Configuring SAML SSO with Namely and PingFederate
Learn how to enable Namely sign-on from the PingFederate console (IdP-initiated sign-on) and direct Namely sign-on using PingFederate (SP-initiated sign-on).
Before you begin
-
PingFederate should be configured to authenticate against an identity provider (IdP) or datastore containing the users requiring application access.
-
Populate Namely with at least one user to test access.
-
You must have administrative access to PingFederate.
Create the Namely metadata
-
In PingFederate, create a service provider (SP) connection for Namely:
-
Configure using Browser SSO profile SAML 2.0.
-
Set Partner’s Entity ID to
https://your-subdomain.namely.com/saml/metadata. -
Enable the following SAML profiles:
-
IdP-Initiated SSO
-
SP-Initiated SSO
-
-
In Assertion Creation: Authentication Source Mapping: Attribute Contract Fulfilment, map the SAML_SUBJECT to your email attribute.
-
In Protocol Settings: Assertion Consumer Service URL, set Binding to POST and set Endpoint URL to
https://your-subdomain.namely.com/saml/consume. -
In Protocol Settings: Allowable SAML Bindings, enable POST.
-
In Credentials: Digital Signature Settings, select the PingFederate Signing Certificate.
-
Note the metadata URL for the newly-created Namely SP connection.
-
Add the PingFederate connection to Namely
-
Sign on to the Namely console as an administrator.
-
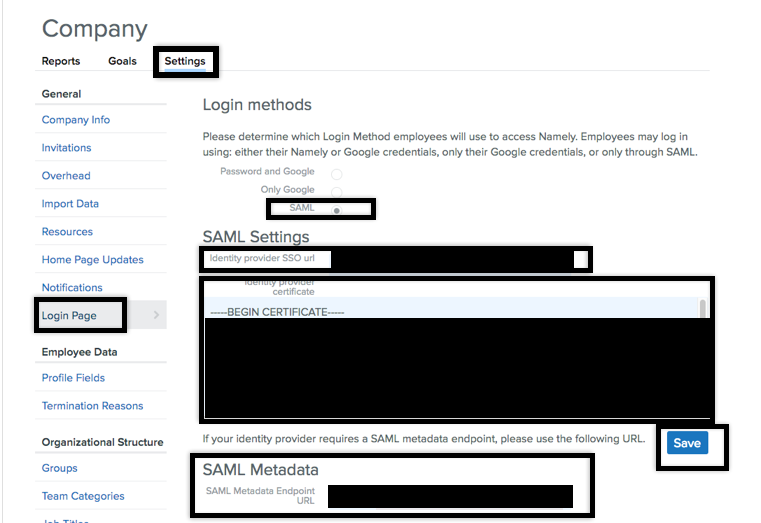
Select Company on the top navigation bar.
-
Click the Settings tab.
-
In the left navigation pane, click Login Page.
-
In the Login Methods section, click SAML.
-
Enter the Identity Provider SSO URL from PingFederate.
-
Copy and paste the IdP Provider Certificate value into the Identity provider certificate.
-
Enter the SAML Metadata URL from PingFederate.
-
Click Save.