Configuring SAML SSO with DocuSign and PingOne for Enterprise
Learn how to enable DocuSign sign on from the PingOne for Enterprise console (IdP-initiated sign-on) and direct DocuSign sign on using PingOne for Enterprise (SP initiated sign on).
Before you begin
-
Link PingOne for Enterprise to an identity repository containing the users requiring application access.
-
Make sure DocuSign has a valid domain, an organization created, and is populated with at least one user to test access.
-
You must have administrative access to PingOne for Enterprise and DocuSign.
Copy PingOne values for the Supplied DocuSign Application
-
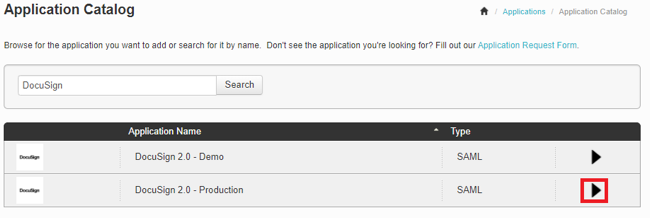
Sign on to PingOne for Enterprise, go to Applications → Application Catalog, and search for DocuSign.
-
Expand the DocuSign 2.0 - Production entry and click the Setup icon.
-
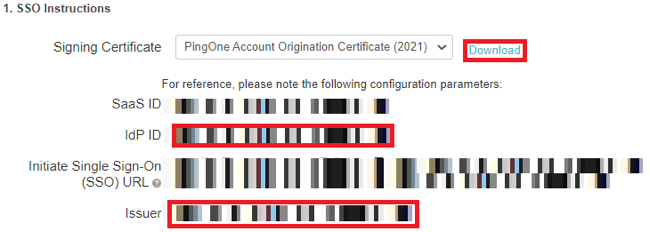
Copy the Issuer and IdP ID values.
-
Download the Signing Certificate.
Add the PingOne for Enterprise IdP Connection to DocuSign
-
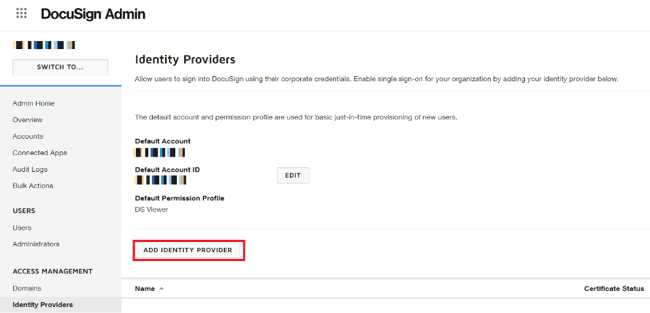
Sign on to your DocuSign Admin organization as an administrator.
-
In the left navigation pane, select Identity Providers, and then click Add Identity Provider.
-
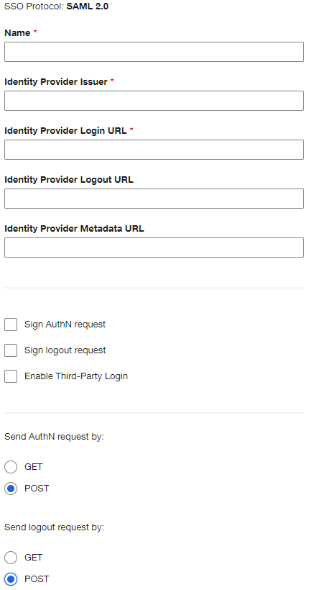
Configure the following fields
Field Value Name
A name for the identity provider
Identity Provider Issuer
The Issue value from PingID
Identity Provider Login URL
https://sso.connect.pingidentity.com/sso/idp/SSO.saml2?idpid=PingOne for Enterprise IdP ID valueSend AuthN Request by
POST
Select Send Logout Request by
POST
-
In the Custom Attribute Mapping section, click Add New Mapping, and then:
-
In the Field list, select surname, then enter
surnamein the Attribute field. -
In the Field list, select givenname, then enter
givennamein the Attribute field. -
In the Field list, select emailaddress, then enter
emailaddressin the Attribute field.
-
-
Click Save.
-
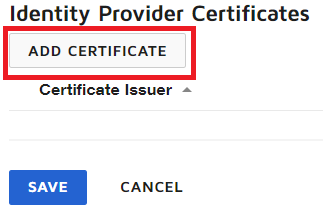
Click Add New Certificate.

-
Click Add Certificate.
-
Select the signing certificate that you downloaded from PingOne for Enterprise. Click Save.
-
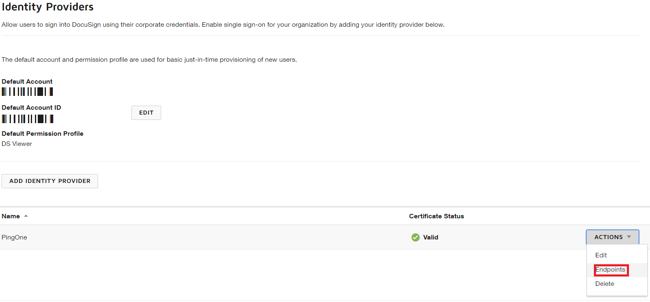
In the Actions list for the IdP that you created, select Endpoints.
