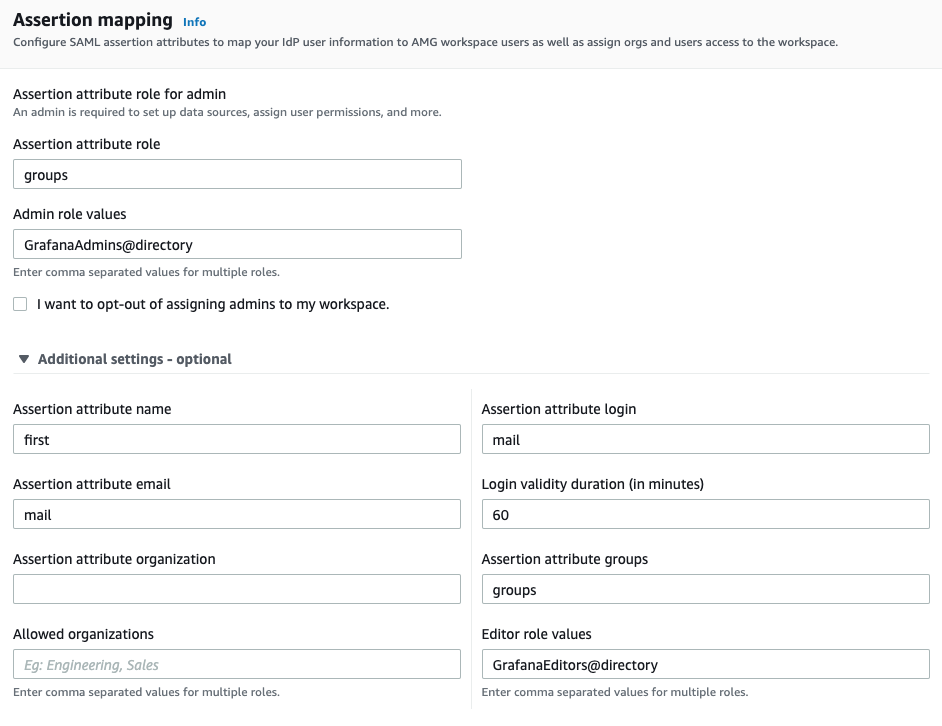
During authentication to Amazon Managed Grafana, you can optionally assign the Grafana Admin role to users by defining an admin role attribute and populating a PingOne SAML assertion attribute with the expected agreed-upon value.
For the example configuration, in PingOne, the memberOf attribute is mapped to the SAML assertion groups attribute. In Amazon Managed Grafana, the SAML assertion groups attribute is mapped to the Grafana admin role value, as shown in the following image.
Steps
-
In your Amazon Managed Grafana workspace, go to SAML Configuration.
-
In the Assertion mapping section, in the Assertion attribute role field, enter
groups. -
Set the Admin role valuesto the PingOne group for Grafana admins.
The example in step 7 uses GrafanaAdmins@directory. The @directory is appended to any PingOne group name.
-
Optional: Set the Assertion attribute groupsto the groups and Editor role valuesto the PingOne group for Grafana editors.
-
Click Save SAML configuration.
-
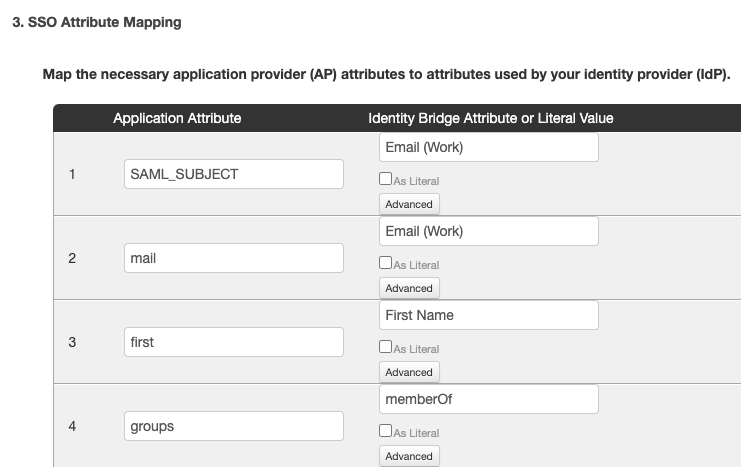
In PingOne, go to Amazon Managed Grafana application Attribute Mapping.
-
Map PingOne’s memberOf attribute to the SAML assertion groups attribute.
Result:
Users in the PingOne GrafanaAdmins group are Just-In-Time provisioned during authentication as Grafana admins, and users in the PingOne GrafanaEditorsgroup are Just-In-Time provisioned during authentication as Grafana editors.