Configuring SAML SSO with SAP Netweaver and PingOne for Enterprise
Learn how to configure SAML SSO with SAP Netweaver and PingOne for Enterprise.
Before you begin
Refer to the vendor documentation and complete the following:
-
Ensure that HTTPS is enabled for your SAP system.
-
Activate Secure Session Management.
-
Enable SAML 2.0 support:
-
Create a local provider.
-
Export metadata for local provider.
-
About this task
The following table details the required and optional attributes to be configured in the assertion attribute contract.
| Attribute Name | Description | Required / Optional |
|---|---|---|
SAML_SUBJECT |
Username |
Required |
Create a PingOne for Enterprise application for SAP Netweaver
|
The following configuration is untested and is provided as an example. Additional steps might be required. |
-
Sign on to PingOne for Enterprise and click Applications.
-
On the SAML tab, click Add Application.
-
Enter the following:
-
A suitable Application Name, such as
SAP Netweaver. -
A suitable Application Description.
-
A suitable Category, such as
Information Technology. -
(Optional) Upload an icon to be used in the PingOne for Enterprise dock.
-
-
Click Continue to Next Step.
-
Select I have the SAML configuration.
-
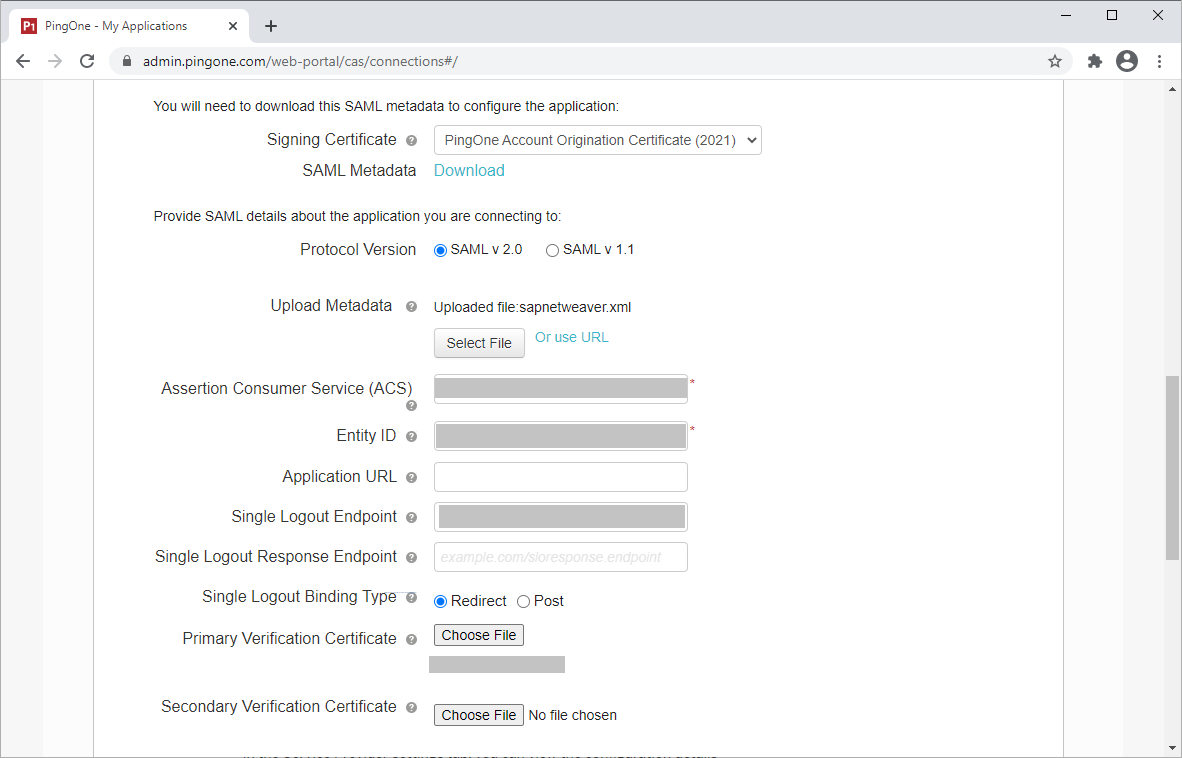
In the Signing Certificate list, select a suitable signing certificate.
-
For Protocol Version, click SAML v.2.0.
-
Upload the metadata from your SAP Netweaver local provider configuration.
-
Click Continue to Next Step.