-
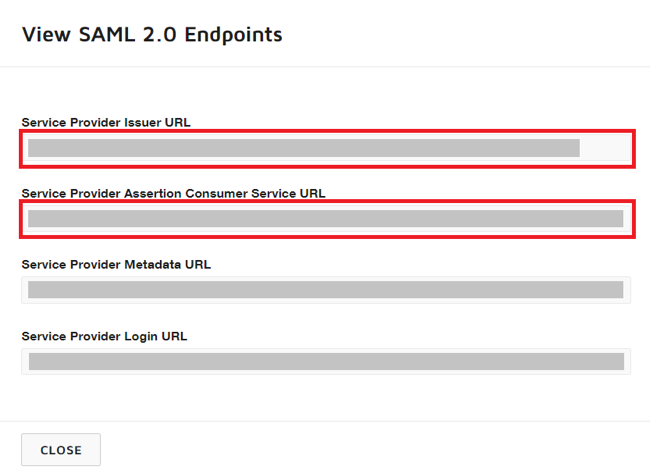
Copy the Service Provider Issuer URL andService Provider Assertion Consumer Service URL values.
The DocuSign connection configuration is complete.
After testing, you can set the domain to require IP authentication to remove the DocuSign sign-on screen.
Complete the DocuSign setup in PingOne for Enterprise
-
Continue editing the DocuSign entry in PingOne for Enterprise.
If the session has timed out, complete the initial steps to the point of clicking Setup.
-
Click Continue to Next Step.
-
Set the ACS URL to the DocuSign Service Provider Assertion Consumer Service URL value.
-
Set the Entity ID to the DocuSign Service Provider Issuer URL value.
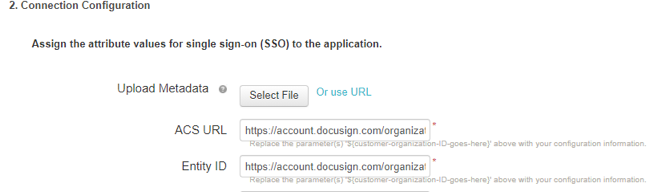
Do not just update the organization ID.
-
Click Continue to Next Step.
-
Map the required attributes to the corresponding attribute names in your environment.
The corresponding attribute names might not be an exact match.
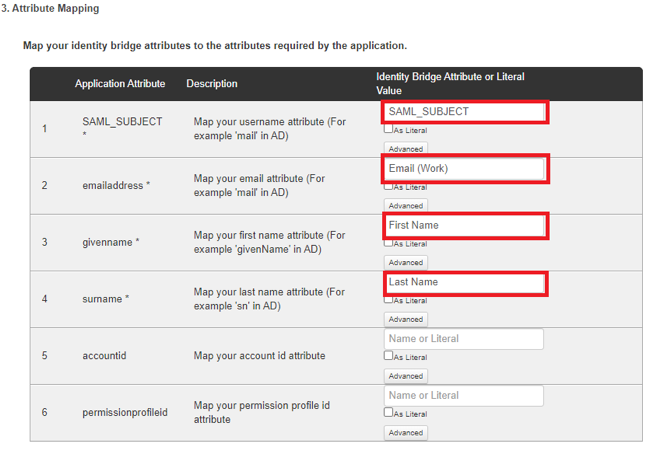
-
On the SAML_SUBJECT line, click Advanced, and change the name format you’re sending to DocuSign to
urn:oasis:names:tc:SAML:2.0:nameid-format:persistent. -
Click Continue to Next Step twice.
-
Click Add for all user groups that should have access to DocuSign.
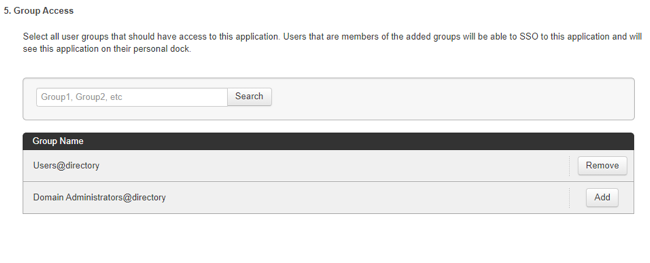
-
Click Continue to Next Step.
-
Click Finish.
PingOne for Enterprise configuration is complete.
Test the PingOne for Enterprise IdP-initiated SSO integration
-
Go to your Ping desktop as a user with DocuSign access.
To find the Ping desktop URL in the Admin console, go to Setup → Dock → PingOne Dock URL.
-
Complete the PingOne for Enterprise authentication.
You’re redirected to your DocuSign domain.
Test the PingOne for Enterprise SP-initiated SSO integration
-
Go to https://account.docusign.com.
-
Enter your email address.
-
Click Use Company Login.
-
When you’re redirected to PingOne for Enterprise, enter your PingOne username and password.
After successful authentication, you’re redirected back to DocuSign.