Configuring SAML SSO with Salesforce and PingOne for Enterprise
Enable Salesforce sign-on from the PingOne for Enterprise console (IdP-initiated sign-on) plus single logout (SLO).
Before you begin
-
Link PingOne for Enterprise to an identity repository containing the users requiring application access.
-
Populate Salesforce with at least one user to test access.
-
You must have administrative access to PingOne for Enterprise and Salesforce.
Extract the PingOne for Enterprise metadata for Salesforce
-
Sign on to PingOne for Enterprise and go to Applications → Application Catalog.
-
Search for
Salesforce.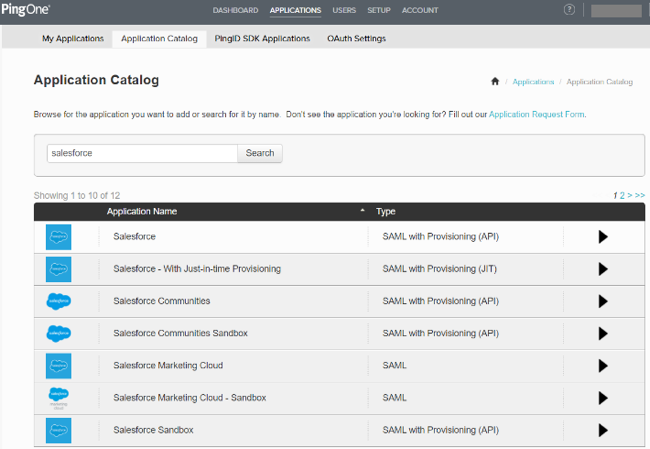
-
Expand the Salesforce entry and click the Setup icon.
-
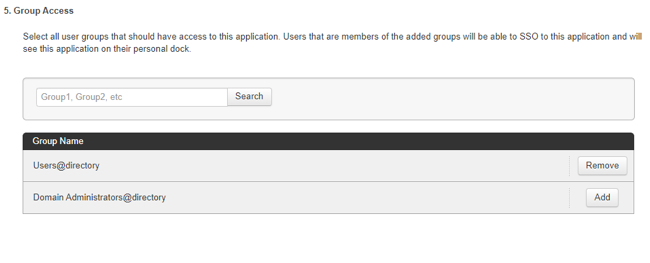
Click Continue to Next Step until you’re on the Group Access page.
You’ll configure the application settings later through metadata.
-
Click Add for each user group that should have access to Salesforce.
-
Click Continue to Next Step.
-
Download the PingOne for Enterprise signing certificate and SAML metadata.
-
Click Finish.

Add the PingOne for Enterprise IdP Connection to Salesforce
-
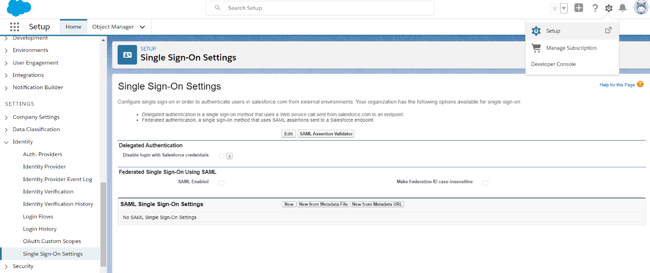
Sign on to your Salesforce domain as an administrator.
-
Click the Gear icon (), then go to Setup → Identity → Single Sign-On Settings.
-
On the Single Sign-On Settings page, click Edit.
-
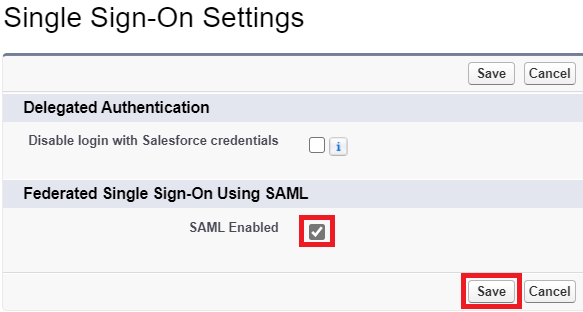
Select the SAML Enabled check box to enable the use of SAML SSO. Click Save.
-
Click New From Metadata File.
-
Click Choose File, select the SAML metadata file that you downloaded from PingOne for Enterprise, and click Create.
The summary screen opens.
-
On the Identity Provider Certificate line, click Choose File and select the signing certificate that you downloaded from PingOne for Enterprise.
-
Set Service Provider Initiated Request Binding to HTTP POST.
-
Set Single Logout Request Binding to HTTP POST.
-
Clear the Single Logout Enabled check box if you don’t require single logout.
The summary screen will resemble the following:
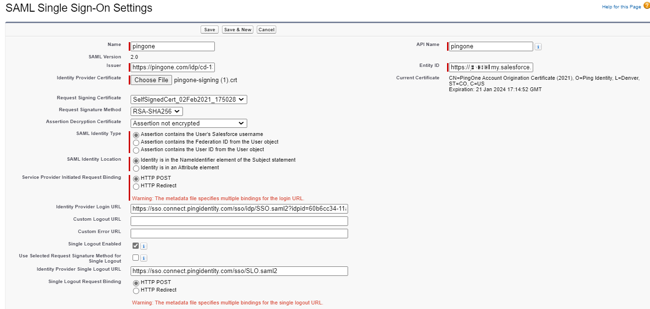
-
Ignore the metadata file warnings and click Save.