-
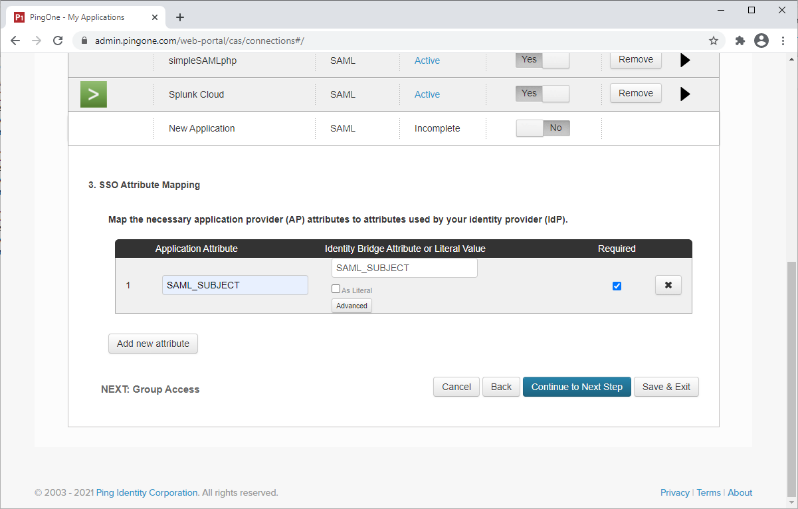
In the SSO Attribute Mapping section, add the following mapping for the SAML_SUBJECT:
-
For Identity Bridge Attribute or Literal Value, select the appropriate attribute. This should match the username for the user in SAP Netweaver.
-
Select the Required check box.
-
-
Click Continue to Next Step.
-
Add the user groups for the application.
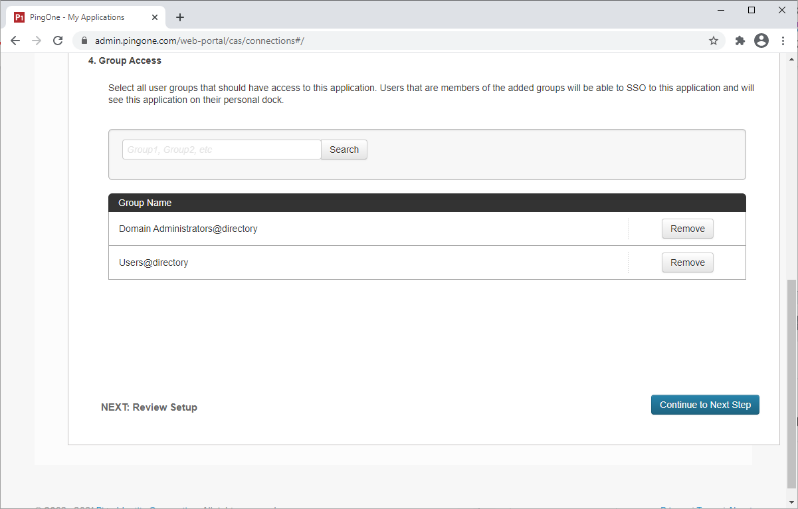
-
Click Continue to Next Step.
-
Review the settings.
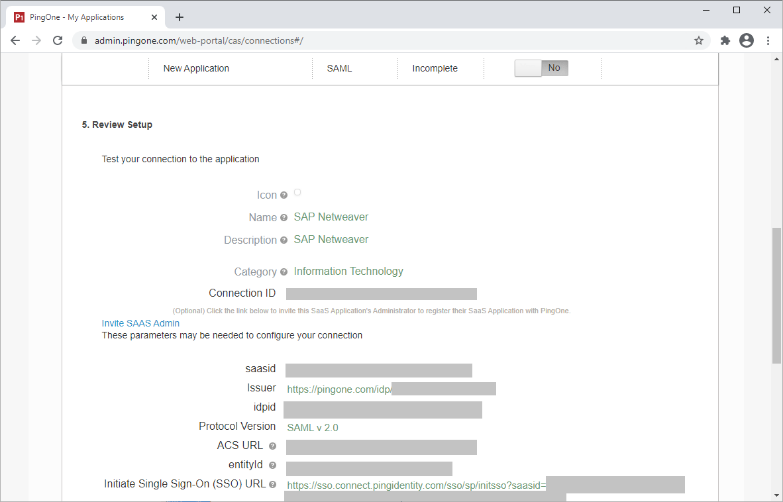
-
Copy the Single Sign-On (SSO) URL value to a temporary location.
This is the IdP-initiated SSO URL that you can use for testing.
-
Note the idpid and Issuer values.
-
On the Signing Certificate line, click Download.
You’ll use this for the application configuration.
-
On the SAML Metadata line, click Download.
You’ll use this for the application configuration.
-
Click Finish.
Configure the PingOne for Enterprise IdP connection for SAP Netweaver
-
Sign on to SAP Netweaver as an administrator.
-
Go to Trusted Partners and select Identity Providers.
-
Click Add.
-
Click Upload Metdata File, select the file that you downloaded from PingOne for Enterprise, and click Next.
-
On the Provider Name page, verify the data populated. Click Next.
-
On the Signature and Encryption page, verify the data populated. Click Next.
-
On the Single Sign-On Enpoints page, verify the data populated. Click Next.
-
On the Single Logout Endpoints page, verify the data populated. Click Next.
-
Select Binding as HTTP POST. Click Finish.
-
Enable the provider.
After testing, you can enable SP-initiated SSO for SAP Netweaver by editing the configuration in sap/opu/odata/iwfnd/catalogservice.