-
Click Download Metadata to save the Salesforce metadata.
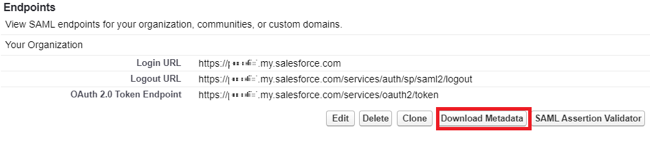
Import the Salesforce metadata into PingOne.
-
Sign on to PingOne for Enterprise and go to Applications → My Applications.
-
Expand the Salesforce entry and click Edit.
-
Click Continue to Next Step.
-
Click Select File and select the metadata file that you downloaded from Salesforce.
The ACS URL, Entity ID, Single Logout Endpoint, and Primary Verification Certificate fields should now be populated.
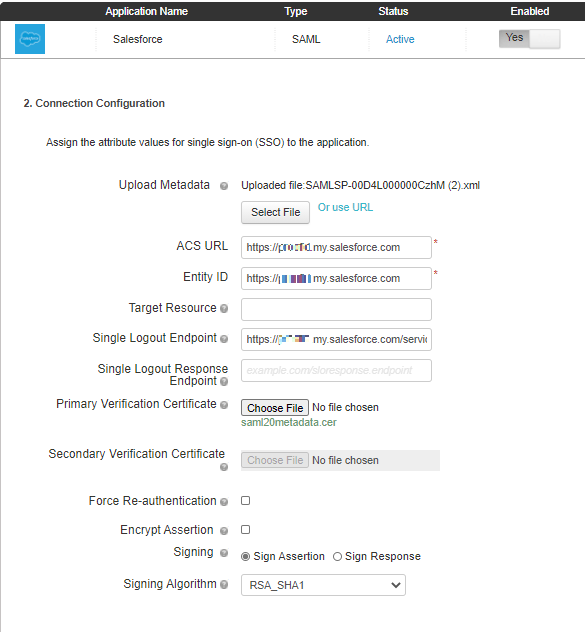
-
Click Continue to Next Step on the remaining pages then click Finish.
This step assumes that your usernames in Salesforce match the ones in PingOne for Enterprise. If this is not the case, then you must map the expected Salesforce username value on the third page.
Test the PingOne for Enterprise IdP-initiated SSO integration
-
Go to your Ping desktop as a user with Salesforce access.
To find the Ping desktop URL in the Admin console, go to Setup → Dock → PingOne Dock URL.
-
Complete PingOne for Enterprise authentication.
You’re redirected to your Salesforce domain.
Configure direct Salesforce sign on using PingOne (SP-initiated login) plus SLO
Before you begin
-
You must first enable identity provider (IdP)-initiated sign-on.
Enable PingOne authentication in Salesforce
-
Sign on to your Salesforce domain as an administrator.
-
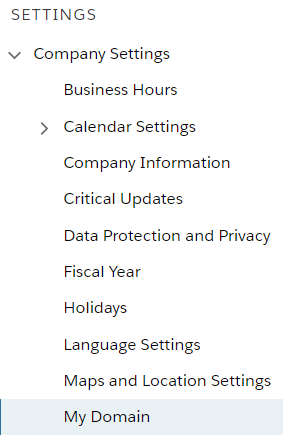
Click the Gear icon, then go to Setup → Company Settings → My Domain.
-
Make a note of your domain name, for example,
https://your-company.my.salesforce.com -
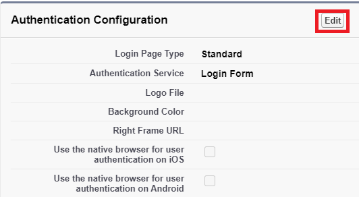
In the Authentication Configuration section, click Edit.
-
In the Authentication Service list, select PingOne. Click Save.
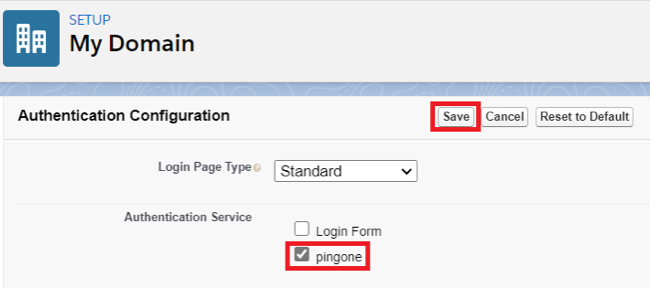
This entry was created as a result of the IdP-initiated sign-on task.
Configuration is complete.
|
Salesforce will now redirect to PingOne for authentication of all new sessions. You should also select the Login Form check box during the testing phase in case of authentication issues. Testers will be offered the option of the standard Salesforce login form or PingOne authentication. After you’ve successfully tested authentication, you can clear the Login Form check box so that authentication automatically defaults to PingOne. |
Test the PingOne SP-initiated SSO integration
-
Go to your Salesforce domain.
If the Login Form check box is still selected, the Salesforce sign-on screen still displays, and you’re offered a choice of Salesforce sign on or PingOne sign, select PingOne.
If you’ve cleared the Login Form check box, you’re not offered a choice.
-
When you are redirected to PingOne, enter your PingOne username and password.
After successful authentication, you’re redirected back to Salesforce.